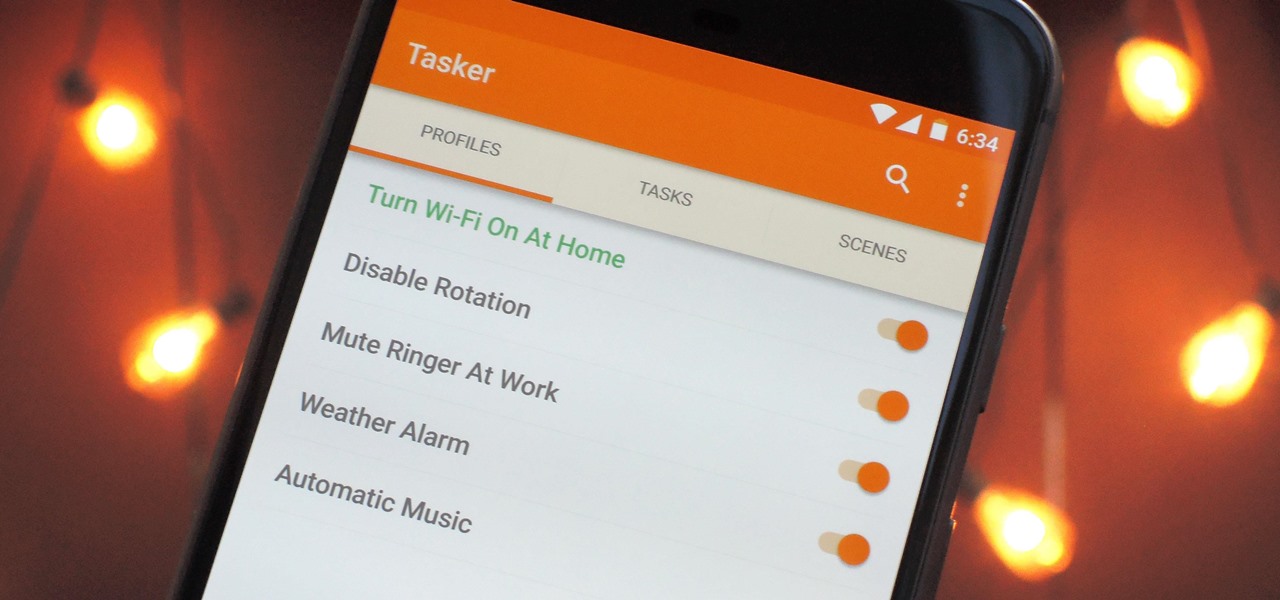
When it comes to automation apps on Android, Tasker is still the king of the hill. For a price of $2.99 on the Google Play Store, it's a great buy for any would-be tinkerer that would like to get into automating actions on their Android device. Then, when you consider that there's a free 7-day trial version available, there's almost no reason that you shouldn't at least test the waters with Tasker.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

On this platform, we talk a lot about the future of augmented reality, and we pay attention to what is being said elsewhere as well.

An attacker can create three, five, or even ten new Netcat connections to a compromised MacBook with one command. Performing complex post-exploitation attacks might otherwise be difficult from a single shell without this essential trick.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

xFL1PPYx has found a cool and fun way to your stomp your online opponents in "Saints Row 2". In this video he shows a cool and easy glitch. The glitch allows you to become hidden behind a wall where your enemies cannot go. All you need to do is hit the corner with your bike and if timed and executed properly (as shown in the video) you can attain this ability and give yourself that extra edge to win.

Improve your football game and your value to the team by memorizing and ready to execute your football playbook. Standard memorizing tools like flash cards and practice will help get you through any size playbook.

In this martial arts training course on video, learn how to do basic capoeira moves. Our expert practitioner will walk you through many beginner forms and capoeira techniques, discussing the purpose and intent of the movement and displaying how it is executed.

This is a helpful soccer video because it gives you tactics from both sides of play. Taken from a training routine from the Spanish Football Federation, the video improves your team's ability to retain possession of the ball while also breaking down offense moves in terms of what defense can do to prevent them.

"Connect via Facebook" — these words are coated on over a million websites nowadays, but Facebook Connect poses a risk of leaking personally identifiable information to those third parties. If you're not convinced Facebook Connect is safe, then turn off the flow of personal data to those websites!

