Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

Apple announced four different iPhone models during its Oct. 13 web-only event, but only two of them can be purchased this month: the iPhone 12 and iPhone 12 Pro. Preorders have already started for the two smartphones, and you could have one in your hands as early as Oct. 23, if you're lucky. To help keep your shiny new iPhone protected from scratches and cracks, try one of these cases.
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.

Ever hear of Spokeo? No, it's not a city in Washington state. It's a website called Spokeo.com, and it marks the complete end of privacy on the internet. If your phone number and address has been posted in a phone book, it's on there. If you own a house, chances are there's a picture of it. If you have a Facebook profile, it's probably listed.

John Park poses a kitty conundrum: Who's going to feed the cat while you're on vacation? Using a motor from an old VCR, he creates an automated feline feeder. While building this Make: magazine project, John learned that newer VCRs have safeguard technology, limiting access to the motor. Watch John as he demonstrates his solutions to this challenge.

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

Need to keep people out of your precious room? Tired of all of those "do not disturb" signs not working? Locks just aren't cutting it these days? Safeguard your privacy with your very own electric fence. Remember Jurassic Park, when the kid got zapped by the electric fence? Think that, but in the doorway of your room.

Keep private info from prying eyes and earn some peace of mind when you safeguard your PC or Mac against nosy intruders. You will need several great passwords, virtual desktop software, snoopware blockers, a screen filter, a mirror, a healthy sense of paranoia, WPA encryption, and an understanding IT specialist.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

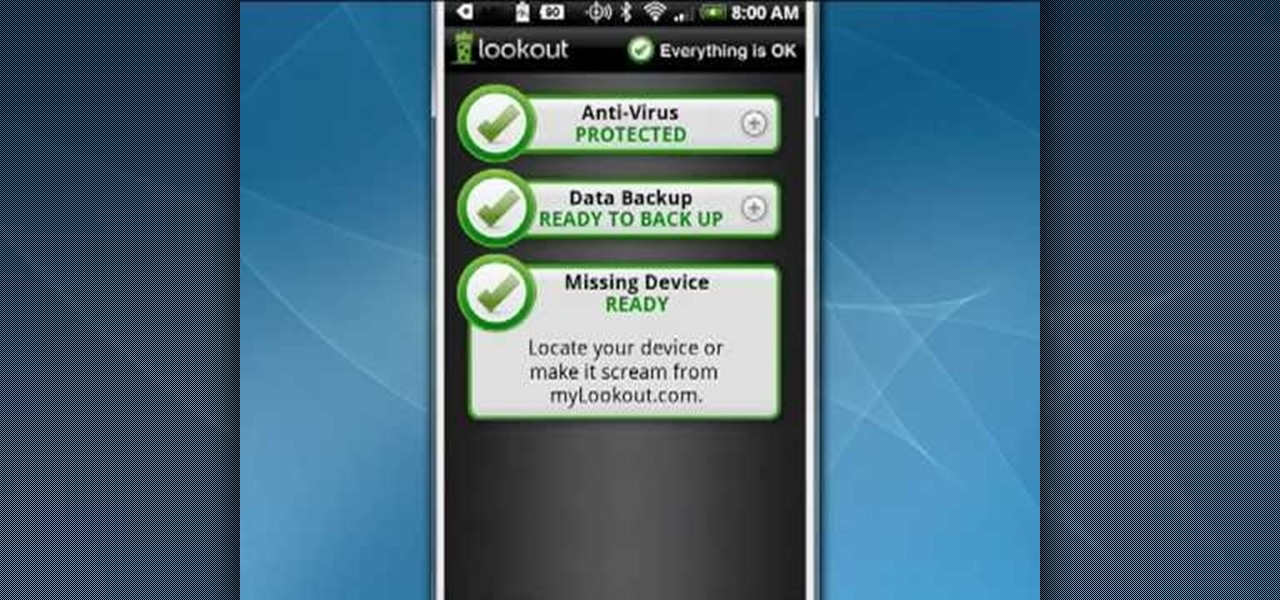
Your Android phone is a computer not unlike a laptop or desktop PC and it shares the same vulnerabilities. This clip presents a quick overview of how to safeguard against viruses and data loss. With the Lookout app, it's easy! So easy, in fact, that this video guide can present a complete overview of the process in about two minutes. For more information, including step-by-step instructions on how to adjust your own Facebook tagging settings, take a look.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

When wearables startup North officially unveiled its Focals smartglasses in October, the stylish frames strongly resembled, in form and function, Intel's canceled Vaunt smartglasses.

