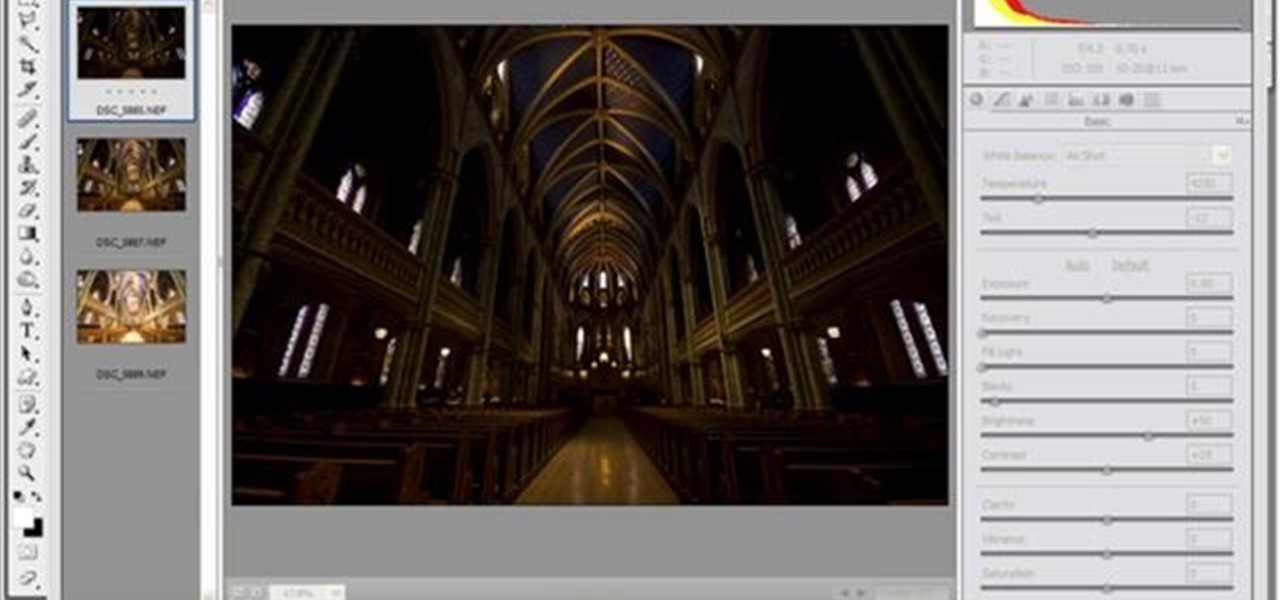
Yanick's Photo School demonstrates how to use Photoshop to make HDR images in Photoshop CS3. This tutorial first explains that HDR means "High Dynamic Range" which is a process to get details from a photo from both the highlights and shadows of a particular scene. The first thing that is necessary is to take multiple views of the same image with different exposures. To start off, you will take three exposures: one that is two stops down, one that is normal exposure, and one that is two stops ...
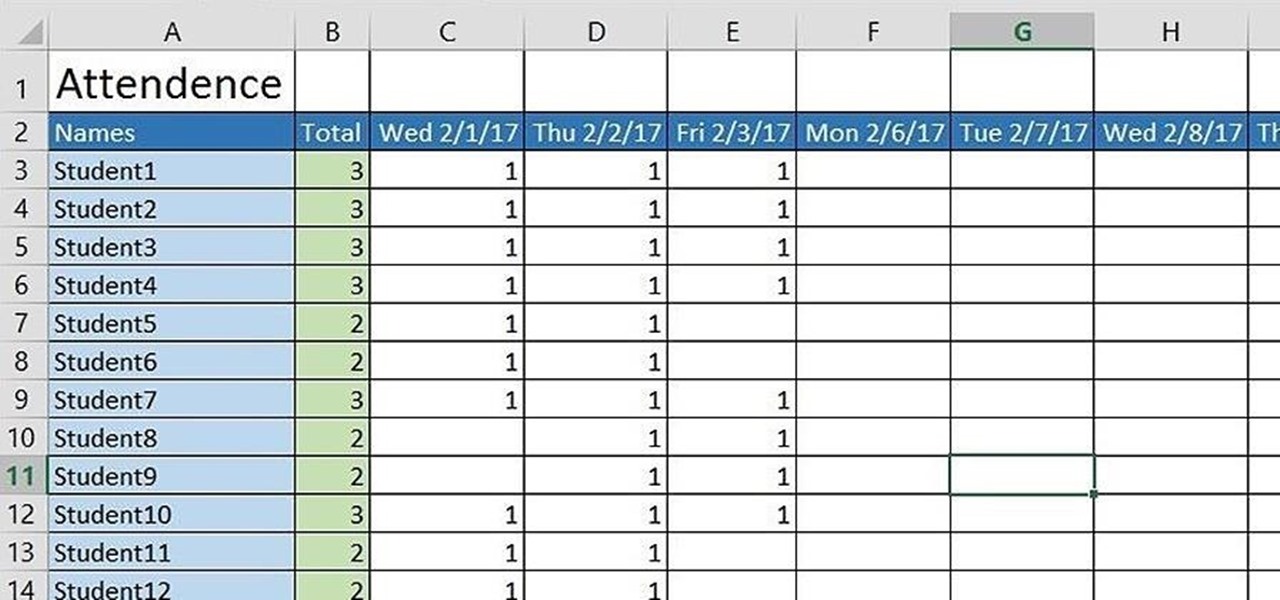
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

