
Market Reality: Magic Leap Seeks Series E Funding, Apple Delays AR Headset, & Snap Starts Selling Spectacles 3
The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.


The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

The day has finally arrived — Samsung has unveiled the Galaxy S9 and S9+. Apart from minor upgrades, the two might not appear to be much different from last year's S8 and S8+, but that's not necessarily a bad thing. One feature that hasn't changed is the Galaxy's IP68 water-resistance rating. That's a great score, but it begs the question — what does that number really mean?


When filtered through the prism of the top stories of the year, the business of augmented reality 2019 was defined as much by epic failures of AR startups as it was by the promising developments that propelled the industry forward into 2020.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

Apple just made its most significant update ever to the iOS lock screen, with a lot of features to be excited about. The theme of this upgrade is customization, giving you complete control over the look and functionality of your iPhone's lock screen.
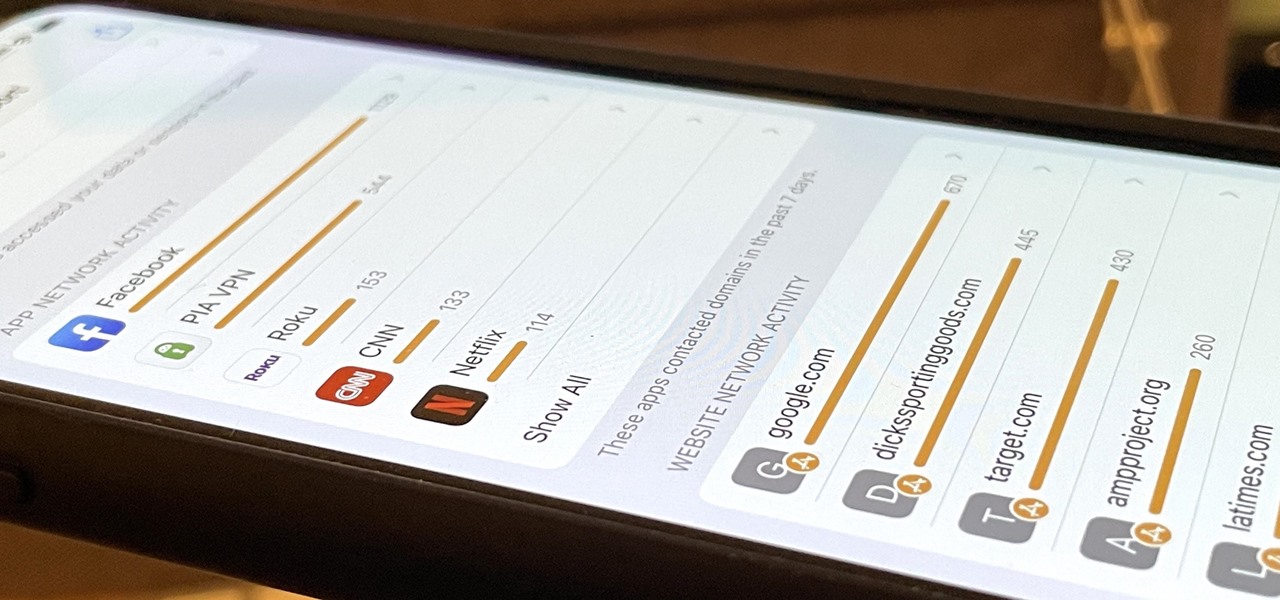
With the holidays right around the corner, it's easy to miss a big software update on your iPhone, and by that, I mean iOS 15.2, which was pushed out Monday, Dec. 13. There's a surprising amount of new features and changes in the updated firmware, and there are a few big ones you need to know about.

