A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

This tutorial for PHP beginners introduces the viewer to the concept of class inheritance. As your coding career takes off, you'll need to know as many ways to work efficently and code with speed to save time and money. Check it!

Are you an aspiring fashion designer? Or do you just love drawing clothes and dresses? In this Hawks Vs. Pigeon Production, learn everything you need to know about drawing a dress form. Get that career as a fashion designer started now with help from this tutorial.

Job applications should be taken seriously, and filling them out with correct information, as well as specific details that make this application stand out, is an art form. Fill out job applications with tips from a career adviser in this free video on job guidance by following the instructions of the application, making it legible and addressing the value the applicant will bring to the company.

When evaluating multiple job offers it is helpful if you take the time to go over your options and determine what factors are most important to you in your career search. This how to video teaches you what to look for when deciding between several job offers.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

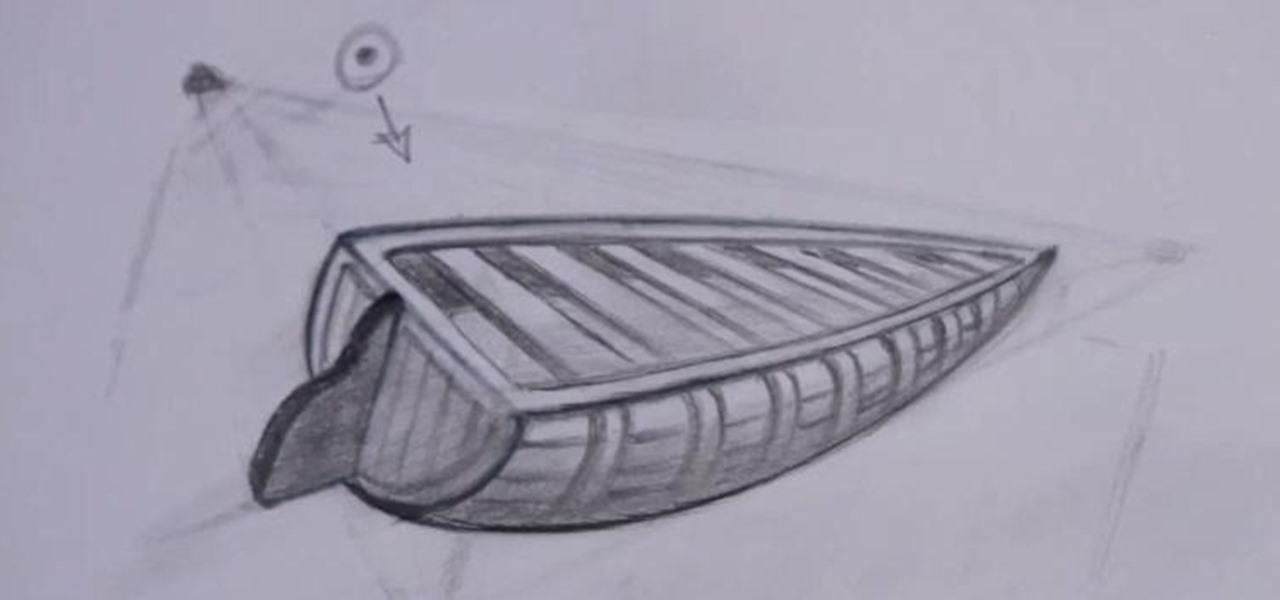
VCAD instructor Glen Kennedy, who has worked for several large studios throughout his career, including Disney, Universal Studios and Marvel Productions, introduces fundamental drawing techniques to encourage young artists to develop and hone their drawing skills. In this five-part drawing series, viewers can follow along with Glen to learn how to sketch a boat in two-point perspective.

Jean Grey was one of the five original X-Men, and is old enough to have gone through some major changes in her career. She's more recently been called Phoenix and Dark Phoenix, and that's what she's known as in her appearance in Marvel vs. Capcom 3. This video will show you the basics of how to fight with Phoenix / Dark Phoenix in the game, including combos and special moves.

The Jonas Brothers may be on their way out as they grow older and Nick Jonas embarks on his solo career, but for their fans their songs will always remain. This three-part video will teach you how to play a cool instrumental version of their song "Fly with Me" on piano, the ultimate expression of your love for the Jonas Brothers. Check out a written version of the song here.

Ernie from "Sesame Street" loved his rubber duckies. In fact, there was seldom a scene in his bathtub - or even outside of it - where he was seen without his beloved bright yellow rubber ducky. We think he may have even loved it more than he loved Bert (just kidding).

This video will teach and demonstrate the thyroid status assessment and thyroid gland examination in a patient. As a doctor, you will, at some point in your career, need to examine the thyroid gland in a patient's neck, and some other parts of the body which are effected by the thyroid.

In this video tutorial, viewers learn how to read a micrometer. This tool allows the user to accurately measure components. They have the ability to measure dimensions accurately to within one hundredth of a millimeter. Micrometers are designed with a wide variety of styles and sizes for normal or specialized applications. Micrometers are able to measure the internal or external dimensions of a component. They are the most important basic measuring instrument used in the metal industry. There...

Everyone's had one. It's how you deal with it that makes a difference. You Will Need

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Looking for a way to speed up the boot time on your favorite programs in Windows? This video will show you a little tweak to make your most-used applications start up in no time. Basically, you just go to the "Shortcut" tab in the program's properties menu. Then add " /prefetch:1" to the end of the target location in the "Target" box. This tweak works on PCs running Windows 7, XP or Vista.

In this Pets & Animals video tutorial you will learn how to train your dog to perform the "cop-cop" trick. In this trick the dog learns to put its feet on your feet. Step 1 – teach the dog to target a book or a mat with their feet by offering them some treat. You can do this either by appreciating or clicking when both the feet touch the book. The next step is getting the dog to target the book with their feet while they are between your legs. You have to continually reinforce the dog to ma...

Looking to work on your form? Try this free video golfing lesson for size. In short: When putting, to be able to release the putter down the line to your target, the club must travel slightly inside the target line. For a complete overview of how to become a better putter, watch this video guide.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

Consumers are chomping at the bit for augmented reality smartglasses from Cupertino's finest, but one market analyst is saying not so fast, Apple fans. Meanwhile, automotive AR is gaining speed, with the latest milestone coming courtesy of a major investment in waveguides by Continental. And although mobile AR apps have already arrived, retailer Target is taking a different approach. So why is Target tinkering with web-based AR? Answers below...

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.