The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

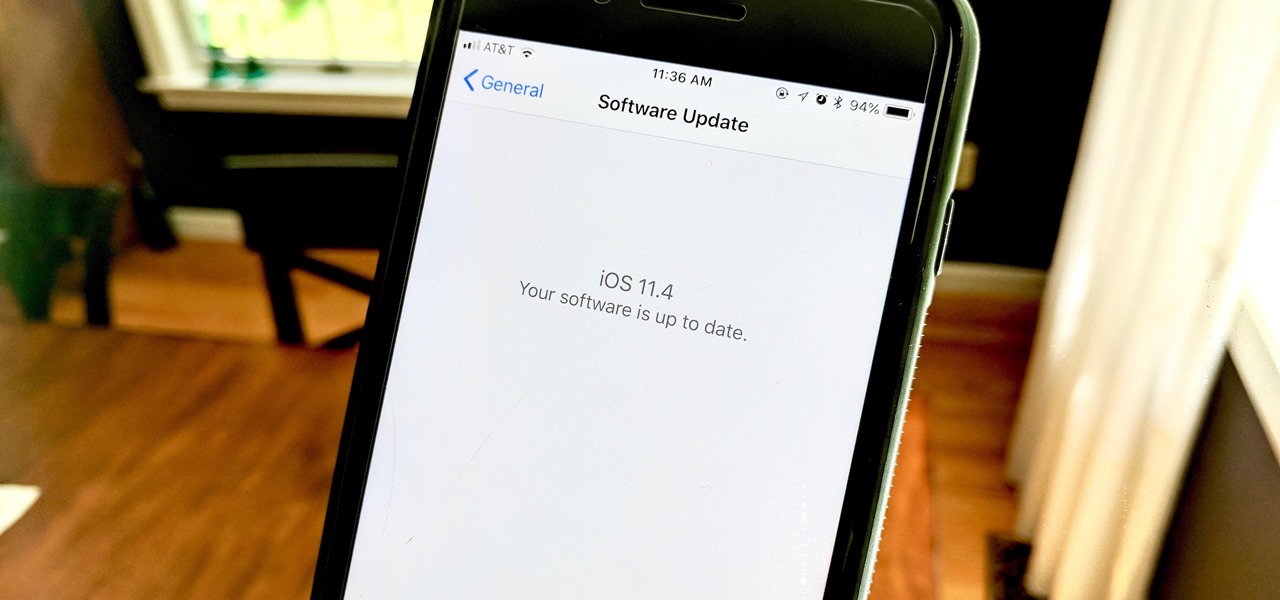
While there are at least five cool things coming in iOS 11.4, they may not be enough to get you to install the iOS 11.4 beta on your iPhone. Since its initial beta release at the start of April, there have been plenty of known issues and user-reported bugs to deal with. While bugs are to be expected with a beta, you may want to read these before installing this one on your iPhone.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Coinbase is the primary go-to for many users when it comes to investing in Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), Ripple (XRP), and more, due to its user-friendly interface. But before you join them, know that the ease of use comes with a price. Coinbase charges fees for each transaction, and your bank might even add charges on top of that. Plus, there is some fine print to be aware of.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

One of the hardest, most intimidating parts of making your own Steampunk guns from scratch is the wooden stock of the gun. To be fair, it's probably the hardest part. It requires the most artistry, and is the easiest to mess up.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

While iOS 11 is ready to take over your iPad, iPhone, and iPod touch, let's take a step back and check out all of the new features that iOS 10 brought to the public when it was released to everyone in Sept. 2016.

Your iPhone has a safety feature that makes it easier to call 911 in the U.S. and other emergency services abroad. Instead of fumbling with your iPhone's dialer, you can call someone for help in various ways — with or without your hands.

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

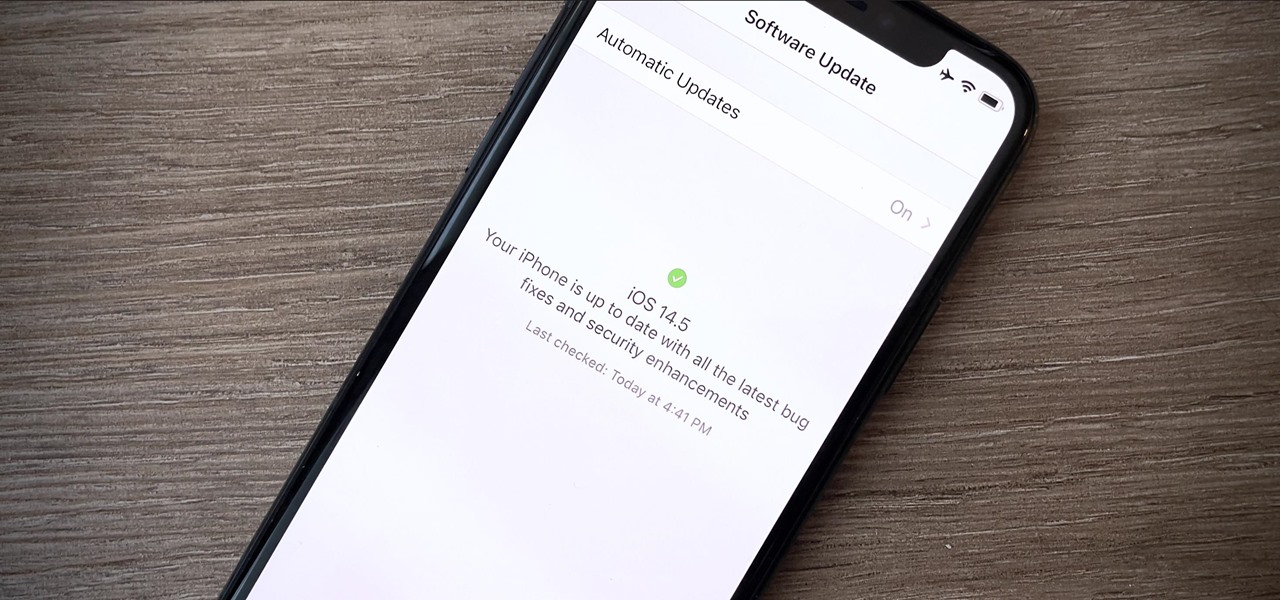
Apple's "Spring Loaded" event introduced us to many new and exciting products, including iMac and iPad Pro models with the M1 chip, an upgraded Apple TV 4K, a purple iPhone, and the long-awaited AirTag. However, one of the most anticipated announcements came in the form of a software update — the biggest update since iOS 14.0 and iPadOS 14.0 came out — and that's iOS 14.5 and iPadOS 14.5.

