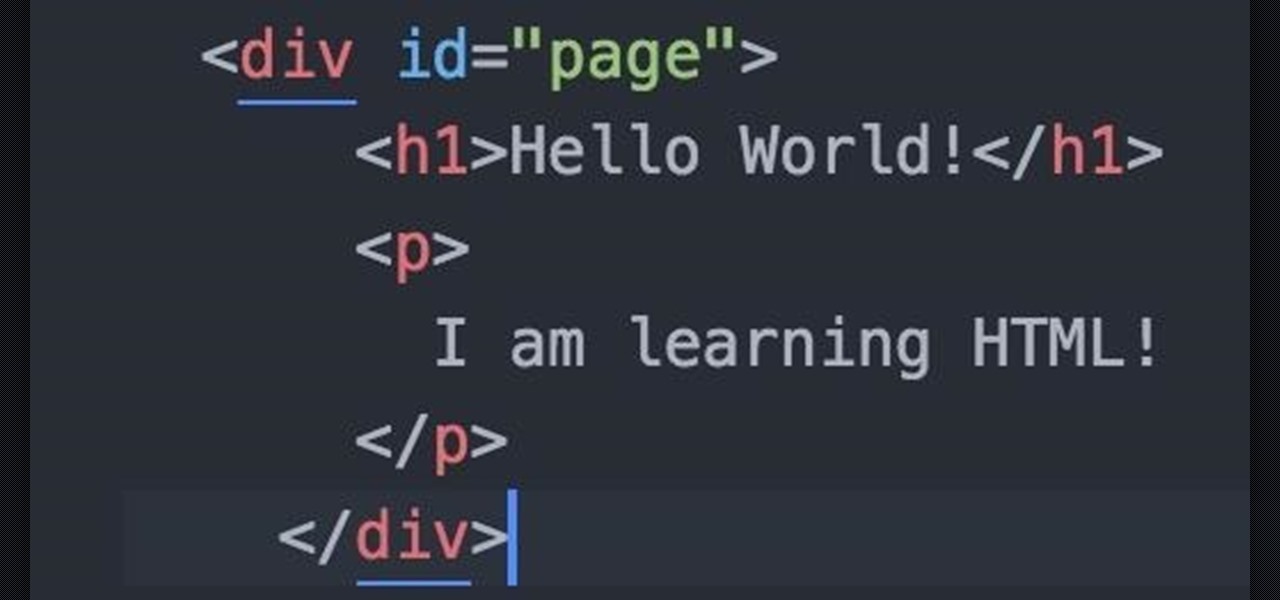
This video tells us the method to transfer photos from your iPhone to your Mac. In the first step, launch the image capture. Connect your iPhone to Mac via a USB cable. 'Download To' option is used for specifying the folder in which you want the downloaded files. 'Automatic Task' specifies the task which the application must do after the transfer of files is over. Go to the 'Download Some' option. Select the file(video or photos) you want to transfer. Choose the download folder and click 'Ope...
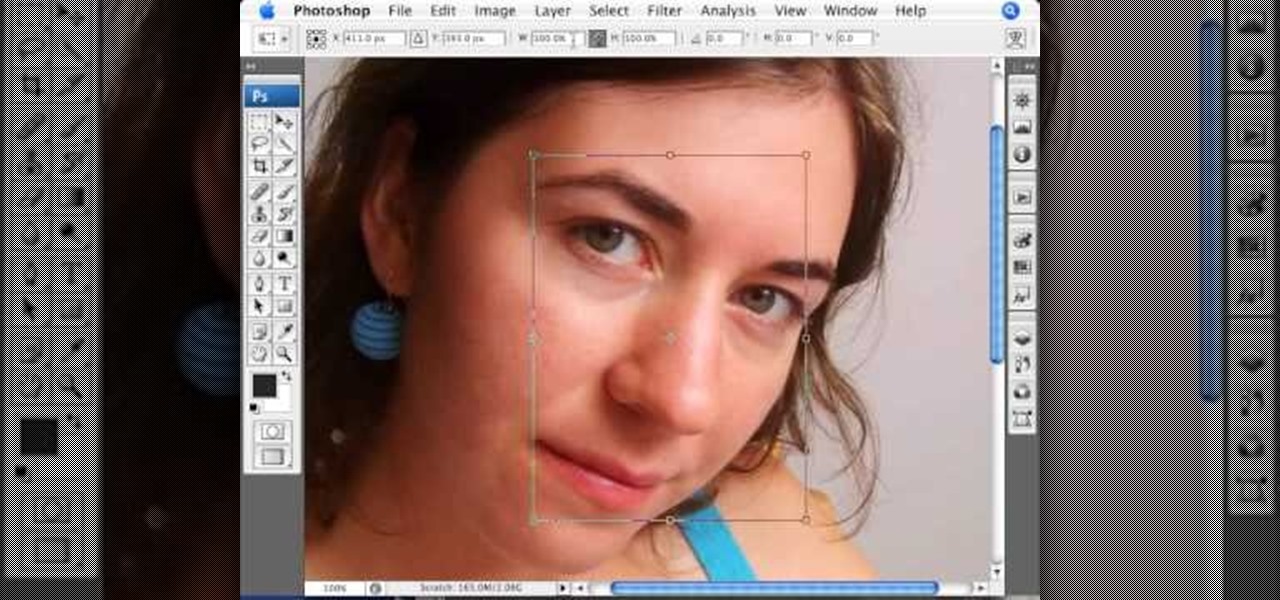
This Photoshop tutorial on performing a nose job using Photoshop contains detailed instructions on the use of Photoshop tools to, depending on taste, enhance the appearance of an individual. The person narrating the tutorial specifies the necessity of subtlety with the modification of the picture in order to remove any appearance of modification. The way described is essentially to select the general nose area, feather the selection by an optional amount, and set it in a separate layer. Then ...

