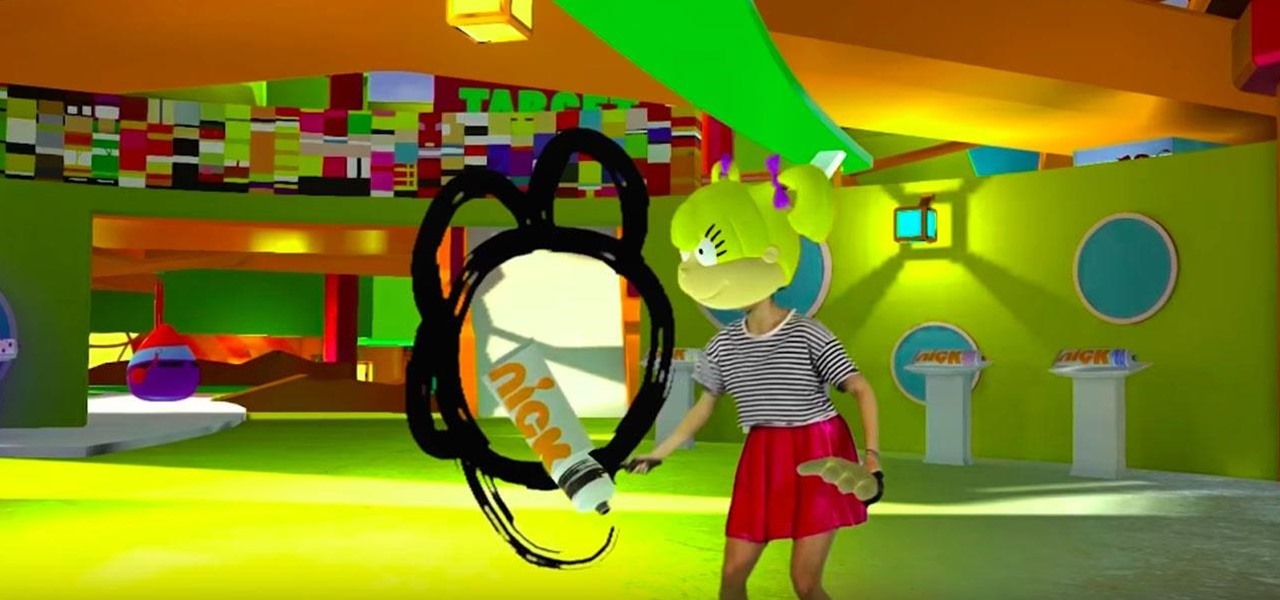Sick of lasagna? Check out this recipe for baked macaroni and branch out to new baked pastas! This recipe for baked macaroni is made in the style of Panlasangpinoy, a baked pasta dish from the Philipines. This meal is large and serves many, so consider making this for your next pot luck or family gathering. It tastes so yummy, you won't even have leftovers to clean up! Enjoy!

Make matchsticks jump! This impressive magic jumping matchstick bar trick is revealed for all - all the details. Win beer or money anywhere. Perfect for performing at a gathering, and it's so easy to learn. Only common household items are used.

Showing you how you can create the French braid look even with short layered hair about five inches in length. Starting at the front of your hair you begin the braiding process by gathering three lengths of hair. As you go further back you continue to gather hair into the braiding strands to continue the French braid look all the way back and secured with a scrunchy at the end to make a longer French braided style look otherwise not creatable with regular short hair. Easy to repeat and follow...

Curious about acrylic paints and how to apply them to your fantasy-inspired works of art? Get some tips from a professional! This tutorial hosted by Ed Beard, an internationally reknown fantasy artist known for his published works in Magic the Gathering and Tolkien takes us through a quick step by step approach to "block-in" techniques with acrylic paints. "The Evolution of a Dragon Painting" is a great how-to video for those of you aspiring to be painters!

Need a little help on your shading technique? This tutorial on shading and shadowing techniques is hosted by Ed Beard, an internationally reknown fantasy artist known for his published works in Magic the Gathering and Tolkien. This video demonstrates how to choose a light source when shading, the values of dark to light, and how to ultilize shadows to embelish the three-dimensional depth to your drawing.

Ingredients Bun: All purpose flour: 180g, Warm water: 50ml, Sugar: 1 tsp, Dry yeast: 2 tsp, Oil: 2 tsp, Milk: 60ml

Have a crazy toddler at home? Patience is a key factor when taming an out-of-control toddler. Learn how to deal with a toddler's temper tantrum in the most effective way in this video.

It seems the French invent all the cool things! If you want to braid your hair in a new and stylish way, check out this video.

Learn how to cope when a pet dies. Few will ever love you as unconditionally as your pet does. So when you lose them, it's can be hard to move on. Here is some help.

Watch as a seasoned expert walks you through the steps of sliding screen door repair, from gathering your tools and buying the correct replacement parts to adjusting the newly-repaired door, in this free online video series about home maintenance.

This video tutorial shows you how to wallpaper. 1. Set the mood: To wallpaper a room you need caffeine and music, it's best to get that first. 2. Prepare the space: Basically this step is set to gathering tools, patching holes, cleaning and sanding the walls, moving furniture and removing outlet and switch face plates. The tools are as follows: level, pencil, tape measure, step stool, wallpaper paste, paint tray, paint rollers and brushes, wall paper, squeegee, water bucket, sponge. utility k...

