
How To: Remove the Shortcut Virus from Flash Drives
You encounter this problem many times, when you plug your flash drive, and suddenly you find that all your data has become shortcuts everywhere!!!


You encounter this problem many times, when you plug your flash drive, and suddenly you find that all your data has become shortcuts everywhere!!!

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.
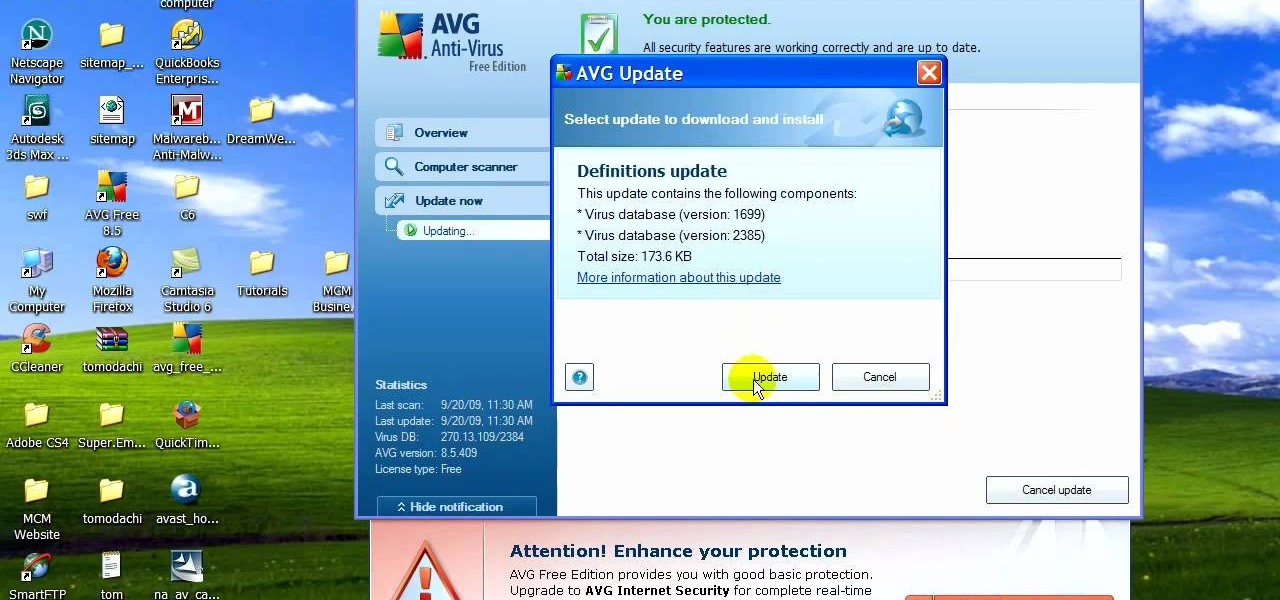
If your computer is working slow--or not at all, there could be some unsavory programs running amok in your system. Trojans, malware, viruses, and hacks are dangerous to the health of your operating system. This video tutorial demonstrates the measures to take in order to rid your PC of malicious programs. Stop being bullied by harmful applications and use such programs as AVG Antivirus and Malwarebytes to protect your computer. Once you've cleaned up your system, be sure to configure your se...