The FN P90. Everybody wants one, but more than likely, you can't get your hands on one, especially if it's illegal in your area. Designed by FN Herstal back in the 80's, the P90 personal defense weapon is the cream of the crop. It's full name, Project 90, specifies a weapon system of the 1990's. If you want this firearm for a weapon prop or just to have, you can easily build one yourself with household materials, mostly cardboard. Watch this video tutorial to learn how to build a P-90 prop ca...
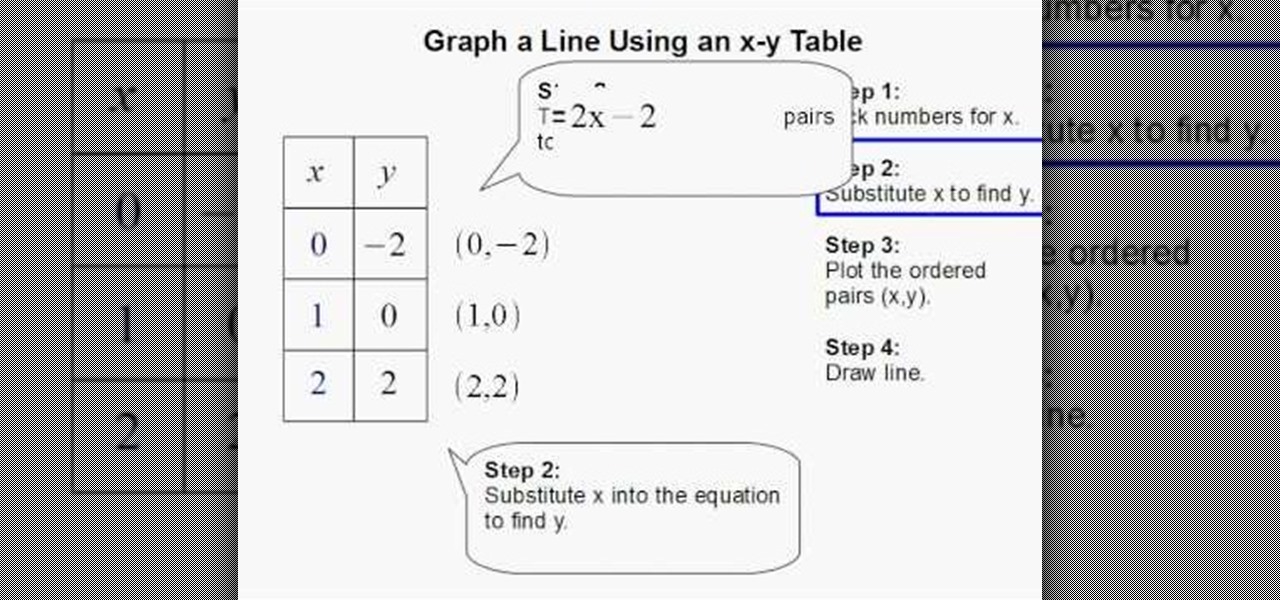
In this video the instructor shows how to graph a line using X-Y table values. He specifies a four step approach. In the first step he picks numbers for the value of x. In the next step he substitutes the values of x in the equation of the line to obtain the corresponding y values, in the third step he plots these ordered pairs on a graph sheet. Finally in the fourth step he joins them resulting in a straight line for the given equation. This video clearly shows how to graph a line using an X...

Check out this instructional home repair video that shows you a very simple way to clean the condensate drain on your air conditioner. If you follow these simple steps, it could save some money, not to mention the grief. If you have an A/C and have ever experienced a backed up condensate drain, you know what I mean. Avoid this inconvenience by watching this air conditioning tutorial video.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

Will smartphone batteries ever last as long as we need them to? Perhaps not. That's why we rely on external batteries to help us stay connected for hours, even days, longer than usual. But in 2018, you don't want to use just any external battery. Modern Android phones have fast charging — so should your portable charger.

Do you remember the last time we used BeEF? Well, now we get to use it again, but this time with MITMf! We are going to auto-inject the hooking script into every webpage the victim visits!

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

With numerous insider reports, patent awards, acquisitions, and hires over the past few years, augmented reality smartglasses from Apple appear to be an inevitability.

