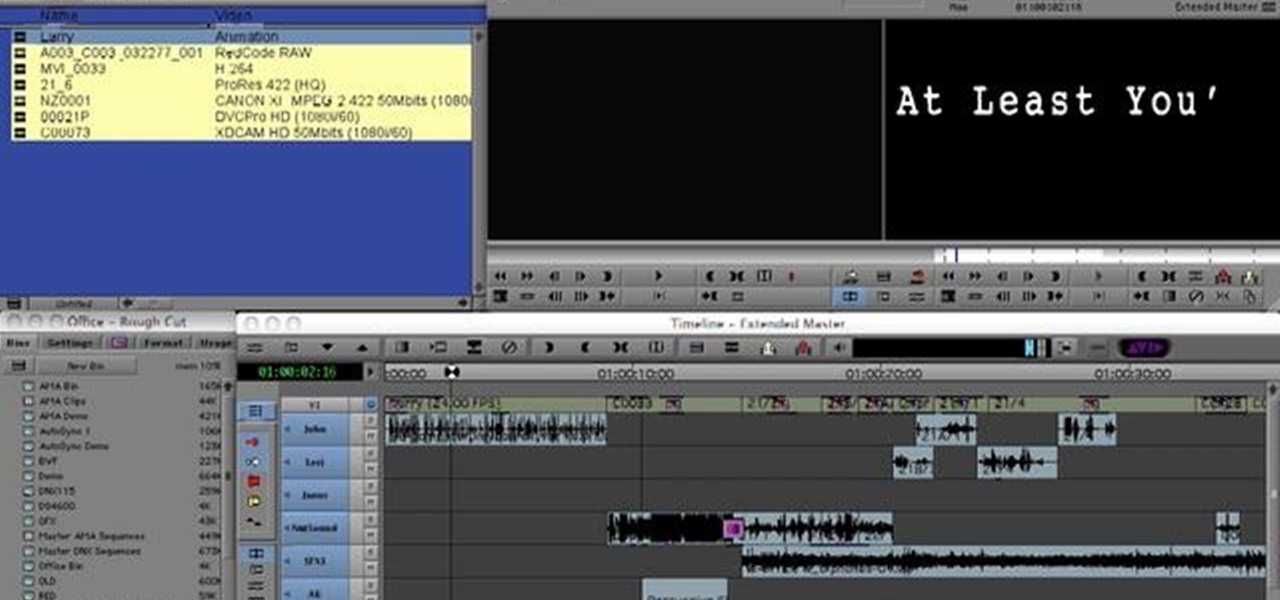
The AMA architecture within Media Composer 5.0 has been expanding since 2009, to include the base of file formats which it is capable of supporting. This tutorial runs down many of these file formats, and how you can work with them After Effects and Avid Media Composer.
Alex Oliver demonstrates how Art Directors and Cinematographers can use the Film & Stage plugin in SketchUp to explore the use of different camera lenses and aspect ratios on location or on a production set. The Film and Stage plug-in is a great way for film makers and directors to pre-visualize shots and scenes in SketchUp, a software you may only have thought useful for architecture and product pre-visualization. Learn how to plan shots and do animatics in this SketchUp tutorial.
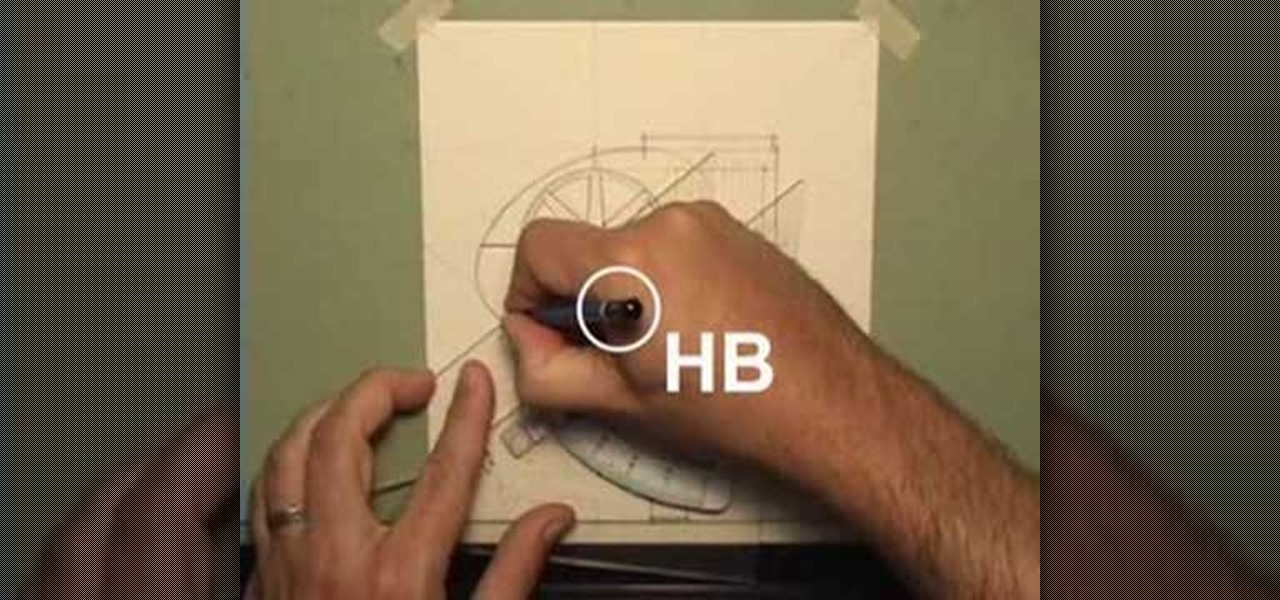
Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw with lead like an architect.

