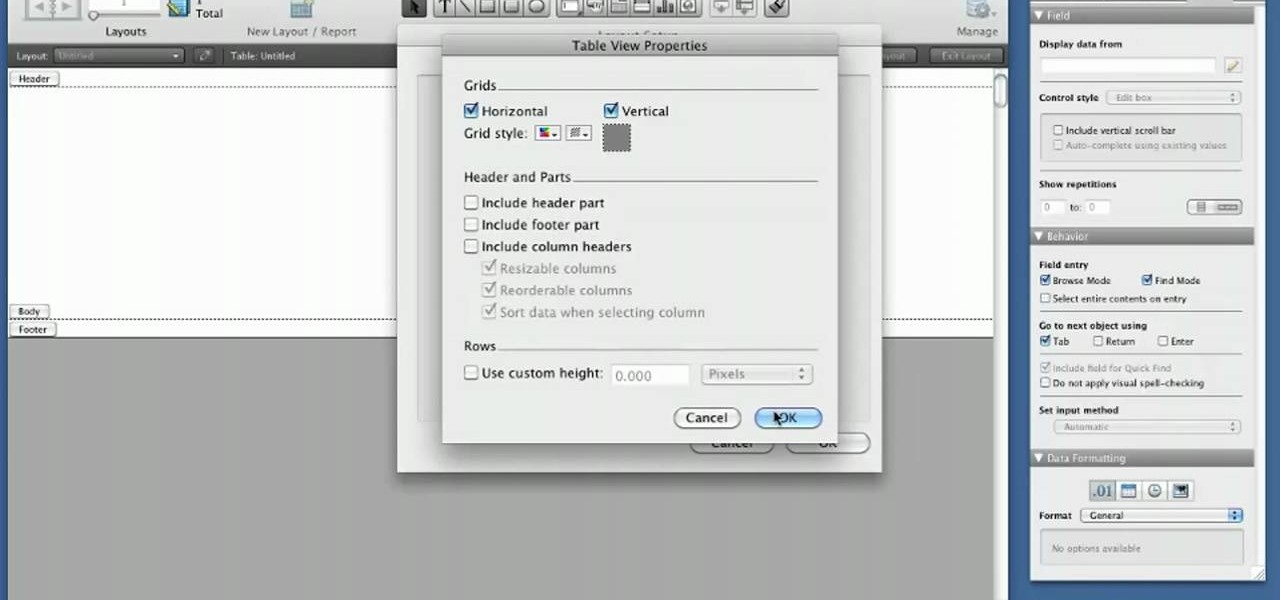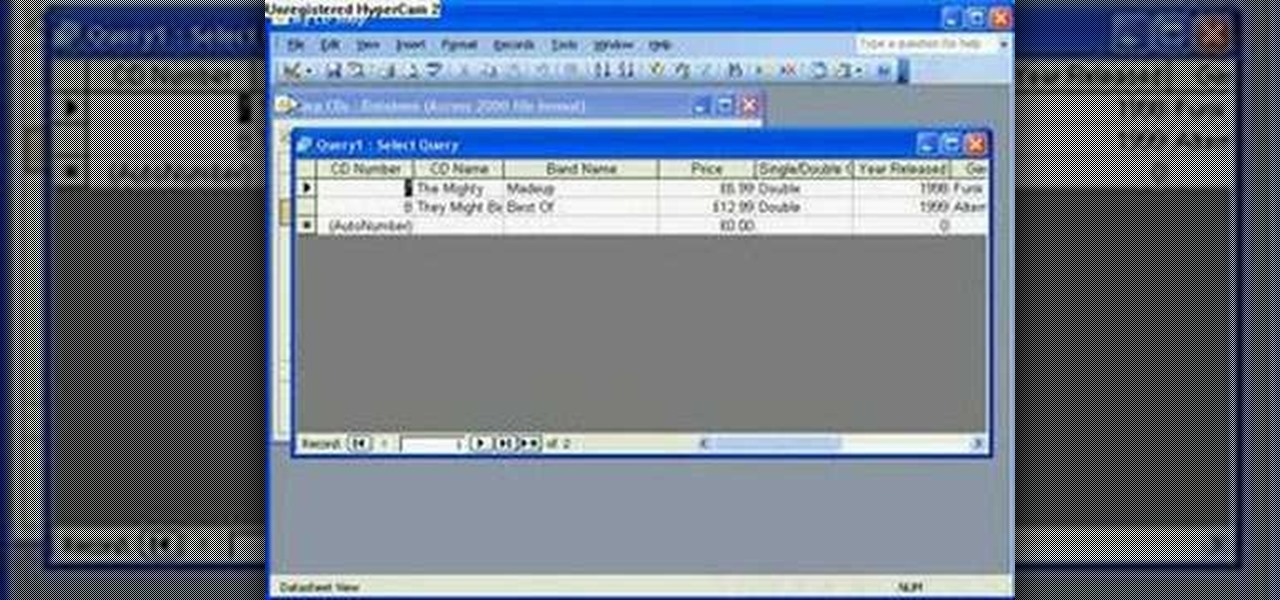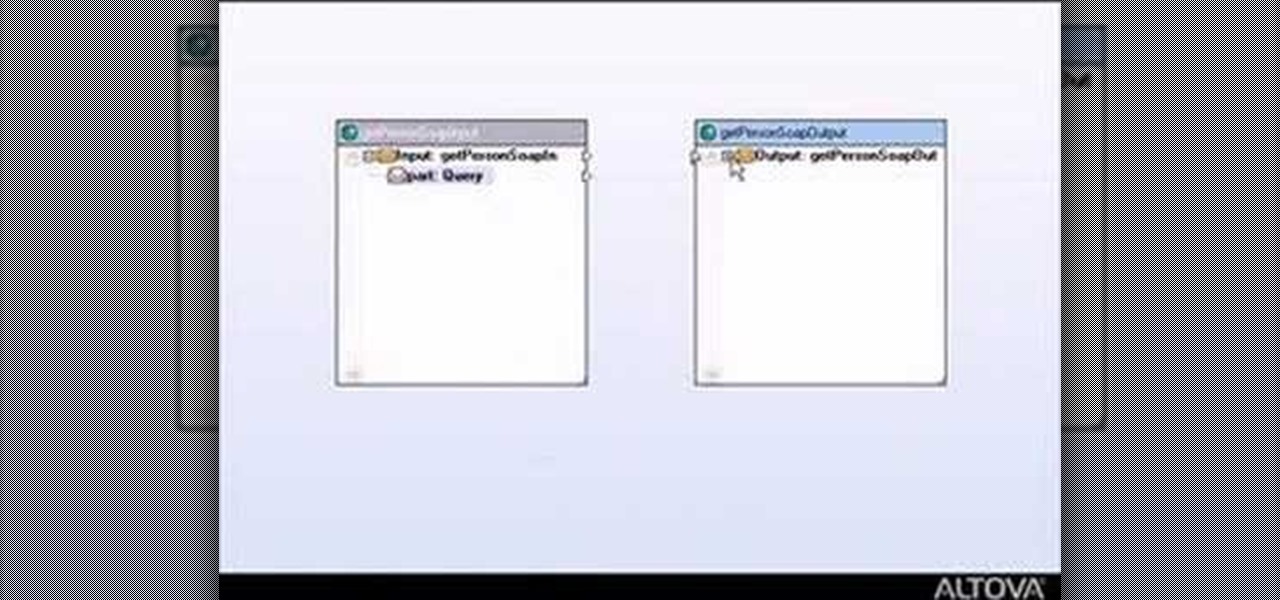