In general, smartphones and cars don't mix—but this is mainly because you have to take your eyes off the road to poke around on your handheld gadget. In reality, the only difference between your smartphone and your car's FHWA-approved infotainment system is that the latter is mounted in a fixed position and has an oversized interface that makes it easy to use without looking away from the road.

If you're tired of the default yellow link colors in your Notes app, which I find hard to look at in light mode, there's a way to change them to another color on your iPhone, iPad, and/or Mac.

Though not as flashy as Face ID and other features, Low Power Mode has become one of the unsung heroes of iOS. When you're away from a charger, enabling this feature will dial back performance and networking to help you eke out up to three extra hours of battery life. If your device is jailbroken, you can even automate Low Power Mode to ensure your battery never dips to critical levels while out and about.

Bob and Brett explain all about automation options when using Pro Tools. Automation is a way to allow volume control and automate fade rides etc.

Jeff Schell shows you some of the options and configurations available when working with images that do not match the dimensions of your program monitor in Premiere Pro CS3. In addition, Jeff will introduce you to the 'Automate to Timeline" feature that helps you quickly create a photo montage or slide show with the click of a button.

Since its launch in 2009, Google Apps Script has given creative thinkers the ability to perform light-weight application development within GSuite. Based on JavaScript, you can build your own simple tools that will increase your efficiency and productivity.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

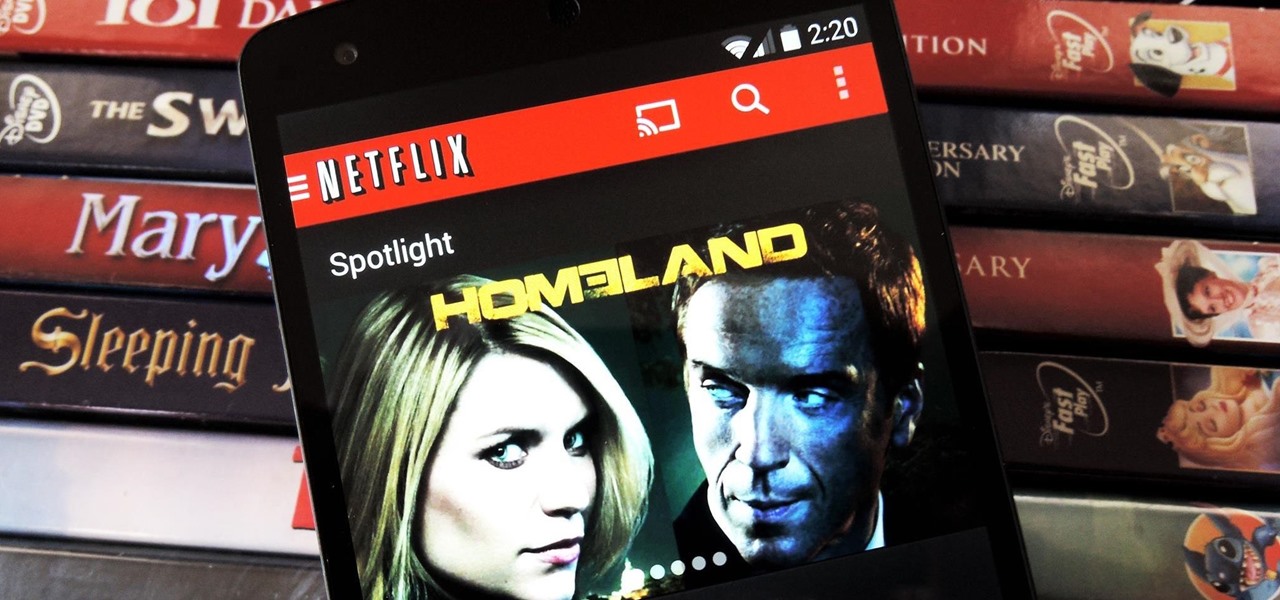
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

