We're all for heaping piles of shredded cheese on our tacos, but what if all that cheese could actually be the taco shell instead? Since this was perhaps one of the more profound food questions we've had in a while, we wasted no time getting to the kitchen and tackling this cheesy challenge.

I've had a thing against bananas ever since Mario Kart; not only do I believe it's the worst weapon in the game, but it's also a very funny-looking food. Nevertheless, bananas are a great source of potassium, and I can't overlook that.

When the time comes to move home, the logistics of moving your belongings can easily become tiresome, tricky and even disastrous. However, with a little careful planning and foresight, the act of packing can be a simple process. The key to getting the most from your move is in efficiency, planning and care. Here, we take a look at the best ways to pack in order to ensure a safe and simple move.

In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.

If you shatter your new Samsung Galaxy S8 display, then be prepared to pay a hefty repair fee for that bezel-less baby.

We've been dying to see how the new LG G6 stands up to wear and tear, with its near bezel-less display and glass construction, ever since the device was announced at Mobile World Congress 2017 in Barcelona.

So you dropped your smartphone and the screen cracked. Again. Just the thought of sending it out for repair or buying a new phone is driving you mad.

No crème brûlée is worth its custard without the crackled, caramelized crust it's famous for. For this reason alone, many cooks have a brûlée torch sitting somewhere in their cabinets.

Poaching, the cooking method that gently cooks food at the barest simmer, is awesome because it keeps in moisture and flavor. The no-cook poaching method is even better, because you don't add heat to your kitchen on hot days, and you don't have to watch the pot.

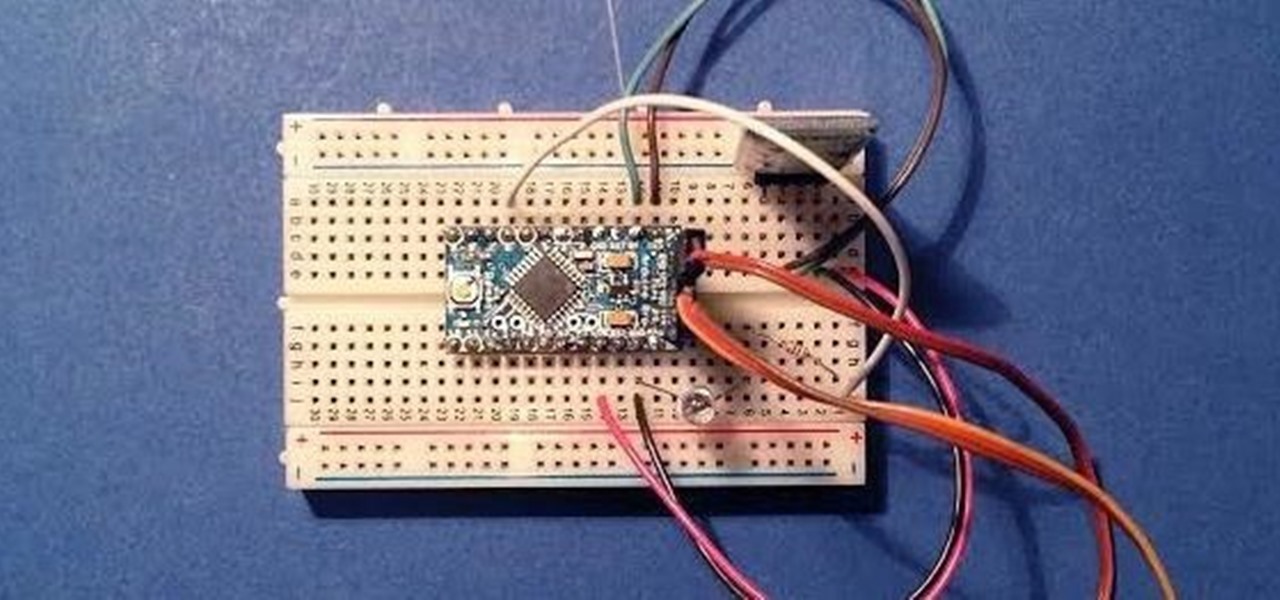
Since its creation, Arduino has been growing exponentially more popular as DIY enthusiasts and Makers alike realize its potential. As new versions of the device are released, many easy-to-use peripherals are showing up on the market also.

