In this tutorial, we learn how to draw a scary demon mother. Start off by drawing a circle for the face with huge sharp long teeth and small evil eyes. Add in details around the face to create a more realistic feel and creases in the eyes. Next, draw in the hair by using your pencil and just drawing in straight and straggly hair. After this, add in additional details to the eyes and the rest of the face, creating a nose and other features you want. After this, draw in lines on the bottom of t...

Are you a true "True Blood" fan? Then you probably recognize this evil vixen makeup look as that of Lorena, AKA Bill's maker, from the hit HBO series.

Prep for your dream career in tattoo artistry by watching this easy video which shows you how to draw a skull tattoo. Broken down into four parts, you'll keep equal concentration on the skull's head spikes, evil cranial contortion, unexpected eyes, and severe undereye circles.

Picking up dog poop is not one of life's great joys. It is, however, a necessary evil to owning an adorable dog, or having a lawn that someone else's adorable dog may want to use as a toilet. When it comes to this unpleasant task, the shop vac is actually a very good way to pick up dog poo. You want to make sure, however, that you're not using your shop vac for anything but this one task. It can easily vacuum in small objects with weight in them and, better yet, you never have to touch it!
The javelin glitch in Modern Warfare 2 is currently being exploited for great and evil purposes. Watch this video to learn how to take advantage of this glitch, for both the XBox 360 and the PS3. Fair warning, though: doing this glitch could get you banned by the powers that be at XBox Live.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

Johnny Blaze has a really cool curse. Whenever he's in the presence of evil, he transforms into a leather clad demon with a burning skull for a face riding on top of a demonic motorcycle with fireballs for wheels. Now that the video game is out, you can take control of Ghost Rider and fight Mephisto's son Blackheart from taking over the unsuspecting human world. Take a look at this instructional video and how to obtain the final soul element before you take on the final dark lord himself in t...

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

So, you're addicted to that award-winning, science-fiction, first-person shooter, computer game Crysis, are ya? Well, then you probably know a bit about the Sandbox 2 level editor then, don't ya?

Is it the midnight hour before Halloween and it's just dawned on you that you don't have a costume yet? Skip the store because you'll probably have to choose between the lesser of two evils (will it be chicken suit or beer wench?).

If you forgot about April Fool's Day, you're going to have to get creative if you want to pull off some not-so-predictable pranks last minute. To help you with that, in this video you'll learn how to set up and execute 5 of the best last-minute April Fool's Day pranks. April 1st will still be a fun day for you, your friends, and family... just watch!

This is just another crazy prank you can pull in the work place or at home to make time go by faster and have a little fun in the process.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

