Apple just upgraded its Reminders app for iPhone, and there are some powerful new tools and improvements for task management that'll make you wonder how you ever lived without them.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.
Beta testing for Apple's big upcoming iPhone update, iOS 13, is well underway. So far, each of the four beta versions we've seen brought new features and changes to the table, many of which were never even mentioned by Apple during WWDC in June. Now, it's time to do it all over again, as Apple just released the fifth developer beta for iOS 13.
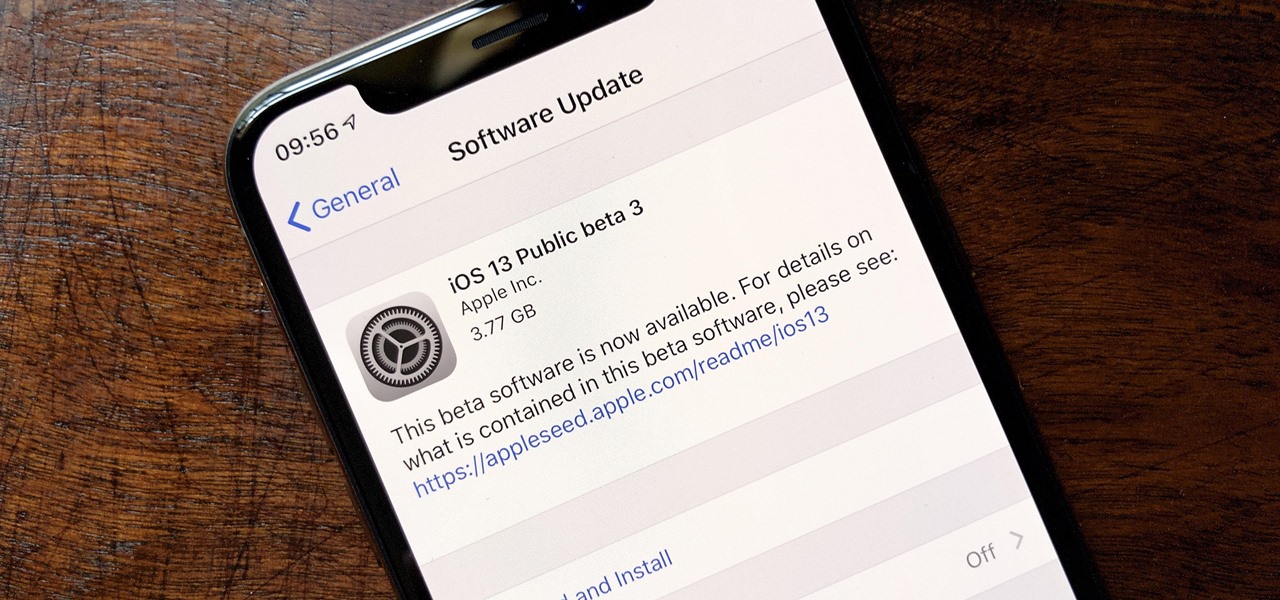
The wait wasn't so long this time. Apple released public beta 3 for iOS 13 on Thursday, July 18, just one day after the release of developer beta 4. For context, Apple took five days to seed public beta 2 after releasing dev beta 3, so it's a pleasant surprise that the latest public beta dropped so soon.
We're pumped for iOS 13 and all of the fresh features and changes that come with it. Developer beta 3 came with new features in the double digits, including AR eye contact in FaceTime and mouse cursor size customization. Developer beta 4, released today, has a few more additions and changes as well.

The third developer beta for iOS 13 has been out since July 3, and while devs have had fun exploring all the new features, those of us on the public beta have sat on the sidelines running the public version of dev beta 2. But we don't need to wait any longer, as Apple just released iOS 13 public beta 2 and all the goodies that come with it.

On July 3, Apple pushed out iOS 13 developer beta 3 for iPhone, and there's a lot found hidden within. A new FaceTime setting, more Arcade details, full-page scrolling screenshots everywhere, a noise cancellation option in the Control Center, and a new markup tool — and that's just a few of the new features.

There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

If you have ever wanted to mod your Android device, your new best friend is easily going to be Team Win's TWRP custom recovery. This gives you access to file flashing on the fly, which can include such things as Magisk for root access, or even a custom ROM to replace the stock firmware that came with the device.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

The volume buttons on the side of your iPhone can do more than just adjust the volume levels for media, ringers, alerts, Siri, and other sounds and voices. You can use them to perform different actions in certain apps and even create custom actions using the Shortcuts app. It's not exactly button mapping, but it's as close as you'll get without jailbreaking iOS.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

Individually addressable LEDs, also commonly called "NeoPixels" after the popular Adafruit product, are a bright and colorful way to get started with basic Python programming. With an inexpensive ESP8266 or ESP32 microcontroller, it's easy to get started programming your own holiday lighting animations on a string of NeoPixels with beginner-friendly MicroPython!

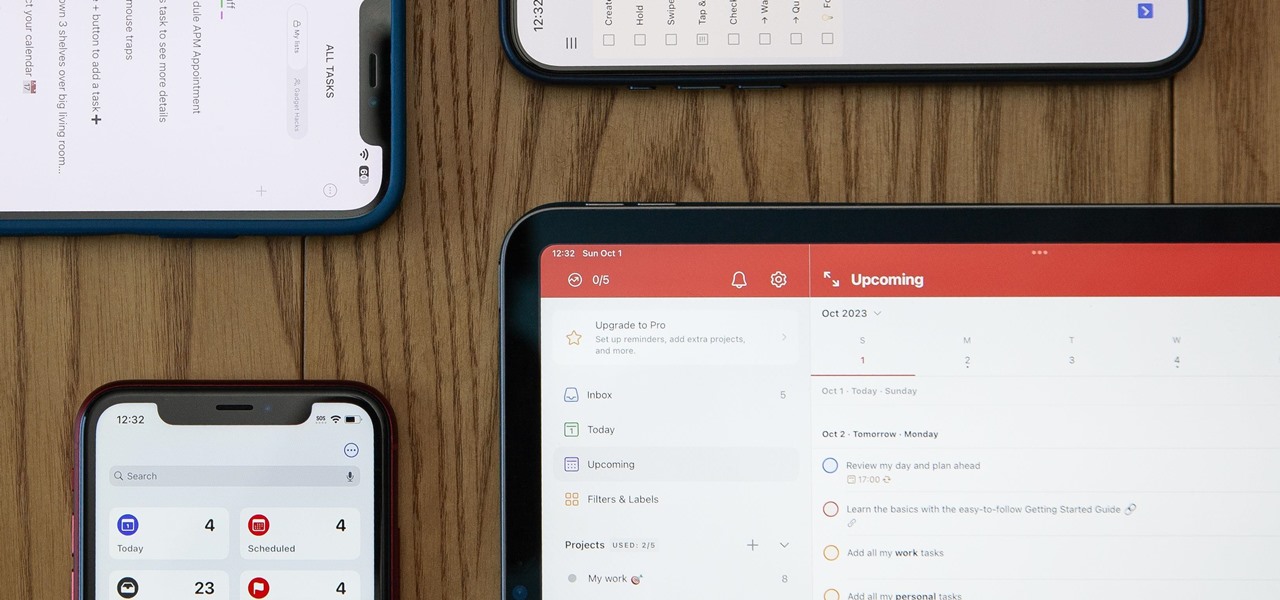
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

Need a lavish way to present your napkins at your next big dinner feast? May we suggest napkin swans? Folding a dinner napkin into a beautiful swan (or peacock) can take you just minutes and completes a dinner table. The idea behind the fold is to shape it so that one end looks like the long, languorous tail feathers of a peacock, but it could look like a swan, too.

The Motorola XOOM was just released last week to Android-hungry fans waiting the next best thing to Apple's iPad. But should it have been released, considering Verizon's switching to the 4G LTE network soon?

The young female presenter starts by recommending the Chi Turbo Digital Ceramic Spring Curling Iron for the project. She starts the hairstyle by sectioning the top half of hair and clipping it to the top of her head. Then she takes a 1 to 1 1/2 inch strand of hair from the bottom layer and curls it outwards (away from her face). When she releases the hair from the curling iron, she lets the hair hang to cool before styling it. She switches to the other side of her face and takes another stran...

If you have ever wondered how to teach kids to play cards then this is the game to start with. This is the best game to teach your kids and educate them about playing cards.

Chef Leslie Mackie demonstrates how to make berry yogurt tart - a delectable yogurt and mixed berry filling completes this basic tart. They start with eggs and sugar and then add vanilla, almonds, and berries to make this tart. Make a berry yogurt tart.

This authentic green papaya salad is made in a North Thailand way that is sure to keep you coming back for more! No only will you learn this magnificent recipe, but you'll learn how to make sure you have the perfect papaya from the grocery shop, which can be a bit tricky.

Let's say today is your birthday. You've just put those boisterous, vicenarian times behind you, reaching the first big step to your upcoming midlife crisis—30 years old. Maybe this is your midlife crisis. After all, if you're not where you want to be in life when you join the tricenarian ranks, the future starts looking bleak.

In this article, I'll show you how to make a simple touch-triggered switch. This is very useful for various electronic projects, from a simple bedside light to a flat panel touch keyboard. The circuit can vary in switching power depending on the transistors you use. For example, if you're looking into creating a 120V light that turns on when touched, you'd need two powerful transistors and an isolation relay. However, a simple flashlight that turns on when touched would only take a couple of ...

Cycling enthusiasts, behold. Fastest bicycle in the world, designed by VARNA of British Columbia. Pretty impressive.

Lock up your grandfather clocks; there's a new lady on the scene. Meet "365" by German designer Siren Elise Wilhelmsen, an electric grandmother clock that completes a two-meter (or six-and-a-half-foot) knitted scarf once every 52 weeks.

Have a few light bulbs and a blowtorch? Then join the folks over at Harvard in a cool science experiment on the conductivity of glass. As you well know, glass is an insulator with low conductivity and high resistivity. In the video below, they flip the switch, demonstrating how heating the glass fuse enclosure from an incandescent light bulb can create a conductive material that completes the series circuit and lights the second light bulb. In the video, the two light sockets are wired in ser...

Meet DareDroid: sexy nurse, geek couture and mobile bartender, engineered into an all-in-one technologically advanced garment. Created by fashion designer Anouk Wipprecht, hacker Marius Kintel, and sculptor Jane Tingley, the team calls themselves the Modern Nomads (MoNo), and their series of garments fall into Wipprecht's invented family of "Pseudomorphs". Pseudomorphs are tech-couture pieces that transform into fluid displays—which is exactly what DareDroid does.

Japanese designer Tokujin Yoshioka (creator of the crystal chair) is back with a new "shape-shifting" chair, set to debut at Milan Design Fair this upcoming week.
I've been frequenting this website I recently found out about called Codewars.com. It's pretty neat! In order to sign up, you need to pass a few simple coding tests and then you can start taking on the challenges, which they call kata. Basically, you are given a task and have to write a function that completes the given task and have to test it out on a bunch of test cases they give you. Once you pass the test cases, you can submit it and gain reputation points. It seems like a really good wa...

Biking at night is dangerous. Seriously. If you've ever taken a night ride, you've probably experience a few close encounters with a set of headlights. Which is why you use bike lights—to make yourself more visible. Problem is, unlike modern car lights, bike lights don't turn themselves off when you're done riding.

So you bought a new flat screen, and now you have to tackle the next issue—you have to mount it somewhere. Most people go for the wall, which is the most obvious place, but if you want to go for something a little different, the ceiling is always an option, too.

This Null Byte is a doozey.

Bourbon is the ultimate American spirit, considering the barrel-aged distilled spirit was originally produced in an area known as Bourbon County, Kentucky. To meet the legal definition of bourbon, it must be produced in the United States, must be created with at least 51% corn, and aged in new oak barrels. There are two types of bourbon whiskeys—straight and blended. Straight bourbon means that the bourbon has been aged for a minimum of 2 years, and has no other coloring or flavoring added. B...

Dungeon Defenders is the most exciting craft game on the Fall 2011 release schedule. I got a chance to play it at PAX in August and interviewed developers Trendy Entertainment last month. After more than a year of publishing difficulty and delay, the game finally came out on PSN, XBLA and Steam. I put about 20 hours into the XBLA version over the past weekend, beating all the campaign maps and racking up a huge pile of in-game money. It is not a perfect game. But it is a huge, challenging, an...
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States

This is a game played by 2 players. It cannot be played by more than 2 players and is played using 30 cards. Regular jokers have no role here. However there are 2 additional jokers, the seven of hearts which is the big joker and the seven of spades which is the small joker.