In this two-part tutorial, learn how to make a homemade, preservative-free refresher spray to set your makeup after application. Hosted by Koren of EnKoreMakeup, part one shows us what goes into making the mixture: Distilled water, glycerine, a tea bag, cucumber, rose water, and essential oils: tea tree, rose, rosemary, sage, lavender, & lemon oil. (Oils can be found at Coastal Scents.) In part two, Koren shows us how to combine these ingredients to make the refreshing, makeup setting spray.

In this video tutorial, "Miki Falls" manga artist Mark Crilley shows us how to draw a realistic eye. For any artist who aspires to draw realistically, it's essential to get eyes right. The eyes, after all, are the "window to the soul," and if something's off with a drawing of an eye, we will always notice.
I go over the basics of the new bone tool in Adobe Flash CS4. Learn how to animate quickly with this essential character animation tool.

You're stranded in Korea, lost your tour group, and you need some money. You stop by an ATM, but, uh no! It's written all in Korean! What to do! Well, we have the lesson just for you. As you learn Korean with us, learn some essential vocabulary words that may just save you when you need it the most! In this free Korean language tutorial video, we'll be taking a look at a Korean ATM and make sure you know all the essential vocabulary. So check out this instructional Korean language video to le...

Watch this instructional poi video tutorial to leran how to spin the Low Same-Direction Reels trick. This video is for beginners who have conquered basic spinning techniques.

Watch this cinematography tutorial on how to use the microShouldermount, which can be attached onto a tripod or used in its typical configuration as a shoulder mount. You can attach a monitor along the grip rod. Learn the essentials of the Redrock mounting systems for professional digital video cameras. Interesting tutorial for professional cameramen & digital filmmakers.

Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

Ever wanted to learn how to pick a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... lock picking. Just watch this video tutorial to see how to pick a Brink's high security lock.

Have you ever been the victim of theft? It sucks. Why would these lazy scumbags rather steal from us than work hard like everybody else?

Video tutorial showing how to make your own solar-powered wireless security camera using an off-the-shelf solar panel and any wireless webcam. See creator site for more detailed graphics.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