With the British exit from the European Union looming, the UK is looking to the auto industry to help boost their economy and secure jobs through the upcoming years. Today, Business Secretary Greg Clark and Transport Minister John Hayes announced the government investment of $136.7 million (£109.7 million) across 38 different automobile projects, as a part of the Plan for Britain.

Unlike in the physical world, on the internet you're actually able to shut people up and block spoilers of newly-released movies, your favorite TV shows, or a sports event you've yet to watch on your DVR.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

Google's personal messaging service Allo could reveal your search history and other private information to friends if the Google Assistant bot is called upon in chats, according to a story from Re/code.

Now that you've updated your iPad, iPhone, or iPod touch to iOS 8, there's a lot of cool new things to explore. If you felt a little overwhelmed from all of the detailed information available in our Coolest Hidden Features of iOS 8 post, then I've got a simple breakdown of all of the new features available with quick links to their walkthroughs and pictures, if available. Watch the short video roundup, or skip below for the list.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

I had my wallet stolen a few months ago, and I knew I would never see it again. My biggest gripe was not the credit cards in there, since they're easily cancelled, but the gift cards. I had some pretty good gift cards in there, and there's no way to get those back.

You really can't go wrong with Samsung Health when it comes to staying on top of fitness-related data. Its features help you keep track of workouts, track calorie and nutrition intake, and monitor your heart rate, just to name a few. And if you start exhibiting symptoms you've never had before, you can even use the app to find out more about what's wrong with you.

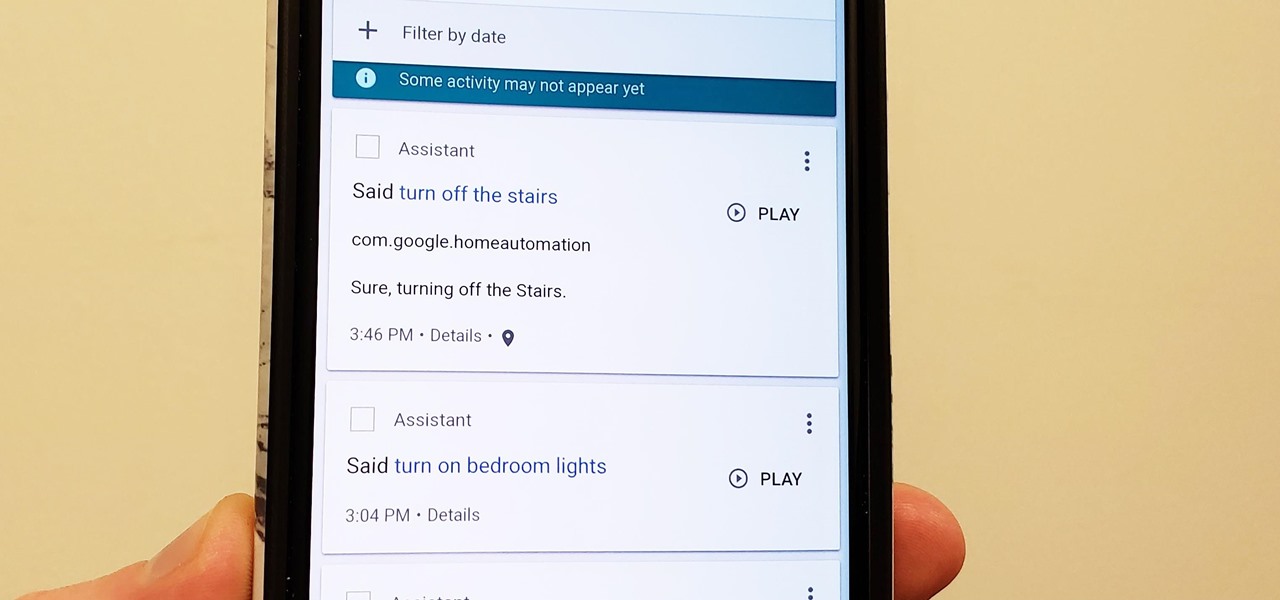
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

