Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

Watch how the F5 Networks BIG-IP Edge Client solution gets you connected automatically when you boot/start up your computer along with seeing the browser based version of the F5 BIG-IP Edge Gateway. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.
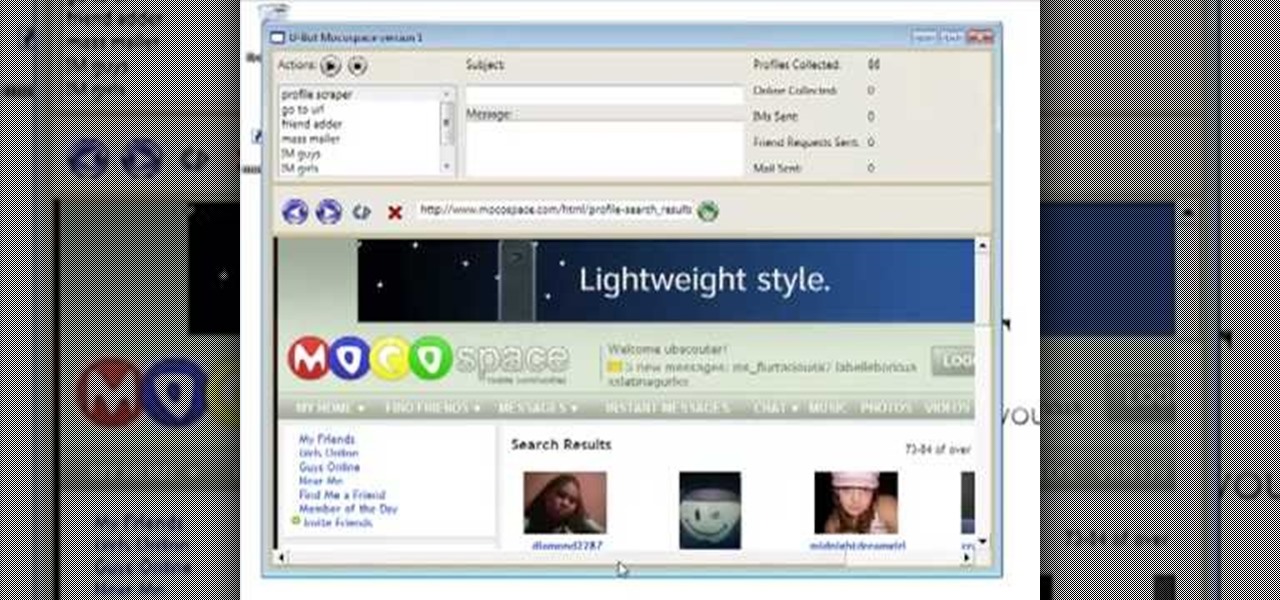
MocoSpace is a newly emerging social network, aimed and designed primarily for users of smartphones and other mobile devices. This tutorial shows you how to use the Ubot software to work with and monitor activity for your clients and customers on MocoSpace.
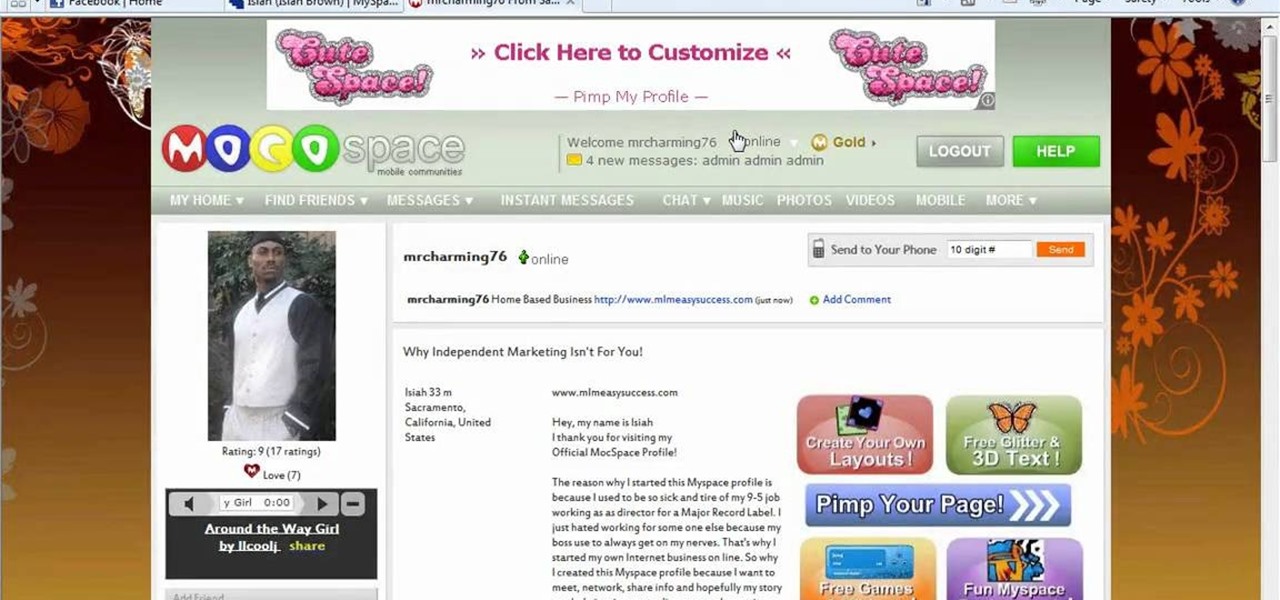