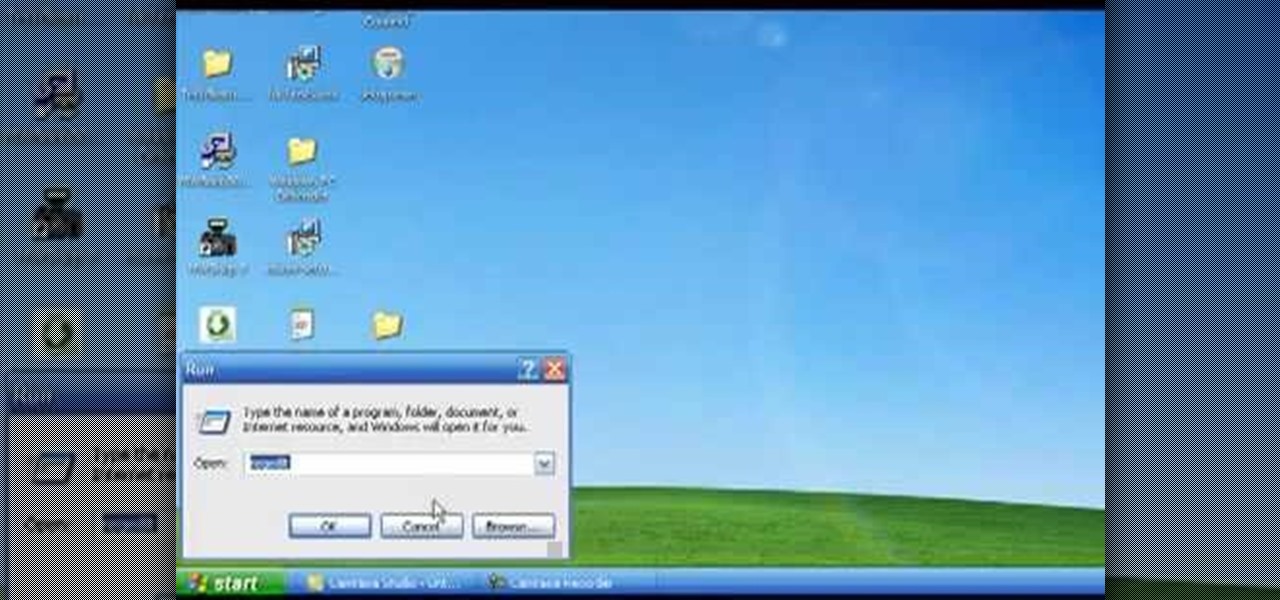
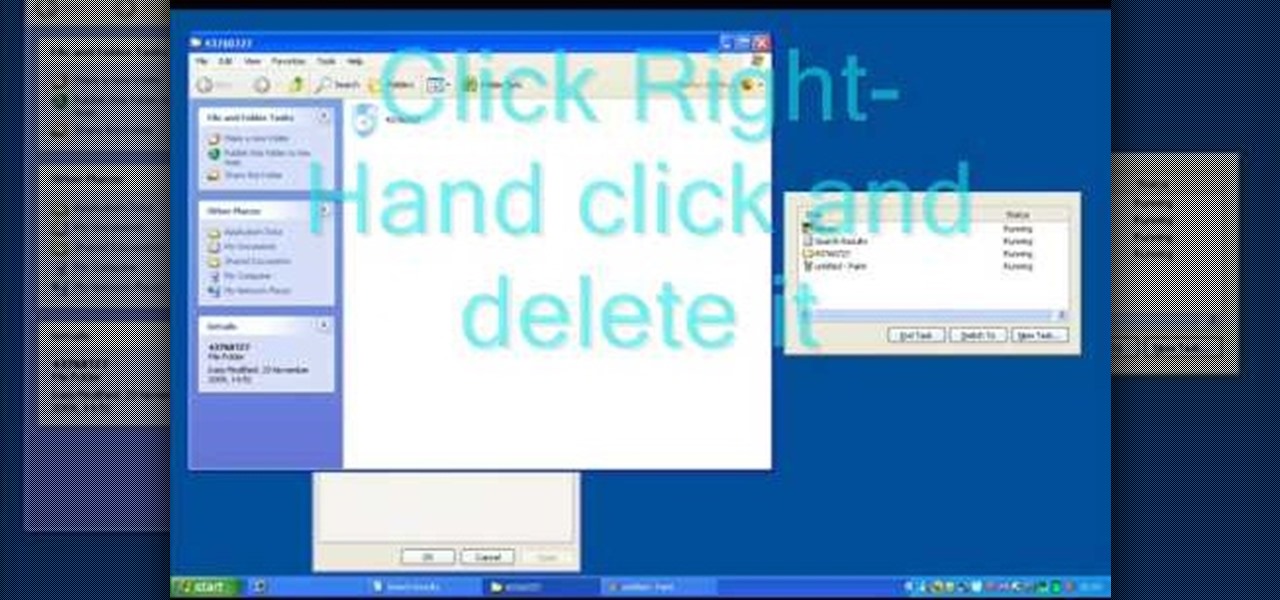
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...