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw like an architect.

This session is tailor-made for advanced Studio users aiming to achieve ultimate quality surface creation.

How can you add your own creativity to the construction and architecture aspects of Sims 3? Make sure your sims are living the life they deserve in comfortable and attractive houses! Add extensions, bay windows, yards, nooks and other details to make a more interesting house in Sims 3.

Have you always secretly harbored a love for urban design or architecture but your parents made it clear to you that they would only financially support you through school if you studied pharmacy? We know your situation sucks, but just because you can't get a degree in urban planning doesn't mean you can't sketch out designs of beautiful cities.

Learn and understand the basics of Trigonometry in this entertaining video. Taught by an experienced YayMath instructor, viewers gain knowledge in the study of trigonometry: the relationship of angles and the triangles they are in. Trigonometry is relevant in many forms of everyday living and careers including architecture. Watch as the experienced instructor gives easy-to-follow instructions and examples including solving "x for y" equations using the 'SOHCAHTOA' method, an abbreviation for ...

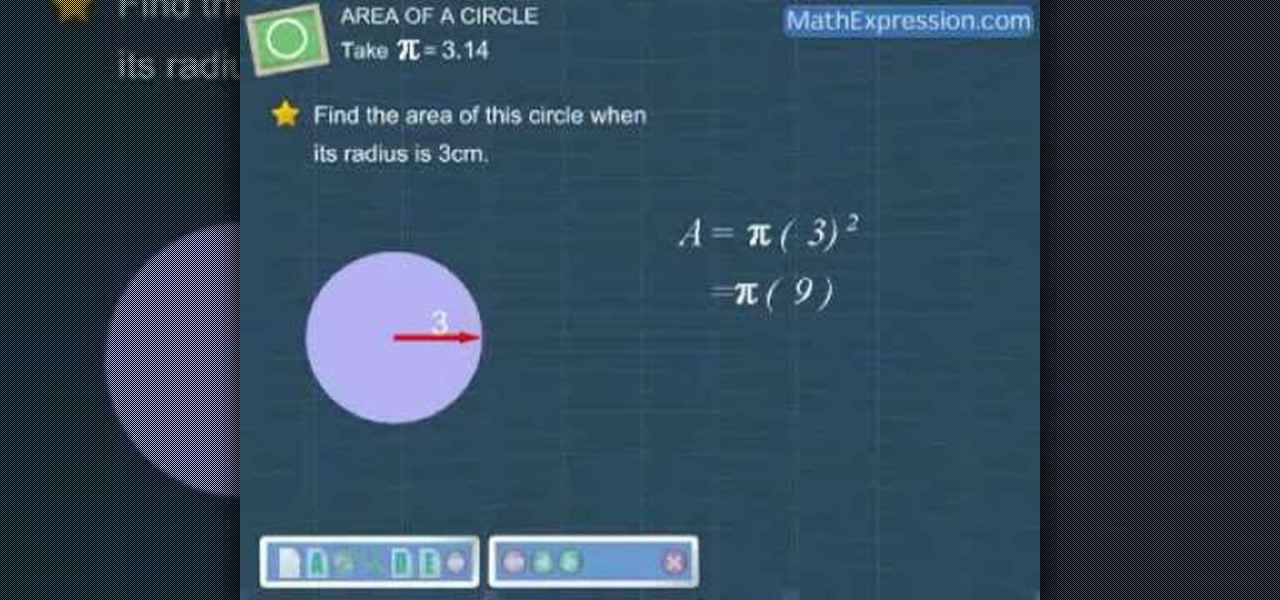
In this video lesson, you learn how to find the area of a circle. The video starts with an explanation of the area's formula. This formula can then be used to find the area of any circle, given its radius, which is half the diameter of the circle. There are many applications for this formula, whether in architecture, or studying for a basic geometry test. Euclidean geometry is the cornerstone of any education, and this video teaches you one of the many formulas in geometry.

