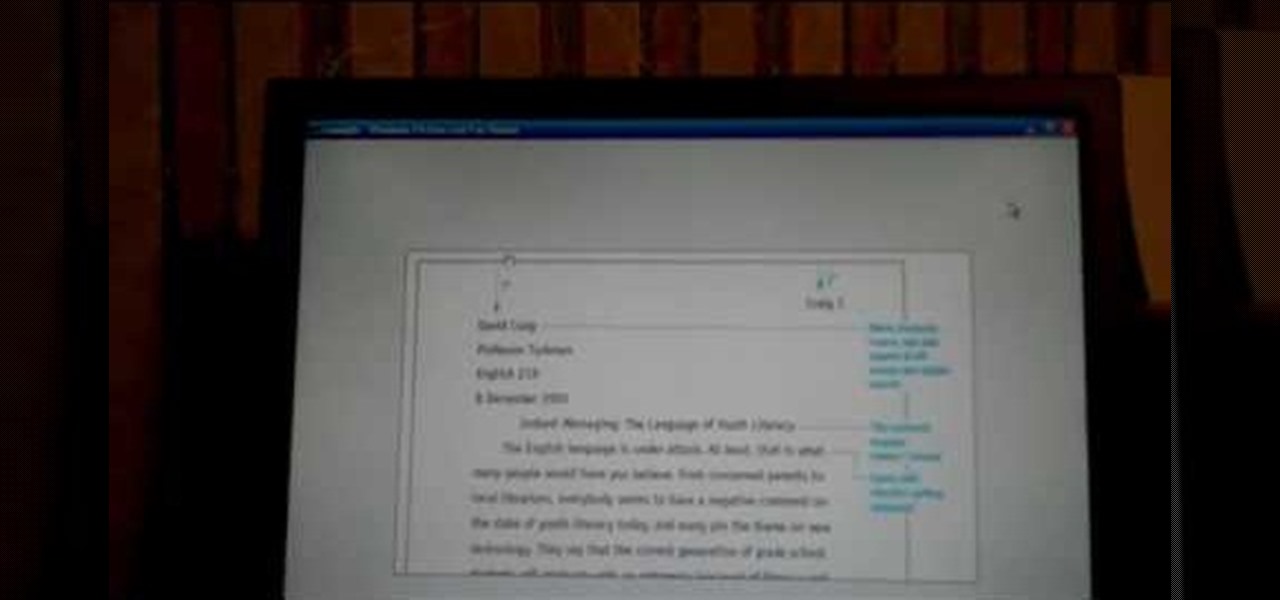
The video demonstrates how to get started with MLA (Modern Language Association documentation format) for an article. One of the first things that is important to understand is how to name your paper, and add a header format that will automatically paginate your paper so that you do not have to worry about it. The entries in your Works Cited need to be alphabetized and also need to be indented. Note that there is no extra space between the entries. You do not have to know how to manually form...

This is a DrawingNow.com video tutorial of how to draw Kenshin from the "Samurai X" anime series ("Rurouni Kenshin" is the title in Japan). The tutorial begins with a blank page and demonstrates, stroke-by-stroke, how to sketch out the basic structure, and then builds on this to produce the finished article. The drawing has been carried out using the tools available on DrawingNow.com's own drawing applet, but the same steps could be done in any drawing program which supports layers. The tutor...

You can't have a werewolf movie without a werewolf, but how do you make one. Well, you should start of small. Try your hands at the wolf claws. To create these furry werewolf claws, you'll need a glove and some other materials. Watch this video tutorial to learn how to make a breakable prop computer. For written instructions on the actual claws, check out the WikiHow article, "How to Make Origami Paper Claws".

Check out this informational safety video that provides a few motorcycle safety tips. This video was created to encourage safe motorcycle riding. Warning! This video contains SERIOUS motorcycle crash videos! Here are a few safety tips to keep motorcyclists safer. The contents of this video are paraphrased & condensed from a motorcycle magazine article. Avoid severe injury and death by learning a few basic motorcycle safety precautions.

You'd like to treat your friend to a drink from the vending machine, but you only have enough cash for one soda. What do you do?

Everyone in the world uses tablets these days, so it's no wonder that the Samsung Galaxy Tab has different languages built right in. To change your language on the Android tablet, all you need to do is navigate to the Settings menu.