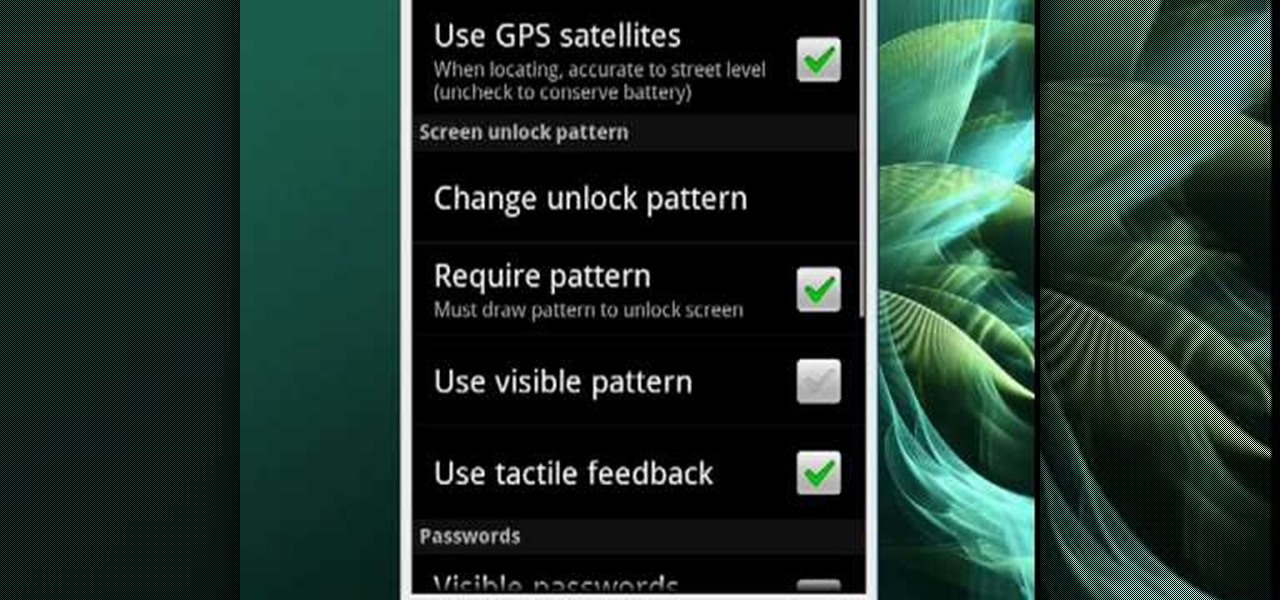
In this video tutorial, viewers learn how to change the lock pattern on an Android phone. The lock pattern allows minimum security on the phone to prevent other people from tampering with your mobile files. Begin by going into the Settings and click on Location & security. Under Screen unlock pattern, select Change unlock pattern. In order to change the unlock pattern, users will have to type in the current unlock pattern. Now type in the new unlock pattern and press Continue. Then retype the...

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Watch this video tutorial, and learn how to turn an ordinary inexpensive webcam into a hidden home security system, viewable anywhere in the world from your cell phone! With a cute and cuddly teddy bear and a cheap webcam, you can make the perfect homemade security camera, or just a camera to spy on your sister and her friends during sleepovers. Follow along with the steps in this how-to video and learn how to set up this spy system. Note: this video is NOT recommended for people who are perv...

By DevonLocks.Com - Security pins can be a pain. This video shows you how to bypass them. See our other video on how to spot them.

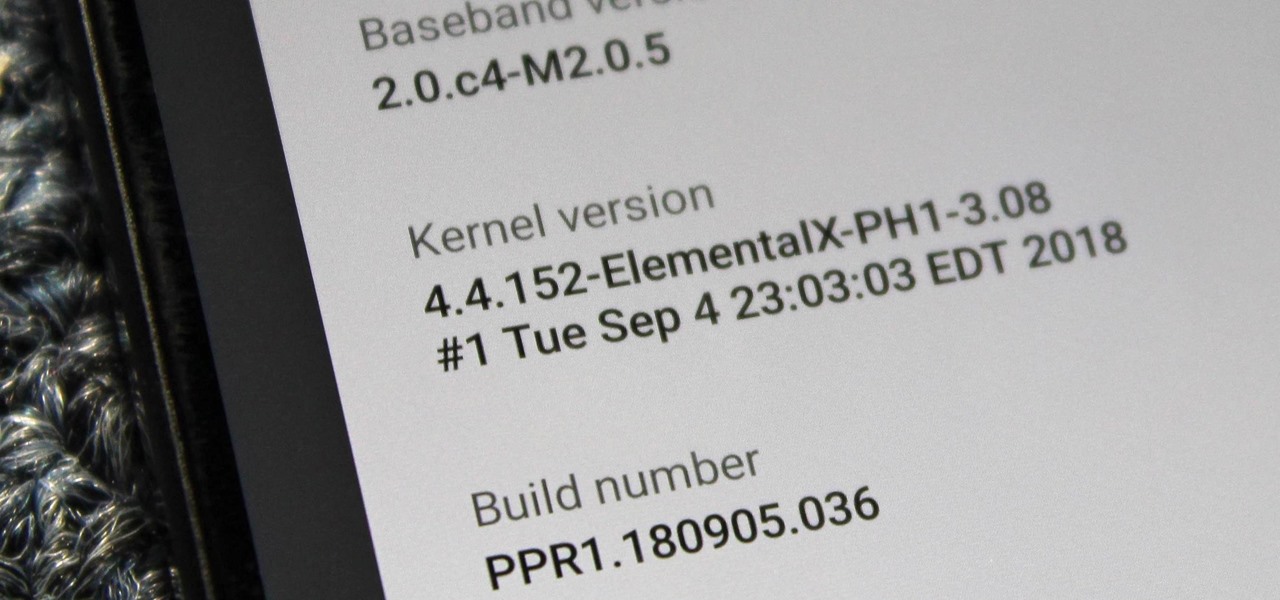
When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Rather than reaching for aspirin the next time a headache strikes, try grabbing a drink of lemonade instead. Not only can it help ease your head pain, but it can also help relieve stress, anxiety, and depression. But not just any old lemonade will do the trick—reach for the lavender lemonade.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

