The new Google Assistant is only officially available on three platforms—newer Android phones (Pixels and those running Marshmallow and Nougat), the Google Allo app, and Google Home. However, most of the Assistant's basic functionality is also bundled into the Google app for Android and iOS, which used to go by the name Google Now, but is now referred to only as Screen Search or your Google app's Feed.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Apple claims that the iPhone 14 Pro and 14 Pro Max have the highest peak brightness of any smartphone, but is that really true?

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

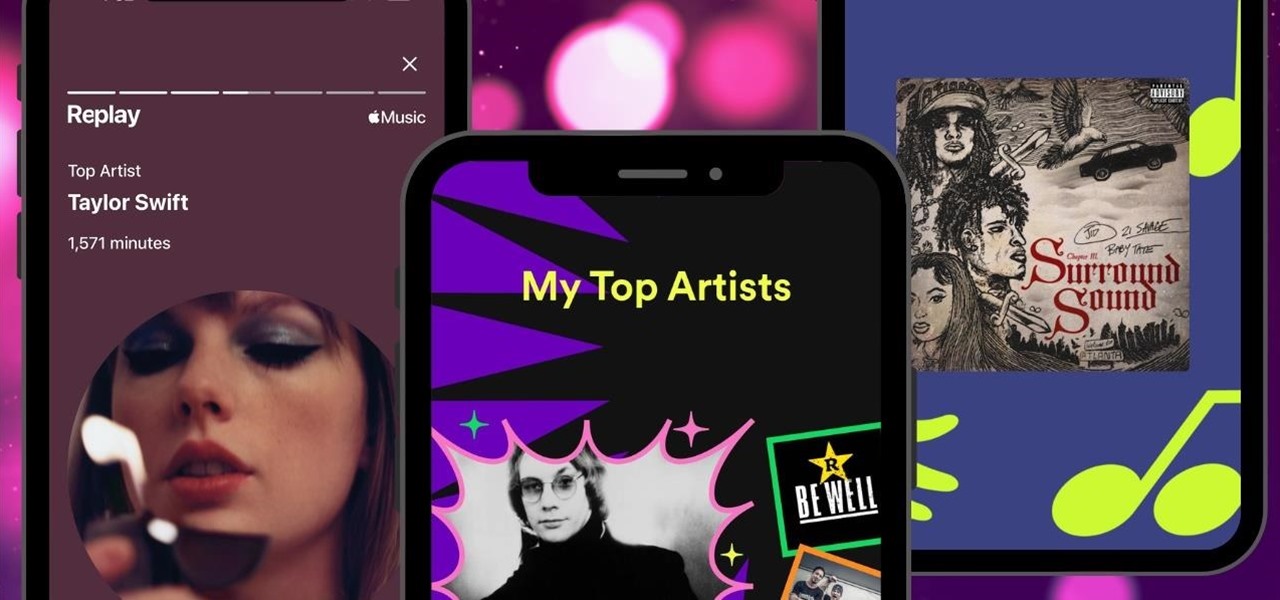
It's that time of year again. No, not the holiday season … the "share your year in music listening" season. And no matter which music streaming service you use, there's a way to find and share (or not share) your activity from 2022.

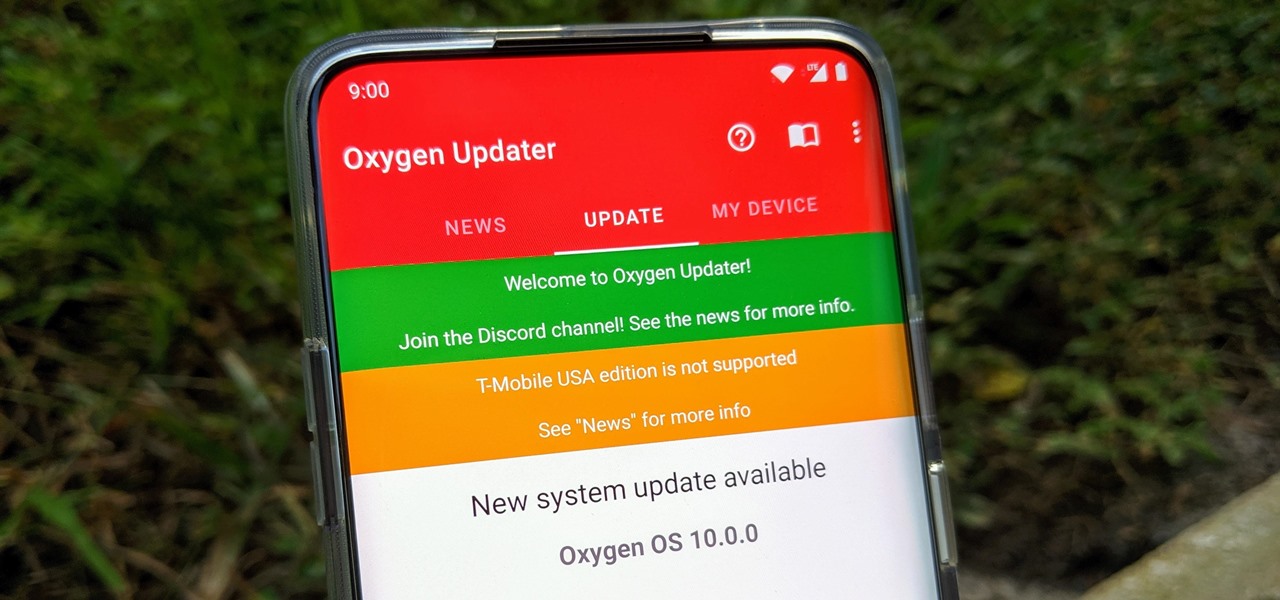
Multiple methods can be used to update OnePlus phones, but if you're rooted with TWRP installed, you might want to try this one out for yourself. The update method outlined in this guide works like a charm while maintaining your root status after an OTA update. One of the best parts about it — you don't have to rely on a computer like you did when you rooted the first time around.

