
How To: Launch a Glider - Aerotow
How a sailplane glider is launched into the air from being towed behind another aircraft (Aerotow). Step 1: Launching a Glider


How a sailplane glider is launched into the air from being towed behind another aircraft (Aerotow). Step 1: Launching a Glider

In a legal brief entered on Monday, Florida-based startup Magic Leap has filed suit against the founder of Nreal, a former employee of Magic Leap, claiming that the company's Nreal Light smartglasses were built using Magic Leap's intellectual property.

It's no secret Uber has had a pretty rough year, in no small part to being sued by Google. But Google doesn't seem to have intended a full lawsuit against Uber from the get-go, as news today shows Waymo pushed for arbitration against their former employee last fall, months before the news broke that they were suing Uber.

Some data can be very confidential. In such case you need to encrypt the data so that it does not go into the wrong hands. There are lots of encryption software available to encrypt the data. But to use them first you need to install then and this can take lot of time. You can also use Windows built in compression client to encrypt information. To use this feature you need not install any software and it is a fairly simple process. So select a file that you want to encrypt, right click on it ...
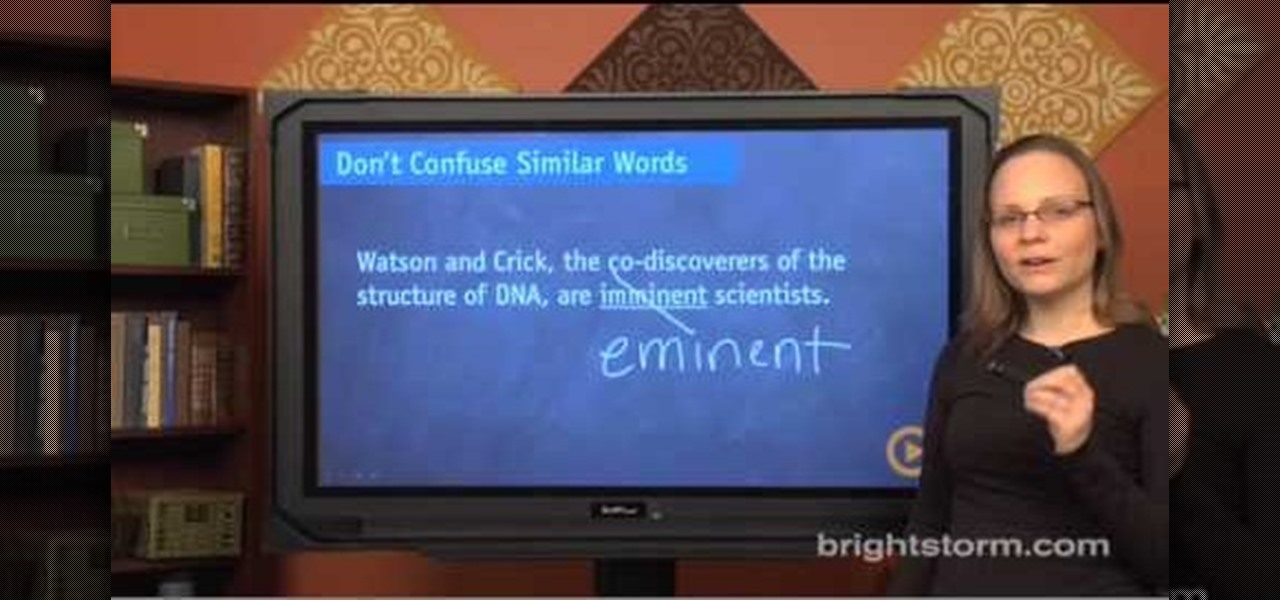
Eva Holz with SAT Confidential demonstrates how to use the right words in the SAT comprehension section. Don't confuse similar words like affect which is a verb and effect which is a noun. The words imminent and eminent may also be tested. Note also the words inferred and implied which also get confused with each other. Also, don't use the wrong idiom. A wrong idiom may often be paired with a preposition. Finally, don't use the wrong verb. Similar words, idioms and verbs are tested most often...