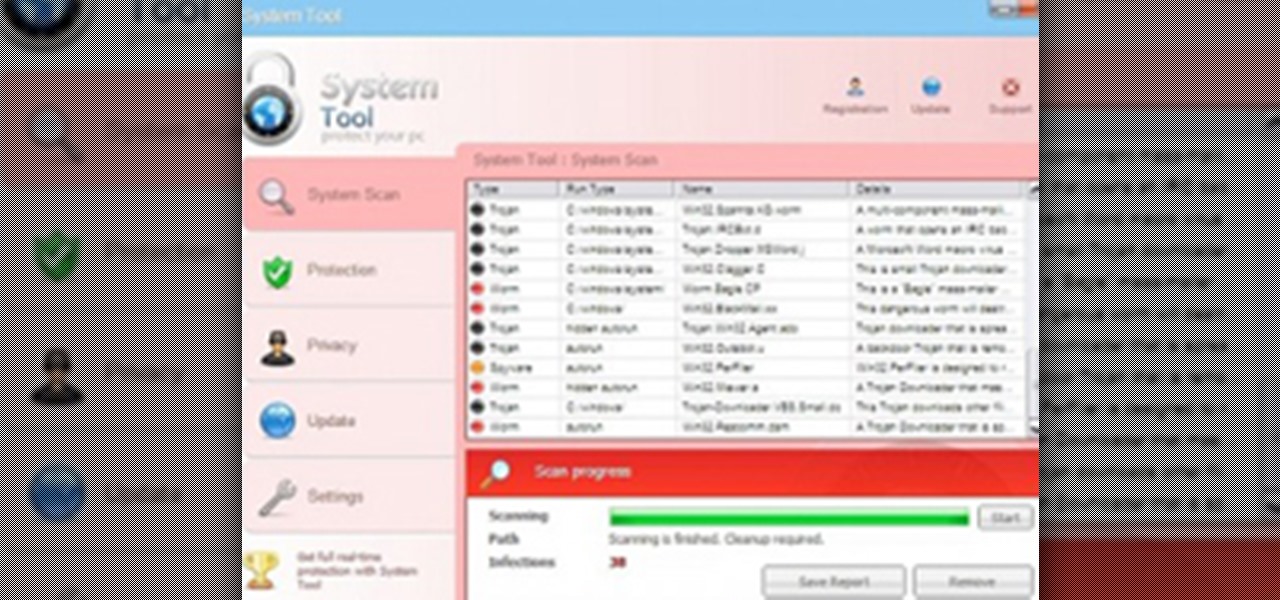
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Scrabble Bingo of the Day: DAUBERY [n] An unskillful painting or work, one that is executed in a messy or inexpert way. Since art is highly subjective, I won't point out any dauberies. You probably already have a few in mind.

Truly spectacular and one the most breathtaking DIY endeavors to grace the front page of WonderHowTo, a recreation of Pixar's UP house was launched to an altitude of 10,000 feet in a private airfield near Los Angeles this past week. The project was executed by a team of engineers, scientists and veteran balloon pilots—(meaning, please, Do Not Try This at Home).

By John Timmer, Ars Technica How much information can the world transmit, process, and store? Estimating this sort of thing can be a nightmare, but the task can provide valuable information on trends that are changing our computing and broadcast infrastructure. So a pair of researchers have taken the job upon themselves and tracked the changes in 60 different analog and digital technologies, from newsprint to cellular data, for a period of over 20 years.

Below, two different sets of schematics for mixing cocktails: the first is the "Engineer's Guide to Drinks" designed some time in the '80s; the second is a set of sleek infographics for mixing the perfect drink, from Brazilian illustrator Fabio Rex.

If you've ever had to call a large communications company with a customer service issue, you've most likely experienced the hopelessly not-at-all helpful operator from hell. Thanks to a program on VRT Belgium, you can now experience a small sense of vengeance for tortured customers everywhere.

At age 32, Tetsuya Ishida apparently threw himself in front of a speeding train. No huge surprise given his exceedingly twisted paintings. To us, he seems to possess a certain internet sensibility. Precisely executed, bizarre, and dark in theme. We dig him.

Brusspup once again blows my mind (see previously below). His latest project is an extremely well executed animation, using a grid of tea candles to represent classic video games.

Bash (Shell) Scripting for Beginners Intro

Warning Don't torrent things that you do not have the rights to torrent. Everything I torrent, I have a physical copy of, and just want a copy on my computer without causing wear-and-tear on my DVD drive's laser. Piracy is naughty.

German photographer Peter Langenhahn's process is incredibly laborious; similar to photographer Lori Nix, he can spend up to three months on a single photograph. But while Nix spends the time constructing elaborate sets, Langenhahn is anchored to the computer, editing.

Food is the meeting place of left and right brainers: Culinary arts call for creativity, but is also deeply rooted in the What, Why and How of basic science—baking powder vs. baking soda, the rising of dough, the falling of a cake, etc. Below, two plays on left brain principles—the Möbius strip and the law of gravity—both executed with right brain flair.

If you've yet to witness B.A.S.E. jumping, it's an activity for adrenaline junkies first publicized by filmmaker Carl Boenish in '78. The freefall sport employs ram-air parachutes, and is most commonly executed in locations such as the highly elevated El Capitan rock formation of Yosemite National Park (El Capitan is also technically the birthplace of the sport).

A radical art group of Russian political pranksters, who go by the name of Voina, have delivered a giant "Up Yours!" to the Russian government... in the form of a 213-foot-tall penis.

This video is very clever, if a bit Rube Goldberg. It is the kind of thing that would be entirely charming if executed by an 8 year old boy.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.