When they first appeared, smartphones came with a promise to make our lives easier and make us more productive so we could have more free time and energy. But now, the average user spends almost 5 ½ hours daily on their smartphone. If that sounds like you, there are ways to use your iPhone more efficiently — without getting sucked into distractions.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

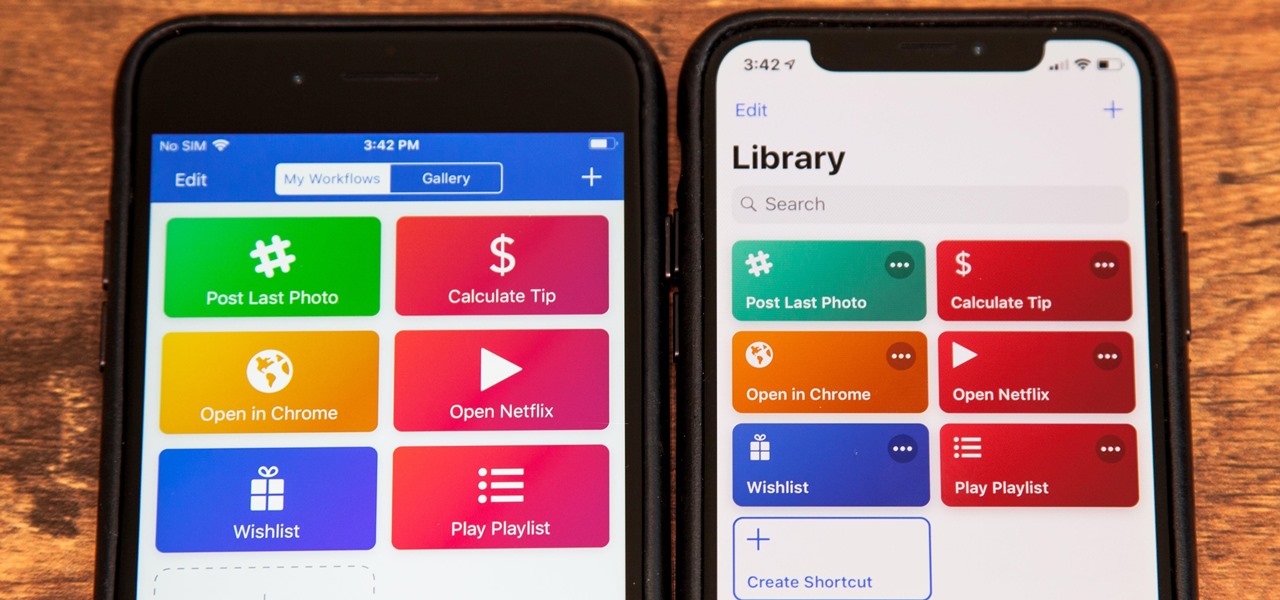
Apple's testing a new app for iOS 12 called Shortcuts, and it has a lot of overlap with their existing Workflow app. So much overlap, in fact, that Workflow won't be sticking around for much longer.

Perhaps the best thing about Android is the endless amount of customization you can add to your device. From icon packs to custom launchers and even custom ROMs, there's truly something for everyone. One of the most popular options among Android enthusiasts is adding a system wide dark theme. The methods to do this vary, but you can now automate this process thanks to Android Oreo.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

There aren't many iPhone apps that let you change their color theme beyond light and dark appearances. They really don't need to either because iOS has a few hidden tricks up its sleeves to help you customize any app's colors either during a specific session or every time you use the app.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

If you tend to use the app switcher a lot to open recent apps, then all of the apps you accessed months ago are just sitting there cluttering things up. While force-closing all of the recent apps on your iPhone isn't really necessary, it's sometimes nice to wipe the slate clean and empty the app switcher completely to start fresh.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