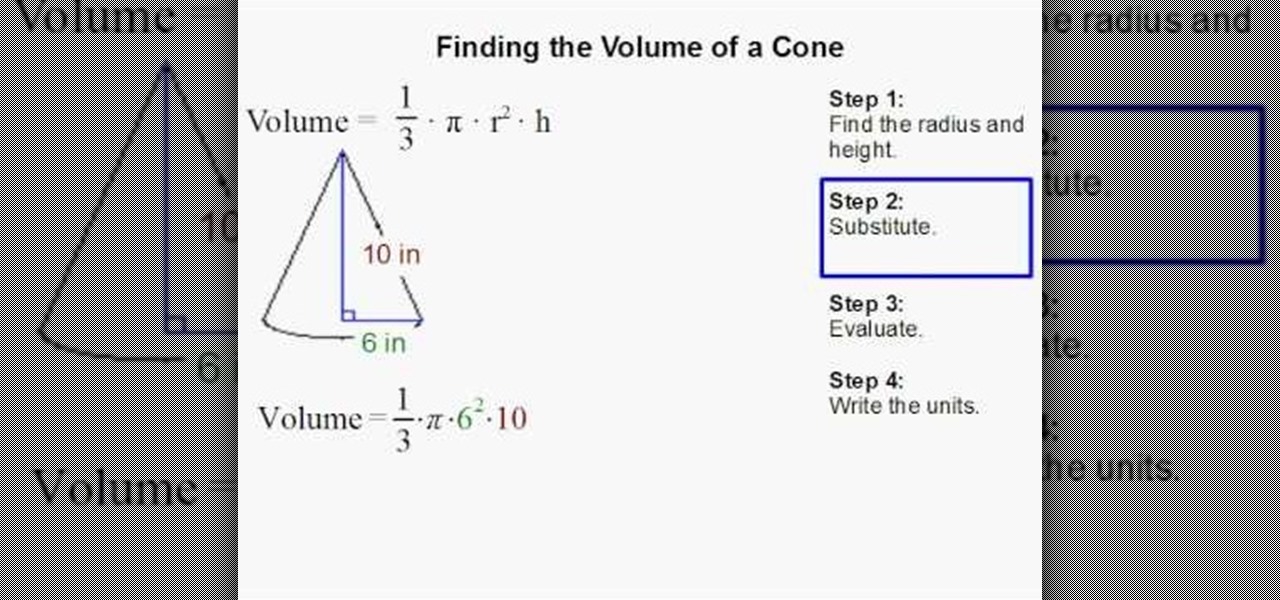
For people who are interested in math or who need to know how to find the volume of a cone for any reason, whether it be homework or architecture, this video will show you how to do so. The formula for finding the volume of a cone is (1/3) pi x radius^2 x height. You can find the radius of your cone by finding half the length across the center of the circle which is the cone's base. After plugging in all the values into this equation, you will be able to find the volume of any cone when given...