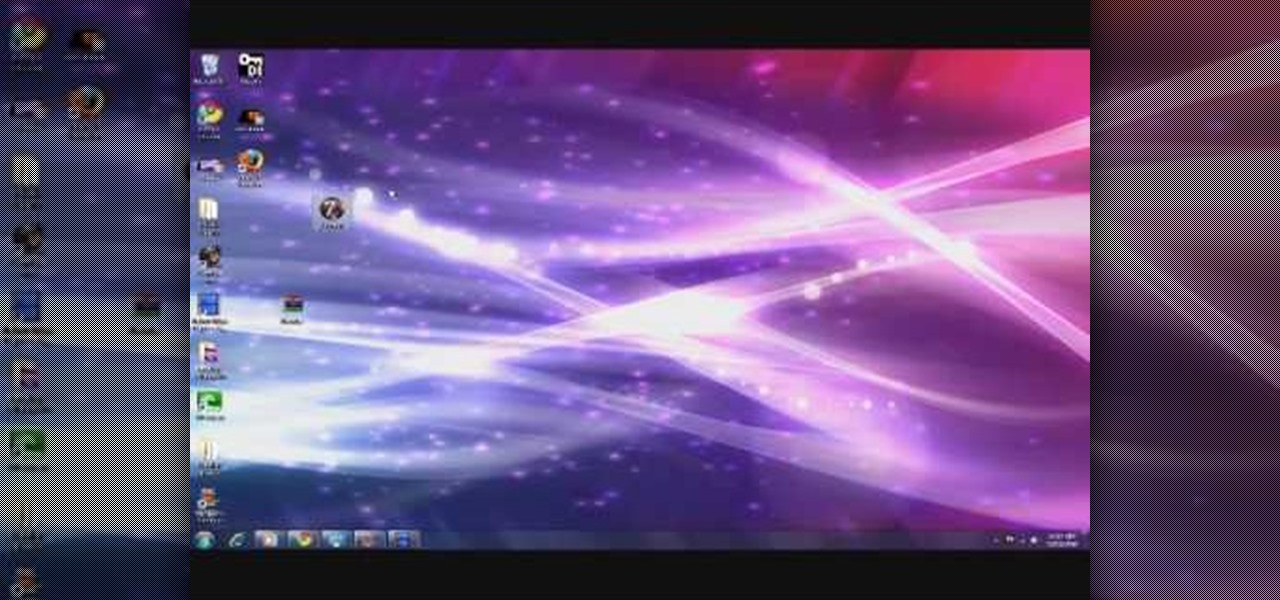
In this video the instructor shows how to activate Windows 7 forever. There is a program called 7Loader that will activate your Windows forever without having to pay for anything. Download the program from the internet or from the link given in this video. After downloading it, scan it with your antivirus program to make sure that it is free of any virus. Now run the tool and on the screen pick your computer make. If you don't know your computer make, look for it in the control panel, as show...

James Marey teaches how to test whether your Anti virus is still working perfectly. First right-click anywhere on your desktop, go to 'New' and select 'Text Document' to open a new document. Now find some text containing a virus from the internet or you copy the text from the video. After entering the text, go to file and save the document. Now if your anti virus is working perfectly it will pop out a virus threat indicating the file you just saved. Finally select the appropriate option to re...

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Welcome back, my greenhorn hackers! Several of you have you have emailed me asking whether it's possible to install a keylogger on a victim’s computer using Metasploit. The answer is a resounding "YES"!
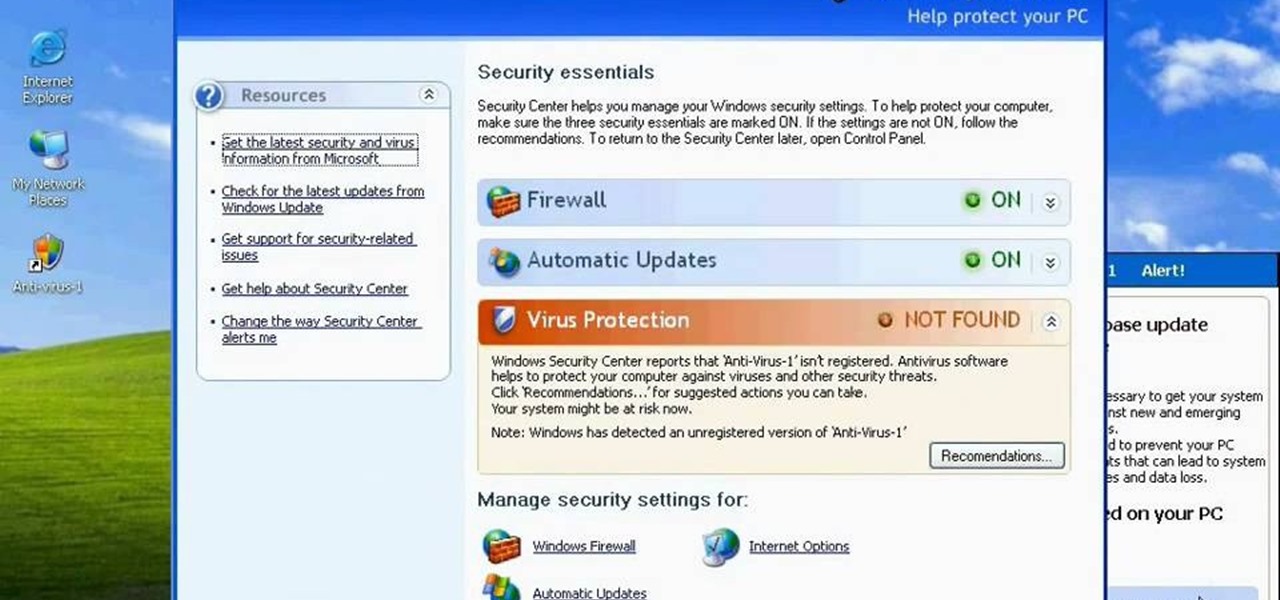
http://www.enigmasoftware.com/support... Having problems with your anti-virus software on Windows?
