Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

I'm one of those types of people who waits until the very last minute to find a Halloween costume, and thanks to last year's attempt at buying one at a local costume shop the day before Halloween, I will just settle for the things I have lying around in my house from now until eternity. It's like Black Friday chaos, only with more gropers.

Many of us experience highly emotional "freakouts", so to speak, more often than we'd like. Weather you experience them personally, or via your loved ones, it can be very difficult to think rationally during an episode, and for some people it can take quite a while to calm down.

It's a trick that never fails to amaze. You're placed in handcuffs, but with a flick of the wrist, you're free! Kick off your career as a daring escape artist with these simple tips.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?
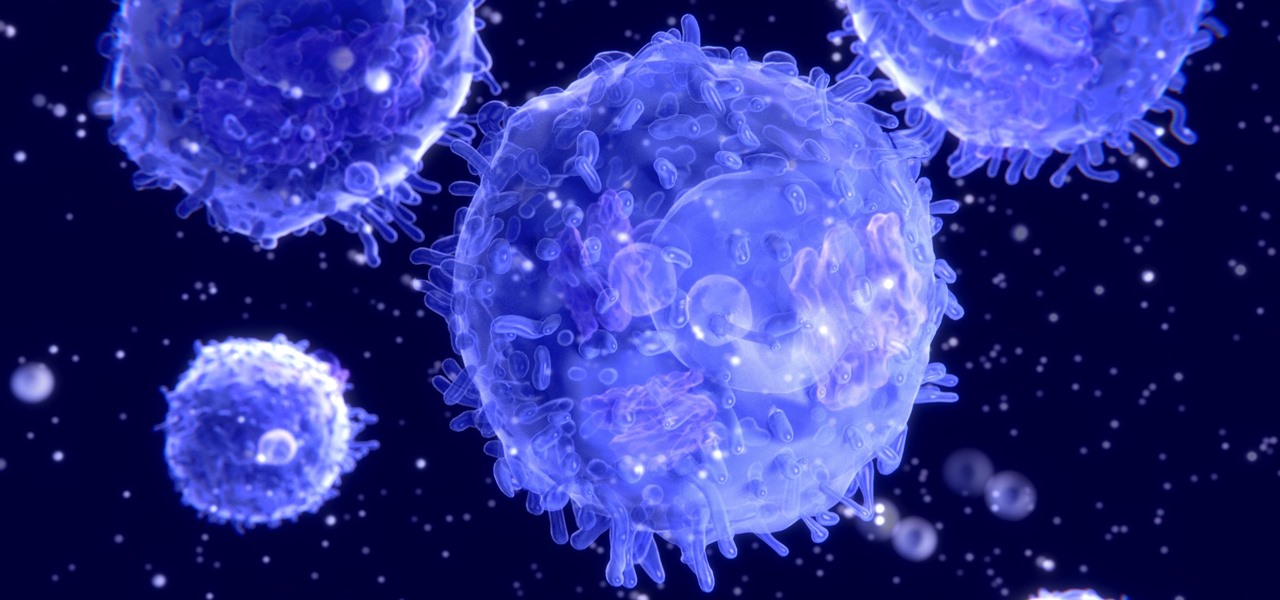
HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, they have been trying to figure out if the remaining HIV is the cause of or caused by increased activation of the immune system.

In the past, creative chefs and bakers have been rewarded for their daring in the kitchen with viral attention from the internet—like the rainbow bagel or cronut. These sensations weren't crafted for the sake of going viral, but ended up generating an insane amount of buzz anyway.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

Cookbook author, celebrity chef, television personality, and former White House nuclear policy analyst Ina Garten is familiar to many as the queen of foolproof cooking. Also known as the Barefoot Contessa, Ina hones in on techniques and tips that make time in the kitchen far less intimidating to folks of all skill sets. We've rounded up 8 of Ina's most useful cooking tips to help you out—from dinner parties to everyday cooking. Her philosophy is that it's always easier than you think!