MocoSpace is a relatively young social networking site, primarily designed for people who have mobile phones or smartphones. Make sure you can stay connected to all your prospective customers and clients by using the advertising tools and opportunities that MocoSpace offers!
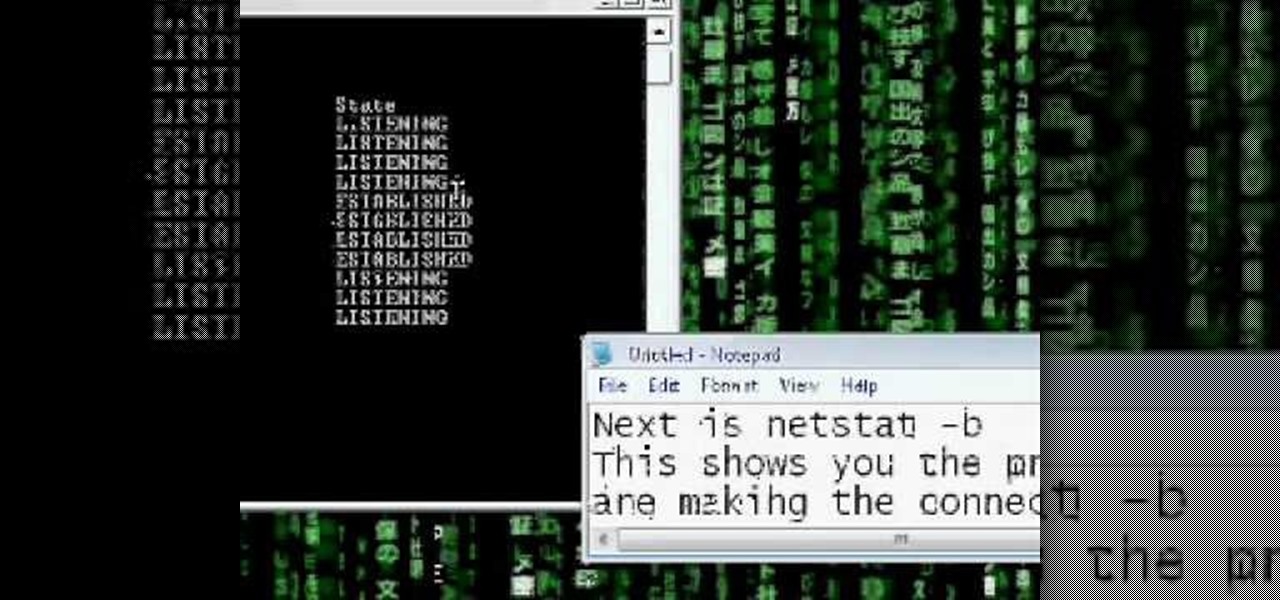
Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Thinking about renovating your bathroom? It's a lot easier than you might think to remodel your bathroom. Find out how to build your own water-tight concrete base for a shower with this tutorial from the DIY network. Watch this how to video and you can build the concrete base to the shower in your bathroom in no time.