Ever dreamed of becoming an architect? Well in this video, the viewers will be instantly thrown into the world of an architect. The video demonstrates and shows how to design like an architect with nothing much than just asymmetrical designs. The video goes in-depth with the idea of asymmetry, what it is and how it functions in architecture. The video is quick paced and very educational. It is highly recommended for any one who wants to become an architect or simply enjoys innovative structur...

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to draw and letter with lead like an architect.

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to write and letter like an architect.

YouTube has a couple of basic gestures: you can double tap each half of the video to skip forward or back ten seconds, and you can swipe down to minimize the video. But wouldn't it be more useful if there were gestures to control brightness and volume? Well, as with all things Android, where there's a will, there's a way.

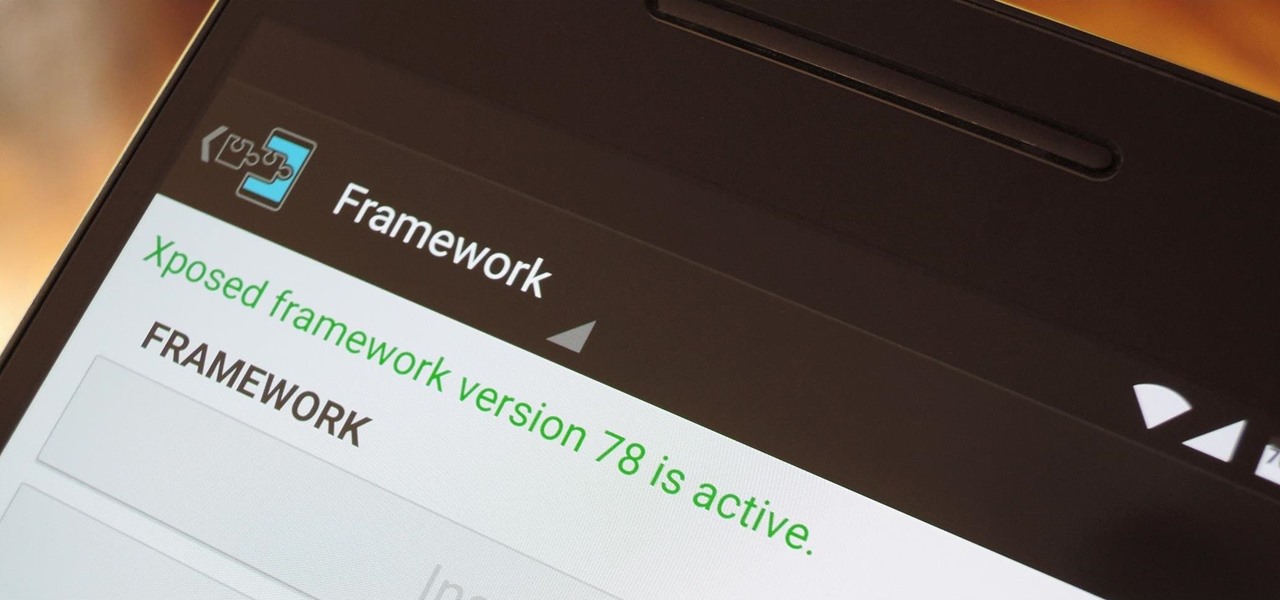
When someone asks me why they should root their phone, one of the top reasons I always give is that it enables you to install the Xposed Framework. Created by developer Rovo89, Xposed basically hooks into the Android system, then allows users to simply install mini-apps called modules that can change almost anything in a device's interface or other installed apps.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Aaron Betsky, director of the Cincinnati Art Museum and previous director of the Netherlands Institute of Architecture, reports on the world's first postage stamp to employ augmented reality. Dutch advertising agency Gummo, the NIA and the Dutch postal service teamed up to present five unbuilt models by different Dutch architecture studios in 3D form. When held in front of a webcam, the illusion of a 3D building is projected in your hand. By slowly moving the stamp, you can experience the vir...