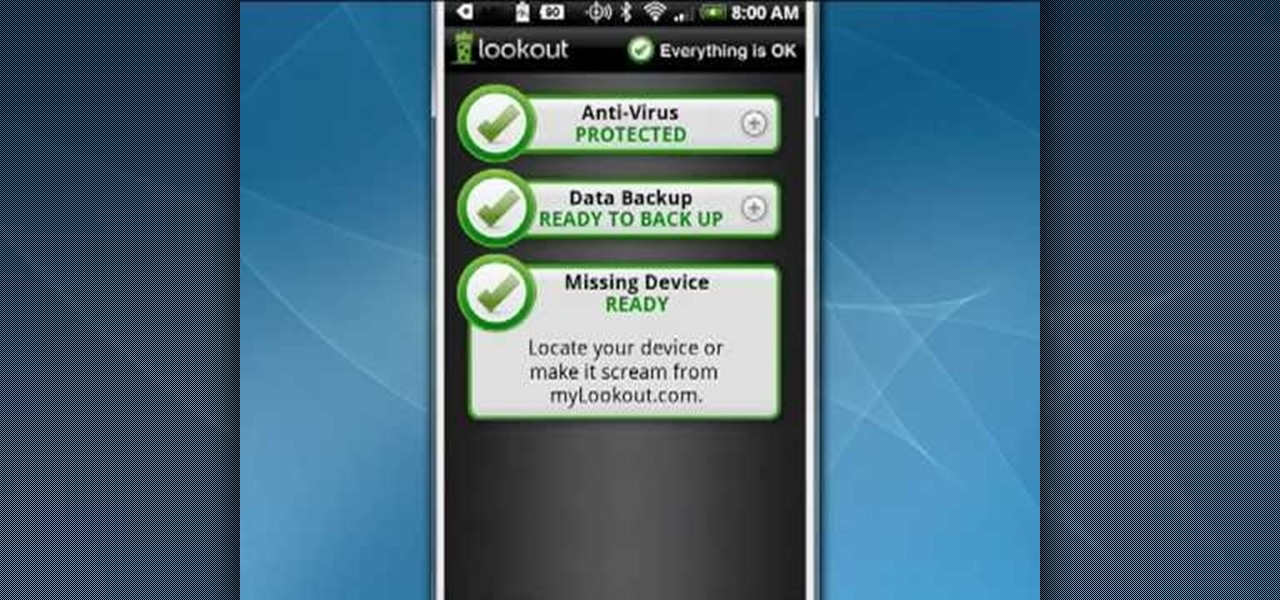
Your Android phone is a computer not unlike a laptop or desktop PC and it shares the same vulnerabilities. This clip presents a quick overview of how to safeguard against viruses and data loss. With the Lookout app, it's easy! So easy, in fact, that this video guide can present a complete overview of the process in about two minutes. For more information, including step-by-step instructions on how to adjust your own Facebook tagging settings, take a look.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.
