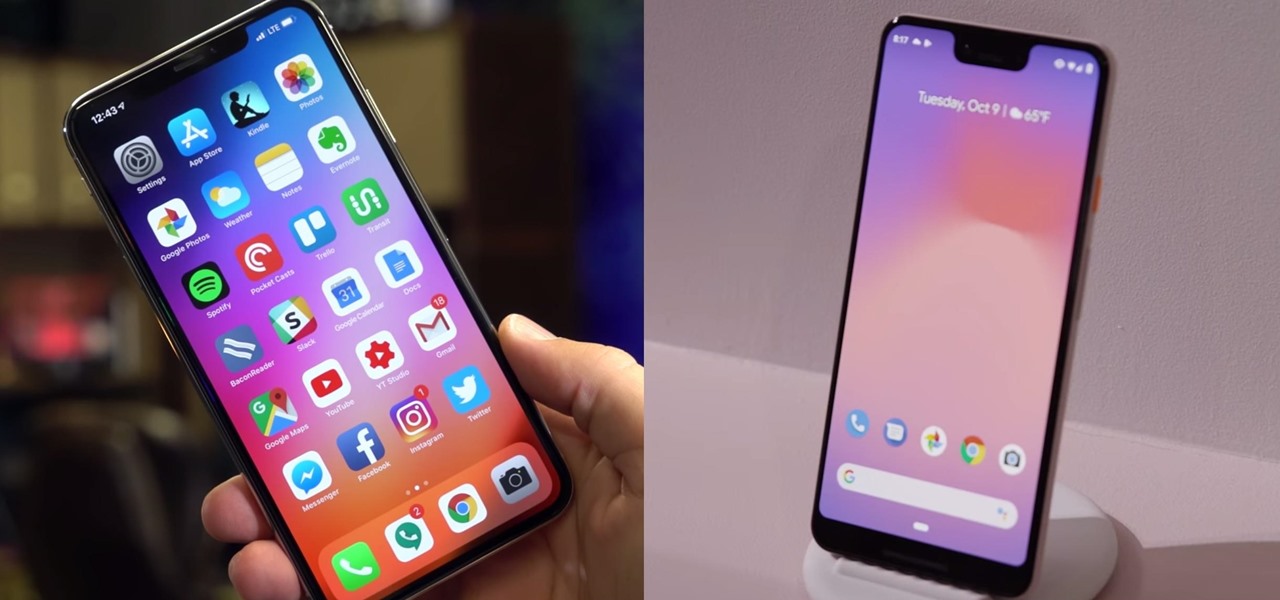
Besides the Apple vs. Samsung competition, few battles are as vocal as the battle between the best Pixel and best iPhone. This year, it's the Pixel 3 XL and iPhone XS Max, two phones that are equipped with minor hardware updates from their predecessors, though both showcase significant OS-level improvements.

Long before Apple and Android became household names, Nokia dominated the mobile industry. The Finnish company was one of the first to develop smartphones, and their classic N95 with 2G "high-speed" internet connectivity was declared the "best smartphone ever" by some in 2007. Outside of the US, before the iPhone became all the rage, owning a Nokia phone was a status symbol akin to wearing a Rolex or Omega watch.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.
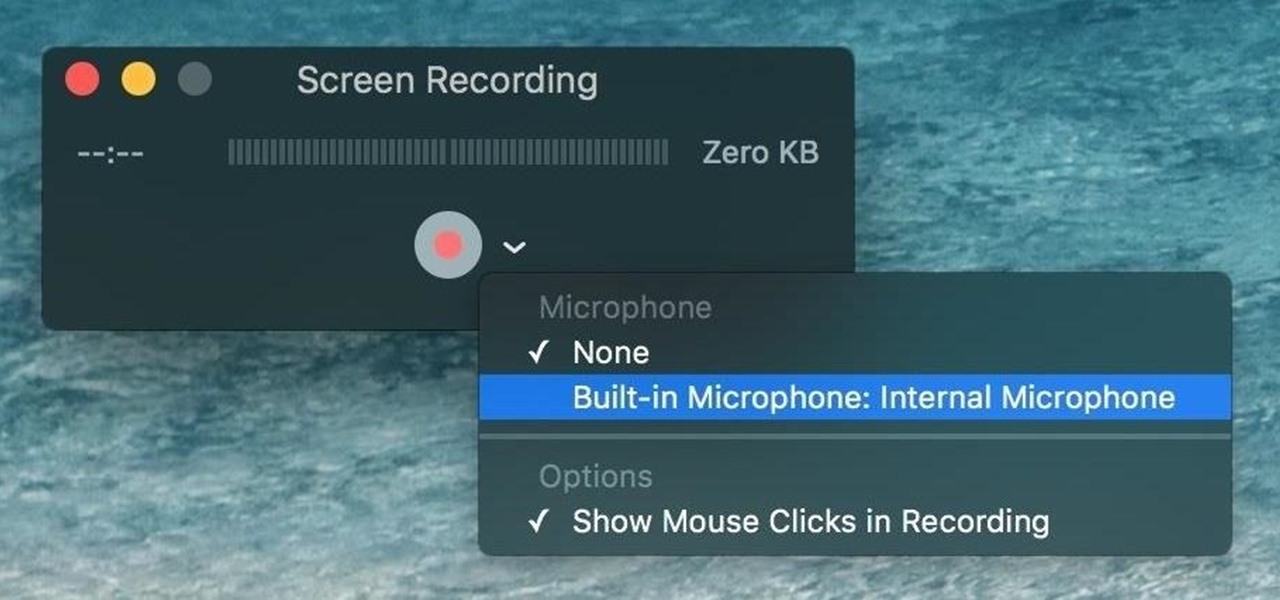
When a friend asks me what screen recording software is best to use, I always say the same thing—you don't need any! Even though it's been around since 2009, many Mac owners do not realize that they have a powerful screen recording software built right into OS X.