Life's pretty good for iOS public testers — we get to check out new iPhone features months before the general public even knows they exist. That said, we aren't first to the party. Developers get priority during beta testing, as evidenced by yesterday's iOS 13 dev beta 6 release. It's not all bad though since Apple just released the public version of that software, public beta 5, this afternoon.

Unlike the realm of virtual reality, augmented reality is less about losing yourself in some fantasy environment, and more about getting things done in the real world. So while we've seen some great games that capture the imagination on devices like the Magic Leap One and the HoloLens, when it comes to real-world usage, the biggest developments coming for AR apps that are the more practical ones.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding your stuff.

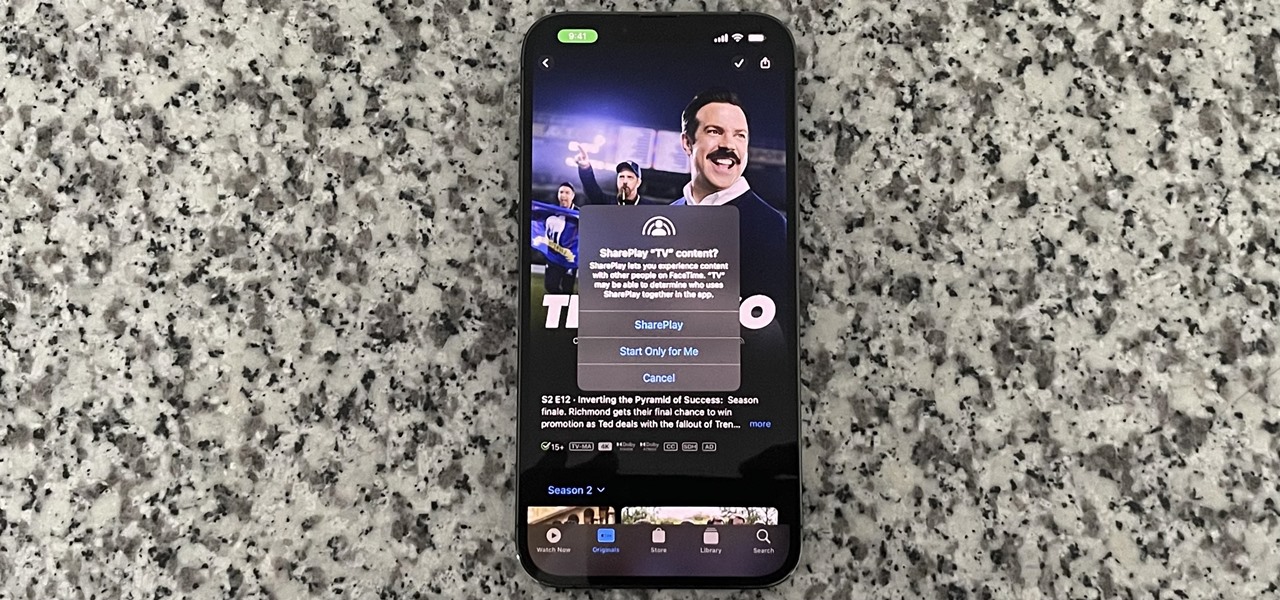
SharePlay is arguably one of the most significant features to hit FaceTime since group calls, and it's still hard to find apps that support shared experiences in FaceTime. Apple does list a few apps, but there is no official index of all the apps with SharePlay integration. That's where we come in.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

