Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

The last update to iOS 12 featured more emoji, Group FaceTime, eSIM functionality, real-time depth control for new iPhones, and a few other interesting tidbits and fixes. Now, in the latest for iPhones, iOS 12.1.1, Apple brought back a few things that were removed or made more difficult to access in previous updates, and it even has a few new features to offer, albeit small ones.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

Nintendo fans rejoice! Not only can you play classic NES games on your iPad or iPhone without jailbreaking, you can play Game Boy Advance and Game Boy Color games. And that's not it. Now, thanks to @angelXwind, we can add Nintendo DS to our list of non-jailbreak emulators for iOS 7.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

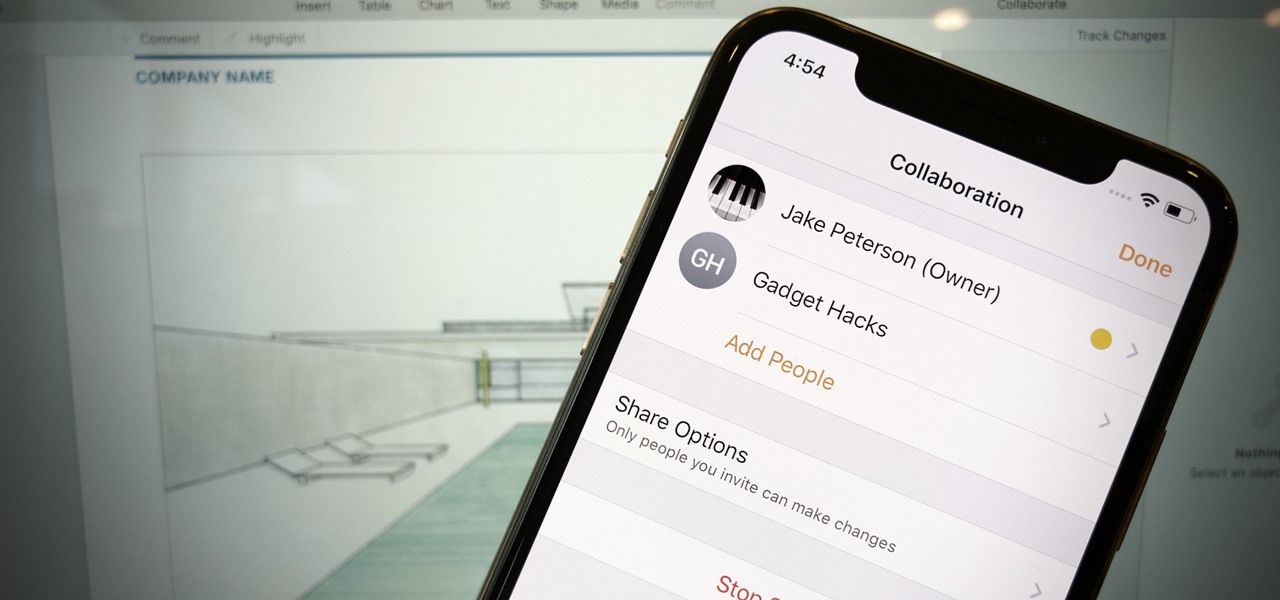
Google Docs is made for teamwork and collaboration, but Apple's iWork suite also comes with the same functionality. If you're working on a Pages document on your iPhone, and you want input from other members of your team, you can easily invite them to view, comment, edit, and more right alongside you.

The iOS 12.0 beta earned admiration for its superior performance to last year's controversially buggy iOS 11. That doesn't mean it was free from problems before the stable release went live. During the initial iOS 12.0 beta testing phase, there were plenty of bugs and glitches, many of which affected the apps we use every day. However, none of these issues persist anymore since iOS 12 stable went live.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

A year and change into its shift towards enterprise customers, Magic Leap has updated Lumin OS and the corresponding Lumin SDK with some key prerequisites for the business sector.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Hello fellow Nullbytiens, today we will be talking about IRC again (if you haven't read OTW's post about head over there now)and more specifically about using 1 nickname with multiple devices or IRC clients.

If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for your costume.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

A few months ago, iOS 12.1 came out with a handful of useful new features, and iOS 12.2 goes even further. While some of iOS 12.2's new features for iPhone are much welcomed, there are some that we'd be better without.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