Learn how to practice proper etiquette on a BlackBerry, smartphone or PDA. Make sure your love for your BlackBerry or other PDA device isn't making you obnoxious.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

This tomato salad recipe with basil and feta is a delicious side dish and great to take-along to a party or gathering. With a loaf of crusty French bread tomato salads are a fresh and summery meal. Tomatoes in a salad are a beautiful and yummy way to bring your garden to the table. Watch and learn how to make this tomato, basil and feta cheese salad.

LX.com's Shira Lazar visits Grace Restaurant to receive expert tips on tasting, serving, and picking out the perfect wine for your wine party. Wine tasting can be an elegant gathering, or a fun party with friends. Wines should be selected with the food serving in mind. Learn how to host a wine tasting party by watching this video tutorial.

This how to video sewing tutorial demonstrates how to sew a whip stitch by hand, just in case you don't have a sewing machine. The straight stitch is excellent for simple hems, decorative stitching and gathering fabric.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Researchers are putting driverless shuttles on campus next year at the University of Michigan and the rides are free for students and teachers.

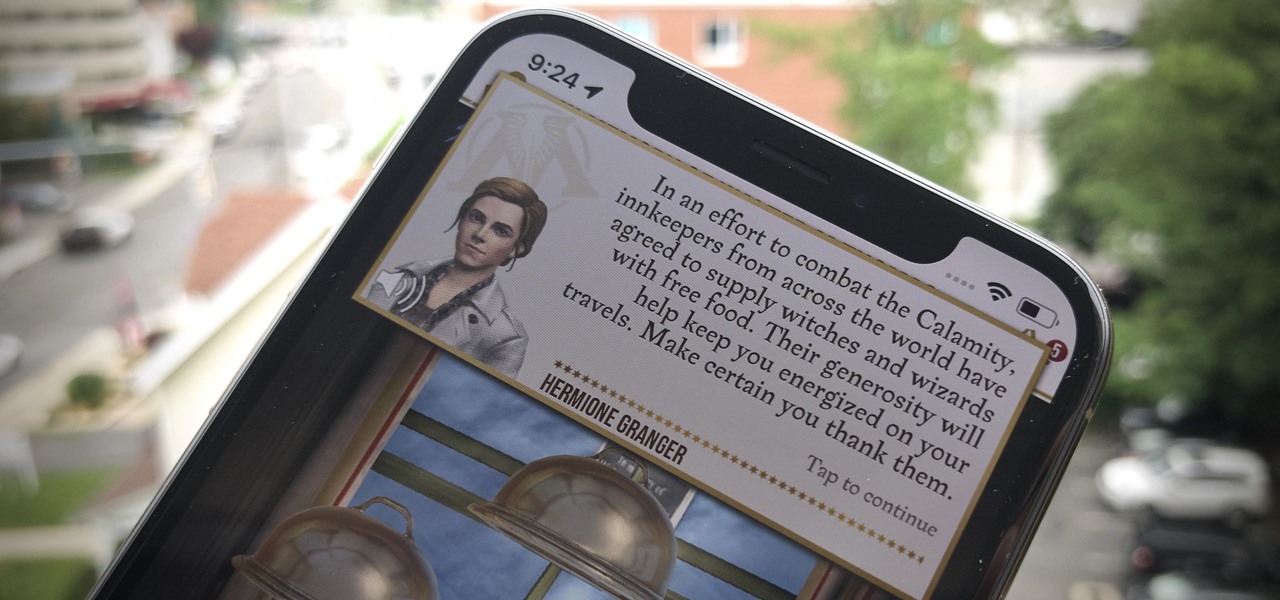
We Harry Potter fans all remember Hogwarts students pulling Mandrake Roots in the greenhouses in Chamber of Secrets. Well, in Harry Potter: Wizards Unite, we now have an opportunity to work in our own Greenhouses, as well as dine inside Inns scattered throughout the map. Let's take a look at how these two establishments help you along your magical AR journey.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Last month was a whirlwind for the augmented reality industry, with the Augmented World Expo, Apple's Worldwide Developers Conference, and an exciting Magic Leap Twitch livestream all wrapping up before the ides of June. Now that we've had a chance to fully digest it all, we have a real sense of where the augmented reality industry is heading.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

One of the big hurdles when equipping vehicles with sensors for autonomous driving is the cost. For example, the Light Detection and Ranging (LiDAR) sensors that power many versions of self-driving car technology are pricey, currently ranging from around several thousand dollars up to $85,000 per sensor—and vehicles often need multiple sensors to see enough of what is going on around them to drive safely.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

You already know that the best place to learn about the cutting edge of augmented reality is Next Reality, but the best event to meet the people and companies pushing the space forward is the annual Augmented Reality Expo (AWE), and we're giving away free tickets!

Magic Leap has been promising to launch a developer conference for years, and now the company is finally making good on that promise. On Wednesday, Magic Leap sent out the official announcement for its first L.E.A.P. conference, which will be held in Los Angeles in October.

Cable TV network Nickelodeon is looking to break new ground with a new series that will be experienced in virtual and augmented reality.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.