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

Elie Krieger from Food Network bakes up a scrumptious chicken pot pie. Her version will give you a healthy boost because she added extra vegetables and cut down on the fat. This southern dish is sure to warm up tummies everywhere and you can customize the ingredients based on your family's tastes. For example, you may want to use turkey instead of chicken, or possibly beef. Maybe your family likes different vegetables. This particular recipe uses chicken, onions, carrots, celery and green bea...

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

The experts at Bunning's have come up with a few tips for the consumer to consider when they are next in the market for paving equipment. Find out if the job needs a solid block paver or a thinner grade paver. Preserving the tools once they leave the store is in your hands. Last, but not least, watch the weight!

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to packet sniff networks with the fundamentals.

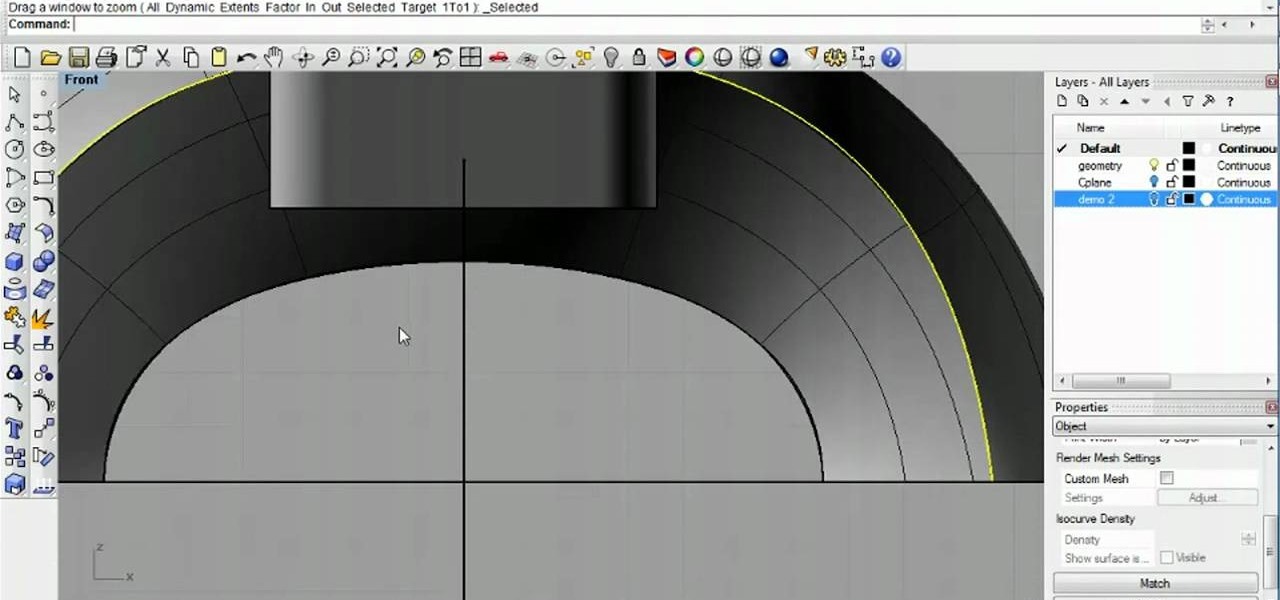
See how to create complex surface shapes using Network Surface in Rhinoceronous 4. Whether you're new to Rober McNeel & Associates' popular NURBS-based modeling application or a 3D arts professional just looking to better acquaint yourself with Rhino 4's new features, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, watch this free video guide.

