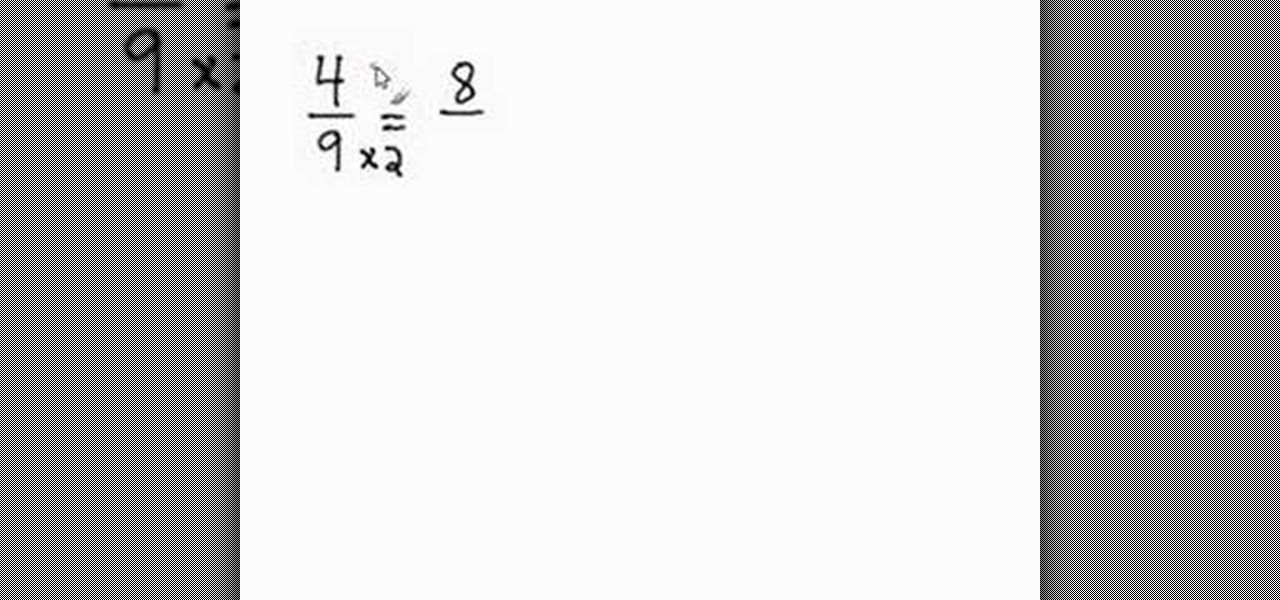We seldom see Kim Kardashian on camera - whether it's formally at a red carpet event or just being captured by the paparazzi while shopping - without a full face of makeup and perfect ringlets in her locks.

Ninjas has captured the imagination of both East and West with a combination of flair, combat effectiveness, and secrecy unlike any other type of warrior in the world. In this three-part video you will learn how to draw a rather muscular example of the group, holding a massive sword and adorned with shruiken, in pencil.