Apple's new iOS 14.5 will be coming out very soon, and that's even more evident now with the release of the iOS 14.5 Release Candidate (RC) on Tuesday, April 20. Anyone can install this update and get all of the same features iOS 14.5 will give everyone for iPhone; only you'll have a head start to using all of the updates in Maps, Music, Podcasts, Reminders, Shortcuts, Siri, and more.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

Rhododendrons must have lime-free soil and that can make them tricky for some of us that garden on neutral or limey soils. Planting in the garden is a waste of time and money. If you want, you can make a raised bed and fill that with acid soil but digging a hole in your garden and filling it with acid (ericaceous) compost only works for a while. The water from the surrounding soil will drain in and spread the lime and although you can acidify soil with sulphur chips you really are making life...

We’ve all been there before. Relentlessly refreshing Ticketmaster and filling in those CAPTCHA codes only to receive the miserable “No tickets are available at this time” message. That’s because ticket brokers with a dozen screens and God knows how many browsers snatch up anything and everything.

There is no fan experience in professional sports quite like watching an NBA game live. Partly, this can be attributed to the combination of fluid teamwork and jaw-dropping athleticism the players exude in the form of size, speed, jumping ability, grace, and strength. What truly differentiates the NBA from the spectators' perspective, though, is the figurative nakedness of the players. While the NFL buries its athletes beneath pads and masks, the NBA presents its talent in shorts and a tank top.

Introduction Halo: Reach is Bungie's latest and final addition to the franchise. Microsoft has claimed the title and from now on 343 Industries will be working on the Halo franchise. In my opinion, Bungie's last game is the best out of all of them. These are some tactics and bits of advice that I've picked up.

Sometimes strange things happen on the golf course, you are outdoors after all. In this video from the New York Times, PGA golf pro Bryan Jones offers advice on what to do in stranger circumstances.

General Electric isn't known for their Christmas lights, but maybe they should be, because their GE Color Effects are pretty awesome. Especially the LED Color Effects G-35 String sets. And especially when someone named Darco hacks them.

Waiting for that first kiss can be an eternity.

Cinematographer Anna Foerster shot tests for Roland Emmerich's new period film "Anonymous". It's nice to actually see a test shot by a legit DP under controlled circumstances.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

If you’re so smart, why aren’t you rich? Although money and mental muscles may seem a natural match, brains, alas, may be more hindrance than help when it comes to getting rich, concludes a new study in the journal Intelligence.”It is still not well understood why some people are rich and others are poor,” writes study author Jay Zagorsky of Ohio State University. “Luck, timing, parents, choice of spouse and many other factors play important roles in shaping an individual’s circumstances,” he...

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

The war against machines is near, thanks to Cyberdyne... I mean... the German Aerospace Center. The DLR Hand Arm System is a terminator-like anthropomorphic appendage that functions just as a normal human hand and arm would. Only it's way more durable and can take a beating from not only a hammer, but a baseball bat. Possibly the next-gen soldier?

Well, this is my first article on WonderHowTo, and is only going to be short because it's an extremely easy and effective method for removing a painful sunburn. This method was recommended to me by my friend's mother, who is a nurse and therefore MUST know what she's talking about. Turns out she did. I hope this helps many painful sunburns to recede or disappear.

Thanks to the advent of smartphones and mobile apps, Scrabble has spread like wildfire across the globe, whether it be Scrabble or one of its many popular word game spinoffs, such as Words with Friends, WordWise and Kalimat.

Sometimes, paying for the whole Xbox LIVE service might seem like a waste of money. You're constantly experiencing lag, you've got people modding and cheating, kids are being loud and obnoxious over the mic, and your kill-to-death ratio is getting dumped on. Basically, the whole multiplayer experience just isn't cutting it anymore—you want to go back to the classic world of single player. Well, there's always downloadable content—simply known as DLC.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.