Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

If you have a hard time remembering what you've just read on your iPad or Kindle, try changing the font next time. The typeface you use to read books, newspapers, and online articles is either hurting or helping your memory, and you'll be surprised which ones are killing your brain cells.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

The most used and most washed articles of clothing are undergarments. Underwear, specifically bras and panties, are in desperate need of attention after each and every use. They're not like a pair of jeans, wearing them twice in a row is not a good idea, nor clean. Shabby’s not chic when it comes to lingerie. Use a little extra care to keep your lace and silk bras and panties looking good.

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.

Apple News. Facebook. Twitter. Reddit. LinkedIn. These are just a few of the apps you probably have on your iPhone or iPad that keep you up to date on today's events. Unfortunately, they can also cause information overload. But a new viral speed-reading tool thinks it can help you process your daily news more efficiently.

It's almost impossible to use Apple News at night without having to mess with the white point and zoom filters. That might sound a bit dramatic, but it's really not when you consider that iOS 13 has a perfectly good Dark Mode that should work for News. So why are we stuck reading most news stories in Light Mode? We're not, but you have to put a little work into it going dark in News.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

Brought to you by Chevy. Video: .

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

How heavy is a plastic bag? Not very heavy at all, but in order to use a plastic bag to help me karate chop a thin wooden stick, I don't need weight—I need air pressure. Below, the "Quick Clip" demonstrates the power of air pressure via the vacuum created between a plastic bag and the countertop.

In this "Quick Clip," I tried dunking inflated balloons into a container filled with liquid nitrogen until they were completely flattened and seemingly destroyed. Once out of the liquid nitrogen, the balloons come back to life and reinflate on their own—without even touching them!

This science experiment deals with sublimation of dry ice into carbon dioxide (CO2) gas. In the video, I'll demonstrate how pushing a quarter into a block of dry ice makes the quarter scream and shake vigorously.

This quick video demonstrates the classic experiment of making a paperclip, or multiple paperclips, float on water.

If you have read any of my previous articles or viewed the many videos I have published, it's quite clear that I appreciate a good rocket or fiery projectile. The following video will certainly not lessen that reputation.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

No one can deny that Bashar Al-Assad’s regime has been responsible for violence. But in failing to equally acknowledge the fact that NATO-backed rebels have also carried out innumerable atrocities is not only dishonest, it represents a deliberate effort by the press to manipulate the narrative of unfolding events in Syria as a one-sided war crime rather than the truth – which is the fact that Syria is in a state of civil war.

Despite the controversy over Scrabble Trickster across the word world, Mattel's modern take on the classic crossword board game is out in stores— but not in the United States. It's only available in and around the UK, but you can snag your copy just in time for Christmas from Amazon UK. You can also visit the official Scrabble Trickster website. I imagine this is going to be a hot item in the United Kingdom this holiday season, but as for me— it's the one Scrabble game I refuse to add to my c...

All of these four videos are excellent. You will notice that while all the videos and articles have slightly different design dimensions, they are fundamentally very similar. I urge you to view and read everything I am serving up. Then, my final words of advice are simply....choose between a barbeque switch and a taser gun. (Hint: there is a right choice, and there is a wrong choice.)

While the iPhone world's attention might be fixated on Apple's upcoming iOS 14 and all of its new features, it's still in beta. What's not in beta anymore? Apple's latest iOS 13 update — iOS 13.6 — which dropped on July 15.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Everyone who owns or runs a website needs to know how they can improve traffic, and search engine optimization is the answer. This 13-part video series on SEO basics and strategies will give you more traffic for your site. It's jam-packed full of tons of great SEO tips! Check out each video in the series:

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

I may be a bit weird, but I enjoy listening to music at night as I fall asleep. Sure, you could create a playlist of songs so that it stopped after all the songs finished playing, but I have a rather extensive database of music and I enjoy listening to them randomly. Also, I like to ensure it terminates after a specific amount of time (I don't want it playing all night). Or sometimes I use it when I am cooking so that when the music stops, I know I need to check on my food, etc.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

We've been expecting the latest Android Pie update for current Samsung flagships like the Galaxy S9 and Note 9 for some time now, but Samsung's running behind schedule in the United States. Thankfully, it appears that One UI has finally started rolling out for some lucky S9 owners.

While there are over 100 cool features iOS 12 has to offer, there are some things Apple has made more annoying on iPhones or just has not addressed yet.

Usually paper beats rock. With augmented reality, The Rock beats paper. Using the Life VR app for iOS or Android, Entertainment Weekly readers can point their smartphones at the cover of the Dec. 8 edition to view a holiday greeting from Dwayne "The Rock" Johnson, star of the forthcoming reboot, Jumanji: Welcome to the Jungle.