In this video tutorial, viewers learn how to record audio, using Camtasia Studio 6. Camtasia Studio is a screen video capture program. The user defines the area of the screen or the window that is to be captured before recording begins; it is also possible to capture the entire screen area. You can also talk, and use a videocam. Begin by selecting the Camtasia Studio icon in the taskbar. Right-click it and select the sound option. When the window pops up, enable all the options to be able to ...
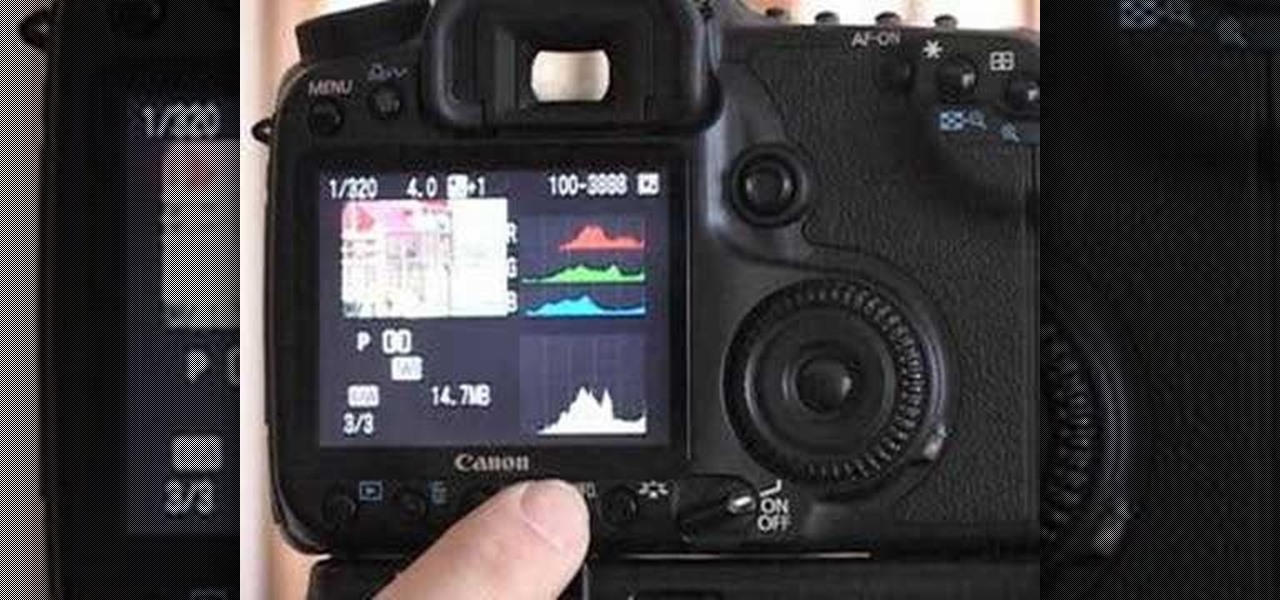
A video from Graham River Productions, presented by Shannon Smith, explains how to interpret Histograms on modern Digital Cameras. Just because a captured image looks nice on the camera screen does not mean that it is really good. One of the better checks for quality of a photograph is the histogram display that is available on many modern cameras. Histograms accurately tell whether the full potential of the the camera's optical sensor has been utilized or not; and are the tools of choice for...

This video demonstrates an Easter egg on the iPhone that enables you to take a screenshot of the iPhone. First, navigate to the website or menu page that you need to capture as a screenshot and capture the screenshot by pressing the buttons as shown in the video. That is it, the captured screenshots can be found in your camera roll. Make sure to have your iPhone in the desired orientation before taking the screen-shot. This can be used for capturing web pages for future reference as well.
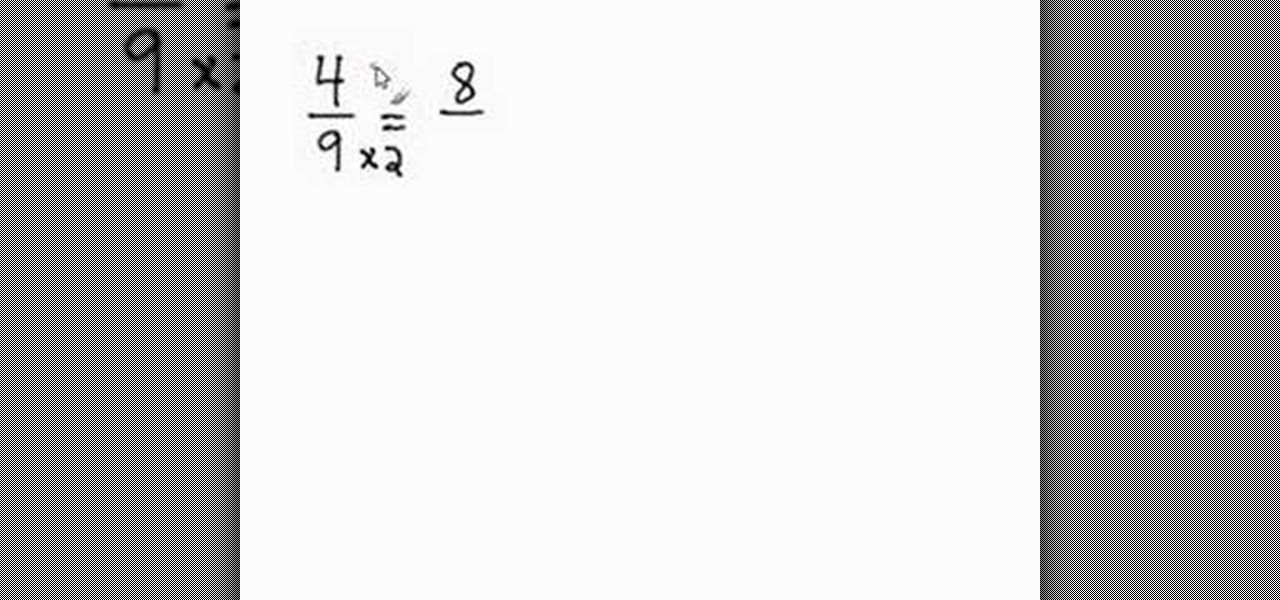
A representative from Math Problem Generator explains in this video that converting a simple fraction from its current state to a higher equivalent can be very simple. He explains the process neatly and provides a great example. To convert a fraction, you must multiply the numerator and the denominator by the exact same number. The example he shows is captured from the screen of a computer and is written out in some sort of a painting program. The example shows that four-ninths equals eight-e...

