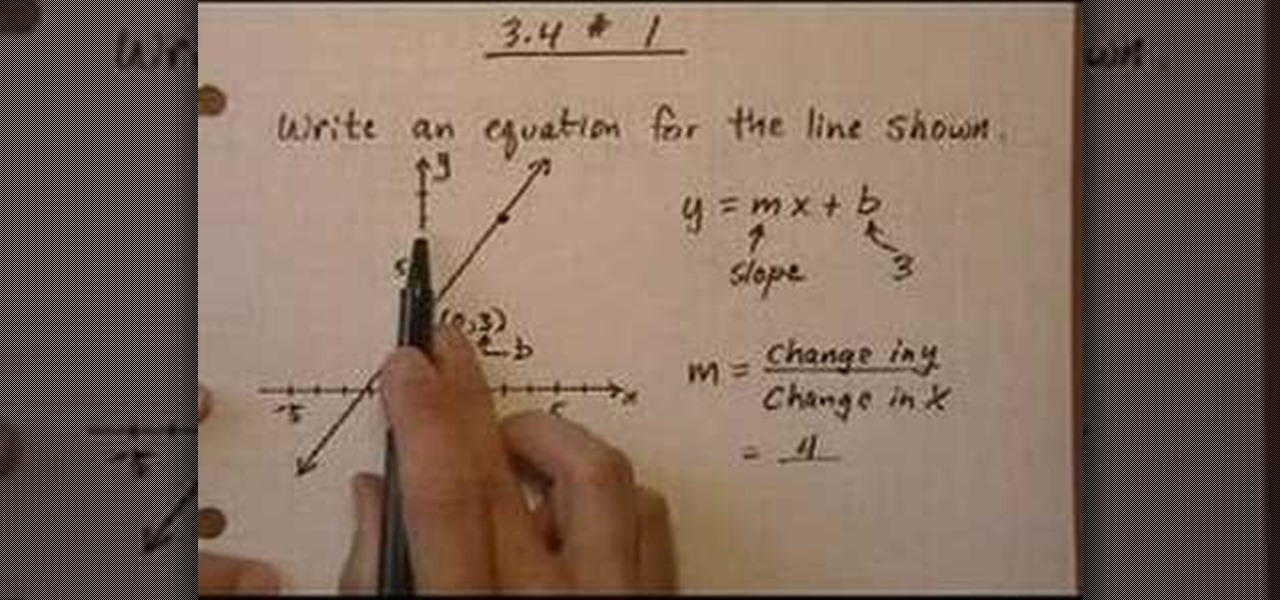
This is the video about how to Find the equation of a line. The equation of a line with a defined slope m can also be written as follows: y = mx + b where m is the slope of the line and b is the y intercept of the graph of the line. The above form is called the slope intercept form of a line. Step1 Set m to a fixed value (m = 1) and change b (b = 1, 2, 3, 4, -1, -2, -3, -4). Compare each value of b to the y-intercept of the line obtained. Step2 Set b to a fixed value (b = 1) and change m (m =...
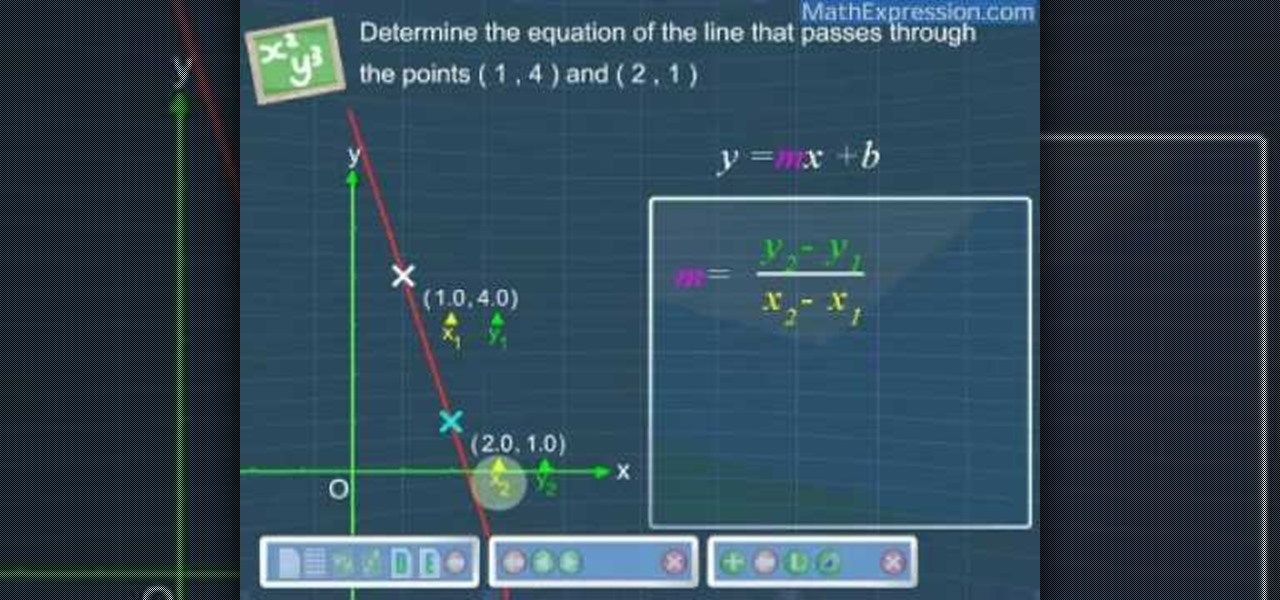
Learn how to determine the equation of a line with this tutorial: The equation of a line can be determined by two given conditions.