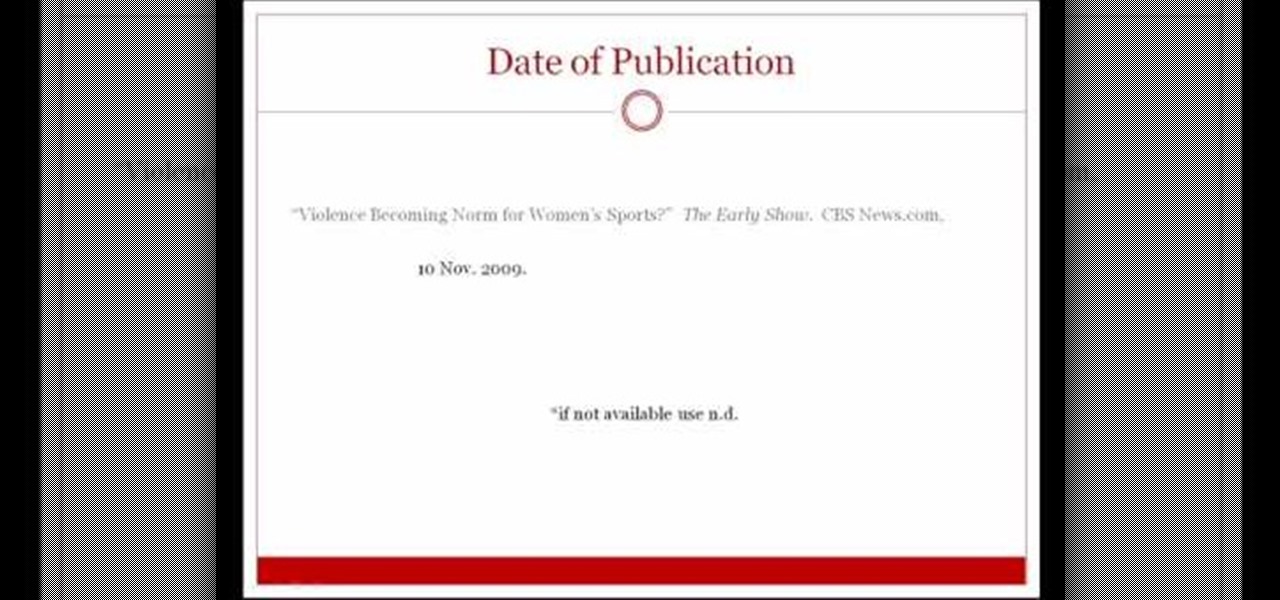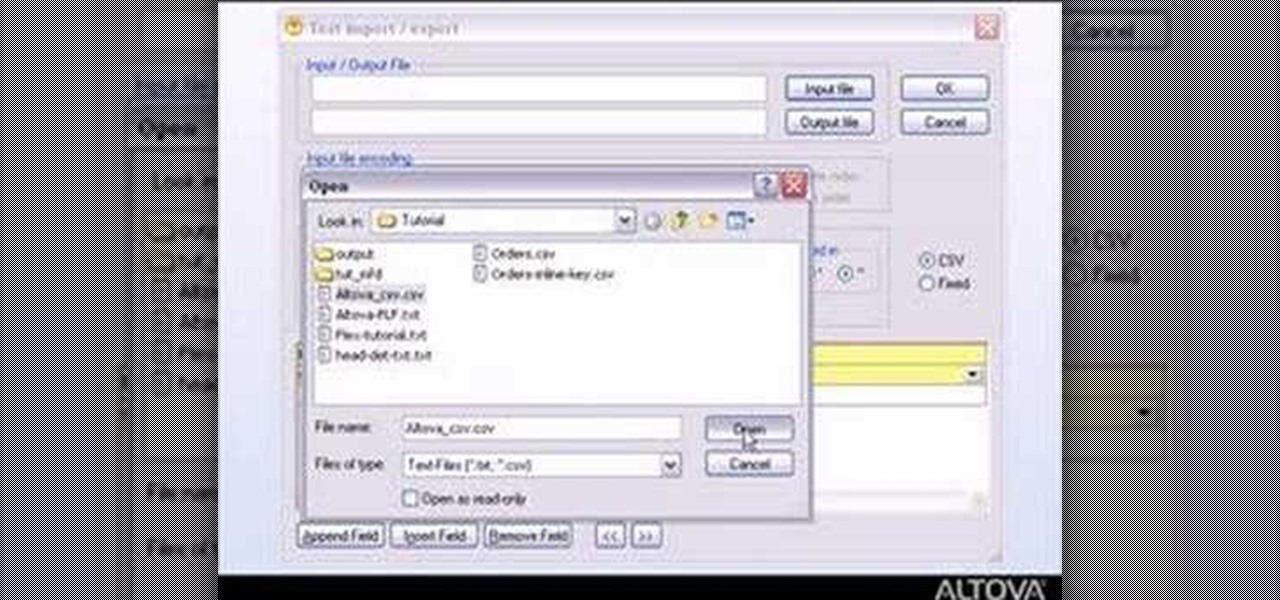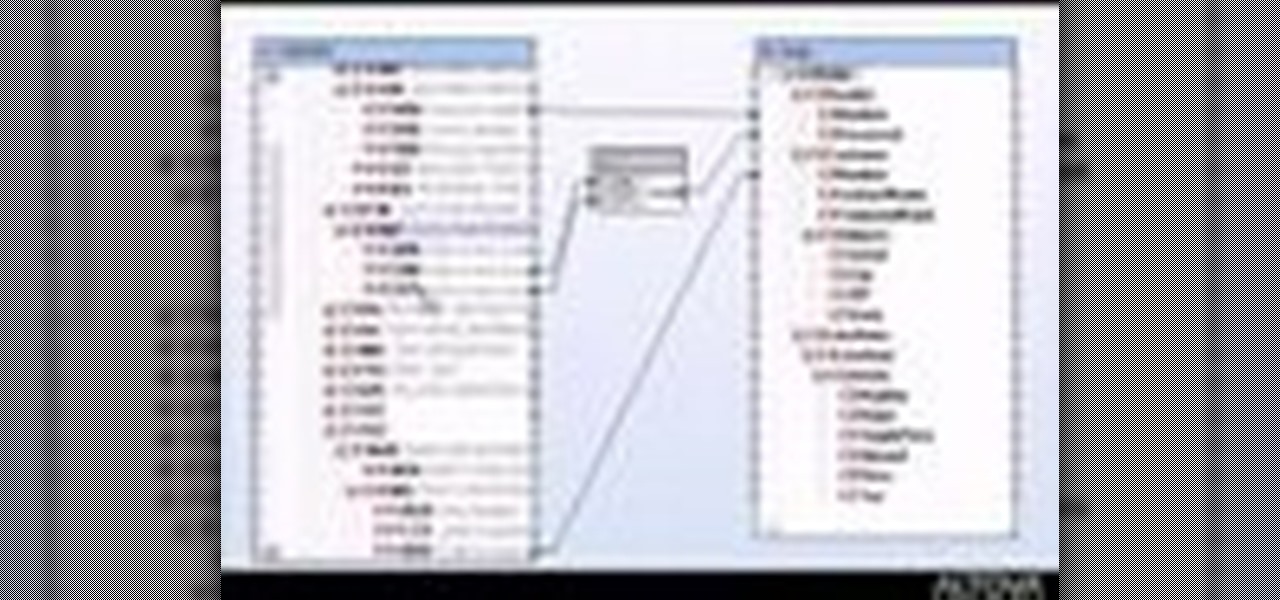