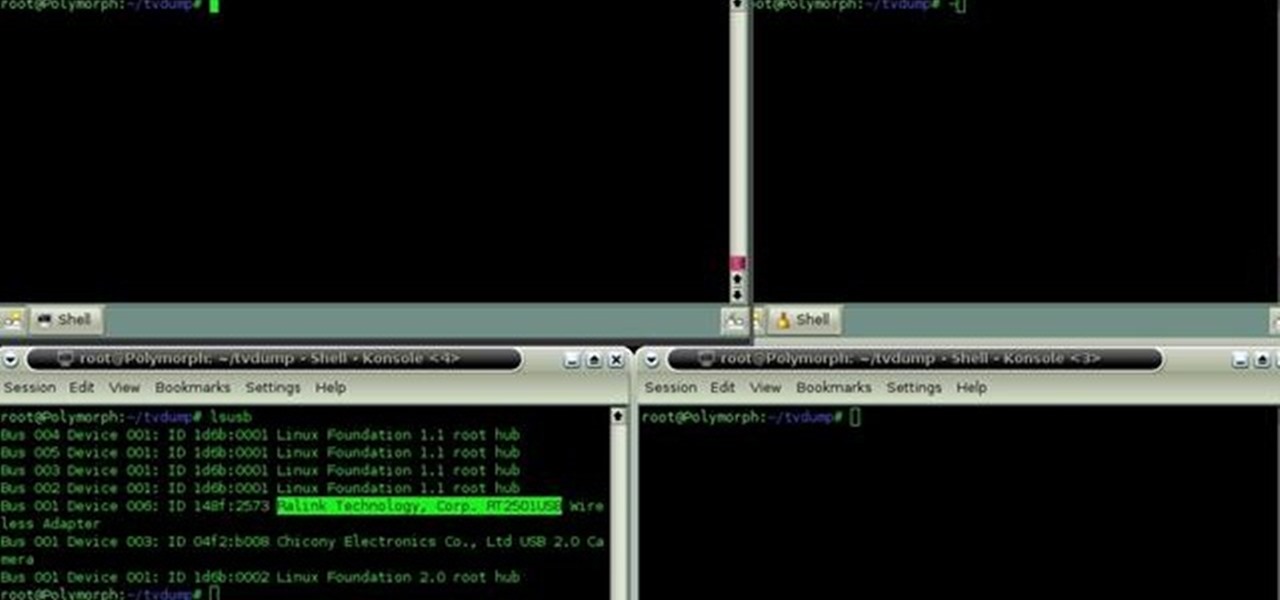
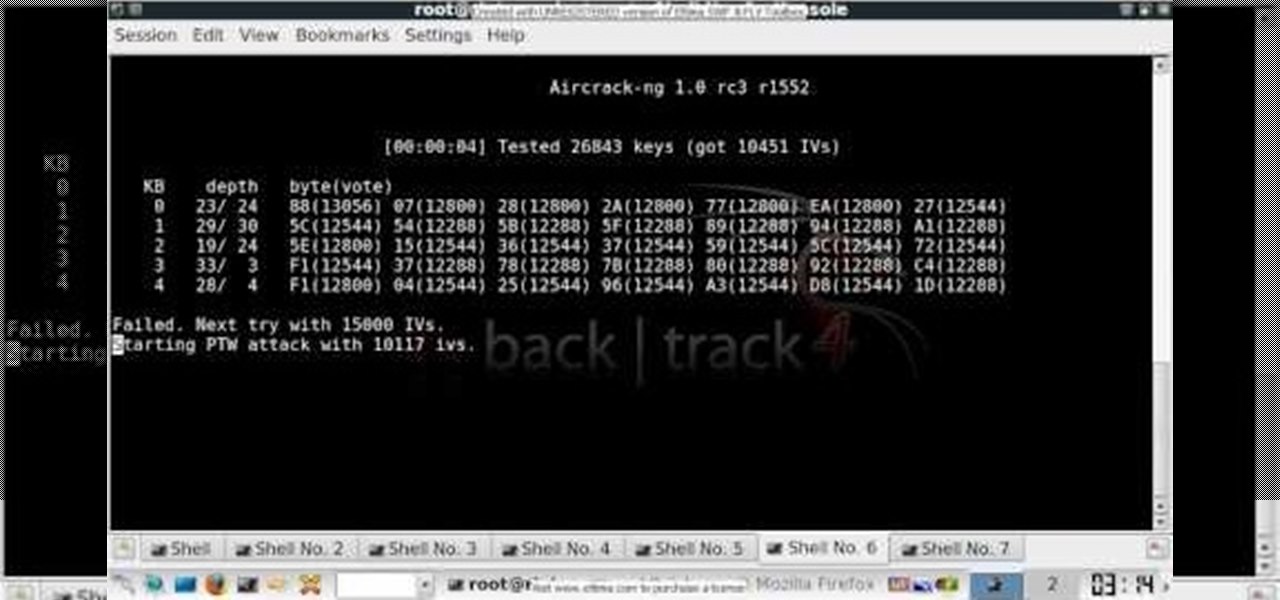
In this clip, you'll learn how to use the BackTrack Linux distro and the Aircrack-ng WiFi security app to hack a WEP network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack 3 Linux distro and Aircrack-ng WiFi security app to crack the password to a WEP-protected wireless network. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