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw an architectural water tower house.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

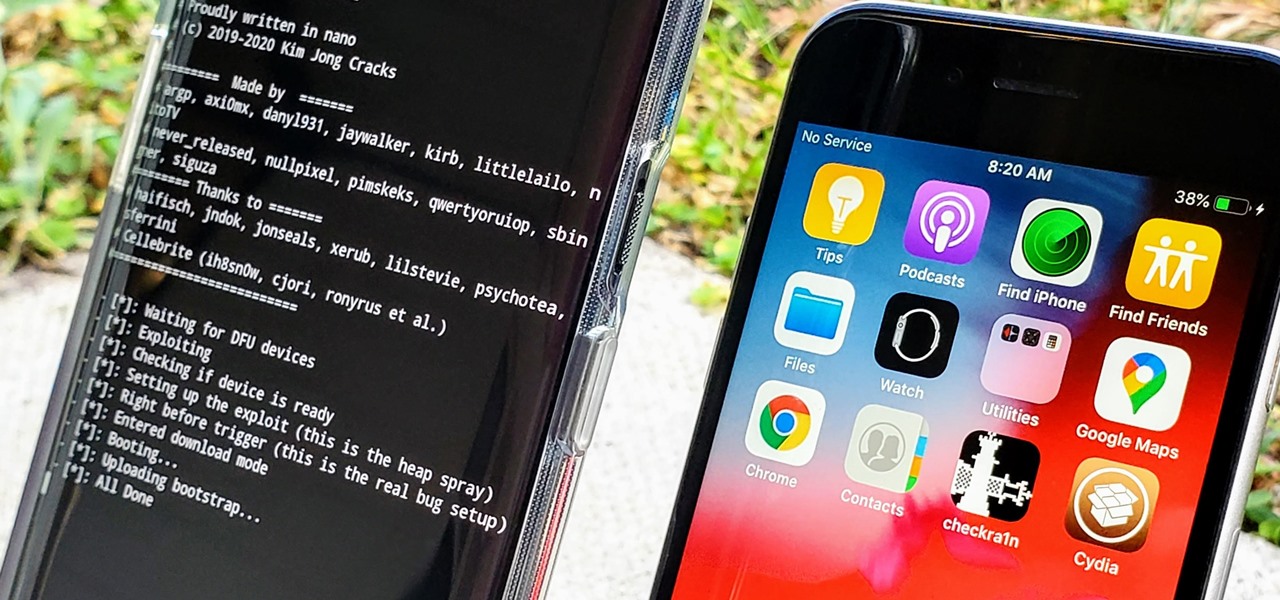
In the iPhone modding scene, the Checkm8 bootrom exploit, by developer axi0mX, led to a powerful jailbreaking tool known as Checkra1n. With it, you can jailbreak a variety of iPhone models without worrying about it getting patched later on. But in the past, it required you to have a macOS computer — but not anymore.

A rather exciting development has recently surfaced in the jailbreaking scene for iPhone. The Checkm8 bootrom exploit was shown off to the public by axi0mX, which made way for the undefeatable Checkra1n jailbreak tool. With it, you can freely jailbreak a variety of older iPhone models without any restrictions. The success rate is quite high, too, when compared to other jailbreak methods.

This is a really simple video guide on how to install Hackintosh OSx86 (Mac OS X) on a PC. OSx86 is a portmanteau of OS X and x86, a so-called collaborative hacking project to run Mac OS X computer operating system on a non-Apple brand personal computer, with x86 architecture processors.

Would you like to know what your next house is going to look like? With the HoloLens, you can just plop a hologram down in an open outdoor area and find out.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

When developing for the HoloLens, keeping a constant 60 fps (frames per second) while making things look beautiful is a challenge. Balancing the processing power to display complex models and keeping the frame rate where it needs is just a straight up painful process, but a solution seems to be on the horizon.

Visualization is one of the obvious commercial applications for technology such as Microsoft's HoloLens. The ability to see the assets of a project in different scales—from micro to larger-than-life—with a quick air tap will play a large part in the coming augmented reality revolution. Whether the assets are art for a game, interior design, raw financial data, or architecture, data visualization will play an important role in the future. This is due, in part, to our ability to absorb informat...

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

While it may seem like the Cold War 2.0 is happening, at least some US spies are getting the content Americans need. That's right, Electrek has gotten some new pictures of the Tesla Model 3.