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

If you've beaten Year 1 - The Sorcerer's Stone of LEGO Harry Potter: Years 1-4 on the Xbox 360, then get ready for the LEGO-ized version of J. K. Rowling's second masterpiece, Year 2 - The Chamber of Secrets. Get every single achievement, every single collectible… everything you can imagine. All the videos and levels are listed below.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

The face tracking of cats and dogs are probably my favorite AR innovations that have come to Snapchat Lenses over the past few years.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

Virtual private networks, or VPNs, are popular for helping you stay anonymous online by changing your IP address, encrypting traffic, and hiding your location. However, common IoT devices, media players, and smart TVs are hard to connect to a VPN, but we have a solution: Turn a Raspberry Pi into a router running through PIA VPN, which will ensure every connected device gets the VPN treatment.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Acclaimed Cinematographer Adam Kimmel Arrested:

This video tutorial will show you the process of drawing blood from rats through the saphenous vein and by cardiac puncture.
Multiple airport screeners have been arrested for allegedly taking handsome bribes to look the other way while loads of illegal drugs slipped through security at Los Angeles International Airport, federal officials announced today.

George Clooney has since been released after paying a $100 fine for trespassing. Clooney was among the group of congressmen and activists arrested for ignoring warnings and crossing a police line outside the embassy

This Guy Has My MacBook is a gripping tale for iOS nerds far and wide, documented via interaction designer Joshua Kaufman's tumblr. When Kaufman's MacBook was stolen from his apartment in Oakland, CA, on March 21, 2011, he quickly activated Hidden, a previously installed app that enabled Kaufman to collect photos of the thief, as well as screen shots of the computer in use.

Anonymous hacktivists announced via Twitter that they had successfully hacked the website of New York Iron Works, a police-equipment supplier, and replaced the homepage with a tribute of love to arrested hacker and Chicagoan Jeremy Hammond.
Here are some topics that I will we working to bring to the site sometime soon. The death of Andrew Breitbart - Co-Incidendce?

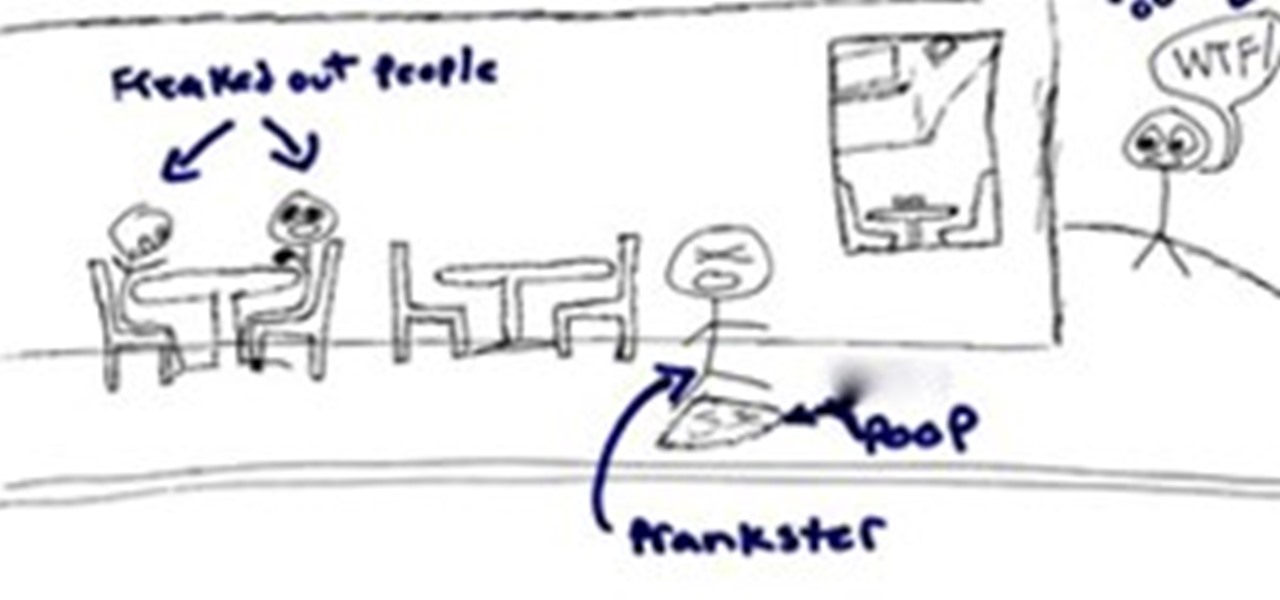
The main idea behind this prank is to have the publics attention/reactions in the city. Get people dressed up as old men