First go to your Wordpress admin and click the "custom file editor" in thesis options. Now copy that code which is showing in the video and paste it in the custom.css file and click on the big green save button. Now select

This is a great quick and easy recipe and a great healthy alternative to store-bought frosting. My husband and children love this frosting, and it's also a hit at my PTA meetings. It goes great on cakes, cupcakes, cookies, or anything you desire to put frosting on.

Learn how to build a mini hovercraft. With a few items found in almost any desk or tool drawer, you can make your very own mini hovercraft capable of gliding over any flat surface.

Having a boring Facebook profile is lame! Impress your friends and flaunt your social networking skills by sprucing up your Facebook profile.

Welcome back everyone. This article isn't going to contain anything related to scripting, but rather some updates about the series. We'll be quickly discussing what we've covered so far and what is to come.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Humans clearly demonstrate altruistic tendencies towards other members of groups with which they identify.

Paula Deen whips up a decadently rich peanut butter no-bake pie. Watch and see how easy it is to whip up this peanut butter pie recipe. The original cooking how-to video from this article was part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen. Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef.

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

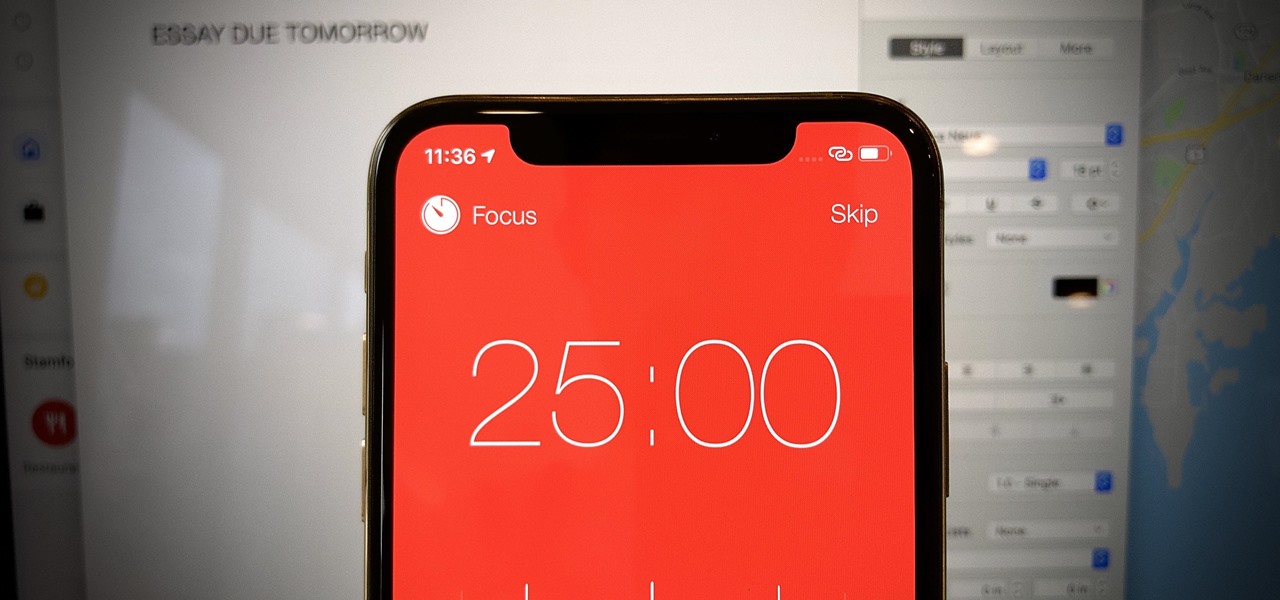
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Unsurprisingly, Google wants to be the caretaker for augmented reality on the web, and its latest move in this endeavor is a 3D model viewer prototype called Article that's designed to work across all web browsers.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

There are few apps on my iPhone that I visit on a daily basis, and one of them is Drippler, the discovery and news app that tells you everything you need to know about your device.

For some of us, mornings are difficult. But if you can manage to start your morning right, you can trigger a chain reaction that leads to a more productive day. Fortunately, our phones have the tools to help us get off to a good start.

