Over the past three years, Epic Games has raised billions of dollars in funding on the success of Fortnite as well as Unreal Engine, one of the top 3D engines available for developing games and AR experiences.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

This is a simple pattern, designed to produce a well-fitting mitten. Both the right and left mittens worked the same up to the shaping for the top of the mitten. A slight adjustment for making one right and one left, then they are worked the same. The gusset for the thumb constructed with the increases made in the center of the gusset, rather than on each side. This makes it easy with a minimal amount of counting stitches as you go. I have been crocheting for 56 years. In doing research for w...

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

This time last year, we got our first taste of what mobile app developers could do in augmented reality with Apple's ARKit. Most people had never heard of Animojis. Google's AR platform was still Tango. Snapchat introduced its World Lens AR experiences. Most mobile AR experiences existing in the wild were marker-based offerings from the likes of Blippar and Zappar or generic Pokémon GO knock-offs.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Are you on a low-salt diet and need some healthy recipes that are friendly on your taste buds and wallet? This superb video serves up an easy and delicious recipe that will please everyone, whether or not the doctor has advised them to cut down on the sodium. The tutorial, one in a fantastic and free video series, offers excellent tips on how to properly cook your rice, as well as how to dress it up without damaging your health.

Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems useless. It affected both free and paid AVG owners.

The trend of online video sharing came to the mainstream with popularization of YouTube, which let users view, submit and share video clips. YouTube started off in the year 2005, and quickly became one of the most visited websites on the internet. Sensing the emerging trend, large companies like Google joined the trail and launched their own video sharing sites (Google later bought YouTube).

Quitting a bad habit is not as straightforward as simply quitting cold turkey and getting it right the first time. So what to do if you really want to quit doing something that isn't good for you?

This past Tuesday, Amazon pushed a big software update to Kindle users the world over. While the update introduces a host of great new features—secondary page numbers that allow readers to reference real-world editions, for example—, it also takes something away. What?

Via WonderHowTo World, CAKES! CAKES! CAKES!: Martha Stewart Living Radio recently held a cupcake contest, and unfortunately the winner was NOT these Alexander McQueen cupcakes, by Julia Cunningham, DJ on SiriusXM U.

Martha Stewart Living Radio recently held a cupcake contest, and unfortunately the winner was NOT these Alexander McQueen cupcakes, by Julia Cunningham, DJ on SiriusXM U.

Going green has never been so hardcore as Jack Mountain's bushcraft podcast. This is basically a 10 minute poo tutorial. Fortunately for us, Jack's "deposit" is simulated, and we are spared seeing the real act or his prodigious backside.

The African Soft Fur Rat though new to the pet trade is a unique little rodent with unusual qualities. Not only is this little rat a great step up for people who feed reptiles it is virtually odorless and that is definately a plus for those who would like to have a pet rat or mouse they can keep inside the house and not spend a fortune in bedding or spend a lot of time cleaning to keep the rodent odor down.

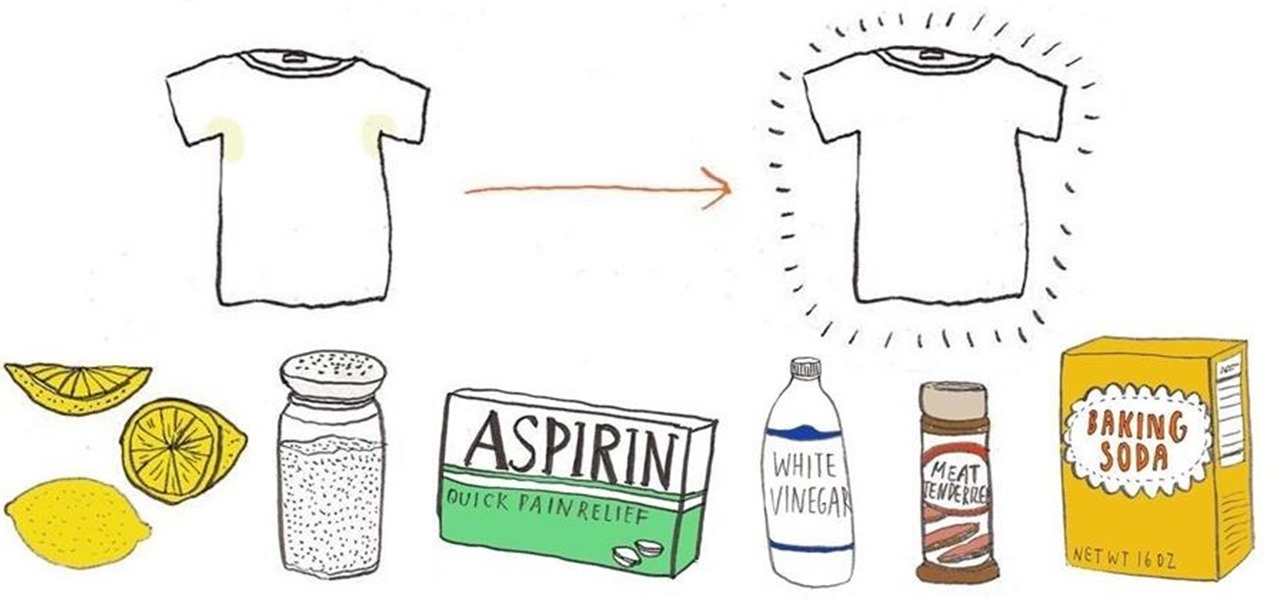
Got a bad sweat stain on the underarms of your light-colored clothing? You probably have something in your kitchen or medicine cabinet that will help get rid of the stain immediately. Aspirin, table salt, lemon juice, white vinegar, baking soda, and even meat tenderizer (make sure it is unseasoned!) are some of the many common household ingredients you can use to make your sweaty clothes look brand new again.

Each aspirant nursing assistant is require to obtain CNA certification for their work employment. Thus, passing the CNA state exam is highly recommended. Usually the CNA testing process has two types of test - written and clinical exam. The most difficult yet challenging part of CNA test is the skill exam.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

How do we really come to the decisions that we make? Is it just flip a coin and hope for the best or is there some underlying procedure that we go through, consciously or unconsciously, that guides our course of action?

Today's article serves as a general guide to keeping Windows 7 and Vista clean. The goal is to clean up your messy computer and have it running at maximum performance in no time. The question at hand is—what is your computer's performance like?

Going on dates can be tiring and can start to become a bit of a chore. But by using these NLP techniques, as advised by love doctor Sam Van Rood from his book Teach Yourself Flirting, you can reinvigorate yourself and continue your search for the perfect match. So Deal with your dating fatigue the VideoJug way. Deal with dating fatigue using NLP techniques.