Trimble is integrating its mixed reality applications into the DAQRI Smart Helmet to enable outdoor and on-site support for design, construction, and heavy industry as part of a collaboration the companies announced today.

In this episode of Have You Seen This?, we will look at Oriental Museum by 247 Technology Limited, a free application in the Windows Store for HoloLens. Museum exhibits seem to be a popular theme amongst the demonstrations going up, so let's see how this one looks.

OneDrive, formerly known as SkyDrive, is a free online storage solution developed by Microsoft. If you're a fan of using cloud-based storage systems, then OneDrive offers you plenty of benefits. It's also heavily integrated into Windows 10, including the new File Explorer, in an effort to make utilizing OneDrive easier for you.

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw an architectural cliff house.

Take a lesson in architecture from renowned architect Doug Patt by watching this video tutorial. If you want to learn about drawing and designing, without going to school, Doug's just the teacher. Watch to see how to design and draw an architectural bridge house.

Apple's iOS 16.3 update for iPhone had impressive new features, but iOS 16.4 might impress you even more.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

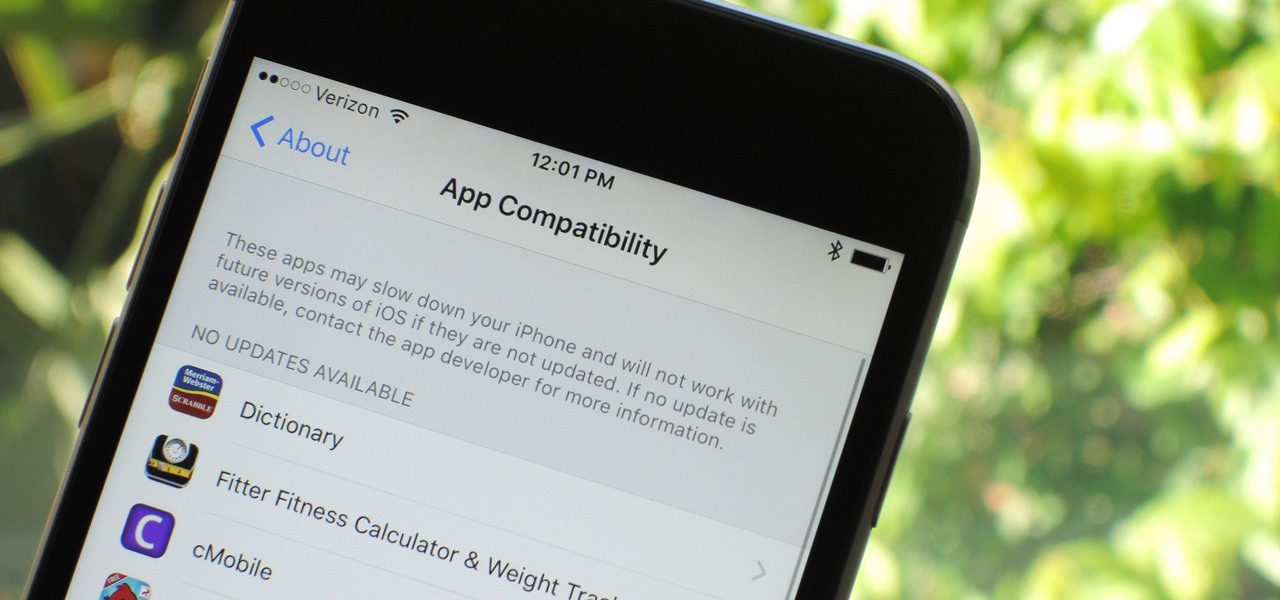
Apple has removed support for older 32-bit applications in the new iOS 11, which was to be expected after the 10.3 update added the ability to detect apps that are still running 32-bit processes on your iPad, iPhone, or iPod touch. Apple even excluded restore images for 32-bit devices such as the iPhone 5 and iPad (4th gen) in the iOS 10.3.2 beta 1 update for developers, so this shouldn't be a surprise.

For many, the stock version of Android is often considered the epitome of what the operating system should look and feel like by default. It's clean and clear of unwanted extra apps that come pre-installed with the system, provides a fluid and fast user experience, and runs on just about any device that has an unlocked bootloader to install a custom ROM with the stock version ready to go.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.