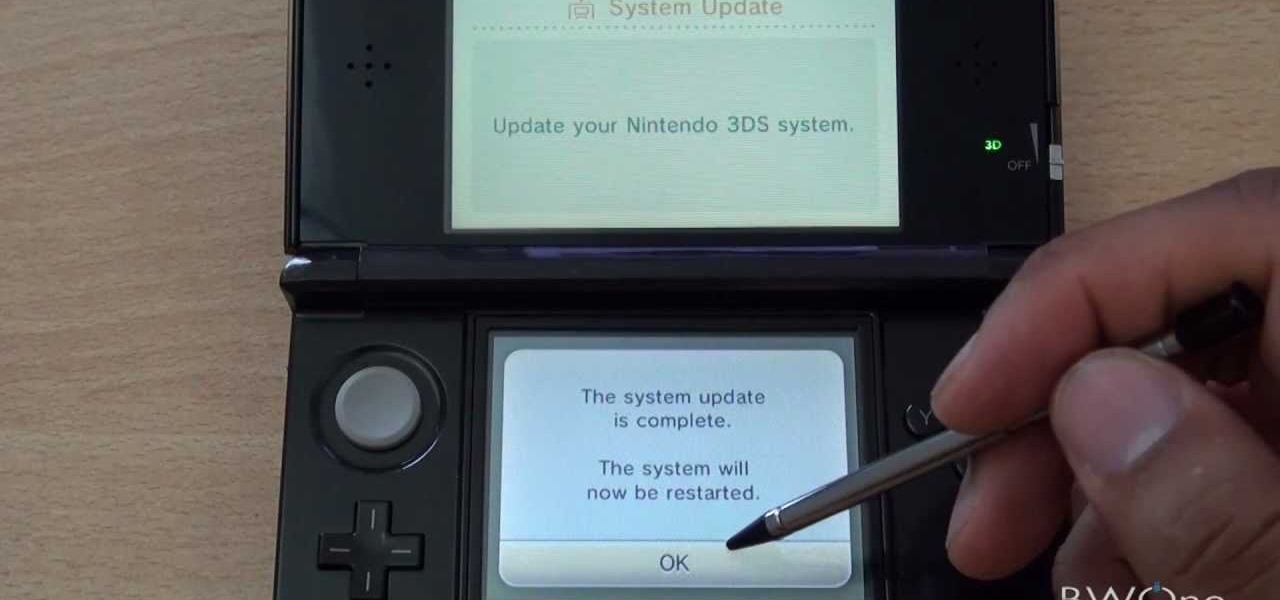
Similar to the Wii, Nintendo frequently updates the apps and software on the Nintendo 3DS. These upgrades are always available using System Update under the system settings on the gaming handheld. Take a look at this guide on how to access the System Update feature, download, and install the updated software. Now you can always access the latest version of the Nintendo 3DS software and apps, such as the eShop and internet browser.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

Looking to create your own mod or write a game to round out your design portfolio? By using the free Reality Factory software, you can create levels, weapons, monsters and everything else that goes into writing a video game. This tutorials shows you how to create an FPS game using this freeware.
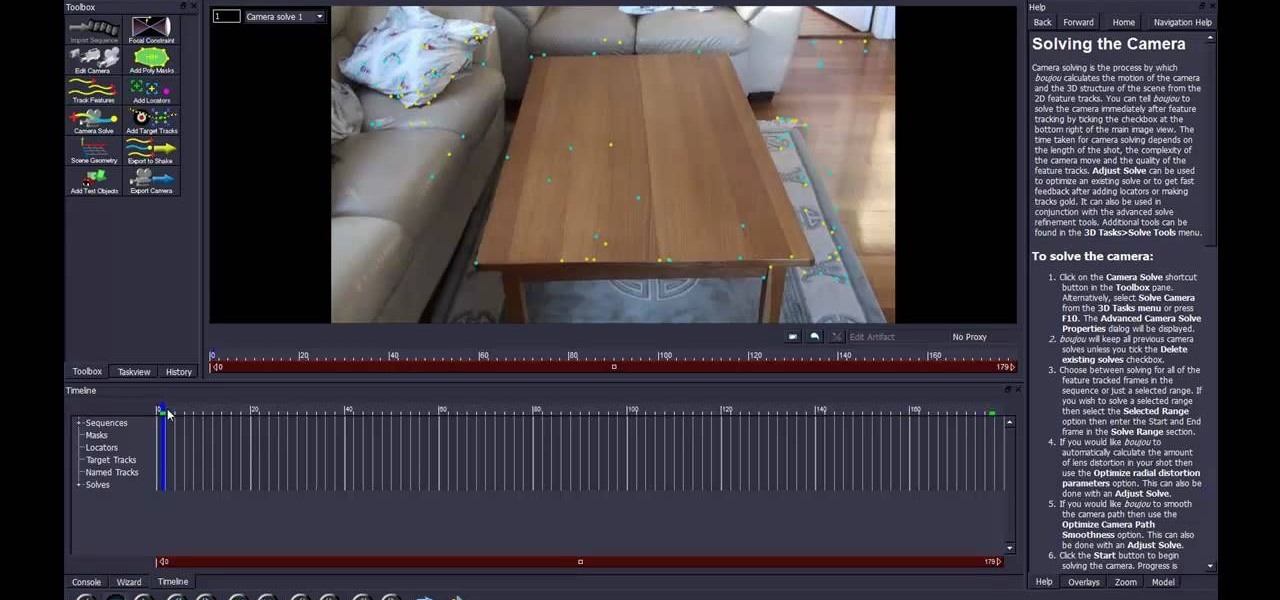
Most of the 3D modeling tutorial videos out there work within one program or at most two, often Photoshop in conjunction with a 3D modeling program like Maya. This video will walk you through a complete project using four program: 3DS MAX for modeling, Boujou for 3D tracking, Photoshop for texture editing, and finally After Effects for compositing. If you have all of those programs and want to create a seriously good-looking image, look no further.
