Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

The Oscars are just a couple of days away when Hollywood will celebrate the best crop of films from 2019 in the US and internationally.

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

The latest augmented reality feature from The New York Times gives readers a close-up view of the damage left behind by the eruption of Volcán de Fuego in Guatemala earlier this month.

Samsung kicked off their Android Oreo rollout earlier this week. The update already improved the lock screen significantly with new wallpaper color-matching for the clock. With the newest update, we also get the ability to tweak the transparency of lock screen notifications.

If you're a Doctor Who fan, you've likely always hoped to see that iconic blue box appear on your doorstep with the Doctor asking you to come on an adventure. With the 13th Doctor just announced, this seems like the perfect time to tell you that thanks to Apple's ARKit, exploring the TARDIS is now possible!

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

You already know that 3D-printing technology is swiftly evolving—it's been used to print balloon animals, bikinis, and house keys, and there's even an affordable home version of the printer, as well as one you can 3D print.

The video featured in this article demonstrates the function and design of a powerful form of air cannon that operates using a purpose made valve that opens very rapidly. This allows for a massive amount of pressurized air to be released at once to throw a projectile many hundreds of yards. The design of the cannon also allows the barrel and the air chamber to occupy the same space, and so it is very compact and manageable which makes for an enjoyable shooting experience.

It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

What do you do when your favorite new car is still two years away from hitting the road? Look to augmented reality, of course.

Augmented reality as a storytelling medium can do some extraordinary things words and images alone can't convey -- such as transporting readers 400 years into the past.

To build hype for the HoloLens 2 among developers, Microsoft is borrowing a page out of Magic Leap's playbook.

Magic Leap One owners, start your virtual engines, as automotive virtual reality developer RelayCars has published an app to Magic Leap World that lets users customize and test drive a 2019 Kia Stinger.

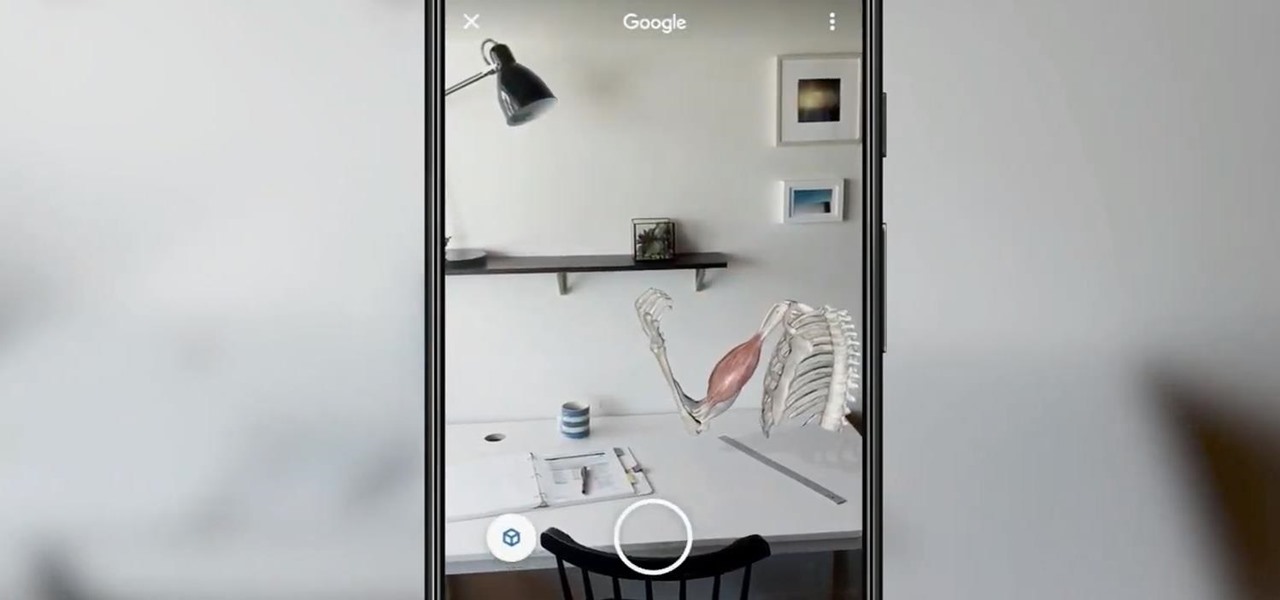
Unsurprisingly, Google wants to be the caretaker for augmented reality on the web, and its latest move in this endeavor is a 3D model viewer prototype called Article that's designed to work across all web browsers.

After hosting millions of free 3D models online, Sketchfab is betting that augmented reality and virtual reality developers and creators will be willing to pay for premium 3D content.

It's fitting that students at the University of Washington can catch a glimpse of the new, 135,000 square-foot computer science building in augmented reality before construction is completed.

According to Dr. Lindsey Fitzharris of The Chirurgeon's Apprentice, hospitals during the first half of the nineteenth century were known as "Houses of Death."

The Washington Post believes augmented reality adds an extra layer to stories, and they're doubling down on that belief by adding in new AR features into their already popular "rainbow" news (iOS and Android) and Classic (iOS and Android) news apps.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.

Brought to you by Tomcat. Falling snow, warm fireplace, delicious hot cocoa, quiet reading time, mouse. Quick quiz - which one is not like the other? Nothing can ruin a perfectly cozy afternoon in your home like a pest on the loose. With dropping temperatures, you may have some unwelcome residents, like mice, looking for shelter from the cold.

Apple has acknowledged a problem with the sleep/wake key, better known as the power button, on a certain number of iPhone 5's manufactured through March 2013. As a result, the company has announced the iPhone 5 Sleep/Wake Button Replacement Program, which will replace the power button mechanism, free of charge, for certain iPhone 5 models.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

It might sound odd to call interior decorating exciting, especially if you're not a professional within that industry. But that's exactly what it is when combined with augmented reality.

If Google hasn't already demonstrated that it is serious about augmented reality, then it made it abundantly clear at the Google I/O keynote on Tuesday.

Microsoft is adding another important piece to its growing immersive computing arsenal by putting its newest Mixed Reality Capture Studio in the center of the movie business: Hollywood.

Luxury automaker Mercedes-Benz has joined the growing list of automakers adopting augmented reality to provide an assist to its manufacturing operations, in this case, via the Microsoft HoloLens.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

According to Indiana Jones, certain things belong in museums, but, thanks to augmented reality, you can now see some of the ancient treasures of the world in your own home via the Civilisations AR app from the BBC.

To the best of my recollection, Fruit Ninja was one of the first touchscreen games that appeared to really take advantage of the new paradigm of user input, turning the player's finger into a produce-slicing katana.

One inventor wants to bring augmented reality to internet radio and home audio speakers. Meanwhile, a leading consumer electronics company has opened up access its deep learning tools for building augmented reality apps. In addition, analysts examine how augmented reality will impact the design and construction and profile the top developers in augmented and virtual reality.

How can bacteria that lives in the throat of 10%–35% of people—without causing an infection—cause life-threatening meningitis and sepsis in others?