
How To: Count from 60 to 70 in French
Watch to learn how to say the numbers from sixty to seventy in French. soixante - sixty


Watch to learn how to say the numbers from sixty to seventy in French. soixante - sixty

Watch to learn how to say the numbers from fifty to sixty in French. cinquante - fifty

Watch to learn how to say the numbers from forty to fifty in French. quarante - forty

Watch to learn how to say the numbers from thirty to forty in French. trente - thirty

Watch to learn how to say the numbers from twenty to thirty in French. vingt - twenty

Watch to learn how to say the numbers from one to twenty in French. un - one

Watch to learn how to say the numbers from 1 to 10 in French. un - one

Rooting your device gives you all-powerful administrative access to your phone and its system settings. Of course, with such power comes great responsibility, and sometimes that responsibility becomes to burdensome or just plain unnecessary.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).
The U.N. recently revived its long-held desire to take control of the Internet. It is unlikely to get its way. So, led by European nations — who else? — it has hit upon another means by which to exercise its influence: Taxes.
In late 2011, representative from China, Russia, Tajikistan and Uzbekistan submitted a proposal called the International Code of Conduct for Information Security (ICCIS) to the UN Secretary General Ban Ki-moon that called for international consensus of a global set of rules and regulations that standardize information flow on the internet.
Computación en la nube es un nuevo modelo de prestación de servicios de negocios y tecnología, que permite al usuario, acceder a un catálogo de servicios estandarizados, para responder a las necesidades de su negocio, de forma flexible, pagando únicamente por el consumo efectuado.


Art or candy? Would you eat the chocolate nipples? Via Gastronomista:

A bipartisan group of 51 senators on Thursday threatened to oppose a global treaty regulating international weapons trade if it falls short in protecting Americans' constitutional right to bear arms. 51 US senators voice concerns with UN arms treaty | kvue.com Austin.

At a conference in Geneva this past weekend, the UN brokered “deal” for the “creation of a transitional national unity government” made the illusion to executive powers given to Syria. Russian representatives asserted that Assad should be part of the interim administration. The ultimate transitional government would also oversee the drafting of a new Syrian Constitution and advise the electoral process. » UN Bureaucracy Just a Formality Before US Military Attack On Syria Alex Jones' Infowars:...

Is your iPod frozen and won't turn off? Are you nervously waiting for your iPod to un-freeze on its own? Give your Apple device a little push with a trick taught in this video on how to reset your iPod if it freezes.

Do your sauces come out to thick and un-pourable? Adjust a mixture that is too thick, using stock. Watch adn learn.

So you're staring at your un-knitted ball of yarn wondering, "What have I gotten myself into?" Fear not, a simple slip knot is the first step in any knitting project, so after this lesson you'll be an expert in getting started.

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

This video in the Fitness category will show you how to do barbell hack squats. The video is from Livestrong. Michelle Trapp, a Certified Personal Trainer at Gold’s Gym will demonstrate this routine. Keep the bar low enough so that you can safely un-rack it. Stand next to the bar facing away from the bar. Lift the bar and step away from the rack. Keep the bar close to your legs and let it slide along your legs as you come up and down. Your chest should be up and your head should be straight u...

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.
There are a couple swipe gestures in ProtonMail for Android and iOS that let you swipe right on an email to mark it as spam or swipe left to trash it. If you don't get a lot of spam or don't delete a lot of messages, it's easy enough to changes these gestures to perform another action.

In this video, we learn how to use "It's + adjective + infinitive" in English. To form these sentences, you will use the pattern that is stated above. This is very common in the English language, and you can put whatever you want into the sentence as the infinitive. You can change this from "it's hard to do" to It's not hard to do" to "it's easy to do". You can also make something negative, by giving it the prefix "im", which would change "possible" to "impossible". You can also ad in "un" to...

Meter, specifically iambic pentameter, can be used to analyze a poem. Iambic pentameter is used in poetry and drama and describes a particular rhythm that words establish in each line. Rhythm is created through the stressing and un-stressing of syllables. Small groups of syllables are called feet. A foot is a group of two or three syllables and will often contain a stressed and an unstressed syllable. Iambic describes the type of foot that is used. Pentameter indicates that a line of poetry h...

They don't call them salad days for nothing; you probably can't afford to eat anything else. But there are ways to trim your food budget—and they're even good for you. Learn how to eat cheaply on a budget.