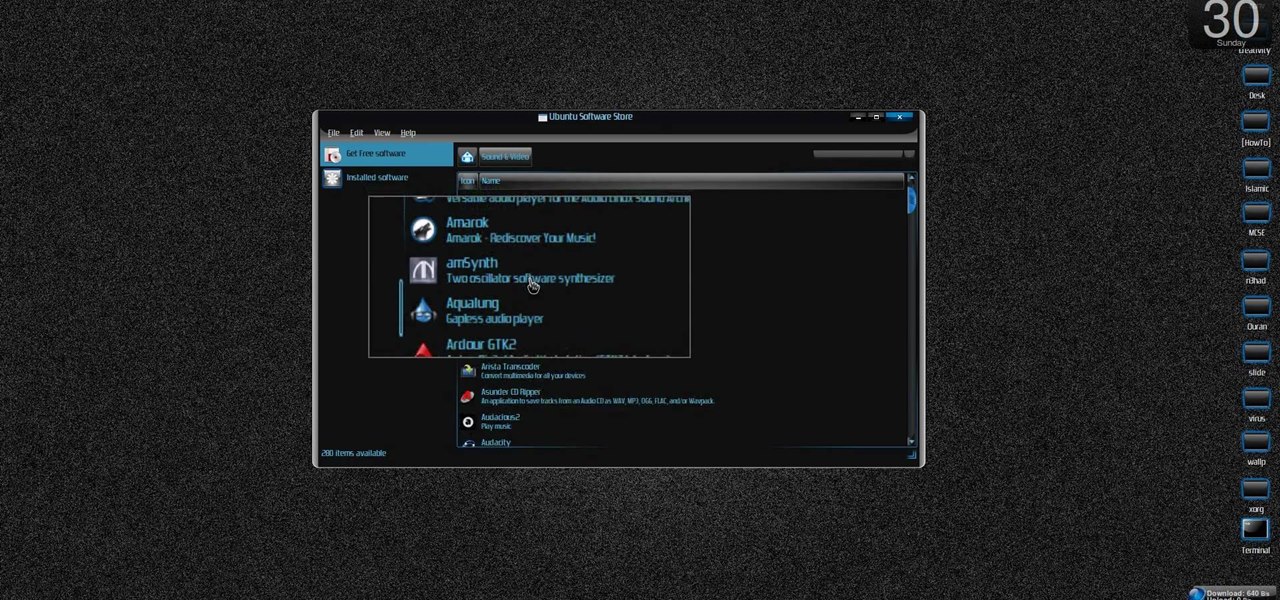
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the Ubuntu Software Store on Ubuntu Linux.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Learn how to create texture maps and apply them to figures using Poser rendering software with expert 3D animation and rendering tips in this free software tutorial video series.