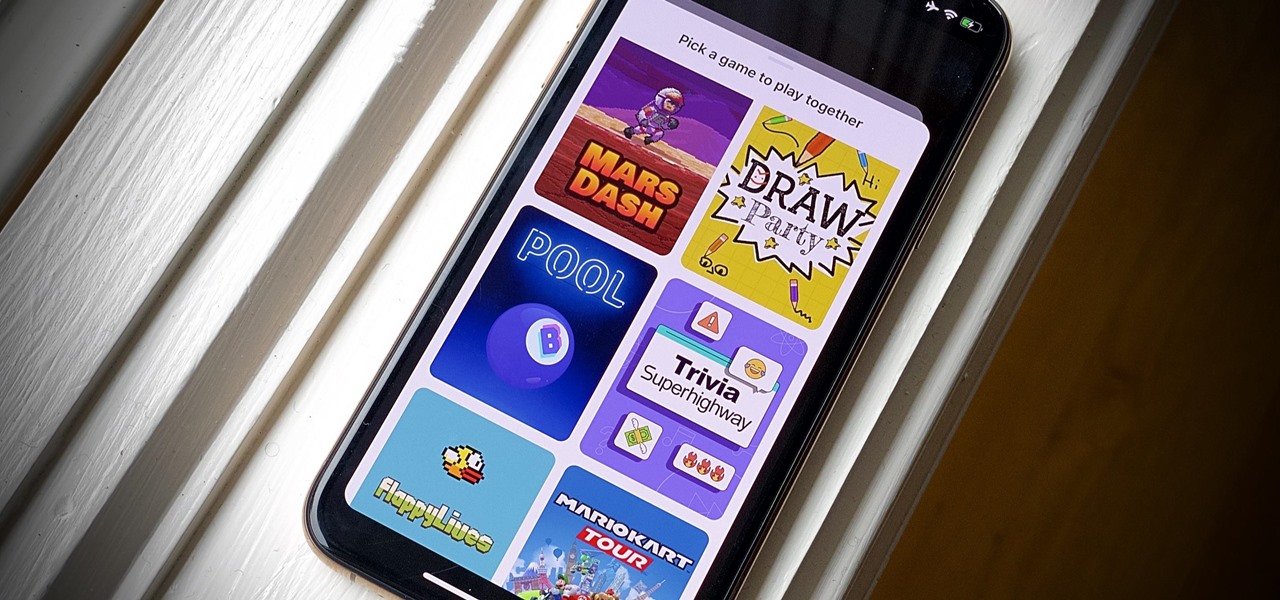
Even for those of us who enjoy spending time alone at home, at a certain point, it just gets boring. We all need social interaction, but with stay-at-home orders, that can be hard to come by. If you're feeling the itch to hang out with friends and have a good time, you should know there are plenty of free multiplayer games for iPhone and Android that will let you do just that — remotely.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Dr. Frank-N-Furter, the mad doctor played by equally strange Tim Curry, has one hell of a makeup look. Extremely darkened brows, matte black shadow extended out in an evil upturned cat eye, and two stripes of black shadow extended down the sides of the nose made his face look almost cartoonish.

Easttexas937 shows viewers how to properly use a Ouija board to get the best experience. First you will need a Ouija board and a pointer. If you want to make these two things, you should use lightweight glass and make sure you make the board properly. You have to have an open mind and good intentions when you go in to use the board. There also must be no secrets between the friends playing and you should not have a friend that is not trustworthy. This will keep evil spirits out. Always have m...

1. Shallow Bow You bump into someone in passing

Watch as Novastar and Gundamaniac demonstrate detailed wiring for a crystal focus board for Star Wars Lightsabers! Making your very own Jedi Light Saber may be a daunting task if you don't know what you're doing, but this four-part video tutorial will save the day from evil forces. To start off wiring the CF board, make sure you have your SanDisk on it already.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Thanks to "Mean Girls," we now know that Halloween is the only time you can dress like a slut and get away with it. Which means that if your concept of a witch costume still includes a crooked nose, warts, and a green face, then you're living way in the past, honey. Blast forward to the future—and the sexier side of things—by dressing up as a sexy witch this Halloween.

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.

Draw cartoons with realistic facial expressions to bring characters to life, capturing happy, sad, angry, evil and surprised looks. Learn to draw cartoon facial expressions from an artist in this free cartooning video series.

In this video series, watch as professional makeup artist Matt Cail teaches how to do scary clown makeup for Halloween. In this step by step makeup lesson learn how to apply the base paint, how to add triangles and fake blood, and really turn clowns into an evil thing. Take a walk down horror lane and pay tribute to IT and John Wayne Gacy Jr. thanks to the help of the experts at ExpertVillage.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

In this tutorial the author shows how to find out a Cool XP Easter Egg hidden in the XP which comes by downloading the latest update of widows update. The author now opens Internet Explorer and visits the windows site. Now he quits the explorer and holds down both the Control key and alt key and right clicks on the desktop seven times. Now keeping the control key pressed, he releases the alt key and right clicks the desktop and chooses the option 'Create ShortCut'. Now he releases all the key...

Tech companies are embroiled in controversy this week. No, not the hearings on Russian interference in last year's election; in this case, it's all about the burger emoji.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.

Augmented reality dogs have been a big hit with developers using Apple's ARKit. RoVR hit YouTube a few days ago and people have been clamoring for it ever since. Not to mention the Good Dogs Game created by the people behind the famous We Rate Dogs Twitter.