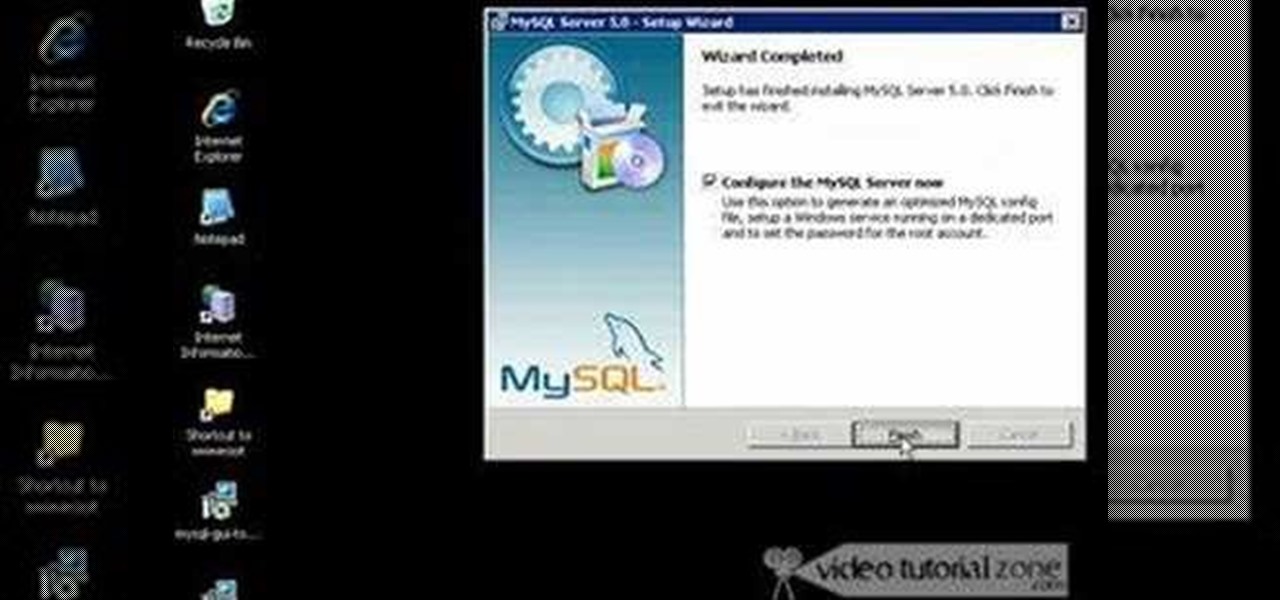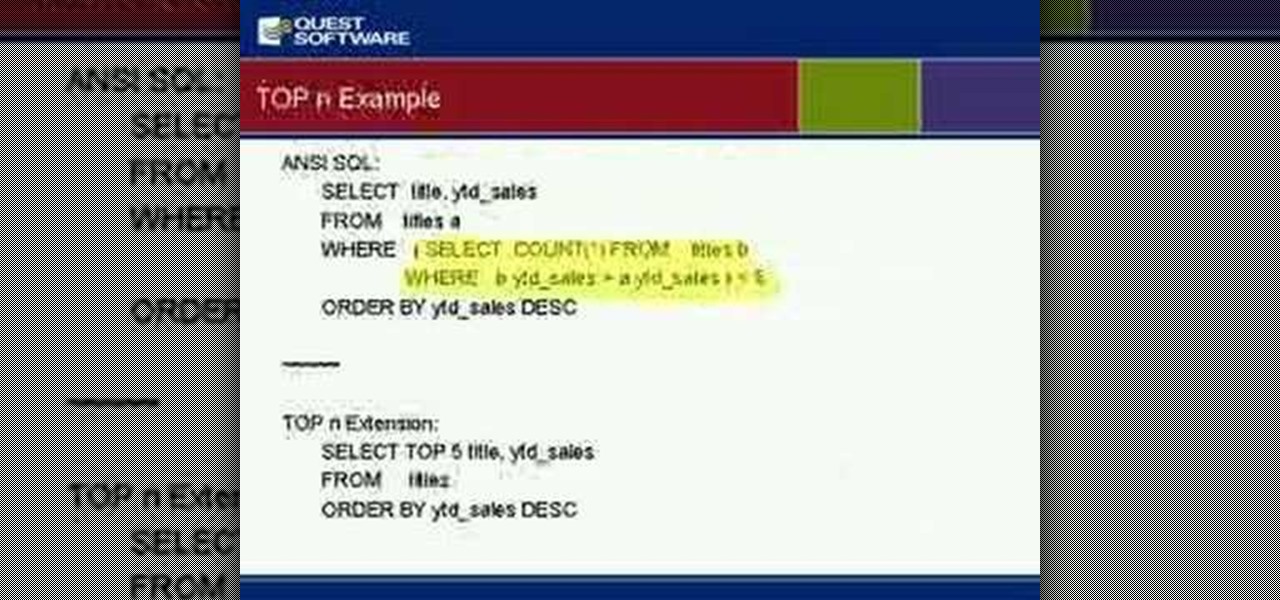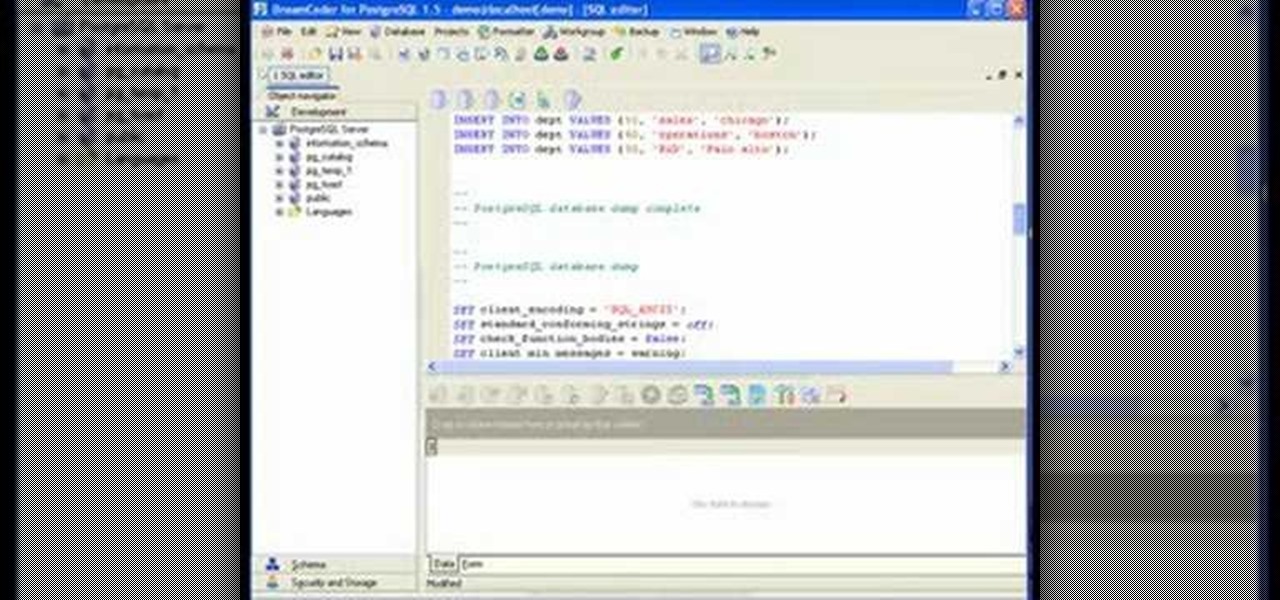
If you're new to DreamCoder for PostgreSQL, one of the very first features you should acquaint yourself with is the export data process, which will permit you to backup your PostgreSQL databases with ease. For step by step instructions, consult this how-to.