Eva Holtz with SAT: Confidential demonstrates how to use modifiers on the SAT reading and writing sections. A modifier is a group of words that describes a noun. On the SAT, modifiers frequently appear in the improving sentences questions. It often appears at the start of the sentence, followed by the noun it describes. Make sure that the modifier correctly describes the noun that immediately follows and not a similar, but incorrect, idea. Make sure that the noun that follows the modifier is ...
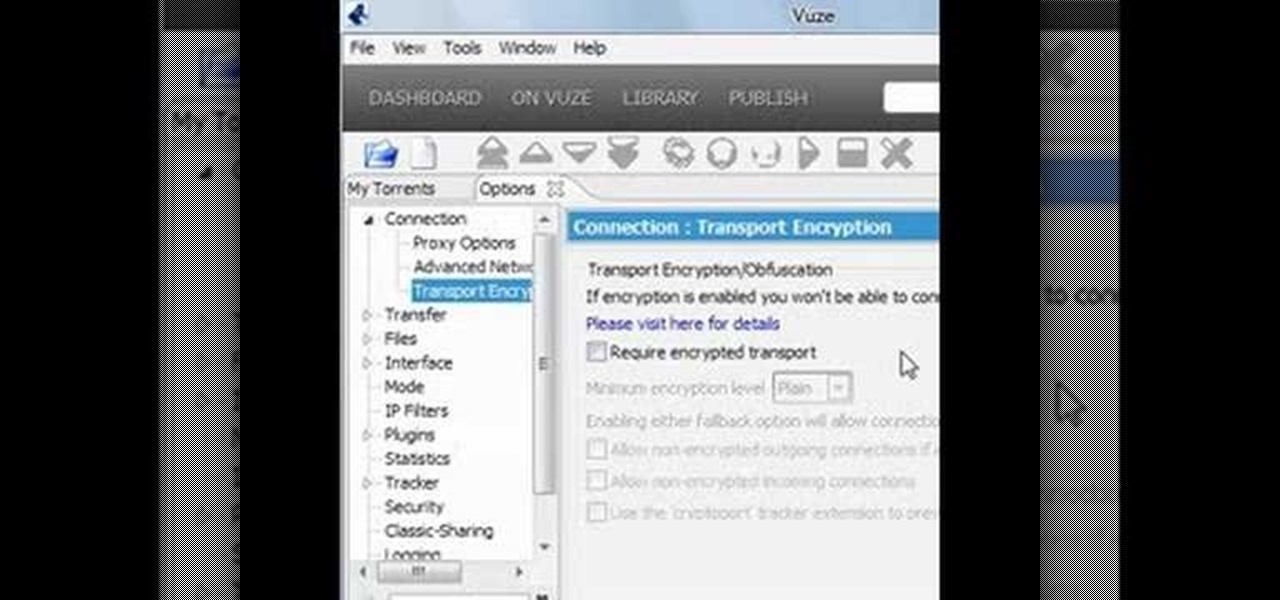
Torrents are a wonderful technology to share your files over the internet. If the data that you are sharing is confidential you may need to encrypt these files before sharing. To encrypt torrents in Azereus, go to tools and select options. From the left hand side menu select the connection option. Select the 'Transport Encryption' option from the connection sub menu. This section is intended for intermediate mode or higher and it is not available in beginner mode. So go to mode and select the...
On Last One Out...Turn Out the Lights in Halo: Reach, you will be able to earn the I Didn't Train To Be A Pilot achievement which requires you to at least be on Normal difficulty and you have to destroy three of the anti-aircraft batteries. If you're hunting around for a straggler or have NO idea how to do this achievement, check out this video! You will get all the locations of the various anti-air batteries and be set for a cool 10Gs!

One of the most integral parts to being a pilot is knowing when and how to land. And in short-field areas, some may find this tricky, depending on what type of aircrafts you're flying. This video features pilot Mike Lents, Lead Flight Instructor, shows you landing standardization by introducing the Short-Field Approach and Landing.

This aircraft origami masterpiece is a JKF-18 Hornet, which is modeled after the McDonnell Douglas F/A-18 Hornet] supersonic fighter jet used by the United States Navy and Marine Corps, along with the Royal Australian Air Force and Spanish Air Force. It's a fantastic plane—but this origami version of it is better!
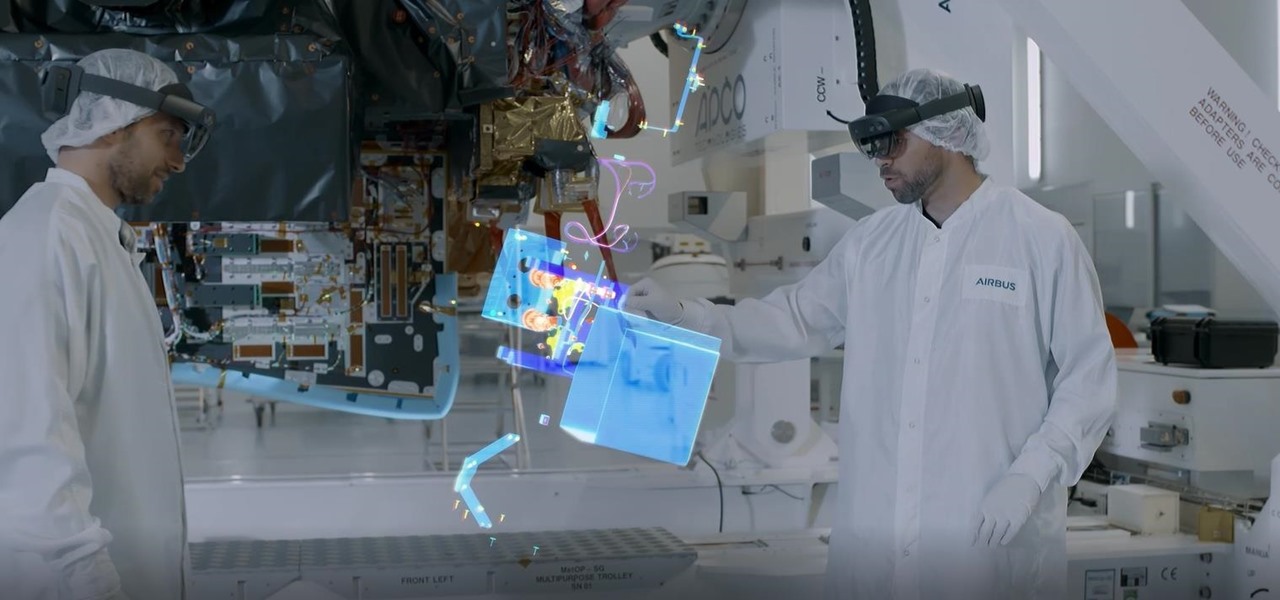
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Considering how often many of us fly on commercial airlines, the idea that a hacker could somehow interfere with the plane is a very scary thought. It doesn't help to learn that at Defcon, a researcher found that the Automatic Dependent Surveillance Broadcast (ADS-B), transmissions that planes use to communicate with airport towers are both unencrypted and unauthenticated.