In this tutorial, we learn how to capture HV30/HV20 HD video in Sony Vegas with Bill Meyers. First, go to "file" then "capture video" if nothing is happening, you can fix this. Go to "options" then "preferences". Now, click on the video tab and if you are uploading in high definition, you will need to un-click the box that says "use external video capture application". When finished, click on "apply" and you should be able to capture live video. Instead of seeing the blank screen when you cli...
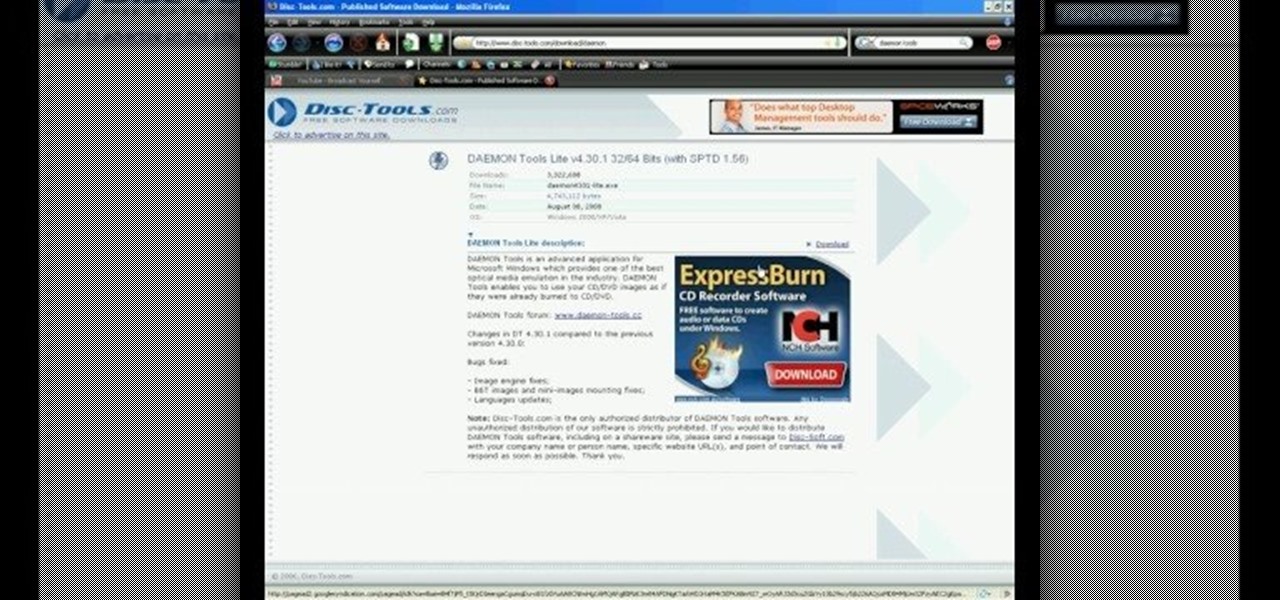
In this video, we learn how to use an ISO file after downloading a torrent. First, download Daemon Tools from Daemon Tools. After you install this on your computer, open it up. Then, find your ISO file and mount it through your computer. When you use the Daemon Tools, make sure it finishes downloading before you open it up. After you un-mount the disk to your computer, you will be able to open it up through your computer. This should work within just a few minutes and will help you open up yo...
In this tutorial, we learn how to lock and unlock cells in Excel. First, right click one cell and click on format cells. Go to the protection cell, and then un-check the locked category. Click ok, then go to protect sheet, inside of tools. Now, do now allow locked cells to be checked. Now, you will not be able to select cells in the worksheet except cells that are unlocked. This is a great way to protect your information, so it won't accidentally get deleted or ruined. You can do this for ent...
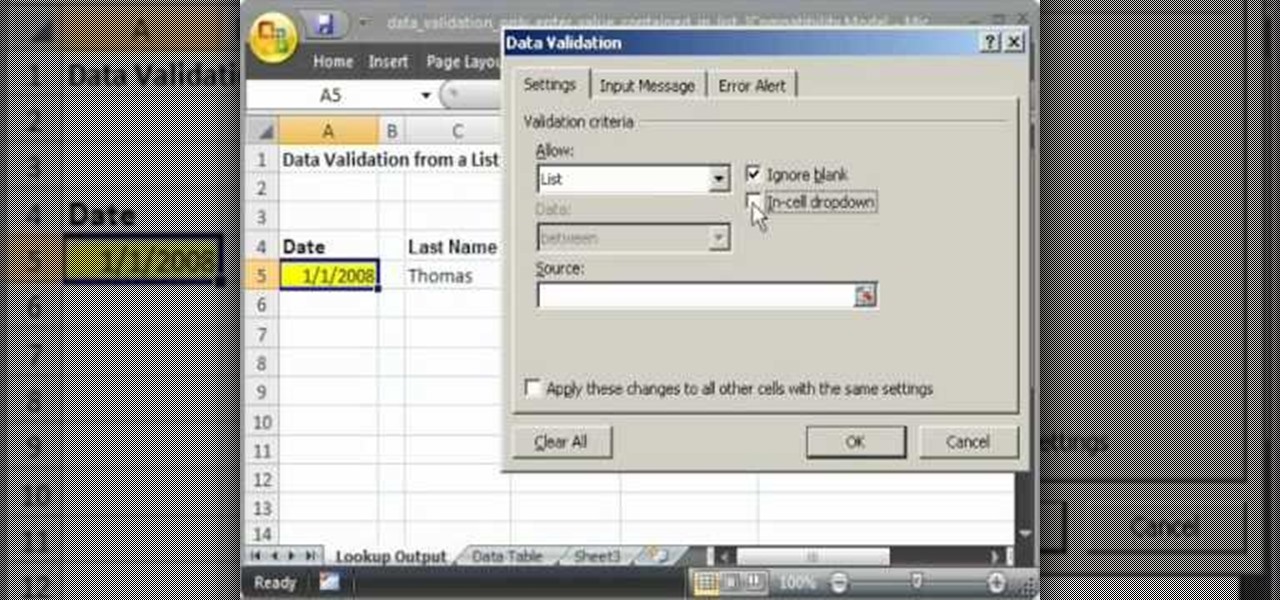
This video shows you how to idiot-proof a data set in Excel pretty much. It demonstrates how to enable data validation in a cell, so that when you type something in it must be in a predetermined list or will not work. Start by typing in your data table in a second tab. His example is a date, then information about certain employees based on that day. To enter the data validation menu, click the cell you want to use and then hit ALT+D+L to bring it up. Go to settings, then under the Allow menu...
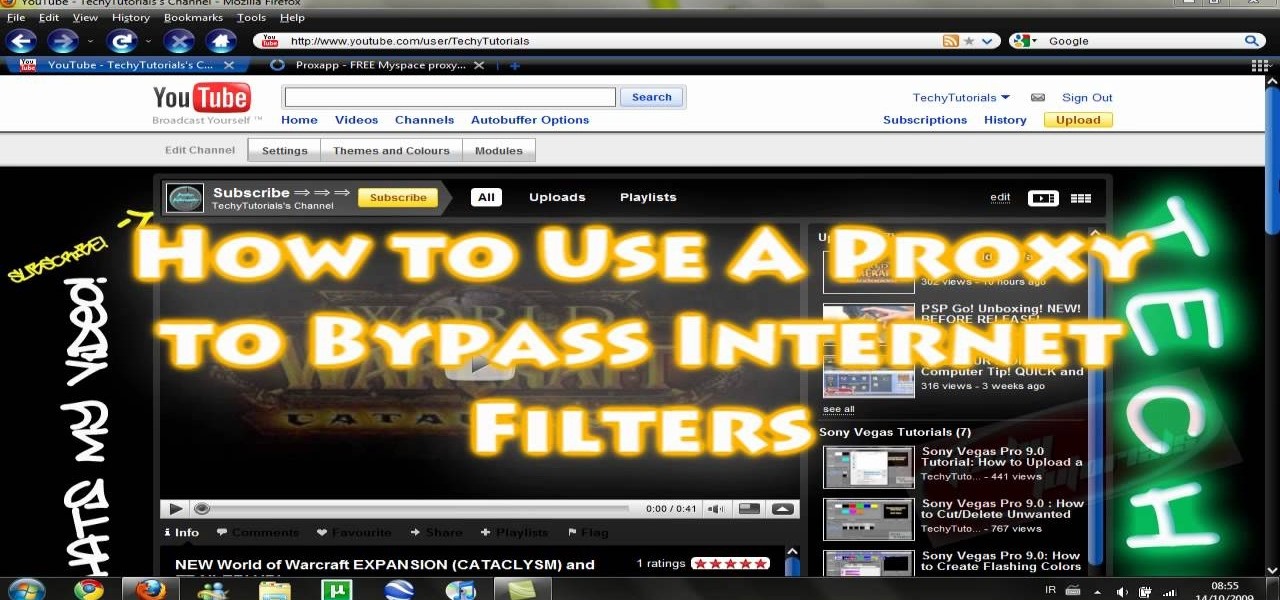
The video shows us how to use a proxy to bypass the Internet Filters. Most of the times in our schools and colleges most of the websites including the social networking ones will be blocked for security reasons and makes us unable to log into those websites. In such cases even the ones from the YouTube, several videos will be blocked. So in this video, we will be shown how to bypass those filters and log into those sites. Firstly go to the website Proxapp and over there you will be asked the ...

