Balsamiq is a really cool software suite that allows you to create Apps visually without having to write any code! This two-part video lecture will introduce you to Balsamiq and show you how to use it to create your own cool Apps. If you want to learn Balsamiq, you really couldn't do any better than this.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

Cyanogen, Inc., the for-profit company that spun off from its CyanogenMod roots several years ago, has announced that they're shutting down all of their services. The company's impending demise shouldn't directly impact many Android users, but the announcement does have one major repercussion: The servers that used to host the popular CyanogenMod custom ROM have now been shut down.

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Proud new papa Gjoci wanted to make sure he never had to worry about whether or not his baby girl was breathing, so he built this amazing breath-detecting baby monitor using a Wii remote, a printed circuit, and a laser. First, he opened up the Wiimote and took out the camera, then used an Atmel Atmega88 microcontroller to make a printed circuit. Low-power infrared lasers shine on the baby's clothing and the Wii camera detects the motion of the baby's breath, activating an alarm if the motion ...

When you use a scanner to look for error codes on a car, many can show up at once and confuse you as to the nature of the problem. Often, all of the codes are responses to the same problem. Watch this video for tips on interpreting multiple error codes.

Interested in learning how to code and create a modern website from scratch? Let this eight-part video tutorial series be your guide. It's easy and this series presents a complete, step-by-step overview of the process. For more information, including detailed instructions, and to get started creating and coding your own website groups, take a look.

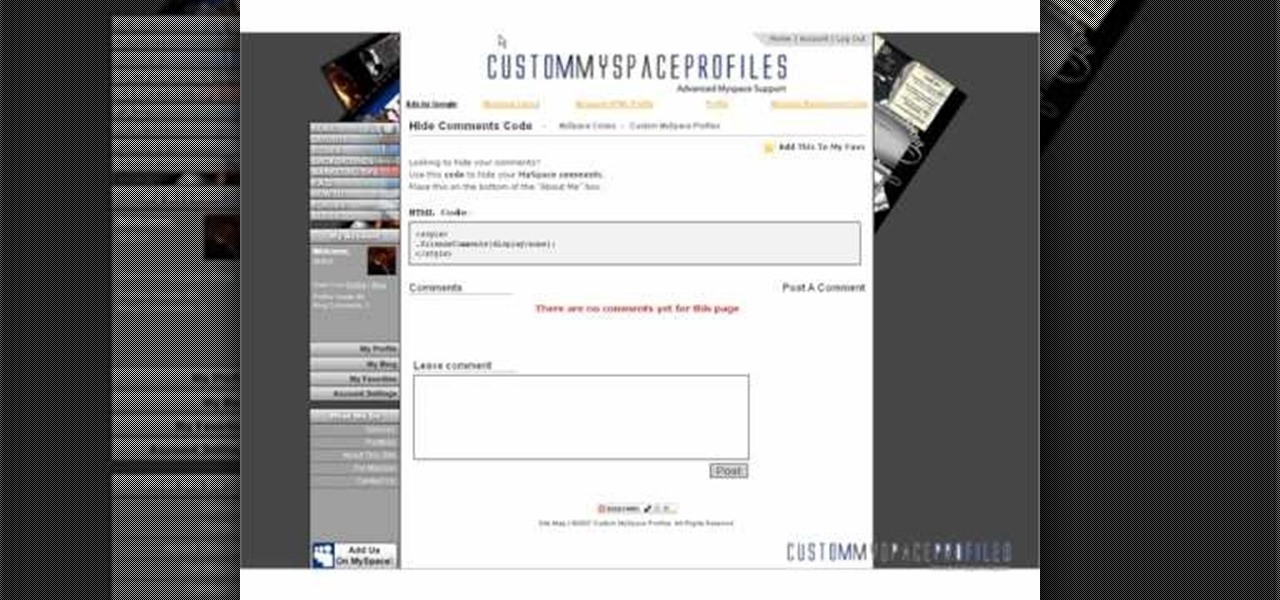
This tutorial will show you how to hide your MySpace comments using the custom MySpace profiles website. All you have to do is visit the website mentioned in the video, and copy a simple code in the codes section. The code that you will be looking for in the list is the 'Hide MySpace comments' code. The code is then pasted in to your MySpace profile under the 'About Me' section. If you follow the directions entirely in this tutorial, your MySpace profile comments will be disabled until you re...