Following the most recent election, some argue that increasing political polarization is dividing Americans. A new app, called Read Across the Aisle, is aiming to combat this by encouraging users to read news from media outlets on both sides of the political spectrum.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

Unlike in the physical world, on the internet you're actually able to shut people up and block spoilers of newly-released movies, your favorite TV shows, or a sports event you've yet to watch on your DVR.

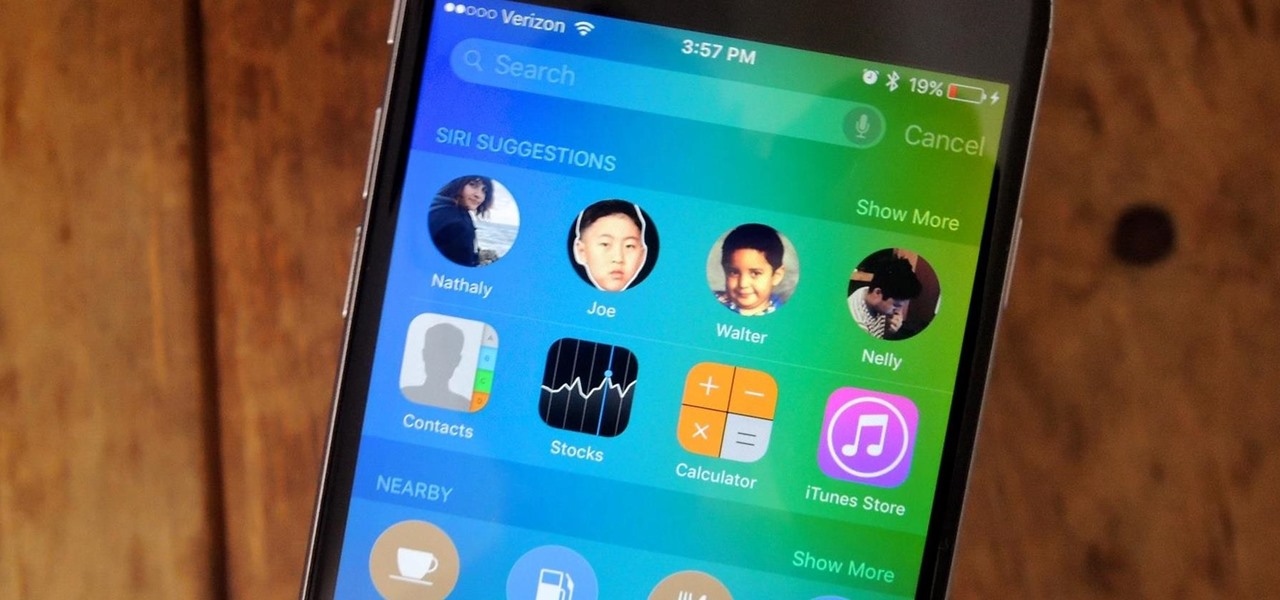
Apple certainly took a page from Google Now with its new "Proactive" search page in iOS 9. Located to the left of the home screen, the page provides quick access to contacts you've recently corresponded with, suggested applications, nearby places, and news articles based off of your Safari activity.