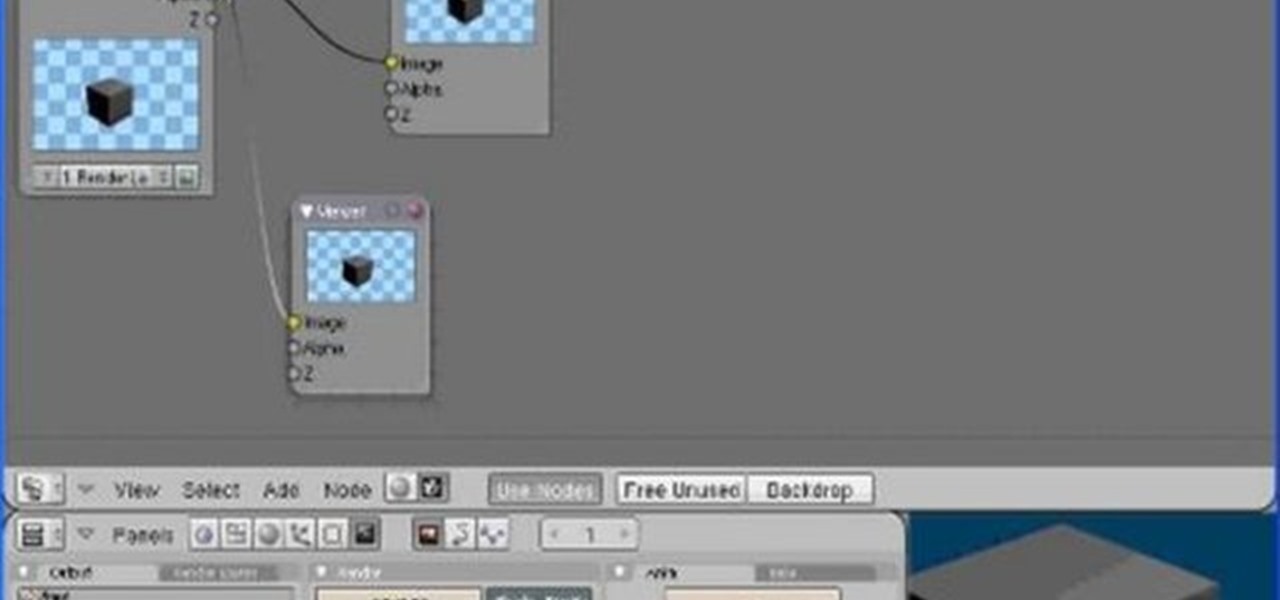
Conceptually, what is node-based compositing and what do nodes do? This clip uses the factory analogy to convey the concept. Blender can process video, images, sequences, and families of images in a directory. Then you'll fire up Blender and talk about threading nodes and how images are duplicated and routed through the compositing network ("noodle"), how threads are created between sockets. Creating threads, cut threads. The clip also points out common threading errors and misrouting threads...

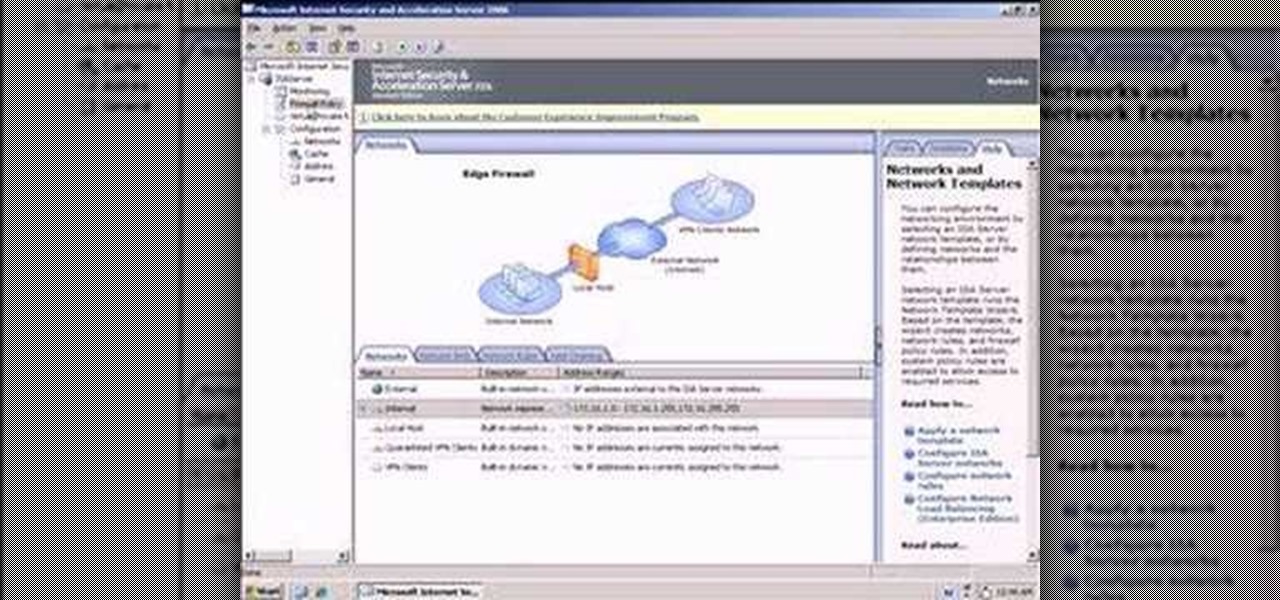
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

In this video tutorial you will learn to use Photoshop to create a shiny reflective logo in a web 2.0 style. Not sure what Web 2.0 is? It generally refers to a perceived second generation of web-based communities and hosted services — such as social-networking sites, wikis and folksonomies — which facilitate collaboration and sharing between users.