Wish there were a way to turn your webcam into a bonafide security camera? Well, there is! And it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over two minutes. For more information, including step-by-step instructions, take a look.

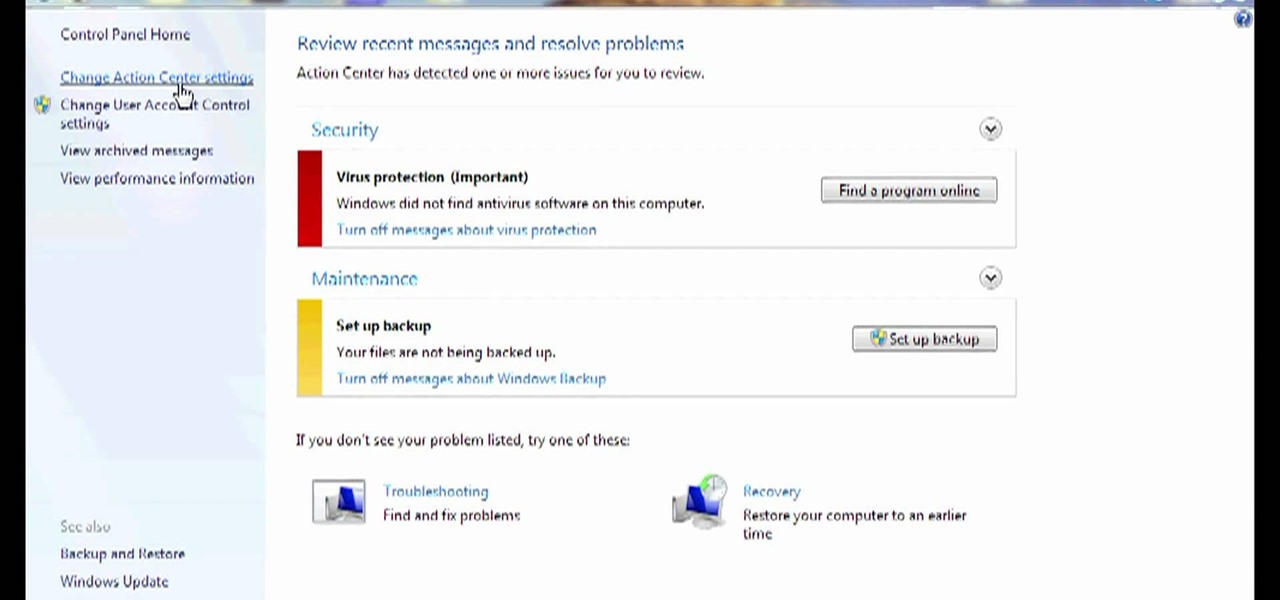
Need some help figuring out how to disable potentially annoying popup security notifications in Microsoft Windows 7? This video tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

In this Microsoft Windows 7 users guide, you'll learn how to take advantage of the operating system's new Applocker security feature. It's easy! So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about a minute and a half. For more information, including complete, step-by-step instructions, take a look.