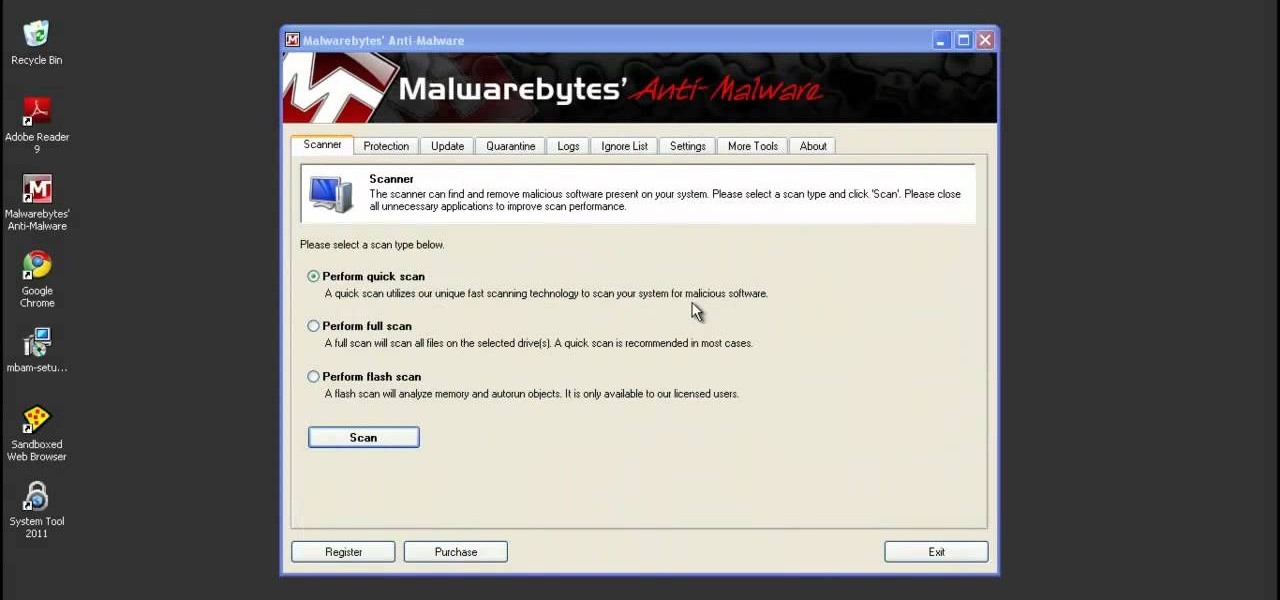
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

Aimed at people who have never created a website before, this tutorial shows you how to use a graphics program to create a website that will have an impact, load quickly and index easily with various search engines. You won't even need to know much coding!

Lego Mindstorms is a great way to take your Legos to the next level by adding in the flavor of robotics! But, with taking it up to the next level, it does get a hair tougher! And if you're having trouble working with the Mindstorms software, this great video with Patrick Norton and David Calkins goes over each step of using the software so you can have your very own robot ready to go in no time!
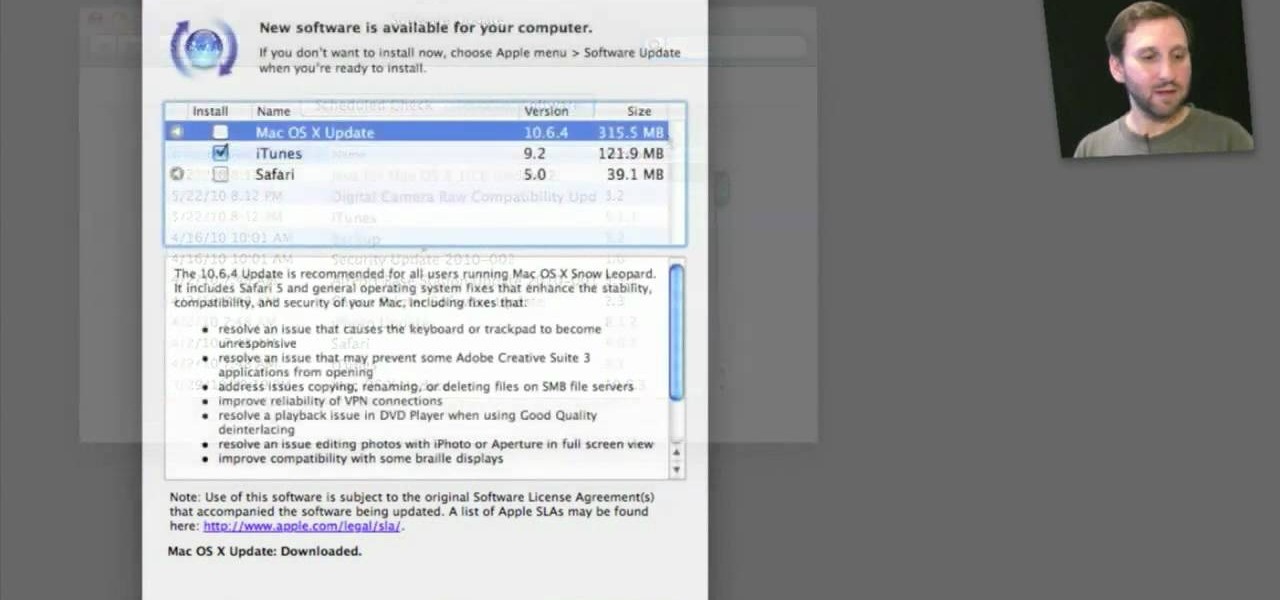
Need a primer on how to use the Software Update feature within all versions of Mac OS X? This Mac user's guide from the folks at Mac Most provides just that. For more information, including detailed, step-by-step instructions, and to get started automatically updating your software and OS with the Software Feature app, watch this video guide.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.