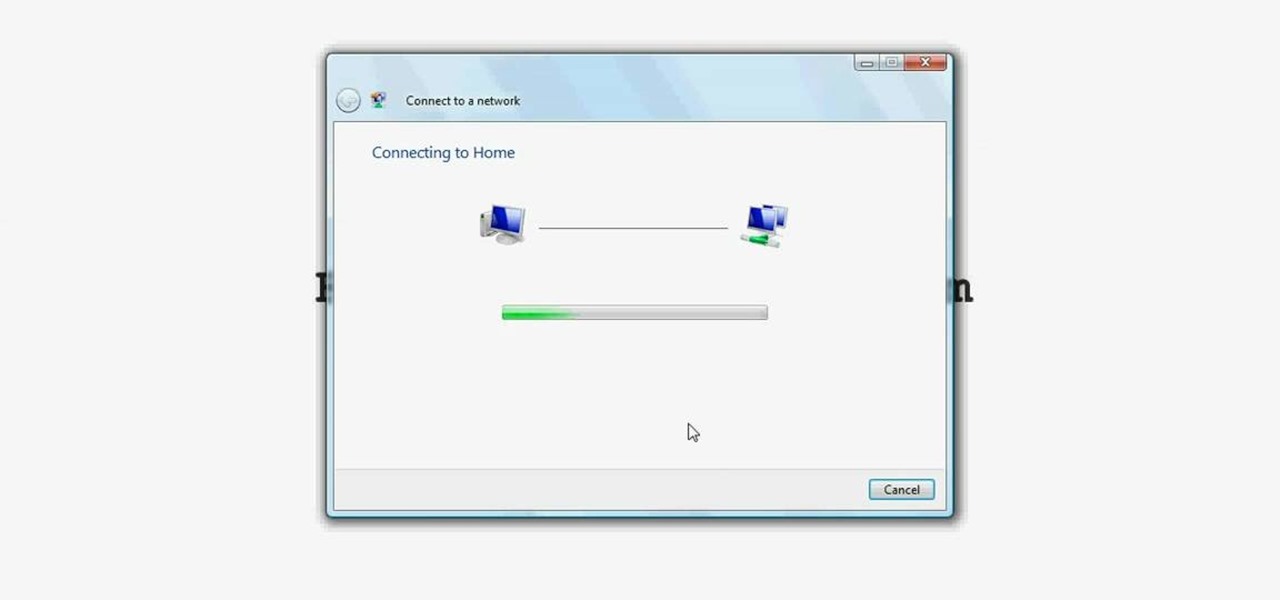
Wireless networks are really the only way to go these days. With WiFi you can access the world wide web from almost anywhere, at anytime, and not have to worry about annoying wires or cords. In this tutorial, learn how to set up a wireless connection in a Windows Vista based machine.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to program a USB development board for cheap.

This clip presents a walkthrough of how to go about creating a particle based explosion in Houdini 10. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

Here's another video tutorial from Needle 'n Thread for a hand embroidery stitch called Roumanian couching, which is used primarily as a filling stitch.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

In this video tutorial, viewers learn how to read Google email offline. Begin by logging onto your Google account. Then click on Settings and select the Labs tab. In the Offline headline, click on Enable. To not grab all your emails, go to the Offline tab and select which messages will be synchronized with your computer, based on labels and time frame. This video will benefit those viewers who use Google mail, and would like to learn how to read their emails offline in case their internet con...