Basically its like good ole trampoline dodgeball. however there are machines surrounding the trampoline ready to shoot the dodgeballs at high speeds. Last man standing wins, that is if a man is still standing.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.
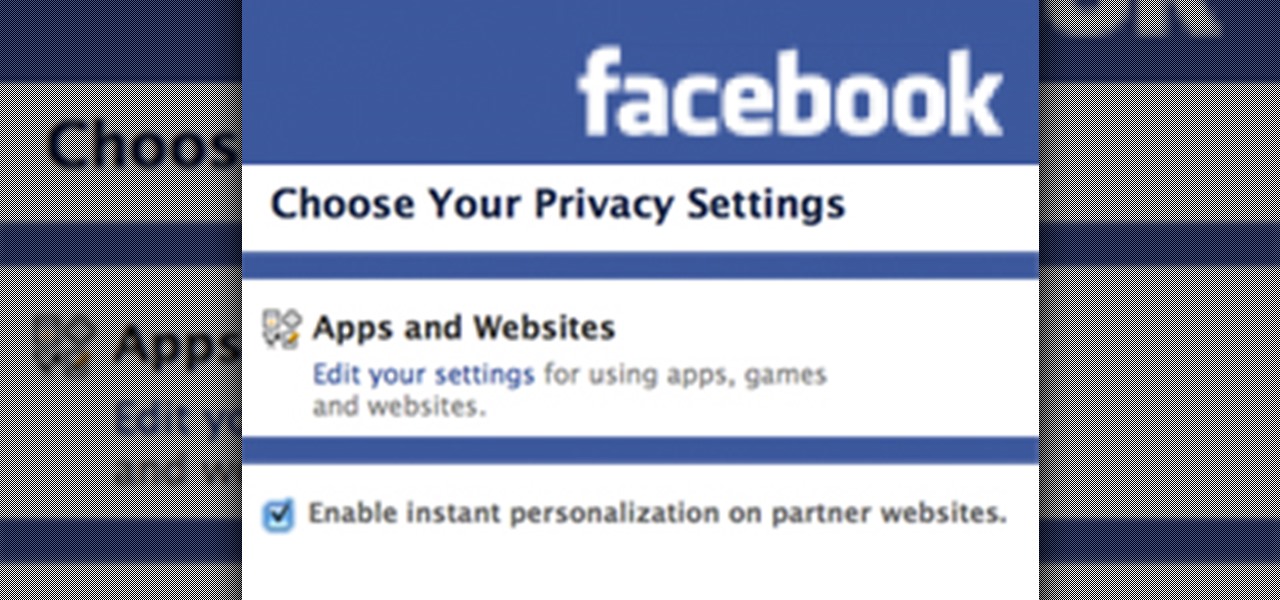
Instant Personalization. If you have a Facebook account, you've probably heard of it by now. If not, you need to educate yourself— and fast. Because they recently made some changes, affecting your privacy settings.