Note: The article assumes that the reader has a fundamental understanding of at least one other programming language and Perl. This is intended serve as a quick reference for Perl's input/output of data to databases.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to optimize your deep web content, like databases and forms, to be crawled by Google using a few simple tricks.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:
A Membership Provider allows a web application to store and retrieve membership data for a user, and the standard ASP.NET Membership Provider uses pre-defined SQL Server tables. In this video tutorial, Chris Pels shows how to create a custom membership provider that uses custom SQL Server tables separate from the pre-defined tables used by the standard provider. The principles covered in the video will apply to creating custom membership providers using other databases such as Access or Oracl...

In this video tutorial, Chris Pels shows how to create a custom profile provider to store and retrieve data associated with a user profile in SQL Server tables separate from the standard ASP.NET membership provider’s aspnet_Profile table. The principles covered in this video will apply to creating profile providers for other databases like Access and Oracle. After learning how to create the custom profile provider we learn how to install the provider in a web site and see a demonstration of l...

This video presented by Cris Ippolite makes a comparison between flat files and relational databases made with FileMaker Pro 10. It starts by showing flat files, which programs like Microsoft Excel use. Flat files have a big disadvantage: they cannot communicate with other files, even those with related data. If you wish to make your job easier, you should use relational databases. With databases, the tables communicate between one another. Once you store an entry in a table, you can use it i...