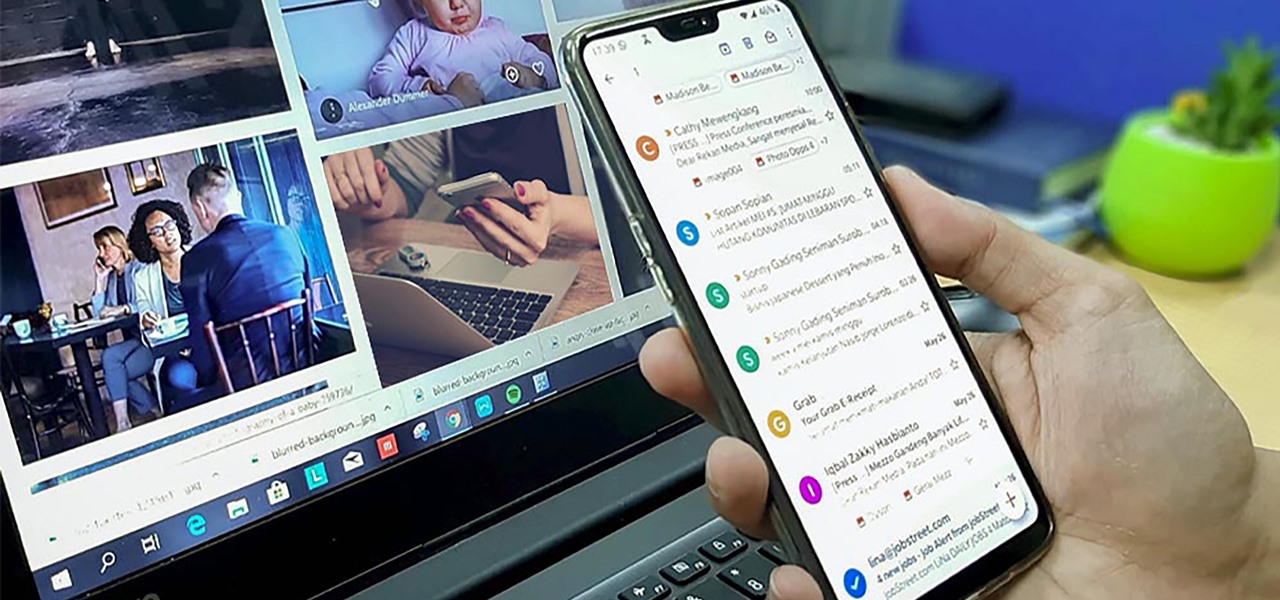
You send out a lot of emails, but probably get very few responses. How can you be sure those emails are even opened?

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Rooting, bootloaders, custom ROMs, CyanogenMod, ClockworkMod... it's all pretty confusing, isn't it? You're not the only one having trouble with this. Many users in the Nexus 7 SoftModder forum have been scratching their heads at these many terms.

If you're anything like me, you use the Calculator app on your iPhone like fifty times a day, and you're sick of the same user interface it's had since iOS 11 came out. While you can't mod the button shapes and sizes, there is a way to breathe new life into your calculations with some Calculator theming.

The life of a busy entrepreneur isn't easy. In addition to coming up with original business ideas and marketing strategies, you also need to be continually thinking about investors, overhead, the competition, and expanding your customer base — often with a limited budget.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

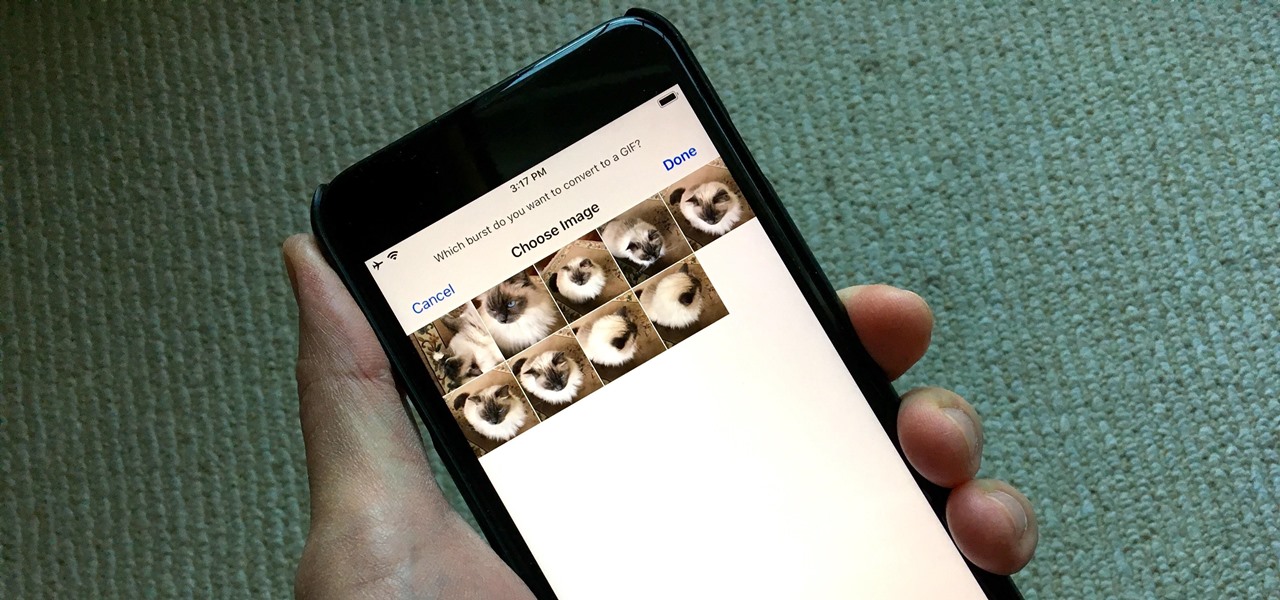
Creating GIFs of your own burst images has been possible for a while with third-party iOS apps, some of which cost money or include in-app purchases to utilize the full potential. Fortunately, with Shortcuts, Apple's automation workflow app, there's finally a native way to achieve this without spending any cash.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Before you head to class, work, or sleep, you're probably doing the same thing over and over again—toggling off system settings like Wi-Fi, sound, data, or brightness, depending on the circumstances. Schedules and routines can help increase efficiency, so while you abide to a particular schedule, so should your Android.