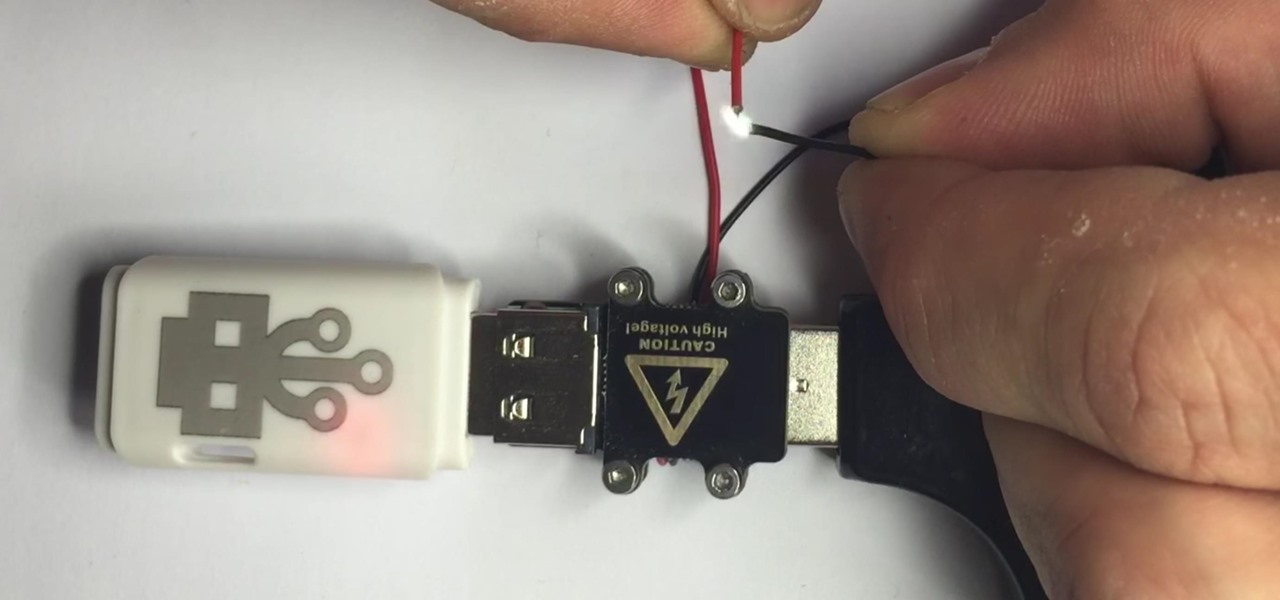
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Facebook announced at its F8 Developer's Conference on April 12th that, in addition to the VR-ready Oculus Rift we have today, it plans to bring Augmented Reality (AR) into the fold of their social machine.

Since it was released last fall, Super Mario Maker has offered us a glimpse into the minds of some of the most evil people on the planet. The game, for Nintendo Wii U, lets players create their own Super Mario levels using a deep list of objects, enemies, and green pipes, which can then be uploaded for anyone to play.

Guardians of the Galaxy wowed moviegoers this summer with its sassy, strong team of intergalactic superheroes. From Groot, the ever-growing tree, to Rocket, the rough-around-the-edges raccoon, the film had an unending supply of unique characters—but no one stood out as much as Gamora.

Throughout history, almost every superstition dealing with evil has had something to do with left hands. In the seventeenth century, it was thought that the Devil himself baptised his followers using his left hand. Today, studies show that left-handed people are more likely to be schizophrenic, alcoholic, delinquent, dyslexic, have Crohn's disease and ulcerative colitis, and a slew of other medical problems. To top it all off, left-handed people have an average lifespan that is 9 years shorte...

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

If you ask me, one of the best things about winter weather is drinking warm beverages to beat the cold. Coffee is my favorite, but hot chocolate is a close second. Whether it's the just-add-water mix from a pack or a spicy homemade Mexican variety, there's something comforting about sipping on warm, liquid chocolate. Looks delicious, doesn't it?

If the number of apps designed to make getting out of bed easier tells us one thing, it's that people hate waking up. Whether it's because you're dreading going to work or school, or just stayed out a little too late the night before, it's almost never fun.