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

Brand new to Microsoft Office Access? This seven-minute free video lessson, which presents a general orientation to using the popular database program, will see that that you're well versed in all of the fundamentals. Learn how to create databases and forms, how to run queries and more. For the specifics, watch this free MS Access video tutorial.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

MySQL is a structured query language (hence the 'sql'), and is an open source language published by Oracle. If you want to learn how to manipulate and use databases (such as customer lists or membership rosters), you will need to learn MySQL.

Use the Quick Table view to quickly create databases within FileMaker Pro. Whether you're new to the FileMaker Pro database management program or just want to learn how to take advantage of FileMaker Pro 11's new features, you're sure to benefit from this free video tutorial from the folks at Lynda. Specifically, this software tutorial provides a complete overview of how to use FileMaker's new Quick Table tool.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 25th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to extract records from databases that do NOT contain a given text value.

This video describes how to edit and delete data in PHP and MYSQL. The video is about twenty minutes long and is perfect for anyone learning how to manage databases and websites with PHP or MYSQL. This video is part of a series on learning PHP and MYSQL. However, this video is not intended for anyone who is technically challenged or not a coder and should only be watched after having a good grasp on PHP syntax.

The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about using simple select queries on one or more fields. For more information, or to get started using simple queries in your own Microsoft Access databases, watch this how-to.

This tutorial shows you how to build web services with MapForce. Load an existing WSDL file and build a complete web service by retrieving data from databases or XML files and using a visual function builder. It's easy to build web services in MapForce as this tutorial shows.

If you're writing a college essay or report, your bibliography is a painful, yet necessary part. And thanks to all of the information available on the World Wide Web, most colleges and universities accept websites as resources in your bibliography. But citing websites can be confusing when using the MLA citation format. This video will breakdown the process.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Hello NullByte! This will be my first How To series.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

MapForce includes support for the two most popular EDI formats, UN/EDIFACT and ANSI X12. In this how-to video, you'll learn how to use MapForce to map and convert data between EDI messages (X12 and UN/EDIFACT) and XML, databases, or text files. Learn to map EDI data with this how-to.

While editing databases with DreamCoder for Oracle, you may find that you want to manipulate master-detail. This minute-long how-to video will walk you through the process in DreamCoder for Oracle. Take a look.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

MySQL is a multithreaded, multi-user SQL database management system which has over 10 million installations. It runs as a server providing multi-user access to databases. It is by far the most popular and common database used in web applications throughout the world, and almost all hosting companies provide it free of charge to their users. MySQL AB makes MySQL Server available as free software under the GNU General Public License (GPL). For this tutorial we are going to download and install ...

Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website...

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

The Operative Framework is a powerful Python-based open-source intelligence (OSINT) tool that can be used to find domains registered by the same email address, as well as many other investigative functions. This reconnaissance tool provides insight about your target through examining relationships in the domains they own.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?