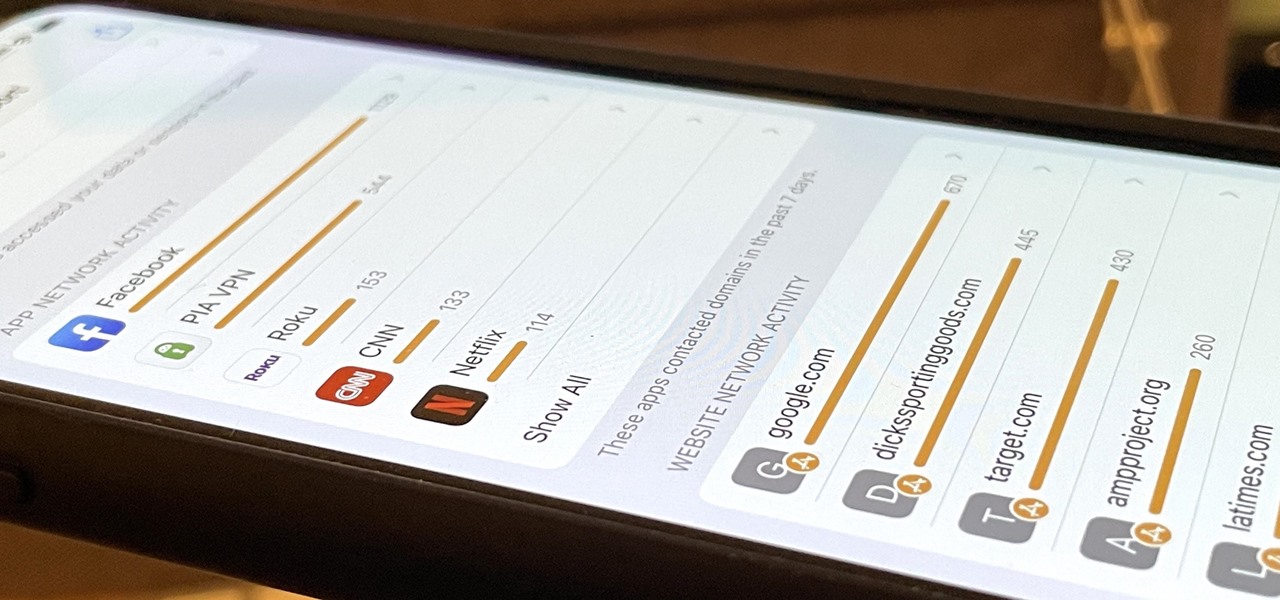
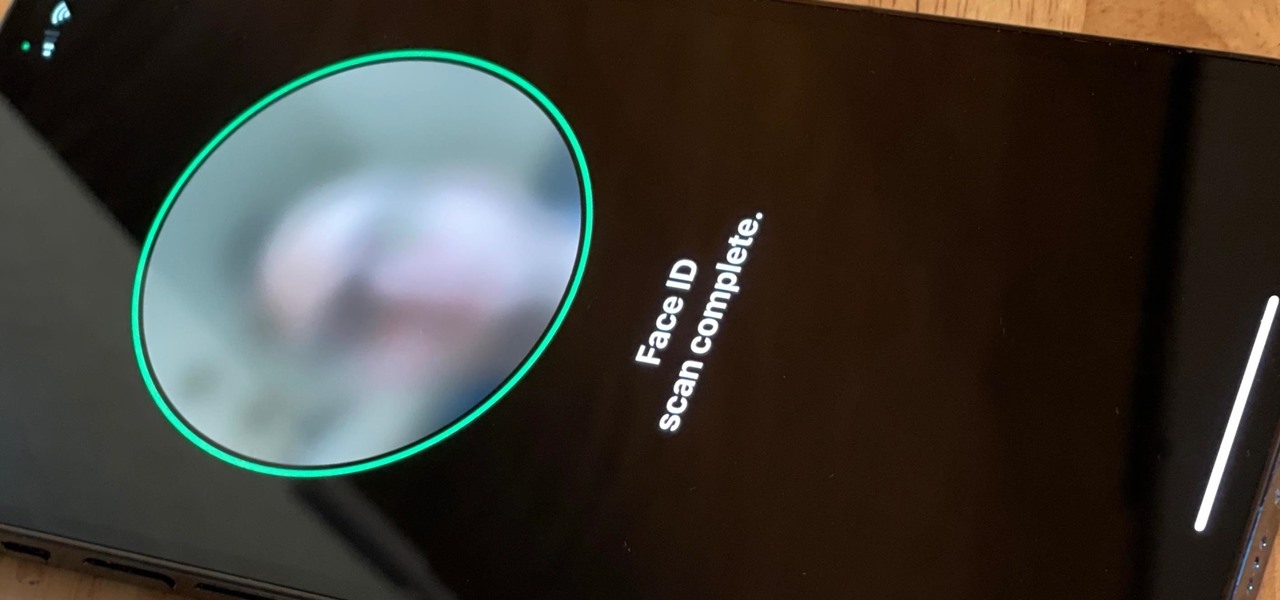
There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

Apple's latest iPhone and iPad software, iOS 15.5 and iPadOS 15.5, became available on May 16, so you can download and install it right now if you haven't already. While there aren't as many new features as iOS 15.4 and iPadOS 15.4 had, there are a few big ones in the U.S. you'll want to know beyond Apple's minuscule "About this Update" information in the "Software Update" menu.

