The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

People tend to skip toasting nuts in recipes or before adding them to salads because it seems time-consuming and the margin for error is high. However, skipping this step is a big mistake. Why? Because when you skip toasting your nuts (go ahead, you can laugh, we're all doing it), you sacrifice flavor and texture. And not just a little flavor, but a lot. Alton Brown recommends wok-frying peanuts before making your own nut butter for this very reason.
Pretend you're a phone thief for a moment. You might be a pickpocket or a stickup kid, but you're in possession of other people's phones on a regular basis. Now ask yourself this: what's the first thing you do after you steal a phone?

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

Marinades are among my all-time favorite tricks as a cook for several reasons. They're easy like Sunday morning, they let time do what it's supposed to, which is work for you, and you get a huge return for relatively little effort on your part.

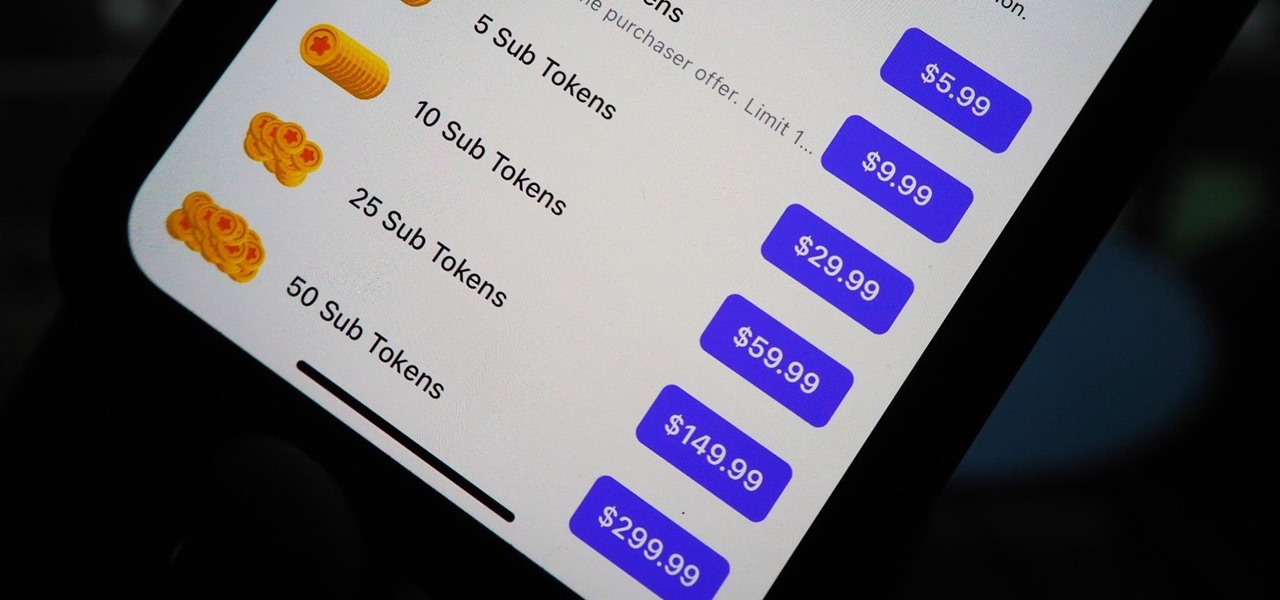
You can't hand over your iPhone to a kid and expect everything to be OK. Not only will they drop your iPhone (and they will), they could also do something much worse than a cracked screen — in-app purchases.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.
Welcome back Hackers\Newbies!