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.

I'm starting to wonder if the people at Boston Dynamics have ever watched a Terminator movie. Not just because the robotics company with the oxymoronic name develops machines that are able to move around environments with animal- and human-like agility, but because the people testing them seem to take such joy in openly antagonizing their creations. It's one thing to tempt fate by creating superhuman robots that could potentially end mankind. You've reached a whole new level of hubris when yo...

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

It's been a while since I wrote up an article for this series but I did say that I'd be covering some WinAPI. So if you're interested in programming for the Windows platform, hop aboard and follow along.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

The economic impacts of the COVID-19 pandemic have been felt in practically every business sector. Now, as we look back at the top augmented reality investments of 2020, the AR industry has been no exception.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

The Kinect is sure to swarm the homes of Xbox 360 gamers this holiday season. Even though some of us are amazed at the hands-free gaming capabilities it offers, others feel it to be frustratingly limited. Adafruit Industries is one of them.

Definition Declare is a card game played by 3 or more people. If 4 people are playing the game, then one pack of 52 cards (without the jokers) is sufficient. For 4 to 8 people, two packs of cards are required, without jokers.

Have you ever heard of Jamaica? Of course you have. It's that island right next to Cuba and Haiti. Well, that's not really what I'm talking about though. I'm talking about the board game Jamaica. This video series will show you how to play the board game with a presentation of the playing cards, the game round, the action types, combat, cost of spaces, penury, treasures, and the end of the game.
In a recent tweet, Notch has declared that we (the community, not just this World) will develop the OS to be distributed with 0x10c. I hope we're up to the task. Notch thinks we are, and that gives me all kinds of warm fuzzies.

Nikola Tesla In my opinion, one of the most neglected inventors of all time. The names Edison and Marconi come to mind as familiar, but Tesla? Most think of a car. Few know that Tesla is responsible for alternating current, florescent lights, radar, remote control, generators that preform efficiently, the spark plug, and many others. The U.S Supreme Court declared in 1943 that Tesla, not Marconi, was the true inventor of the radio.

Dress up the Jackass guys like women, including high heels. Place them in a rodeo arena. Have the Jackass crew sit at a table in the middle of the rodeo. Act out a bad theatre play with the crew discussing random thing and drinking coffee. Release a bull into the arena to chase down each of the Jackass guys. The last person to leave the arena is declared the winner. The losers get to enjoy a nice cup of bull piss.

via AdAge Argentina's Head Coach Diego Maradona declared that if his team won the World Cup, he would streak nude through the streets of Buenos Aires. Well, the trend is catching on.

What's the geekiest way to propose to your girlfriend? Make a robot do it for you. As a self-declared dork, RangerX52 wanted to take a simple task like proposing and make it as utterly complicated as possibly—by having a DIY robot do it for him. With knowledge of his lady's infatuation with the childlike personality of GIR, one of the main characters from the animated Invader ZIM series, he went ahead and built a tiny robotic replica of GIR to do his bidding.
Word out of Idaho is that the Ron Paul bloc in the Gem State’s GOP, perhaps encouraged by recent events at the Nevada and Maine state Republican conventions, plans to attempt a similar strategy.

Video games are the newest major expressive media. As such, their role in society is still being defined continuously. A monumentally important example of this took place yesterday at the US Supreme Court. After a long deliberation, the highest court in the land handed down a decision invalidating a California law banning the sale of violent video games to minors on the grounds that video games are protected speech under the First Amendment, like movies and books.

Boston.com's The Big Picture posts 2009's most amazing Guinness World Record holders. My favorite fanatics below.

American whiskeys tend to get an undeservedly bad rap from Scotch whisky snobs. Prove haters wrong by inviting them over for an American bourbon tasting with your favorite Wild Turkey varieties.

Get a little perspective on FarmVille hysteria, via FarmVille World, written by tenebrism: Did you know it only took five weeks to make FarmVille? That it currently has over 80,000,000 users? That FarmVille farmers outnumber real farmers in the United States by a ration of 80 to 1?

Did you know it only took five weeks to make FarmVille? That it currently has over 80,000,000 users? That FarmVille farmers outnumber real farmers in the United States by a ration of 80 to 1?

I've been dealing with emotional difficulty for many years. It started when I had surgery for the epilepsy I was dealing, and quite literally, dying with. Since the surgery on March 28, 1990 I have had no seizures, but I have had plenty of emotional difficulty. Along with that, surviving some traumatic events has added some emotional baggage...in other words struggling...along the way.

By Ethical Traveler As the world becomes ever more interconnected, being an ethical traveler becomes both easier and more urgent. Travelers today have access to far more information than we did even 10 years ago. We can observe–almost in real time–the impact that smart or selfish choices, by governments and individuals, have on rainforests and reefs, cultures and communities.

Okay so everyone remembers the classic video game donkey kong right? Well we basically do something along the lines of that. Have a larger person dressed up or painted to look like a gorilla standing at the top of a hill or path that is on a hill, and then have someone else running up the hill while the person dressed as a gorilla throws giant barrels down at them. As the barrels get to the person they have to try and jump over them while running up the hill.