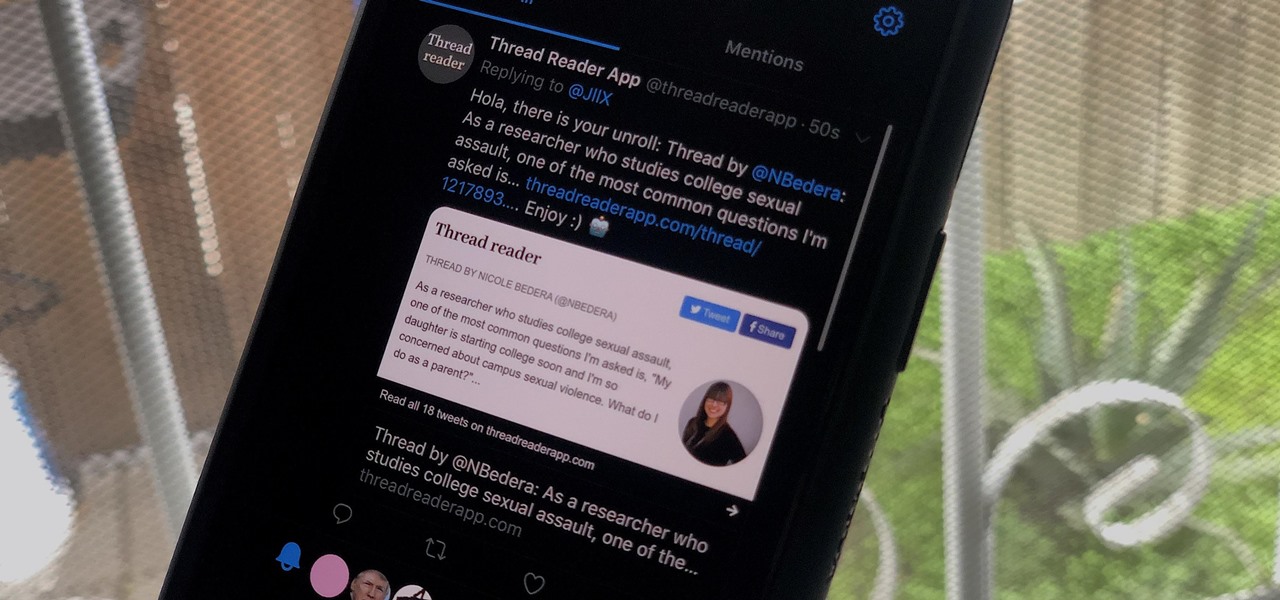
While tweetstorms were a part of Twitter since the beginning, threads, which makes tweetstorms more viable, didn't show up until late-2017. Still, threading multiple tweets at once to create long-form stories, opinions, tirades, and other lengthy Twitter posts, can be hard to digest. However, you can make reading them easier with just a single message.

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

We've all seen the breathtaking, colorful photos of the Eagle, Egg and Cat's Eye Nebulae. You may not recognize them by name, but you've seen them, whether in astronomy textbooks, magazines, websites, album covers, or tee shirts. They are some of the most striking photographs ever taken from the Hubble Space Telescope (HST).

Apple's upcoming iPhone update, iOS 13.3, doesn't add as many new features as iOS 13.1 or 13.2, but there's one under-the-radar change you'll love if you use Apple News on a daily basis.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Android Lollipop still doesn't have a simple way to add a custom lock screen wallpaper, so when I came across Corgi For Feedly from developer Stan Dmitriev, I had to check it out. What sets Corgi apart from other lock screen replacements is that it connects directly to your Feedly account to display top stories from your favorite RSS feeds as your background.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