You've seen code blues called on TV, but how about in real life? If you are becoming a nurse it is important to know what goes on as part of a code blue situation. This nursing how-to video presents a mock code blue presentation with faculty. Follow along and learn what is involved in caring for a patient that has gone into code blue.

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!

Add a chat program to your website and allow the logged in users to talk to each other! You can write this program using Adobe Flash CS3, PHP and MySQL. This tutorial shows you how to write your own Flash chat program incorporating all three systems.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.

The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

We all know that color coding is important because it helps us to quickly organize things based on visual cues. As students in high school, we used differently colored page tabs to denote different subject matters, and some of us color code file cabinets for easier and faster access. The same principle goes for this tutorial, which teaches you how to color code a knitting loom.

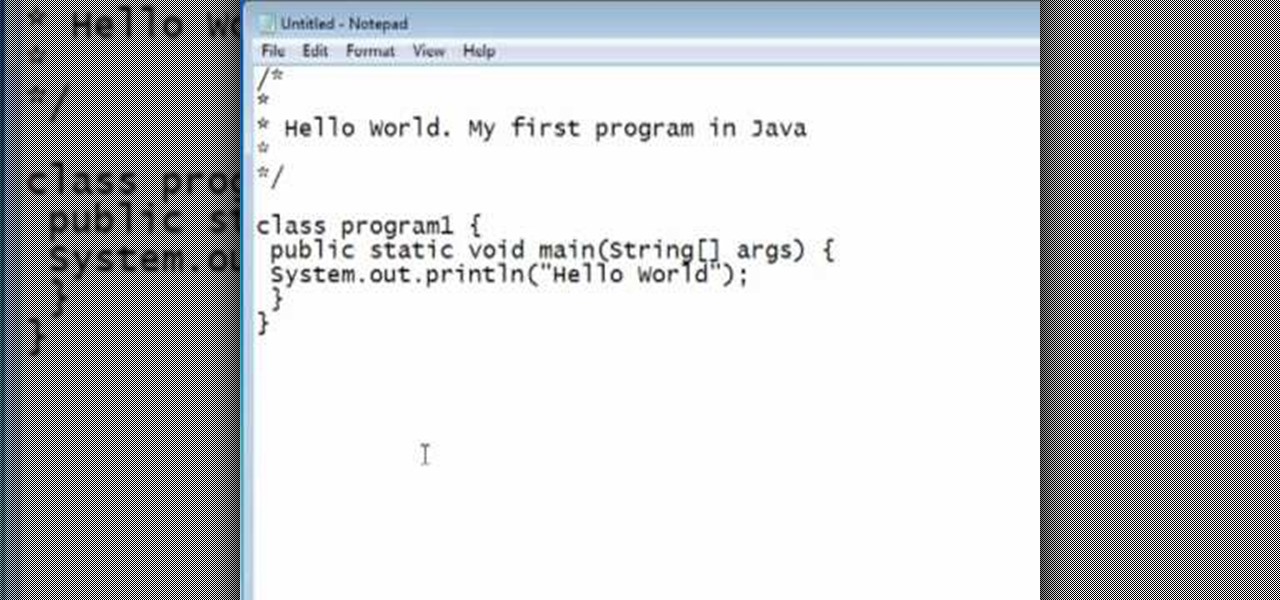
You should already have the JDK installed on your computer, and you should already have optimized your computer's settings. See How to install the Java Development Kit to start programming to do that if you haven't already.

Almost every video on YouTube is embeddable. Only those that choose not to feature an embed code or non-embeddable. This embed code can be accessed directly on the video page of the video that strikes you. If you want to embed it, simply click the "Embed" button underneath the video player to generate the embed code. You can tweak this embed code to better serve you and your WordPress blog or website. It will generate the code automatically, and you can grab it and use it for yourself. This c...

Arceus is a legendary God Pokemon released on Pokemon Diamond/Pearl. Arceus can be caught without Action replay codes but this video will show you exactly how to access and catch Arceus in Pokemon Diamond using codes from Action Replay.