In this how-to video you'll learn all the tricks and tips to getting yourself through airport security quickly and easily, even if you have electronic gadgets. Some companies produce travel gear that the TSA will let pass through without having to remove your laptop or electronics. Timesaver! Watch this video and you'll soon be cruising through the "Expert Traveller" line.

It seems that almost every multiplayer map in Gears of War 2 has a secret glitch-based way of getting underneath it. This video is a tutorial on how to do just one of these glitches. It will show you how to get under the Security multiplayer map using a barrier breaker glitch.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

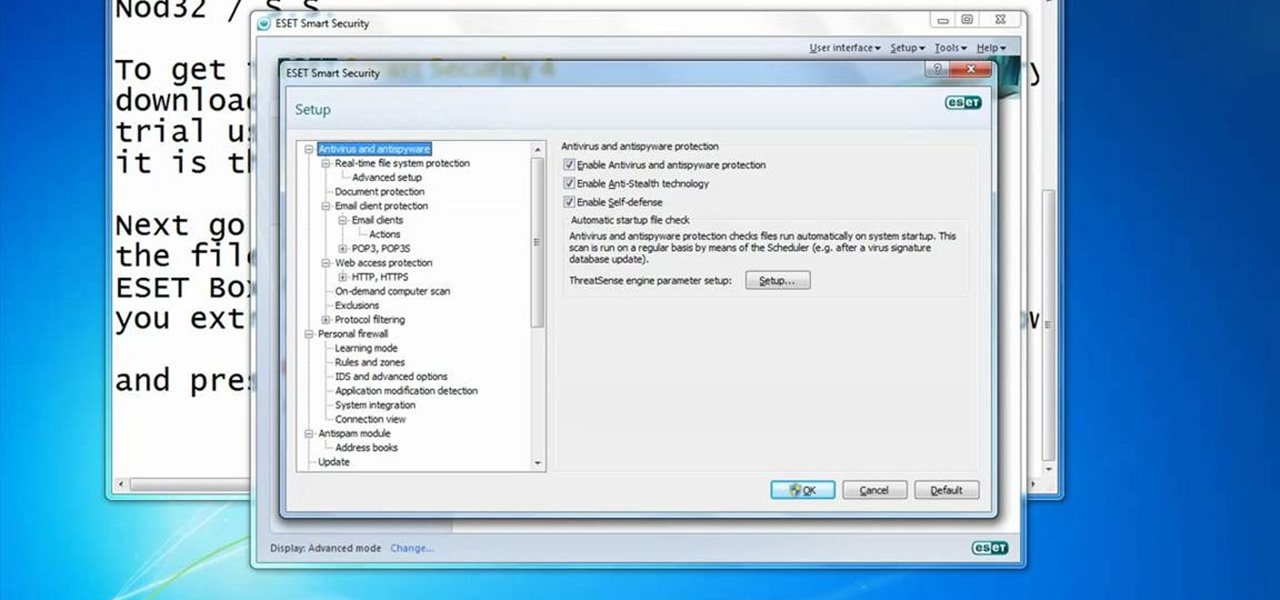
In this video you will learn how to Get ESET Nod32 or Smart Security forever. First make sure you have the trial for ESET Nod32or Smart Security. To do this go into the description of the video, download that file and put in the trial username and password. The downloaded file its called ESET Box4Ever.Before you extract the file open your ESET window and press F5.Uncheck self defense and restart computer. After you restarted the computer extract the files from ESET Box4Ever and run the file, ...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

Got a mystery to solve? Somebody’s been making off with your stuff, and you don’t have a clue who it is, do you? Here’s your chance to catch them in the act. In this how to video you will learn to make a DIY laser security system.

Learn how you can protect your home in a pretty radical and fun way by transforming two cheap household items into a stealth hi-tech, anti-burglar, security system! Literally to hot for any bad guy to handle!

In this video you will see how to access network security cameras through google search engine easily!