In this video, we learn how to write an article. When writing an article, you need to use the proper formatting. This starts with the introduction to grab the reader's attention. Then the middle will elaborate on the introduction with 200 words maximum. The end will give the conclusion and summarize in around 50 words total. Don't give an opinion, just keep it un-biased and let the reader come up with their own opinion. Don't make some common mistakes which include: spending too much time res...

In this video from ItalianLessons101 we learn some words that are useful while at a park in Italian. A disclaimer before the video states that this video is designed to teach non Italian speakers some basic phrases. Here are the words that are learned in this lesson:

In this tutorial, we learn how to make sweet oatmeal cookies. Start with 1/2 c soft margarine in a large bowl. Then, add in 1/2 c brown sugar, 1/2 c white sugar, and blend with a spoon until all mixed together nicely. Now, add in 1 egg and 1/2 tsp of vanilla extract. Mix this together with the same spoon, then add in 1.5 c quick oats, 3/4 c flour, 1/2 tsp cream of tartar, and a pinch of salt. Add in 1/2 c raisins, then combine together. Mix all of this together, then when you are finished you...

This Halloween, forget store-bought prosthetics and expensive makeup artists. If you're looking for that creepy undead look, nasty nails are easily made at home. This video will show you how to make some horrific and ghastly fingernails for your zombie, vampire or other creature costume. The key to these Halloween nails are clear plastic report / presentation covers that you can get from any office supply store.

In this video, we learn how to disable password when waking a laptop. First, go to terminal, then type in "gcomp-editor". Now a configuration editor will open, go to the gnome-power-manager, then lock on the left hand toolbar. After this, un-check the boxes that say "hibernate and suspend", then exit out. Now, go to look at your screen saver preferences and make sure it isn't set to lock when your computer hibernates. After this, when your computer wakes back up, you won't have to worry about...