This shows you how to install an app for the Apple iPhone that records video. You have the capability to record video. The hardware is there. It's simply a deficit of software. Both the iPhone 3G and regular iPhone can record video with the right iPhone App. Here's what you need to get video captured with your phone.

Lisa shows us how to clean up spilled candle wax using an iron and a paper towel, a trick from Japanese Urawaza.

This how to video shows us how to clean up spilled egg yolk using salt. Avoid a slippery sticky mess with these great cleaning tips.

Joy and Gracie show us how to make a newborn infant stop crying and sleep in peace using a wine tasting secret. This is a Japanese Urawaza trick that uses the white noise of a gurgle to ease a baby's cry.

This how to video shows us how to fix a scratched cd or dvd using toothpaste. Don't throw out that scratched cd or dvd, just fix it with this DIY home project.

In order to create a custom caption box in WordPress you'll need to go to your dashboard. Here click on appearances, then on editor. Now over on the right select the sidebar option. Here you'll see some code, what you need to do is find the word that you want to replace on the main page, you can use ctrl+F to find the word. When you've found it within the code just replace it with whatever you want and then press the 'apply' button. You'll see that the main page will now be displaying the wor...

The video shows us how to use audacity to record audio. Firstly you need to have the software audacity installed in your system and for that Google and search for 'audacity' and after that you get a link to save and install the software. Once the installation is done, open audacity and on the drop down menu the default is set to microphone, change that to stereo mix and copy my settings. Once this is done we will be recording the audio. Go to a site like youtube and press the record button in...

This chess tutorial from Grandmaster Alexandra Kosteniuk is a perfect example of Retrograde Analysis.

Learn how to do stability ball pike ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Thanks to modern "smart phones" and the internet, media by the people, for the people is finally a reality. Here's how to use your phone to be a mobile journalist.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Video: . Steel wool fire Photography

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

The latest augmented reality feature from The New York Times gives readers a close-up view of the damage left behind by the eruption of Volcán de Fuego in Guatemala earlier this month.

Google's Chromecast streaming device is a marvel of functionality and form. Even with powerful features such as screen mirroring and collaborative party playlists, it's the device's idle screen that first catches the eyes of most folks.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

Just a day after the release of the iPhone X, the music-meets-comedy pastime known as Animoji Karaoke quickly emerged as one of the popular (albeit frivolous) features used to justify spending $1,000 for Apple's newest smartphone.

Now that Fyre Festival co-founder Billy McFarland is charged with fraud, this is the perfect time to list off those top 15 influencers who promoted tickets to the disastrous event to their loyal followers, right?

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

The art of taking secret photos is one that requires keen awareness and skill. Not only do you need to ensure that your subject remains oblivious, but you also need to make sure that no one near you notices what you're attempting to do. It's great when you buddy is acting a fool, but sucks when they stop their shenanigans when they notice you pulling out your camera phone in an effort to evade your picture.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

The Galaxy S5's camera is amongst the most capable smartphone shooters on the market. With a 16-megapixel sensor that is capable of recording 1080p video at 120 frames per second, the stat sheet was officially stuffed when Samsung brought this device to market.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!