Personally, I know life would be a lot easier if the people in it could just read my mind. Since that technology is currently unavailable, it's comforting to know that your air conditioner can be your personal telepathist with Sensibo.

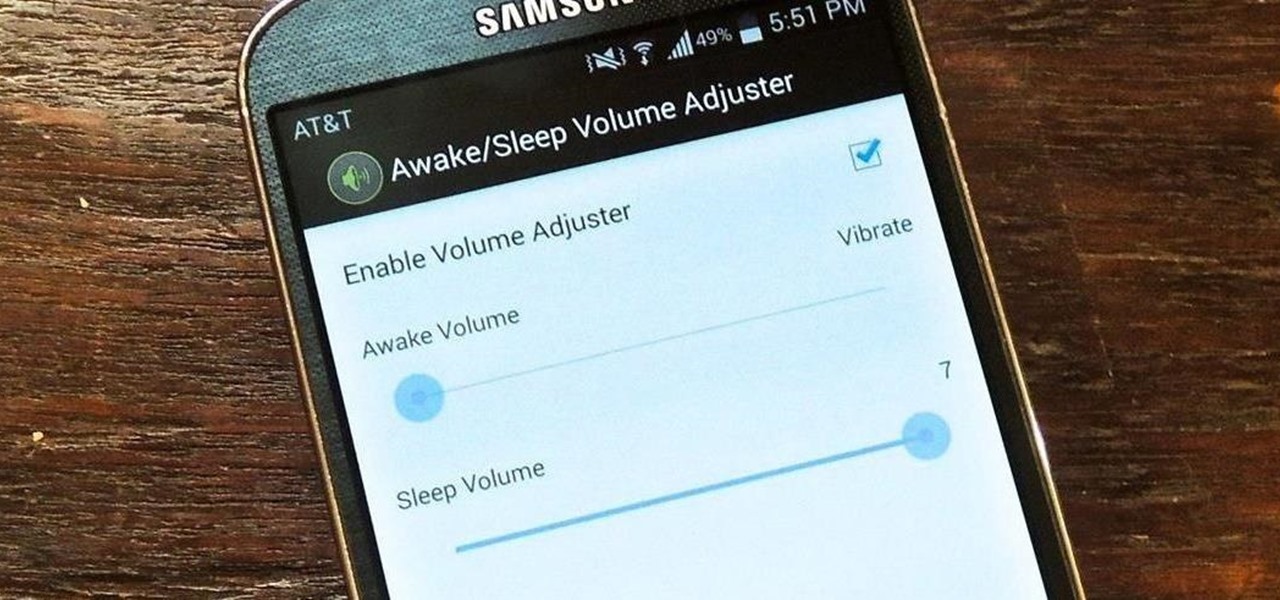
When I'm not actively using my Samsung Galaxy S4, I typically crank the volume up all the way so I can hear it in my pocket or if I'm in another room. But when it's in my hands and I'm using it, I don't want the ringer to blast at full volume, or any volume at all. Either I'll see a notification come in, or a quick vibrate will call my attention to any pertinent alerts.

You can use Twitter to print Instagram photos, track news and weather events, or even remotely shut down your computer, and if you're familiar with IFTTT, there's no shortage of ways your account can help automate your life.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.