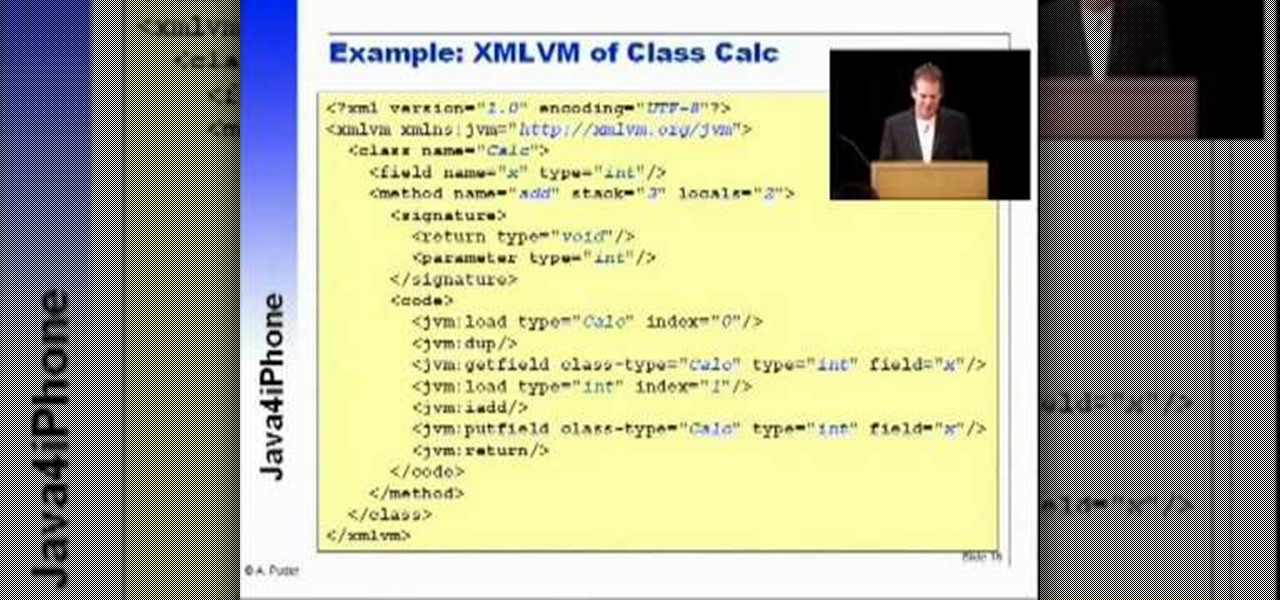
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to homebrew and hack the PSP.

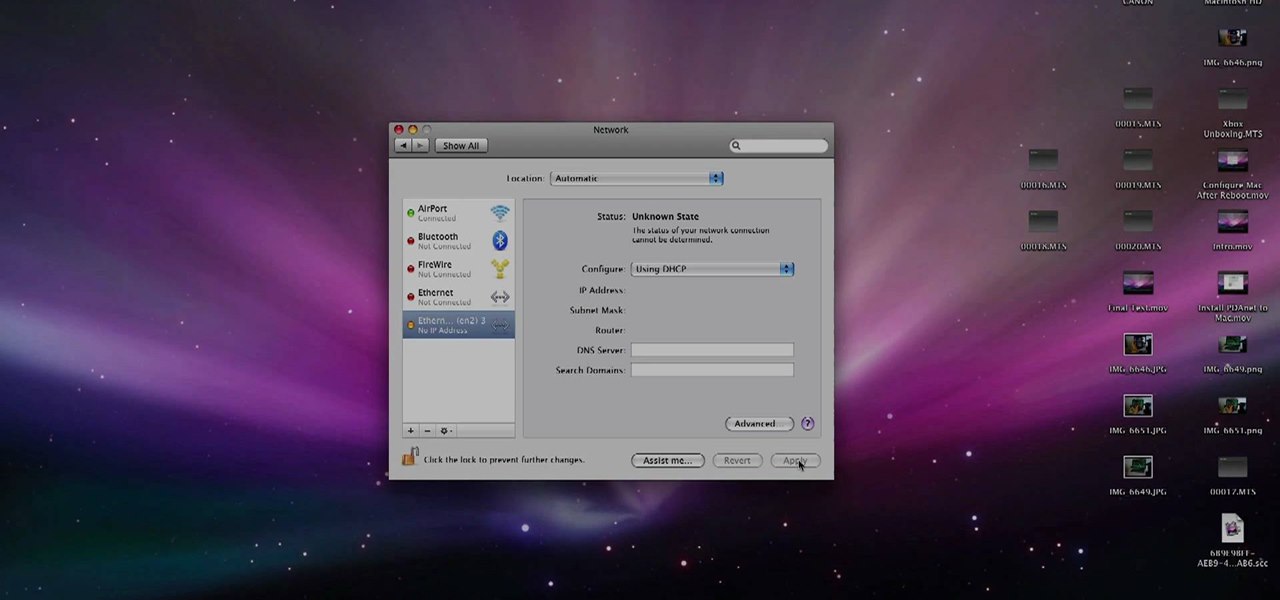
From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to set up a WiFi network on a mac, For Dummies.