The Alt-Tab keyboard shortcut makes switching between apps and programs a breeze on your Windows PC. Just like your computer, your Android phone has the same feature baked in to make switching between recent apps just as hassle-free.
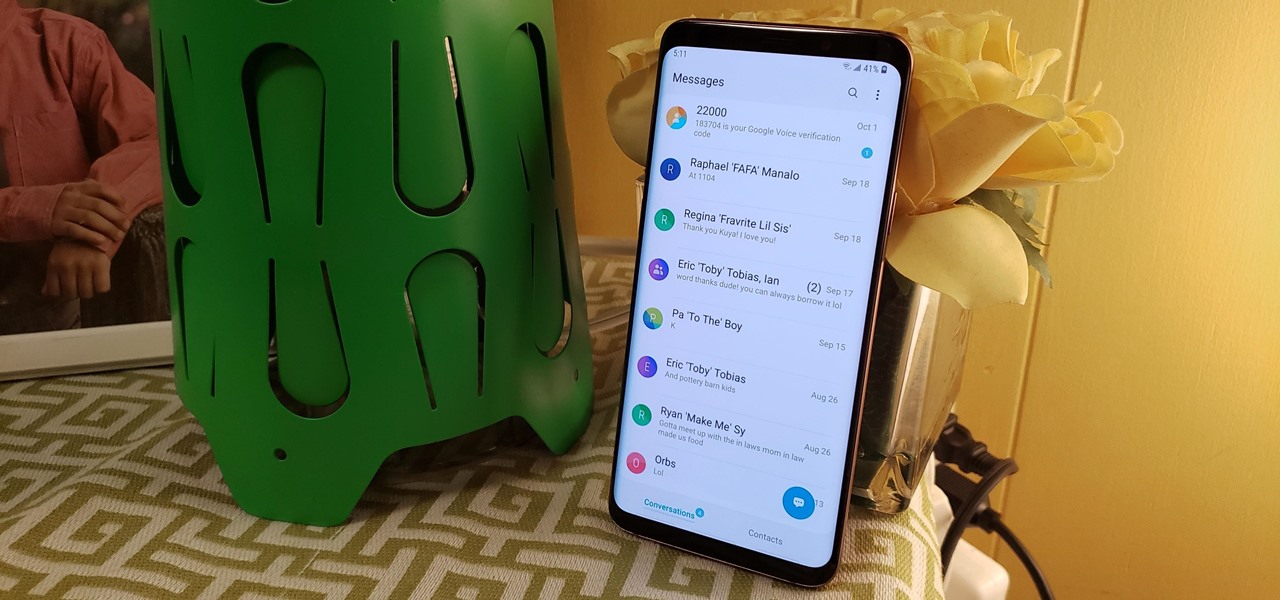
Samsung's version of Android Pie has landed on Galaxy handsets like the Note 9, S9, and S8, though we've known what to expect thanks to leaked beta versions of the software a few months back. The newly dubbed One UI has plenty of new features and improvements, but some of the first you might notice are the visual improvements to the default messaging app.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

When it comes to augmented reality apps, visually immersive experiences are plentiful, but audio experiences are somewhat underrepresented. A new app for iPhones and iPads seeks to shift the AR paradigm toward the latter.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.
We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

Your iPhone might have a great camera, but it can be irritating to get things like exposure and focus right when your fingers are all over the 'viewfinder.' The Pictar aims to change that by making your iPhone as much like a DLSR as it can, keeping your fingers from obstructing your next great photo.

Taking pictures, sharing your location, and making calls are easy enough to do with an Android device, but for the most part, they all require your screen to be on with some sort of swiping and pressing actions. Dedicated shortcut keys are virtually non-existent on any modern day phone, but their utility is something that can be very useful.

Jotting quick notes can be a pain. There have been countless occasions where I've needed a pen and paper to quickly write something down, but either didn't have them near me or was doing something on my phone and neglected to remember.

An isomorphic (or self-transposing) keyboard is "a musical device where a grid of notes is displayed to the user and the interval change between notes in constant for any given direction." For those of you who didn't grow up playing the piano like I did, that basically means that it lets you move between keys easily without having to learn new patterns because the keys are laid out so that a chord is the same pattern in every musical key.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

The App Library is an excellent tool for browsing all the apps on your iPhone, especially since it includes every one of the home screen bookmarks you've made for websites and shortcuts. But it's all the way past your last home screen page. If you have a lot of visible home screen pages, that's a lot of swiping to open the App Library. Luckily, there is a trick to accessing it faster.