In this video tutorial, learn how to unlock (or jailbreak) your Blackberry, with these step-by-step instructions. This video also shows you how to get a IMEI Unlock Code from "Unlock To Talk", however, this code costs money. You can access a code here.

If the speedometer on your car isn't working and the check engine light is on, get your scanner out and look for code P0500. If you get that code, watch this video to learn a quick easy fix for the problem.

Just because your car shows an error code doesn't mean you should pull any parts. This video will show you how to confirm error code P 0340 on a Nissan (Bad Cam Sensor) by using a lab scope to check the cam sensor.

Despite being on the Xbox Live Arcade and PlayStation Network, Scott Pilgrim vs. the World: The Game is actually a pretty hard video game. But, things get a whole lot easier with this cool play modes available with a few secret cheat codes. This video tells you those cheat codes to enable zombie mode, boss rush mode, and two others in the XBLA game.

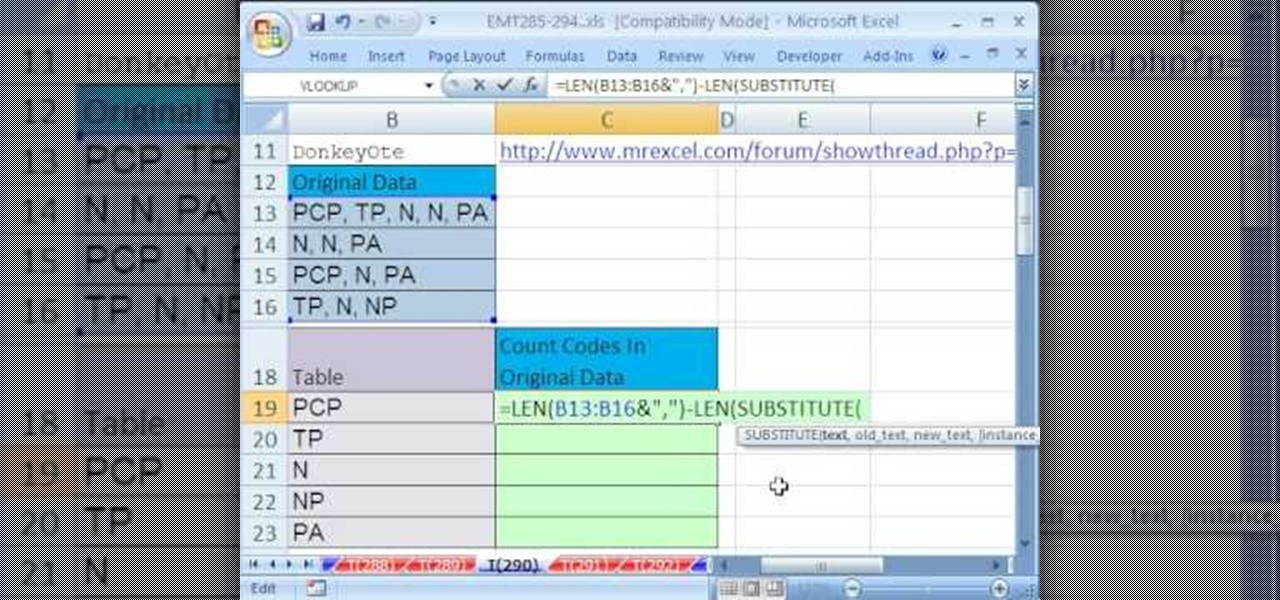
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 290th installment in their series of digital spreadsheet magic tricks, you'll learn how to count codes from a column of text strings that have multiple codes.

This video describes Resistor Color Codes and how to read them. It relates Resistor Color Codes to scientific numbers and engineering notation.

A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Windows Powershell is a powerful but unwieldy tool for web developers, with which the PowerGUI interface is a great means on interacting. This video will show you how to use SnippetManager, recently declared "Best Add-On" in "PowerGUI Challenge 2010", to create and manage code snippets to use in your projects.

If you are the proud owner of a Dodge Neon with a check engine light on and it's showing error code P0141 on your scanner, you probably need to replace the rear oxygen sensor. This video will show you how to do that as easily as possible.