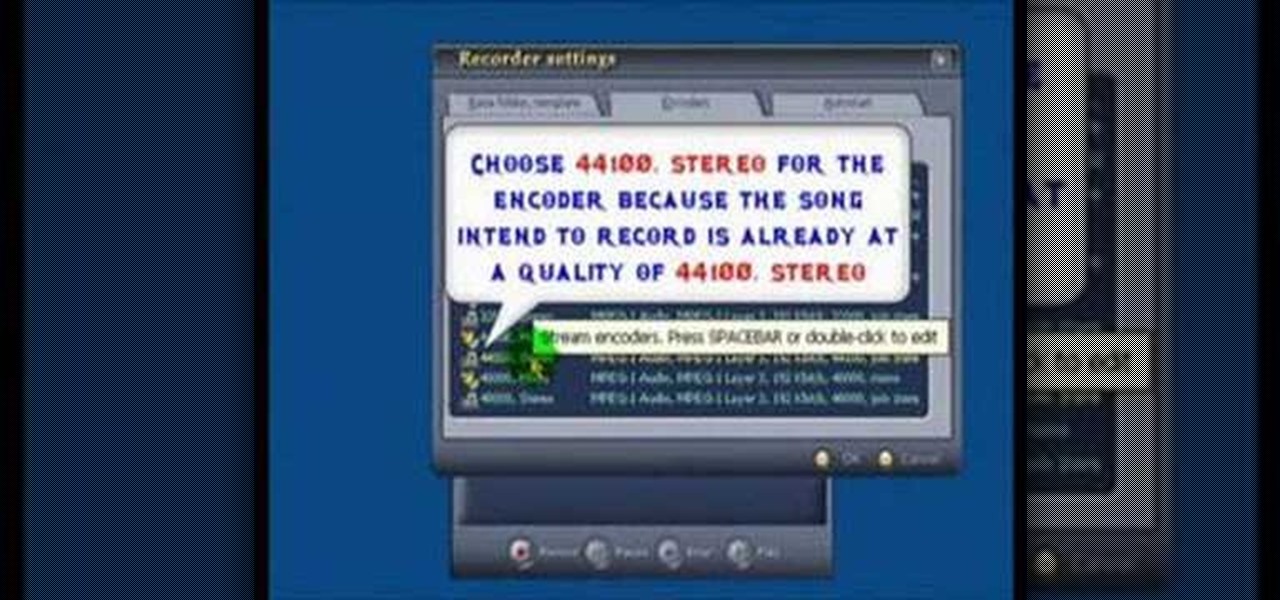
AV Voice Changer Software is a real-time, high quality voice changing software. In this AV Voice Changer Software tutorial you will learn how to record a song from Windows Media Player. Learn how to record streaming songs in this AV Voice Changer Software tutorial.

Learn how to use face room to create facial expressions in computer program Poser with expert 3D animation and rendering tips in this free software tutorial video series.

Learn how to make characters walk and move using the computer program Poser with expert 3D animation and rendering tips in this free software tutorial video series.

Learn how to create realistic hair and clothing using the dynamic features of the computer program Poser with expert 3D animation and rendering tips in this free software tutorial video series.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.