Over the past few weeks, Google, Snap, and Facebook have all taken their turns to show off their new augmented reality technologies. This week, it was Apple's turn, with new AR features for iOS 15 along with new capabilities for developers.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

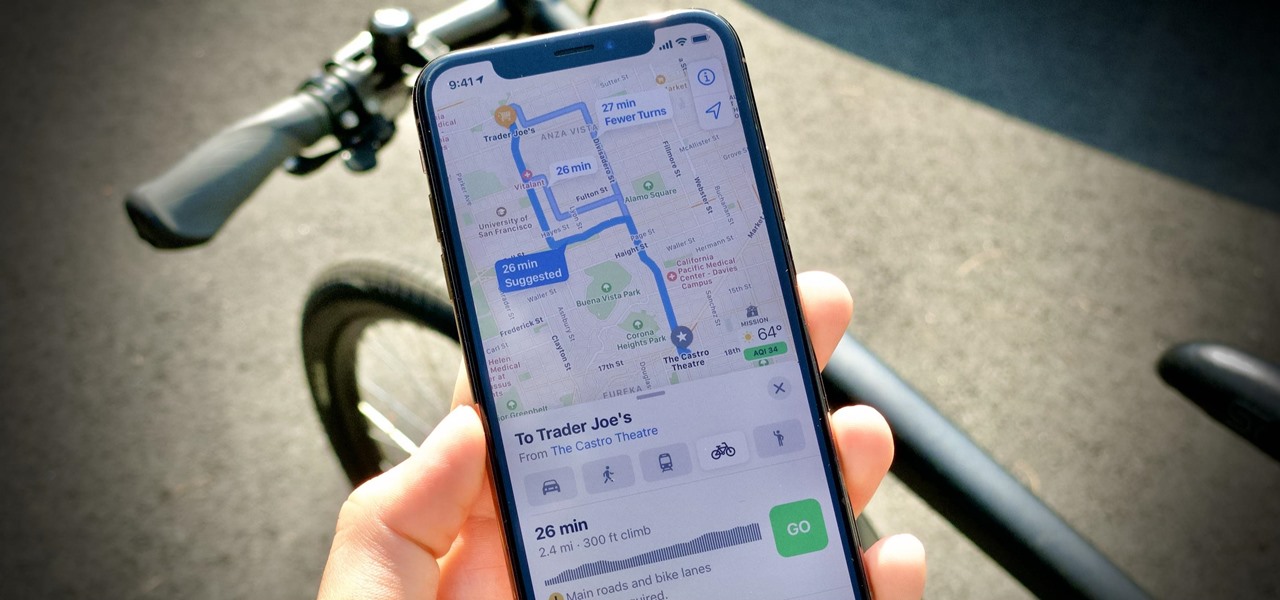
Once the laughing-stock of the navigation app market, Apple Maps is now a powerful, reliable travel companion. Apple rebuilt the platform from the ground up, placing the app in league with Google Maps. That said, there's always room for improvement, as demonstrated by its impressive new features set in iOS 14.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Apple's latest iPhone and iPad software, iOS 15.5 and iPadOS 15.5, became available on May 16, so you can download and install it right now if you haven't already. While there aren't as many new features as iOS 15.4 and iPadOS 15.4 had, there are a few big ones in the U.S. you'll want to know beyond Apple's minuscule "About this Update" information in the "Software Update" menu.

The Galaxy S20 Ultra can take pictures at 100x zoom. The regular S20 and S20+ can both do 30x for photos. But when you're shooting video, these same models are limited to 20x zoom for some reason — that is, unless you know where to look.

When the New York Times paywall first went up, there was a whole lot of balking. The idea seemed egregious to most, and the digerati's overwhelming conclusion was that the system would fail. But interestingly enough, there is speculation that the NYT is actually experiencing an increase in their print subscriptions, which according to Business Insider founder Henry Blodgett, is due to users feeling less guilt over buying the print media if, after all, the digital version is no longer free.

My friend Javi (who will join this group eventually that lazy sack) is a masterful MTG player and deck-constructor. Hell, he's damn impressive nerd all around. One time he made a Black deck out of my cards, and it is pretty devestating despite the fact that I never really collected Black and thus don't have multiples of good cards for it. It has more creatures than most Black decks (again, my fault) but uses it's excessive Mana to deal absurd amounts of damage with them.

We all remember the controversy of SCRABBLE Trickster back in April. SCRABBLE + Mattel + Proper Nouns = BLASPHEMY!