When you're playing a game on your iPhone, the chances are good that you'll come across an ad you have to watch before you can continue — especially on free games. While it may be annoying to be forced to wait for 10 seconds or even up to a full minute, it can be even more frustrating when you accidentally leave the game to visit the ad's linked app or site when trying to hit the little "x" to continue gaming.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Android Pie has finally made its way to signature Galaxy devices like the Note 9, S9 and S8. As you all know, Samsung Experience got a major makeover and has been renamed to One UI, featuring significant aesthetic changes to many of its native apps.
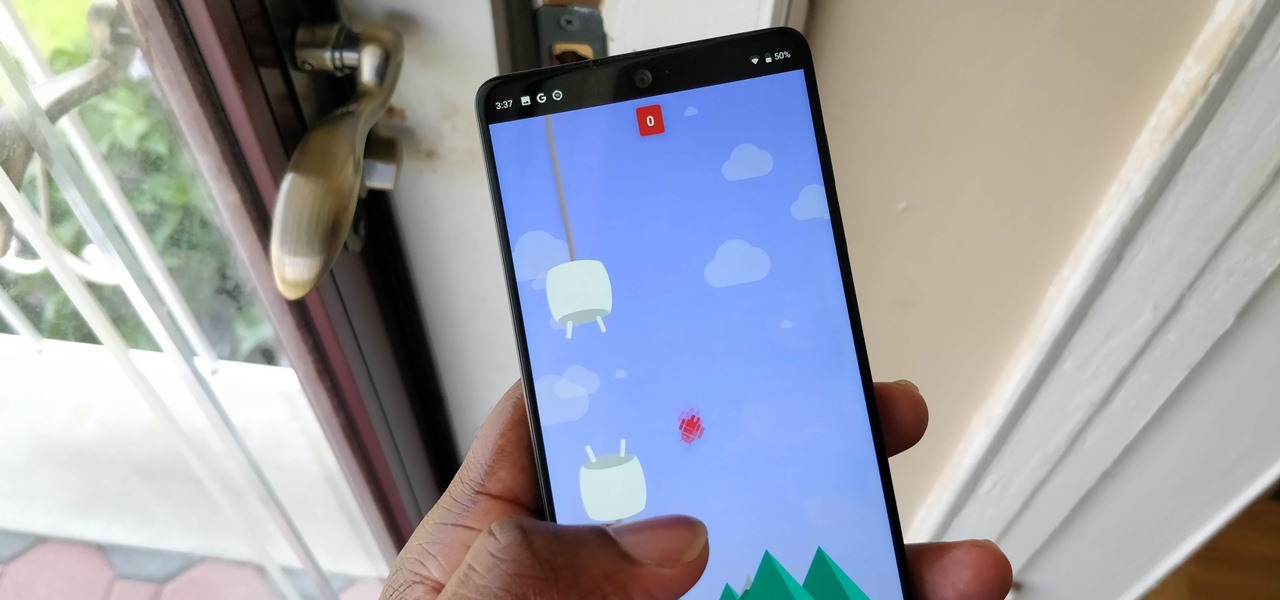
The famous Flappy Bird (technically Flappy Droid) game is still around in Android 9.0 Pie. First introduced in 5.0 Lollipop, the game was originally the version number easter egg for the new Android update. But after Android Marshmallow, Google began to hide it from its usual location, and Pie continues this tradition.

Augmented reality headsets with depth sensors, like the HoloLens, offer a much more immersive experience than the average smartphone at present, and one app demonstrates that in a uniquely entertaining fashion.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.
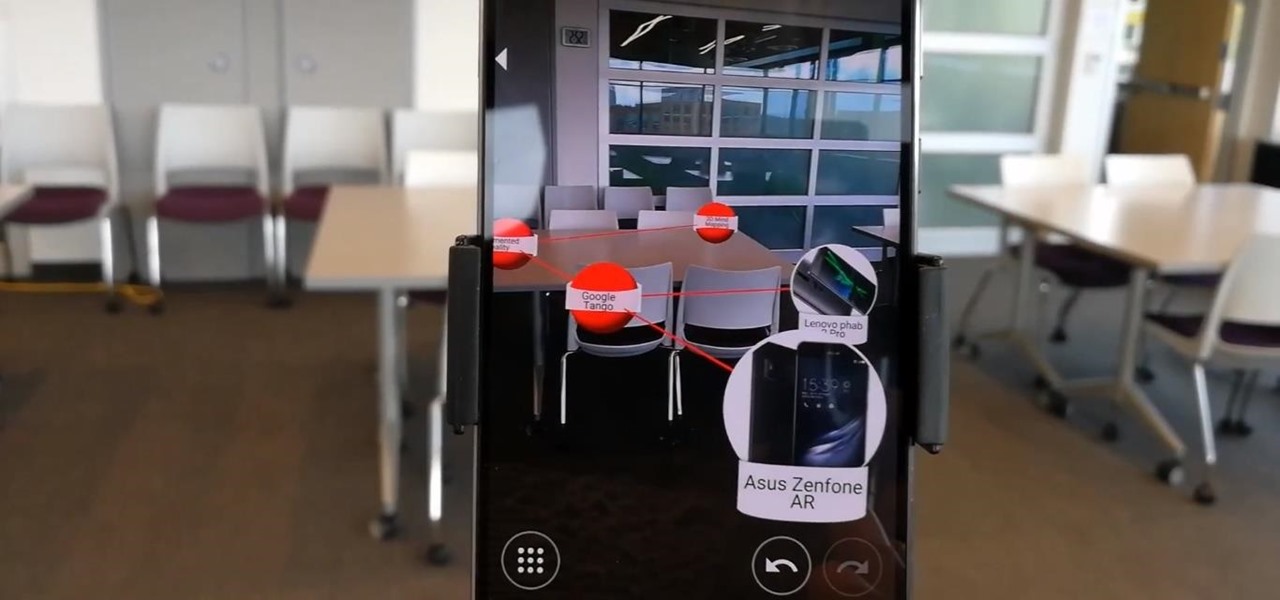
When Google announced its ARCore augmented reality toolkit for Android as its answer to Apple's ARKit for iPhones and iPads, the question from many observers was, "What about Tango?"

