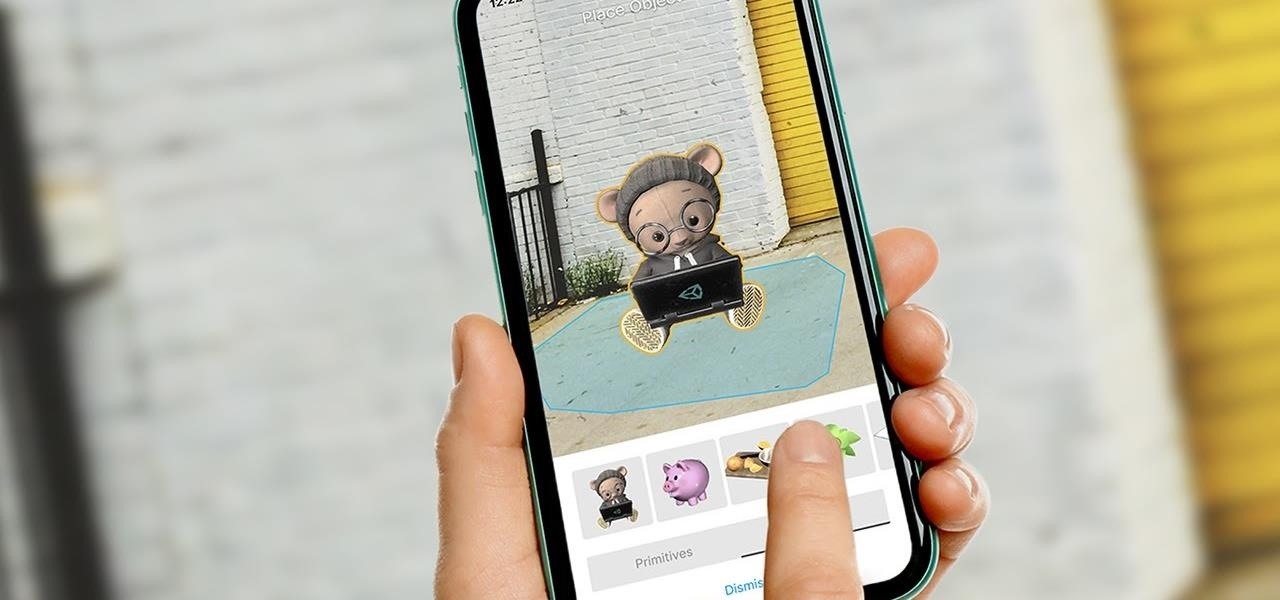
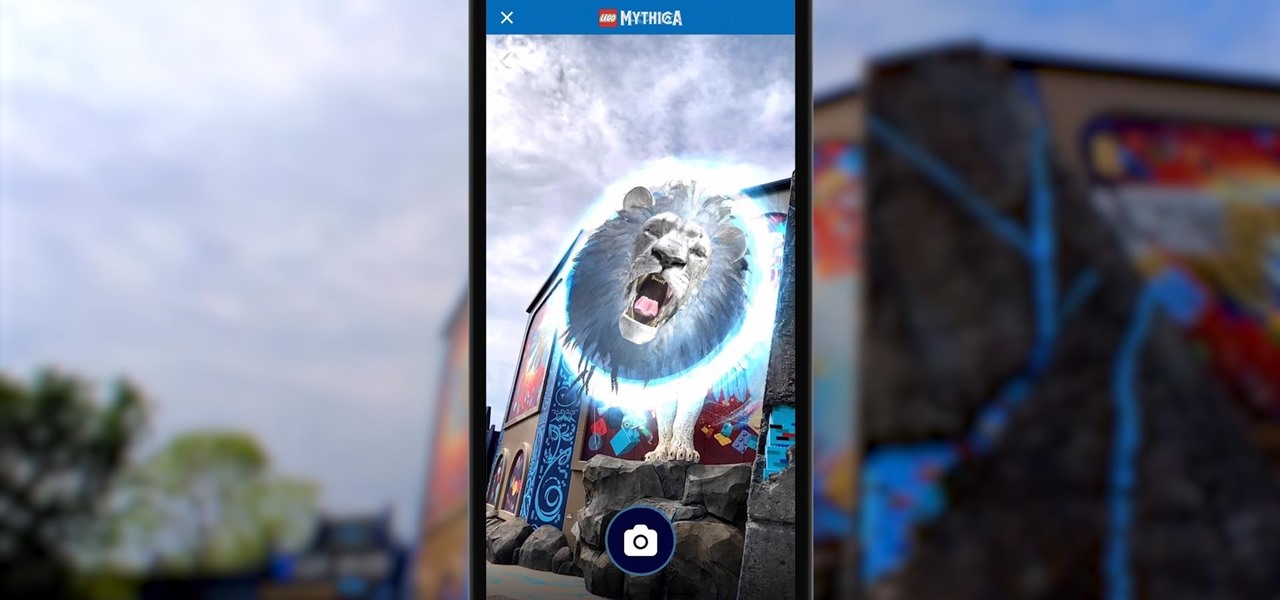
In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

Almost every bread recipe will tell you to look for a golden brown crust or to tap on the bottom of your loaf and listen for a hollow sound. That visual and sound technique will work most of the time, but it can still come up short, leaving you with a soft and gooey spot in the middle of your loaf.

Aside from its many high-end features, the camera on the LG G3 is up there with other heavy hitters like the Galaxy S5 and HTC One.

For the vast majority of people, coffee is a must-have in the morning. It provides a stimulating effect that not only wakes you up, but sets your mood and attitude for the rest of the day. Personally, I wouldn't get anything done without coffee.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

Unity often reminds us that the majority of AR apps and experiences are built with the Unity 3D engine, and now the Unity MARS service, which facilitates easy AR creation for seasoned coders and newcomers.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

Few brands have been more enthusiastic about augmented reality than Lego, which has now expanded its AR experiences from toys to theme parks.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

After the dust settled from Apple's annual iPhone event, there's not a lot to get hyped up about the iPhone 13 lineup, particularly if you upgraded your smartphone last year.

This is a video showing the drilling of live rock from a saltwater reef tank. The 1/2" holes are used for mounting pegs made from acrylic rods or other types of pegs or frag plugs. The live coral are attached to the end of the peg and can easily be positioned in the tank. This process also facilitates moving the coral to another location at a later time, they can be removed from the holes somewhat easily. It also prevents coral from falling as once its pegged well, its pretty much going to st...

Apparently it's not just the iPad that'll have the all the fun with robust apps for the tablet space. Taipei-based Cyberlink has just announced at CES that their editing software PowerDirector will be available on Windows 8 tablets: