You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.
The biggest hurdle faced when text messaging (besides more convincing lies) is accurately communicating our emotion and tone. Anything we say can be interpreted in various subjective ways by the recipient, and that's why we have emoji—to illustrate what we actually want to say.

There's more to earning someone's trust than simply shaking their hand, especially if you're not particularly trustworthy. Your body language doesn't reveal your thoughts, it reveals your intentions, and sometimes intentions are better left unrevealed. Psychopaths, take note...

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

These days, everything is connected. No, really — we mean everything. Your phone, your smart speaker, and even appliances like stoves and refrigerators can be connected and communicate with one another. Welcome to the Internet of Things, the start of our interconnected future. It's projected by 2027 that there will be more than 41 million internet-connected devices in use around the world.

The impact of the COVID-19 pandemic caused by the novel coronavirus has practically guaranteed that the virus, along with the phrases "social distancing" and "flattening the curve," will rank among the top search terms of 2020. USA Today combined the phrases in its latest augmented reality experience, which quizzes your knowledge in the best practices of social distancing.

Gboard is often considered the best keyboard for iPhone or Android. Google made sure to jam-pack it full of features, and you should expect nothing but the best when it comes to Google's own first-party software. But with so many capabilities, a few things might slip through the cracks.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.

In case you missed it, you don't have to chat one-on-one anymore in Snapchat. The company added group chats back in 2016, and they are increasingly gaining new features such as video and audio chats, so communicating Snapchat-style with all your friends at once is better than it's ever been.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

Imagine walking up to enter a live event — but instead of pulling out a physical or mobile ticket to get admitted — you pull out your smartphone which lets out an ultrasonic sound tailored for you that lets you into the event.

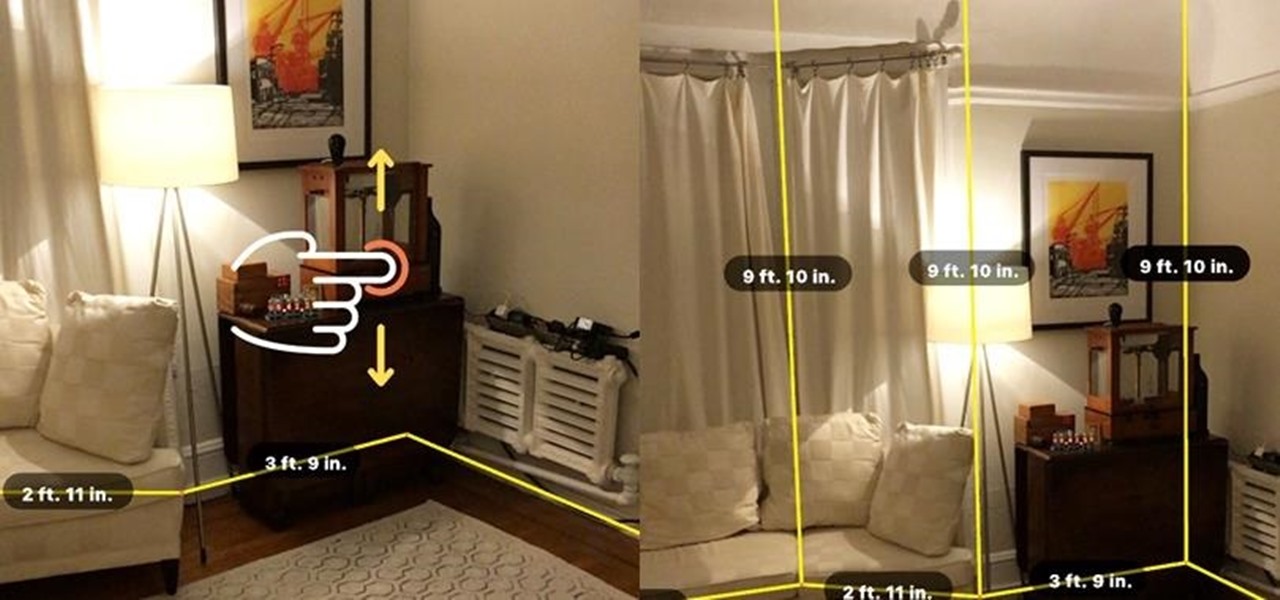
"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

Students have been passing notes in class for decades, so what's the big deal about sending a quick text message? Everybody does it, even your teacher was surely guilty of covertly communicating with his or her peers back when they were in high school.

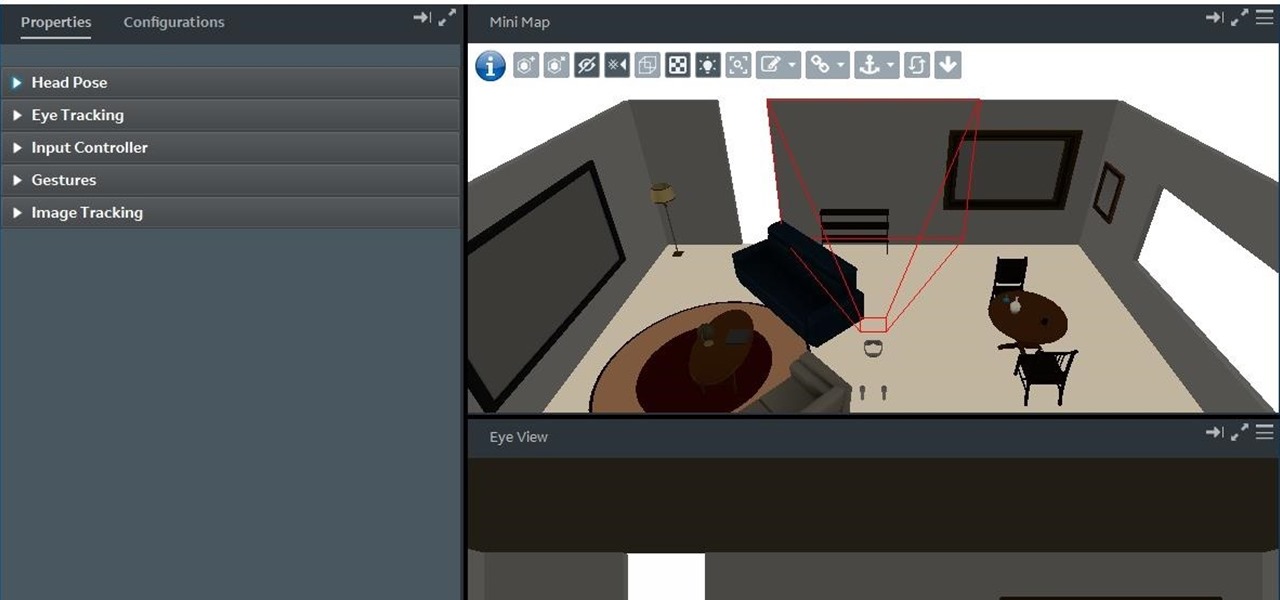
Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Now that 3D display maker Looking Glass Factory is closing in on $2.2 million raised in its crowdfunding campaign for the consumer-grade Looking Glass Portrait device, the company now has a 3D content generator to go with it.

Effective communicators are always in high demand in every industry. Whether your team is building the next billion-dollar app or you have a giant data set in front of you for filtering, communicating with your team is essential.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

Before you can dive into customizing your OnePlus 6T, you must take the initial step of unlocking the bootloader to gain the ability to install TWRP, Magisk, custom ROMs, and other mods.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

DownToDash, an app from an NYC-based startup, connects students to other students who want to hang out the same way they do. The social networking app has gained increasing popularity since its launch in October 2016 and looks ready to become even more available. The app was founded by Sama Jashnani and Anuja Shah, both recent students themselves.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

With the brand new SMS-based ordering service called Magic, anyone with a mobile phone can order whatever they want—really, anything—by sending causal text messages. Who says magic isn't real?

Your Nexus 7 may be a tablet, but it can also be used as a phone, thanks to the continued upswing of VoIP applications, which send voice and media messages over the Internet—not over a cellular network.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.