There are tricks to putting together jigsaw puzzles that will make them more fun to do. You Will Need

Learn how to do neutral grip pull ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

In this video from Raw Radiant Health, Natasha explains how to begin a raw food diet. First, you need to decide when you want to start. Clearly define your goals and stick with them. Once you set a starting date, you can prepare your kitchen beforehand. Your fruit should be ripe. She always has ripe fruit in her kitchen, but she also keeps things that are jut beginning to ripen, so that there is always food that can be eaten immediately, and also food that can wait a while before eating.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

The Crayola washable supertip markers are an ideal tool for any artist, young or old, who wants to bring sharply defined, bright color to their drawings. This video demonstrates how to color simple line drawings using these basic markers.

There are many types of flames you can draw, this video will show you how to draw some long, wavy flames. You can start by coping what is done and then as you recreate them you can start to create whatever style flame you would like . You might want to do the long and defined flames or a fast and sloppy overlapping flame.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

Augmented reality upstart DAQRI announced today that it has strengthened their in-house talent by recruiting renowned physicist Seamus Blackley and acquiring a team of 15 engineers and scientists from Heat Engine, LLC.

This is a tutorial on my personal makeup that I wear on a daily basis. I like the super defined lips and eyes with warm, bronze-ish skin. In my opinion, this look will make anyone look "super hot." Let me know what you think!

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Okay, so you probably weren't looking at Lady Gaga's makeup so much as her dress made out of raw meat at the recent 2010 VMAs. After all, the singer had a designer stitch together cheap cuts of meat into a dress with matching boots and a hat (basically a meat flank she slapped onto her head).

This video is about combining Microsoft Project 2010 and SharePoint 2010. This combination helps project teams to collaborate and share project information. Information can be displayed on a dashboard. We will also discuss various levels of project management such as starting the project, planning, tracking and reporting on the projects progress.

In this tutorial, we learn how to get loose waves with your hair. You will need to have your hair layered to make this hair curly. First, section off the hair so the top is up and the bottom is hanging down. After this, place the straightener in the hair and push it down away from your face and push down until you reach the bottom of the hair. Continue to do this in small sections throughout your entire head. The smaller the sections, the more defined your curls will be. Now, take some hair s...

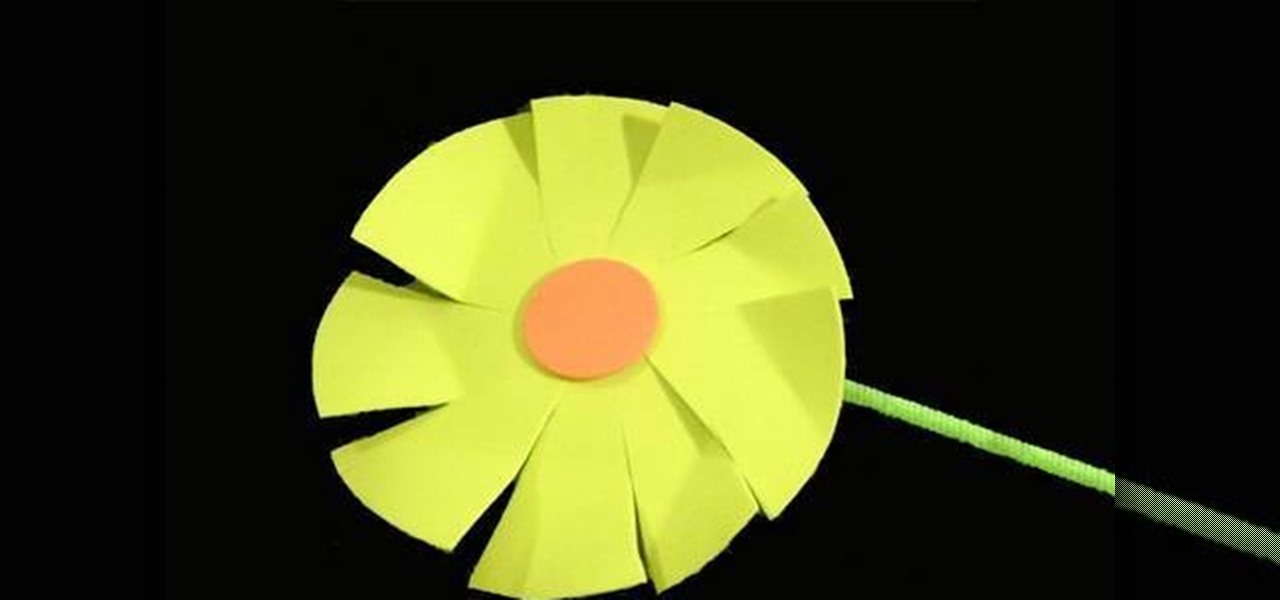
Gaillardia may be a foreign word to you, unless you're a botanist or flower enthusiast, but the gaillardia plant can be simply defined as a daisy. The American plant is usually cultivated for its bright red and yellow flowers, but it can also be the perfect craft project with the kids. This video will show you how you and your kids can make a foam amber wheel of gaillardias, which will surely please your young ones. To make this flower wheel, you'll need:

This is a sped up video on how to draw a female anime face. The artist begins by drawing the cheeks and jaw line. Then the neck is made. Next the artist makes long side-bangs that cover a portion of her face. A lot of his time and detail is spent on making the hair at this point. It is very choppy with defined pieces at the ends. During the hair process, an ear and a headband are drawn. When the hair is finished, the artist begins working on the eyebrows, nose, and eyes. The eyes seem to requ...

The Visual Prototyper is a wireframe design solution that allows you to design a fully functional application wireframe and simulate it.

Everyone from first responders to hotel cleaning staff use radios operating in the sub-megahertz range to communicate, often without even encoding the transmission. While encoding and encryption are increasingly used in radio communication, an RTL-SDR adapter and smartphone are all it takes to start listening in on radio conversations happening around you.

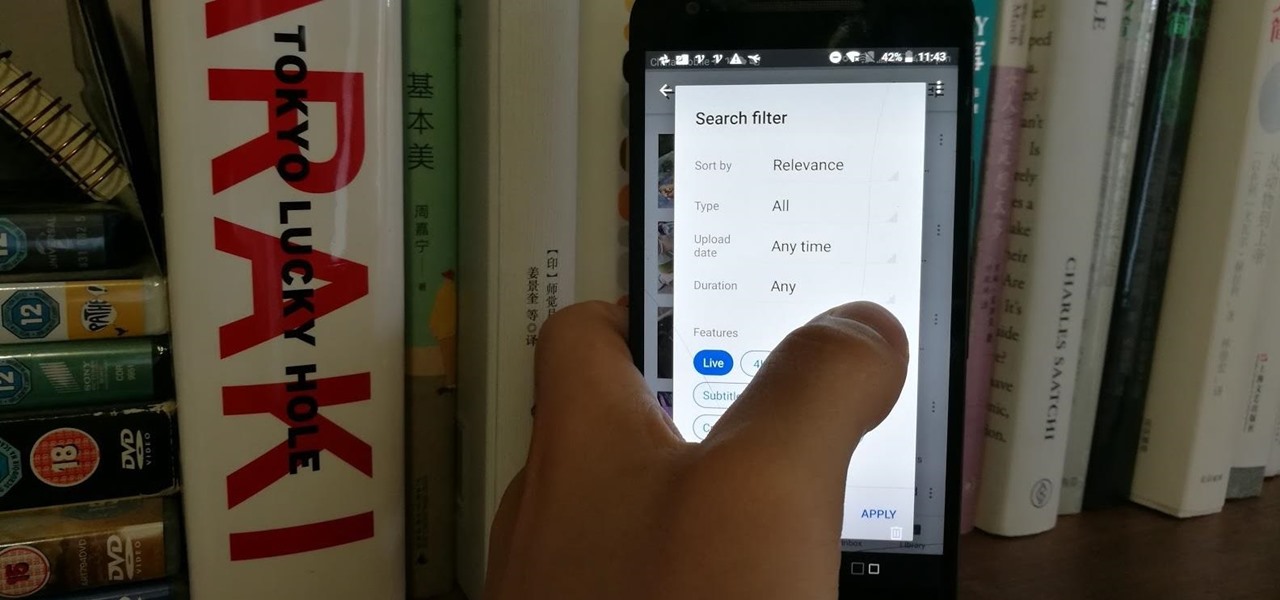
Have you tried searching for 4K HDR videos on YouTube, only to get 1080p videos just because the uploader used "4k" or "HDR" in the description? Or have you tried looking for a video about something that just happened, except YouTube's algorithm surfaces established videos first by default, so all the results you get are older than a month? Well, there's a better way.

What's up readers? We have ever so slightly touched upon this concept of scope with variables but still don't really know what it means. In this tutorial we will learn the behaviors of variables existing in our programs and within functions.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Frosted glass windows are meant for privacy, plain and simple. Sometimes you see it used for aesthetic effect, but primarily it's used to let a little light in while keeping wandering eyes out—unless those wandering eyes have some Scotch tape in their pocket.

A thesis is the basis of any paper or essay. The thesis statement sets the tone and subject of your paper and starts you off on the right foot. In this tutorial, learn how to write an impressive thesis statement and get an A on your next paper!

In these videos, you will get an introduction to the art of origami. Origami, a form of visual representation defined by the folding of paper, originated in Japan in the 1600s.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you have a guaranteed hit for cosplay or Halloween.