Sure you can make Christmas punch this year, but that's just plain boring! Go even more traditional with Wassail! A fantastic alcoholic drink that was primarily consumed in the 14th. century by Anglo Saxtons. In this video you will learn how to make the Wassail with a fantastic recipe!

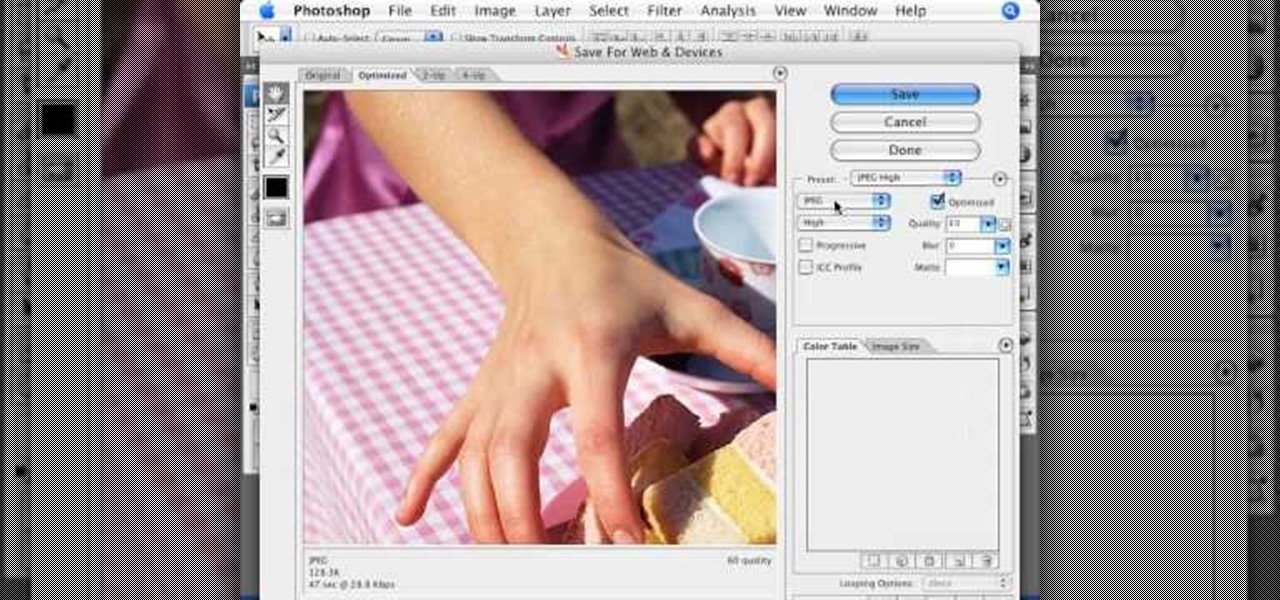
In this video tutorial by photoshopuniverse, from Free Photoshop Video Tutorials, shows you how to automate the process of resizing images using Photoshop, primarily for sending over the internet. The guide takes you through the step by step process of creating a new action to record the process of resizing an image. Using this recorded action, you will learn how to go about applying that action to an entire folder, which will resize all the images contained in that folder.

While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

According The Venture Reality Fund, the introductions of Facebook's camera platform and Apple's ARKit catalyzed increased activity among companies developing consumer applications.

At the WinHEC Shenzen 2016 Keynote, Microsoft showed off a system running Windows 10 smoothly on an ARM processor. This could be great news for developers of mixed reality software.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

In this five-part tutorial, learn how to make the perfect pizza crust with chef, Mark Gill, the executive chef at Little Creatures Fremantle WA. In each of these five short & informative videos learn how to start by mixing the ingredients by hand, how to knead the dough, shape the dough balls then pizza base, and finally, how to toss the pizza like the professionals! Make the perfect pizza dough for your pizza from today forward!

If you have an Android-based cell phone and want to tether it to your MacBook, MacBook Pro, or other computer running Mac OS X software, the secret lies in a little application called PdaNet.

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Go beyond the traditional 3D workflow to an immersive creative experience with the software Modo, created by Luxology. Modo is the next evolution of 3D modeling, painting and rendering for Mac and PC. Modo includes 3D sculpting tools, animation and network rendering, and advanced features such as n-gons and edge weighting.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

If you don't want to be something scary or creepy for Halloween, how about going as a cute little kitty cat instead? This is primarily for children, and shows you how to make your child up to look like a cat. Meow!