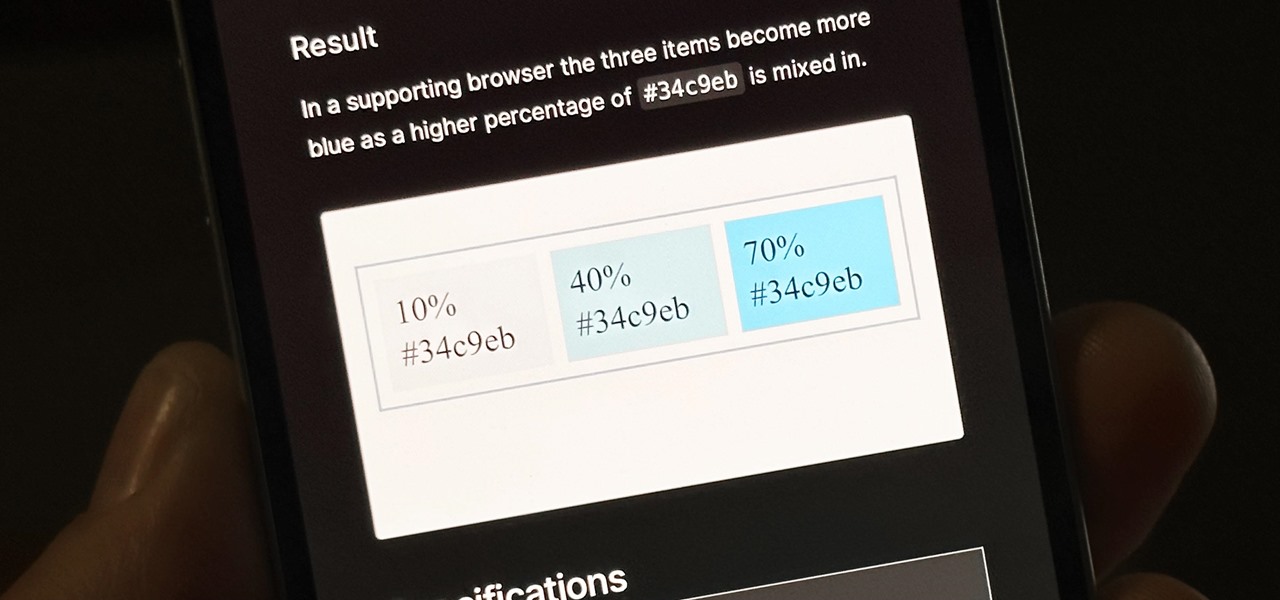
Getting used to your new Firefox 4 web browser? If so, you might have seen some improvements in the Location Bar. The updated features make browsing the web a cinch, so it's no wonder why more and more Internet junkies are calling it the Awesome Bar. It's faster and easier to use, and there's even some optional tweaks that you can employ to make your Internet experience smooth and effortless.

Whether it's the new iPad Killer or not, one thing's for sure—the Motorola XOOM is hackable. Just hours after its release last week, Verizon's new Android-based tablet (running Honeycomb) was rooted by hacker Koushik Dutta, which seems easy enough.

Check out this beginner tutorial on how to solve a sudoku intermediate number puzzle. Each sudoku has a unique solution that can be reached logically without guessing. Enter digits from 1 to 9 into the blank spaces. Every row must contain one of each digit. So must every column, as must every 3x3 square.

Choose and buy a Guitar - A beginners guide to the Guitar. The guitar is one of the most popular musical instruments there is, appealing to both the young and the not so young and spanning different musical genre's such as blues, pop, rock, classical and many more.

The angry New Yorker stereotype sure doesn't miss anyone. A woman from New York is suing her former Catholic college for not doing 'enough' for her while her dorm roommate was having too much sex. We're not entirely sure if the college even handed out ties to hang on doorknobs, let alone provide each room with a humidifier that has 3-4 different soothing sound loops for stress relief and relaxation.

Can't remember when to water the plants? Wish they could just tell you when they need watering—just call you on the phone or something? Or maybe text you, "Help I'm desiccating!" Telecommunications researcher Kate Harman has come up with the device of an absent-minded plant owner's dreams—Botanicalls. It hooks up to your plant and sends you a short text message when the plant is too dry. Each kit costs $99 and includes metal sensors connected to a microcontroller. Insert the sensors into the ...

Not enough bible in your games? Damn right! Until we get Grand Theft Moses this is the next best thing. Think of this game as the Old Testament + Acid Trip + Jpop Male Idols. From the Producers of Devil May Cry, Viewtiful Joe, and Okami. El Shaddai is a very unique looking game, very much looking forward to it.

If you think you're a Scrabble genius because you have all the two-letter words memorized, you're sorely wrong. To be a Scrabble genius, you have to know practically "every" word acceptable in Scrabble, so I'm guessing there's not too many Scrabble geniuses out there, because it's an impossible feat.

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

In a move that seemingly surprised everyone—including Samsung—Korean carriers have released the Galaxy S5 a full two weeks early to avoid being caught up in an about-to-be-imposed ban.

Following the first part in this series on advanced cracking techniques, we are going to go over how we can intelligently crack passwords using the old-fashioned bruteforce method. These unique cracking techniques aren't widely used, because most crackers are Script Kiddies who have no idea what the concepts are behind cracking passwords, thus, word won't get around too quickly.

More password cracking action from Null Byte! Today we aren't going to be cracking passwords per se, rather, we are going to learn the basics of generating rainbow tables and how to use them. First, let's go over how passwords are stored and recovered.

You may have asked yourself, "How do hackers take my password, if the website owner can't?" The answer is simple. When a website stores your login password for the site, it is run through a cryptographic hash function before it enters the database (if the website isn't Sony).

Meat and bourbon is a delicious marriage—whether it's bacon-infused bourbon, or bourbon drenched steaks. The recipe below is adapted from Nancy's bourbon-marinated rib eye recipe over at 'A Recipe a Day'. For this version, we used the classic New York strip, with a little sous vide twist (optional).