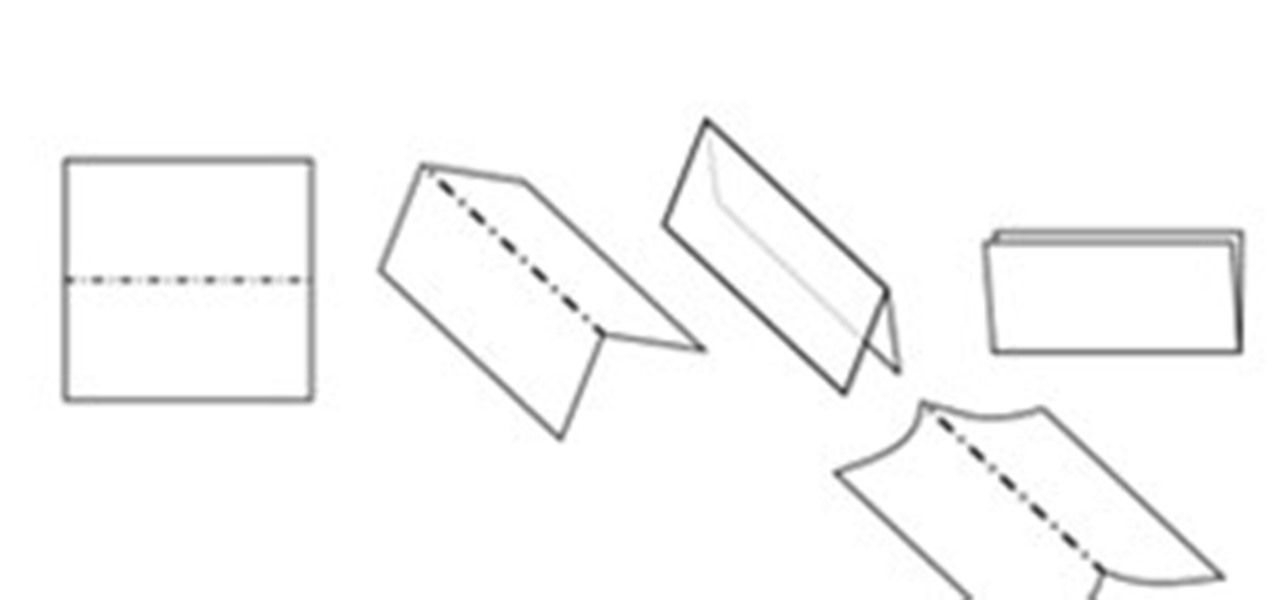
In this article you will learn how to understand written origami instructions, called diagrams. You can follow the video below or read the entire article

Apple News. Facebook. Twitter. Reddit. LinkedIn. These are just a few of the apps you probably have on your iPhone or iPad that keep you up to date on today's events. Unfortunately, they can also cause information overload. But a new viral speed-reading tool thinks it can help you process your daily news more efficiently.

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

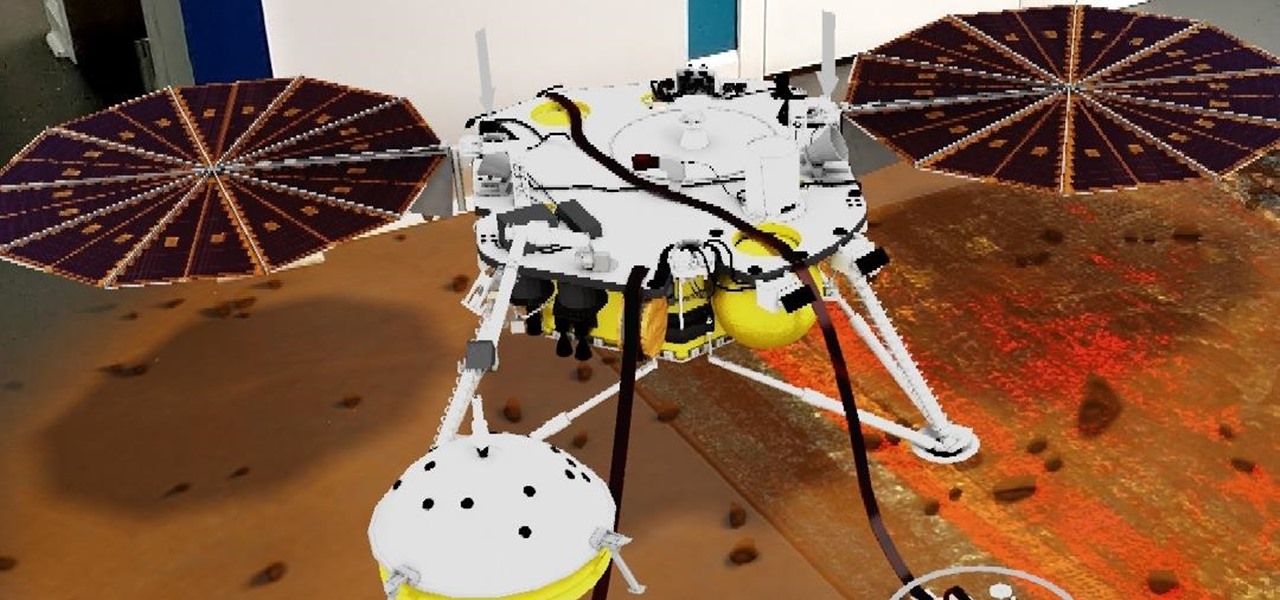
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.