The HoloLens is the world's first untethered holographic head-mounted computer, which Microsoft has been rather proud of—and they have every reason to be. Of course, as soon as we developers get adjusted to the idea of keeping the scope of our projects inside the bounds of the HoloLens' processing power, Microsoft hits us with the Holographic Remoting Player.

Rooted users have been able to remap their hardware buttons since the earliest days of Android, allowing them to change the functionality behind one of the most centralized methods of interacting with a phone or tablet. Up until now, however, non-rooted users have been left out in the cold, meaning these buttons could only perform the functions assigned to them by the device manufacturer.
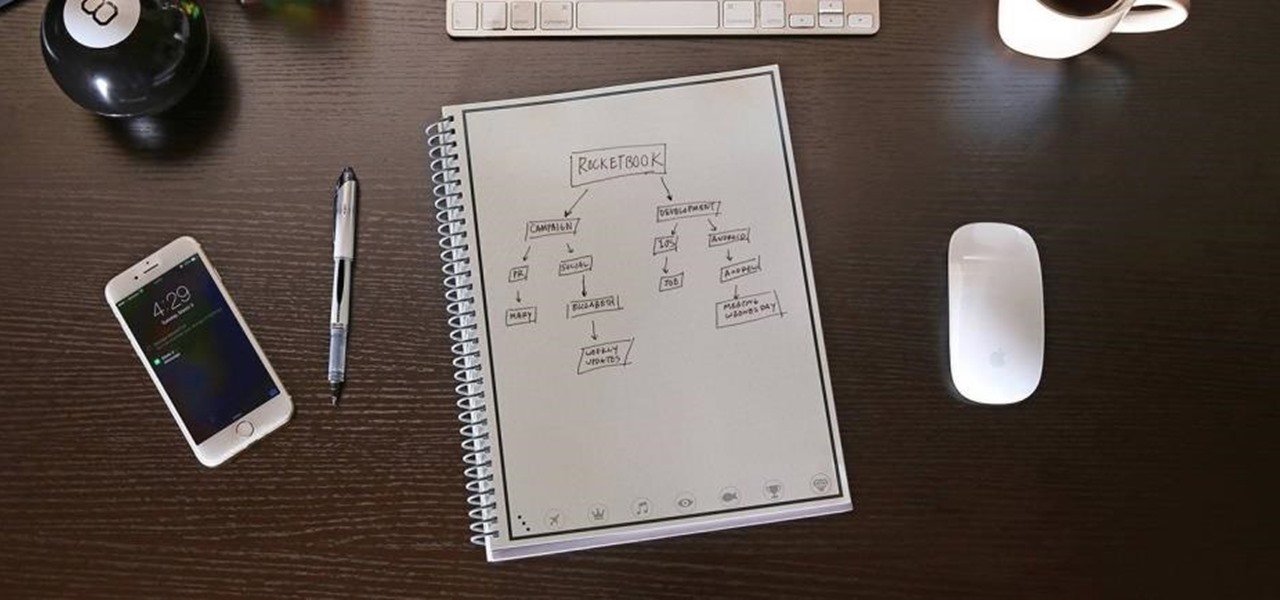
Pretty much every note you save on your computer, phone, or tablet can be uploaded to your cloud and viewed on any of your devices. But what about those notes you write down on actual paper? Well, those notes can also be cloud-friendly, thanks to the Rocketbook Wave.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

Hello again, ***UPDATE: Adding links to the other Two articles****

I'm a long-time and loyal Android user, but one iOS feature that I'm truly envious of is their keyboard shortcuts, which lets you assign a short macro that inputs a longer phrase. For example, typing "home" can input your home address.

If you've ever noticed, even just for a fleeting moment, that the auto brightness on your Nexus 5 seemed to "glitch out"—you are not alone.

Dianne Tice and Roy Baumeister gave a bunch of college students a questionnaire in which the students answered questions about their work habits. In a class which she taught, Tice also assigned a paper with a deadline which she said could be extended and observed which students availed themselves of the option to extend.