Amazon has had a long-standing partnership with its consumers regarding special offers. Amazon sells these Prime Exclusive Phones with lock screen ads and Amazon apps in exchange for discounts on the phones. You also need to be an Amazon Prime Member, leading us to historically believe that these "special offers" weren't really all that special. That is, until today.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

There's a common saying that separates cooks from bakers: baking is a science, while cooking is an art. When baking, one little misstep can alter the texture, taste, and consistency of any recipe.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.

When Apple announced its new iPhone 7 and iPhone 7 Plus models in San Francisco, one of the biggest new features was an "IP67" water-resistance rating. Couple that with a few official renderings that show the new iPhone covered in water, and you'd probably arrive at one logical conclusion: The iPhone 7 is waterproof.

I saw many people asking for a Tutorial about writing their own Remote Administration Tool, so I now introduce you in a basic kind of RAT. This program is not for real use, but for learning how you could write this kind of tool. It will be basicly coded and not very refined. I used Python 3, so you have to install it if you want to use this program unchanged. Also this RAT is for Windows and almost all features won't work under Linux.

Whether it's because you want to make a quick tutorial video or want to show off your gameplay skills, recording the screen your Nexus 7 tablet isn't an easy feat. At least, until now. Hidden inside Android 4.4 KitKat is a built-in screen capturing feature, but it takes a little effort to dig it out.

Apple just released the fifth public beta for iOS 14 today, Wednesday, Aug. 19. This update comes one day after Apple released iOS 14 developer beta 5. It follows iOS 14 developer beta 4 by 15 days, and iOS 14 public beta 4 by 13 days.

Apple just released the fifth developer beta for iOS 14 today, Tuesday, Aug. 18. This update comes two weeks after Apple released iOS 14 developer beta 4, and 12 days after the release of iOS 14 public beta 4.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

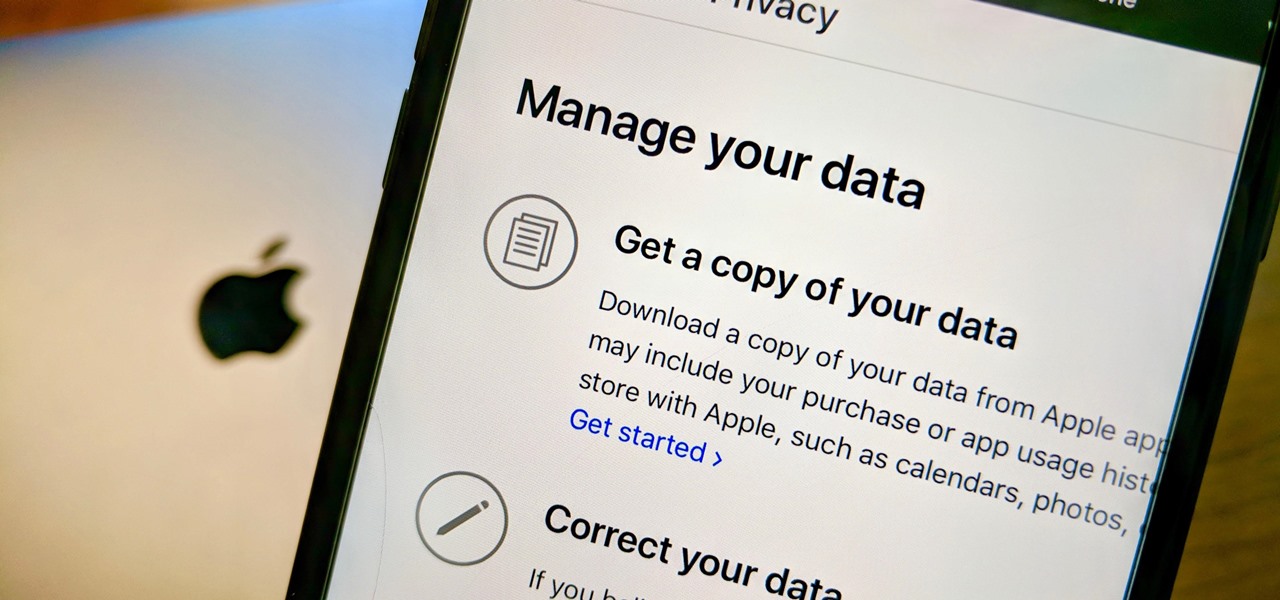
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

Not to be outdone by Apple and it's new line of flagship phones, Google has followed suit and finally announced the followup to their highly regarded Pixel line of handsets — the aptly named Pixel 2. Thankfully, the tech giant has also joined in on the trend towards more durable devices, and has engineered both the Pixel 2 and Pixel 2 XL to have a rating of IP67 under the IEC standard 60529.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

Soda bread, corned beef and cabbage, and colcannon are all great dishes to serve up on St. Patrick's Day, but desserts really let your inner leprechaun come out to play. Not only can you have fun incorporating all kinds of tasty Irish liquors into baked goods, you get to dye things green.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.