Watch this visual demonstration on how to fold the Mirage. The Mirage is an excellent paper airplane. I was amazed the first time this left my hands and sailed -- nay -- floated to a perfect landing. The large wing area makes this glider easy to trim and especially graceful in the air. The "landing gear" helps the aircraft stay graceful during landings and on the ground, but I've surprisingly noticed that it seems to fly better with the landing gear "down and dirty" than with those tabs tucke...

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hack a SharePoint site.

Make your gadgets magnetically controlled with everyday things. People often take for granted the common items and devices they use in everyday life. Looks can be deceiving. It's not what things appear to be, it's what they can become.
» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.

Engineer Anthony Levandowski has officially been kicked off Uber's driverless program by a judge as the company's legal war with Waymo continues.

It seems nowadays there's no limit to what type of companies are looking to invest in augmented reality. Given both the positive outlook on the future of AR, and its reported benefits for efficiency in employees, this makes sense. Safran, an international corporation with three main sectors—aerospace, defense, and security—is one such company taking the plunge into incorporating AR in their business.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.

You will need a snare made of aircraft cable. Snares are relatively inexpensive. Remember that most likely you will only get one catch out of a cable as they kink when an animal is caught.

Whether your plane made a crash landing or your ship got lost on a three-hour tour, now you're stranded on a remote island. Here's how to get help.

This how-to video series is a step-by-step guide to molding fiberglass. These videos give a simple introduction to fiberglass mold construction, explained using a model aircraft cowling but the same technique applies to any fiberglass sculpture. The entire process is detailed from plug, to mold, to finished fiberglass part. Follow along with the eight steps: develop the plug, construct the parting board, lay up the mold, release the mold from the plug, prepare the mold for fabrication, lay up...

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.
This aviation tutorial shows you a very basic way to add add-on aircraft to an FSX. Get all the aircraft you need into Flight Simulator X (FSX) just by watching this tutorial.

FSx tutorial, shows us how to drop off and pick up passengers and theirluggage. The first thing you must do is bring the jetway and that is(ctrl + j), then open the luggage bunker which is (shift + e + 2).now you need fuel to make the fuel truck and fill you up press the following (shift + f)then the jetway is automatically attached to the plane press (shift + e) to open the aircraft door. you can also chose the amount of kerosene needed and the weight of the aircraft. when the luggage is fin...

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

Now that it has buried the legal hatchet with Meta Company, augmented reality startup Dreamworld has announced plans to open up pre-orders for its Dream Glass AR headset.

What a week for iPhone rumors. Monday saw an intriguing photo leak on Reddit of what could be the final designs for the iPhone 8, 7S, and 7S Plus (highly suspect, of course). Today continues the intrigue — iPhone assembler Wistron told reporters in Taipei that Apple's newest smartphones will be waterproof and feature wireless charging.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

The augmented reality team at USA Today closed out a prolific year of immersive storytelling with a hard-hitting companion piece exploring the controversial conflict in Afghanistan.

While flying can be a frustrating and sometimes nerve-racking experience, Airbus is banking on augmented reality features in its new iflyA380 app for iPhones and iPads to help passengers learn to love the ordeal.

With smartglasses designed for navigating drones and an AR drone racing game to its credit, Epson has just added another credit to its pioneering efforts in the AR-meets-drones space with the launch of a drone simulator app.