With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

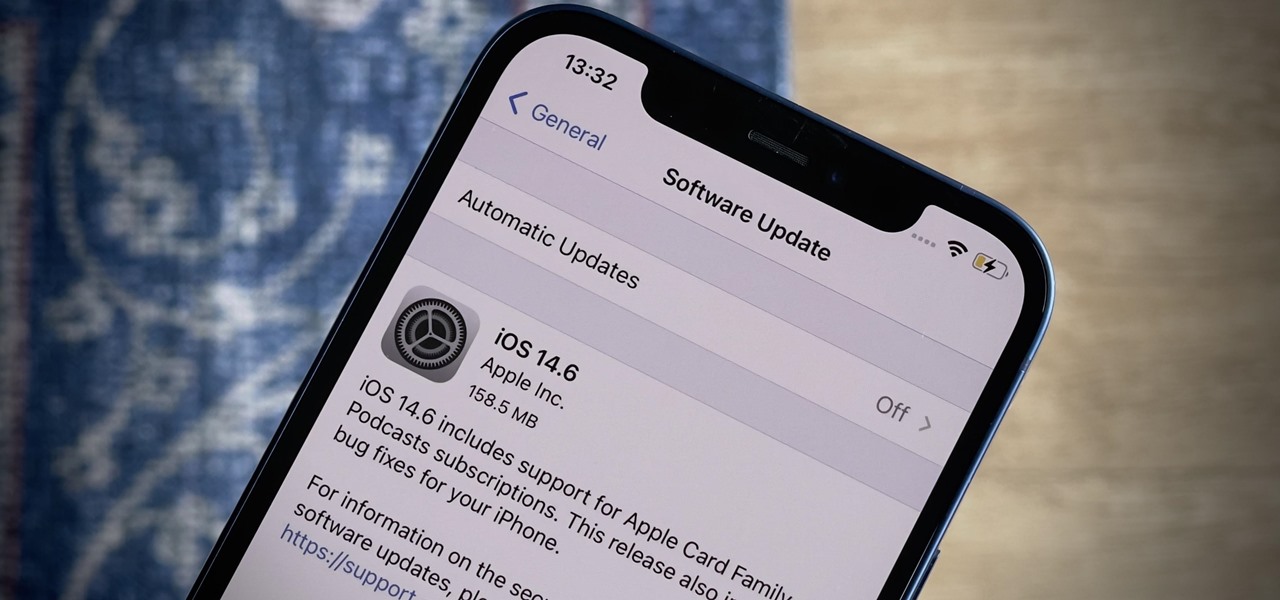
Apple released the latest version of its iPhone OS, iOS 14.6, today, Monday, May 24. This latest update (build number 18F72) introduces new features like unlocking your iPhone with Voice Control after a restart, Apple Card Family support for up to five people, and subscription support for shows in Podcasts.

Archie Leach. It just doesn't have the same ring as Cary Grant, does it? Marriage, divorce, or just dislike of the name your parents gave you – all are reasons to follow these steps toward a new name.
International Pet Travel: Taking Your Pet Animal to a Foreign Country If you are taking a pet to another country (permanently or for a visit), contact that country's consulate or embassy for information about any requirements that you must meet. A list of consulates can be found at Foreign Consular Offices in the United States

Eating fire is a guaranteed method of not only impressing an entire room, but also instantly settling any questions as to whether or not you're a complete and total stone cold BAD ASS. When you can casually whip this trick out in a bar, you're not only going to get your drinks bought for you for the rest of the night, but at least three phone numbers scrawled on the backs of napkins.

Why T-Shirts T-shirts are a great way for people to express themselves, and like other art forms, unique t-shirt designs are becoming more and more popular. Websites that specialize in just t-shirts are popping up all over the internet with tons of opportunities for designers, and artists from all over the world are now considering t-shirt design as a way to expand their portfolios and make some cash.

It's mid-January and some of you happy tax-paying citizens have already started receiving your W-4s and 1099s in the mail. But before you start filling out your 2010 Federal Tax Return, make sure you're hip to all the tax tricks in 2011. You could end up saving some money!

Follow Mark Amey's step by step guide to looking after baby tortoises. Tortoises are interesting pets but need committed owners as they can live for over 100 years. Care for baby tortoises so they live past that century milestone! Buy your tortoise from a reputable breeder or pet shop. Don't buy them over the internet as they may be sent to you in the post and won't be kept in safe conditions. If your tortoise has been legally bred it will come with a sales certificate known as Article 10 of ...

This video demonstrates how to set up an account at the iTunes store. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to set up an account at the iTunes store, For Dummies.

Announcement #1: Holiday season is here! Every Wizard101 account that logs in between December 21, 2010 and January 1, 2011 will receive a silent nightcap, which is different for both boys and girls! Merry Christmas and a Happy New Year!

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

Final Fantasy 14 the MMO is now live. The special edition priced at $75 enables people to play eight days earlier than people getting the regular edition, which comes out on September 30th. Mine arrived yesterday and here are some pictures of what's inside the special edition version of the game:

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

Ever had your car broken into? Or worse, your apartment? Ever been pickpocketed? Handheld electronics—iPods, iPhones, iPads, GPS devices, digital cameras—are easy to snatch, light to carry, and useful to most. And when they're gone, they're gone.