While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

Apparently, we learned nothing from Jurassic Park, as scientists are still working on bringing extinct species back to life. Until that day comes, you can interact with long-lost animals through augmented reality...if you have a newer model iPhone.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

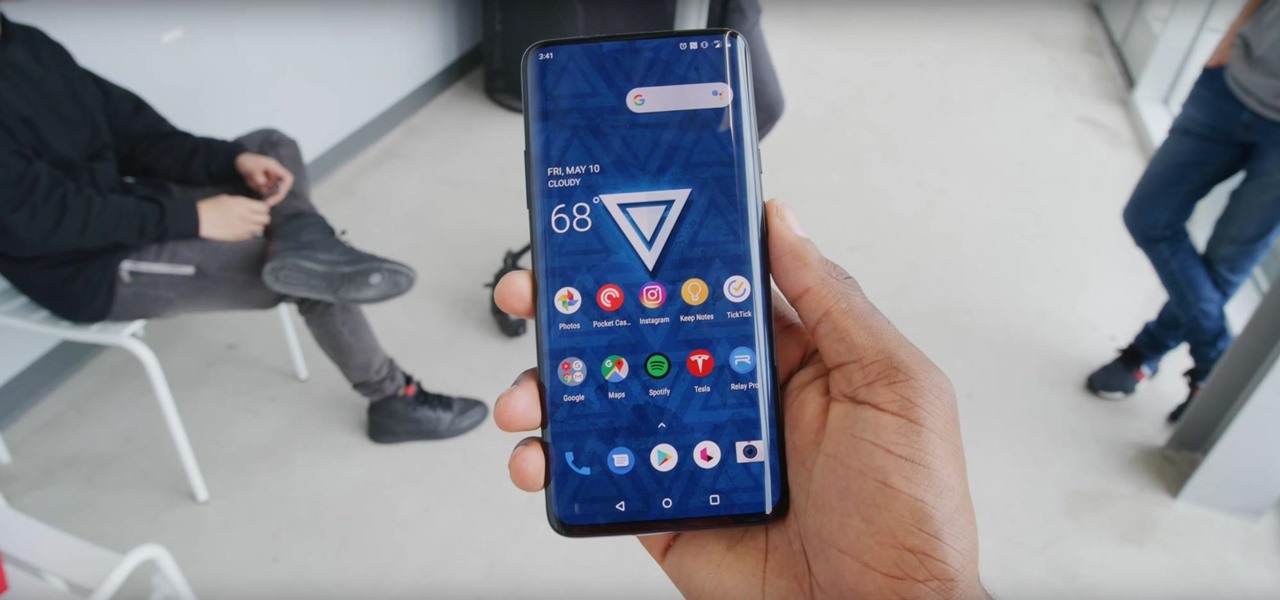
The OnePlus 7 Pro is definitely a beast on paper. With a specs page that ticks virtually every box and a price point that undercuts the competition by hundreds of dollars, it's hard to overlook this phone. But before you get too excited, know that OnePlus has repeatedly shown to be misleading with their official specs.

The emergence of Facebook's collaboration with Ray-Ban to launch Stories smartglasses has finally put an exclamation point on a new category of smartglasses: the pre-augmented reality wearable segment.

Facebook's annual earnings call on Wednesday didn't come with any big surprises, that is, if you took everything at face value.

We often discuss the augmented reality efforts coming from the biggest players in Silicon Valley like Google, Facebook, Apple, and others, but one name that keeps coming up when you really begin to dig into the AR space is Vuzix. Since the late '90s, the company has quietly but deliberately worked to build itself into a viable competitor in the enterprise space via its wearable display technology.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Presentation matters. Make sure you have the best shot of getting your artwork out there by putting together a pleasing and professional artist portfolio. Include your best work and make everything look finished and neat.

Today, sailing is usually done for leisure or pleasure rather than traveling or moving cargo. While shipping is still the most viable way of moving goods overseas, with the advent of the airplane, sailing has transformed from a necessity to a sport. Some people put their sailing skills to the test in sailboat races; some just find it exciting to be riding the ocean waves on a non-motored vehicle, using techniques which sailors have employed for thousands of years.

Adopting a style that favours the body's stronger muscles is important when climbing. On steep rock, the most effective way to increase your performance may well be to change the way you climb.

What's the easiest way to adjoin two fishing lines? The blood knot. And no, you're not going to cut yourself, that's not why it's called the "blood" knot. It's also referred to as the Barrel knot, and is usually used for monofilament nylon lines. Wade Bourne of MyOutdoorTV will show you how to tie the blood knot.

Self-storage may not be a new industry, but it is one that is rapidly reshaping its operations to suit a progressively more modernized customer base. In order to stay competitive with your self-storage facility, you'll need to keep an open mind, embrace current marketing trends, and most importantly, have a well-defined set of marketing goals. Your main focus should revolve around the following points:

Drawing cars is one of the most fun and practical things that a 3D artist can spend their time on and get employed doing. This video is a walkthrough for making a 3D model of a rim and tire of a car. It should be good practice for getting you ready to start designing your own cars on the computer. Make a 3D model of a rim and tire.

Business owners and marketeers are diverting from traditional marketing techniques, including billboards, radio and TV advertising, brochures, and any other outdoor promotions, to cheaper but effective Internet marketing strategies. Under the new arrangement, business owners reach out to the final consumers through advertising on the World Wide Web.

LiveOps is a web-based company that employs work-at-home employees to work as call operators. It is a top-notch call center that offers employees to take a range of different approaches to what they will be doing their time at LiveOps.

Need some advice on fly fishing? Fly fishing is a distinct and ancient angling method of fishing, most notably as a method of catching trout or salmon. Fly fishing is also well employed today for a large variety of species other than trout and salmon, including pike, bass, panfish, grayling, carp, redfish, snook, tarpon, bonefish, and striped bass.

Need some advice on fly fishing? Fly fishing is a distinct and ancient angling method of fishing, most notably as a method of catching trout or salmon. Fly fishing is also well employed today for a large variety of species other than trout and salmon, including pike, bass, panfish, grayling, carp, redfish, snook, tarpon, bonefish, and striped bass.

Art Babble is a video network for artists and art lovers alike, launched by a group of curators at the Indianapolis Museum of Art. The site is divided into channels, series and partners, with a wide variety of top notch videos from institutions far and wide. The Getty Museum has posted some especially fascinating content, most notably their series on modern artisans and craftsmen demonstrating antiquated art techniques.

German photographer Peter Langenhahn's process is incredibly laborious; similar to photographer Lori Nix, he can spend up to three months on a single photograph. But while Nix spends the time constructing elaborate sets, Langenhahn is anchored to the computer, editing.

Can you really make an explosive from salt, sugar and weed killer? Does glycerol and water actually recover text from burnt paper? Is it possible to develop film with a first aid kit and some orange juice? MacGyver says yes.

Area 51 is the most secretive military base in the United States, a base that U.S. government officials to this day still barely acknowledge because of its top secret development and testing of experimental aircraft and weapons systems. But a slew of Cold War-era documents have finally been declassified, and National Geographic has discovered a rather low-tech method the military used to hide its high-tech prototypes.

As Popsci says, these DIY snow vehicles show winter who's boss. The Snow Chopper

35-year-old artist from Shandong, China, Liu Bolin, has created a series of photographs entitled "Camouflage". No trick photography employed, no photoshop alterations. Every effect was created by anal, fastidious painting and the exact alignment of subject to background.

Time to prepare for that upcoming insufferable summer heat. For real. This tutorial actually works.