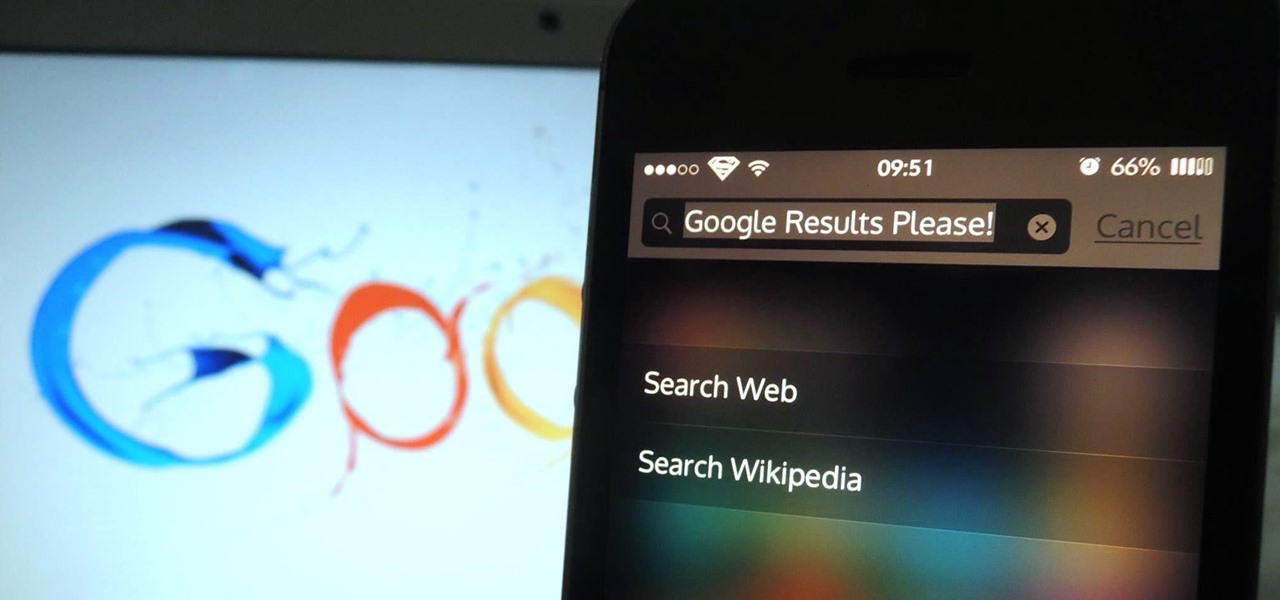
Spotlight makes finding apps, contacts, emails, songs, and old messages extremely easy on an iPad, iPhone, or iPod touch. You can even search for Wikipedia articles online, as well as perform general web searches.

With over 500 million downloads on Android alone, I find it safe to assume that most of us use the Chrome Browser on our mobile devices; it's great for reading articles with Reader mode enabled, syncs open tabs and bookmarks across all your devices (as long as you're signed in to your Google account), and is regularly updated with new features and optimizations.

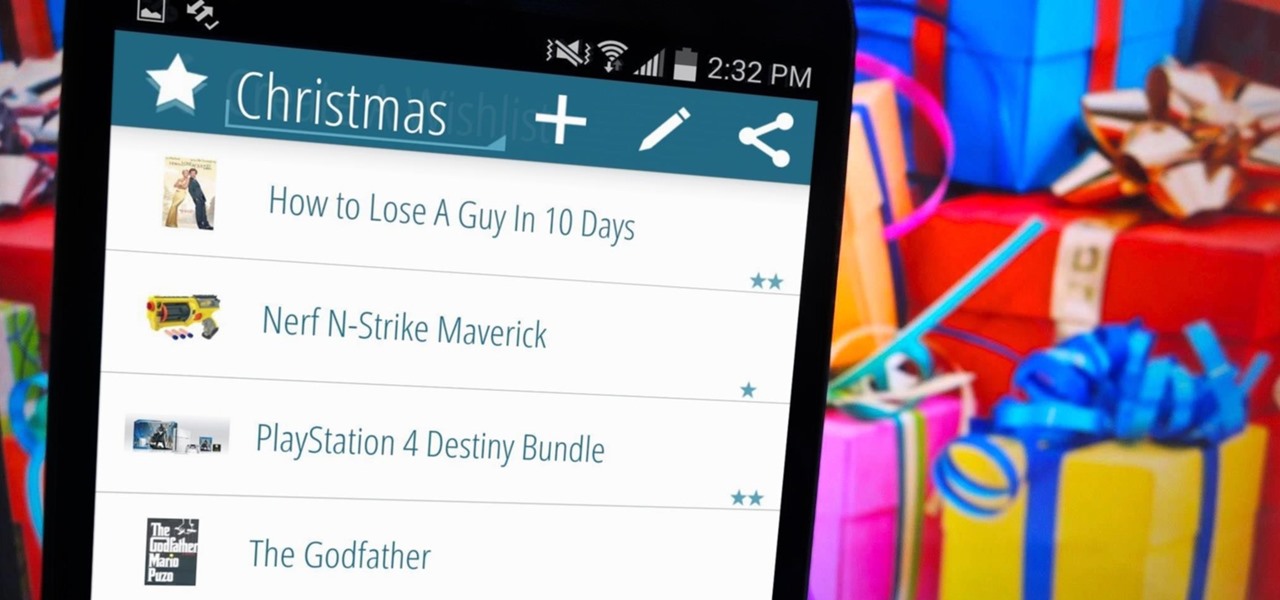
I love the holidays, but man am I sick of receiving oversized sweaters as Christmas presents. As well as people think they know us, their gifts often say otherwise. Instead of stocking up on useless items and articles of clothing you'll never wear, it's high time to create a wish list that's easily sharable amongst family and friends, and it's incredibly easy to do on Android.