Ginger root is one of the most underappreciated and versatile spices around. It's simultaneously hot, sweet, and piquant. It's also a pain in the tush to peel, thanks to its thin, fragile skin and the thick, knotty rhizome that contains all the flavor.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

This is a tale about microbes, a man who became a hermit, and the parchment that carries both of their stories.

One thousand feet under the ground, extremophile microbes that have not seen the light of day for four million years are giving up some fascinating facts to scientists who go the distance.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

What happens when you find your ball deflated and there's no pump or needle in sight? You could always cancel your plans of kicking around the soccer ball or starting that pickup football game in the park. Better yet, you could be terribly clever and find another way to get air into the ball. From a pen to a balloon to a gas station, there are ways to inflate it.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Go to a chain supermarket, and chances are you'll see one type of garlic—maybe two or three if you're lucky. However, there's a mouthwatering slew of Allium sativum out there, far beyond those papery white bulbs most of us encounter at the nearest Stop 'n' Shop.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

Hard-boiled (also known as hard-cooked) eggs are notoriously easy to mess up. We've all ended up with tough, rubbery egg whites and overcooked yolks that have that unappetizing gray-green ring around the edge. An ideal hard-cooked egg has a firm yet tender white, while the yolk is creamy and well-done without being mealy.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

Your smartphone stays with you everywhere you go, so it's only a matter of time before you spill coffee all over it or drop it on the ground. For some of you, it has already happened, perhaps even multiple times. That's why we thought it was important to find out which flagship phones are the most life-proof.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

A broken screen may seem like the end of the line for your laptop, but don't worry! The screen is the most fragile and vulnerable part of a laptop, and it is not uncommon for it to break. You can replace it yourself and give your Dell Inspiron a new life.

These grass seed heads make great miniature cedar trees when painted. They are a little fragile for wargaming but great on model railroads. Watch this video miniature-making tutorial and learn how to make a mini trees out of grass heads for dioramas, models, and terrains.

If your cray fish or crawfish has tiny tiny worms crawling over the shell, watch this how-to video to fix the problem.

Easter isn't the typical occasion for pranking your friends, co-workers, or boss (if you dare). But this Easter egg-inspired prank by Redditor cheesewing is pretty ingenious, and handing out chocolate eggs any other day of the year might raise some suspicion.

The internet is something most people rely on, so when you buy a used laptop without a wireless card or yours needs to be replaced, it's easier to do it yourself. Having someone else do it can cost more than you think, so here's an easy way if you own a Dell Inspiron E1505.

There are not many stitches that are more beautiful than this LACEY EYELET RIB STITCH. And, there are few that are easier. Most knitters are apprehensive about knitting any lace patterns, and truthfully, many are difficult because of so many rows. This one, however, consists of only 4 rows. You can use either side of the work and it is a lovely stitch to know. You can use it for a beautiful scarf or for just about anything for a baby. I've made many baby sweaters and blankets using this stitc...

Heat, moisture, dirt, static, and fragile electronics are only some of the many PC dangers that can ruin your PC. Watch this video and get some great tips on how to maintain your Personal Computer Maintain your PC.

Use the abdominal thrust technique on a child with an obstructed airway. Infants are more fragile. Put the infant face down on one arm and rest your arm on your thigh. Administer 5 back blows between the infants shoulder blades. Turn infant over and administer 5 chest thrusts in the middle of the sternum. Repeat until airway is clear. Clear an obstructed airway on a child or infant.

There are many different types of countertops, but of all those available, post-form countertops are probably the quickest and easiest to install. Post-form countertops consist of a laminate surface that is glued to a particleboard base. Typically, the base is shaped so that there is a curved front edge and an integrated backsplash with either squared off or 45-degree angle ends available.

The last tree on earth The world looks new today.

Cyriak's latest animation features '50s stock footage remixed into a horror show. Our dark and twisted animator keeps churning them out, each creepier than the last. Be warned: "a journey into horribleness, not recommended for the faint-hearted or fragile-minded..." More by Cyriak:

Train your dog on how to act around babies. Make your dog understand that a baby is not a toy but a fragile thing. These steps will show you just how to do that and ensure you have a safe and happy family. Train your dog to be around a baby.