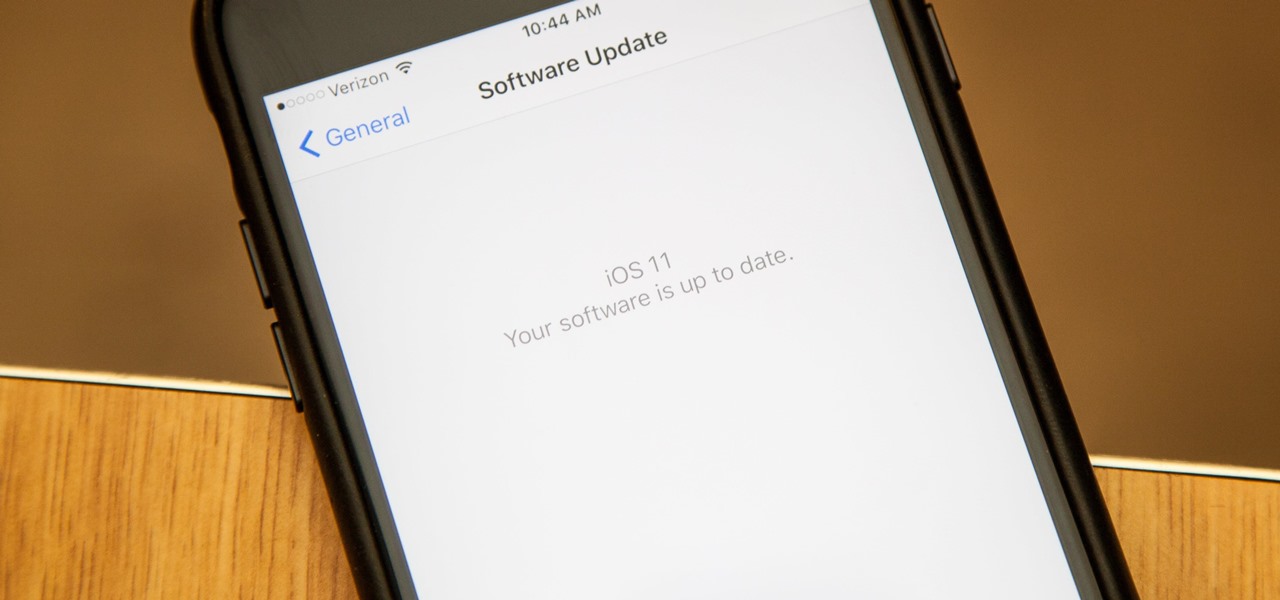
Apple introduced their new mobile operating system for iPad, iPhone, and iPod touch at WWDC on June 5, 2017, and there are a lot of great new features to try out. While the official version of iOS 11 was released to the public on Sept. 19, you can still sign up either as a developer or with the iOS Beta Program to get new versions of iOS 11 before anyone else does.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

The memories on your devices are precious, even if you don't often get a chance to revisit them. The worst thing in the world is when something happens to your computer or phone, and you end up losing some of those memories because your files weren't backed up or your microSD wasn't fireproof.

If you're interested in joining the increasingly popular and lucrative world of ethical or "white hat" hacking, you're far from alone. More and more coding and programming pros are turning to this field thanks to the high pay, countless opportunities, and exciting work environment.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.