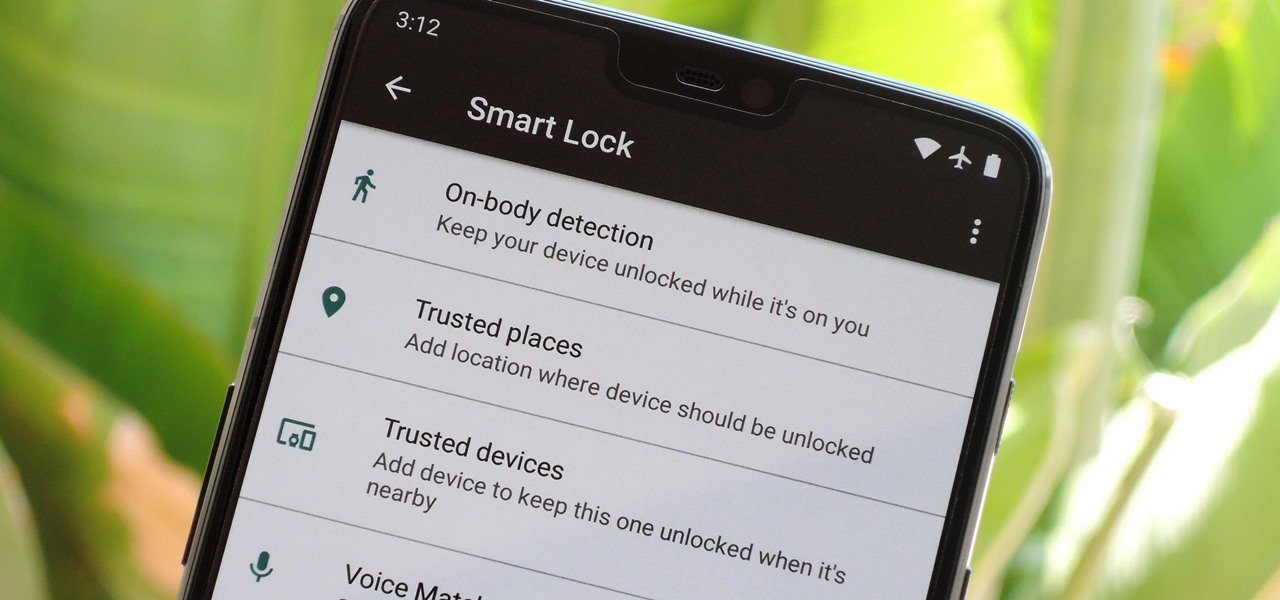
When it works, Android's Smart Lock feature is incredible. There's no need to enter your PIN when your phone "knows" it's in your hands — just unlock and go. But Smart Lock, particularly its Trusted Places feature, can be finicky sometimes.
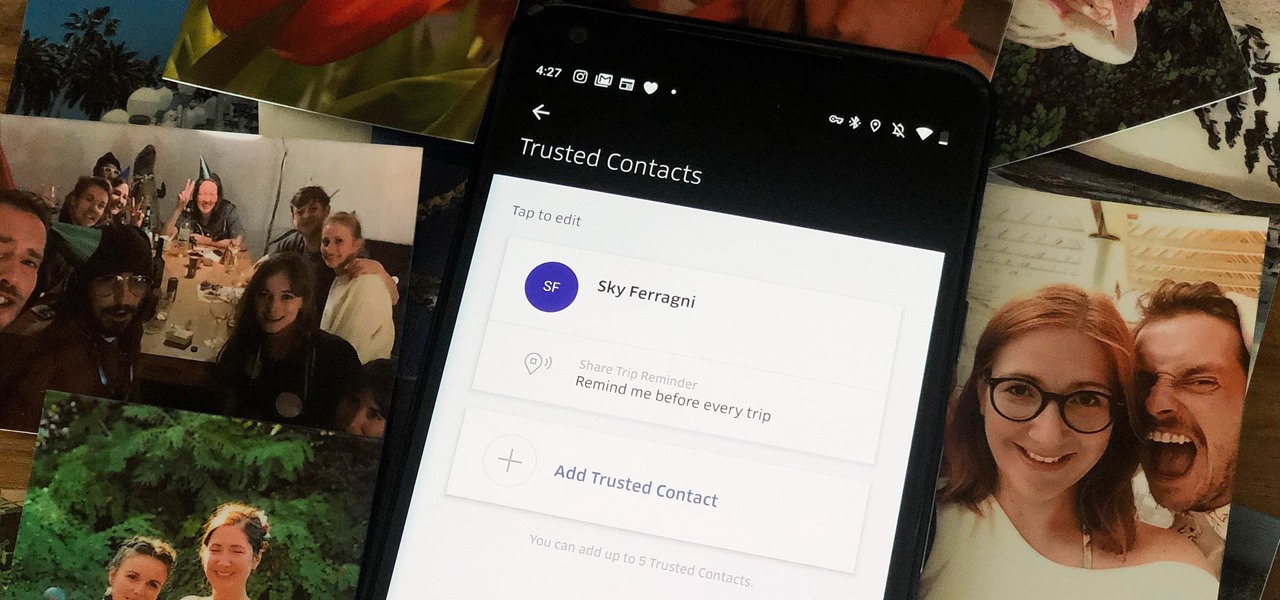
When you're riding in an Uber, on your way to meet family or friends, they may want to know where you are exactly to see how long until your arrival. On the other side of the coin, there may be times when you want to tell family or friends where you and your Uber car are without them asking, like when you're in a dangerous situation. Uber makes this easy, as long as you set it up first.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

This tutorial will make you think step by step how to add a plug-in (Firefox Add-on) to your Mozilla Firefox browser that will allow you to download videos and music from YouTube and similar sites. The add-on that is used is called Video Downloadhelper. This is a trusted author and a trusted download. To begin this tutorial you will first need Mozilla Firefox and flash. This will enable you to go through the video and help ensure that YouTube will play the video you are trying to download.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

Watch this video to learn how to cheat on a test with help from your iPod. Ask a trusted friend for their notes/answers the night before. Then at your computer, just type up their notes/answers, or the important parts, and then save it in your computer as "How to make Grandma's Secret Fudge Brownies.txt" . Now plug your iPod into your computer and click Start- My Computer- (someone's iPod- Notes. Now you will need a separate window. Click Start- My Computer. Now find "How to make Grandma's Se...

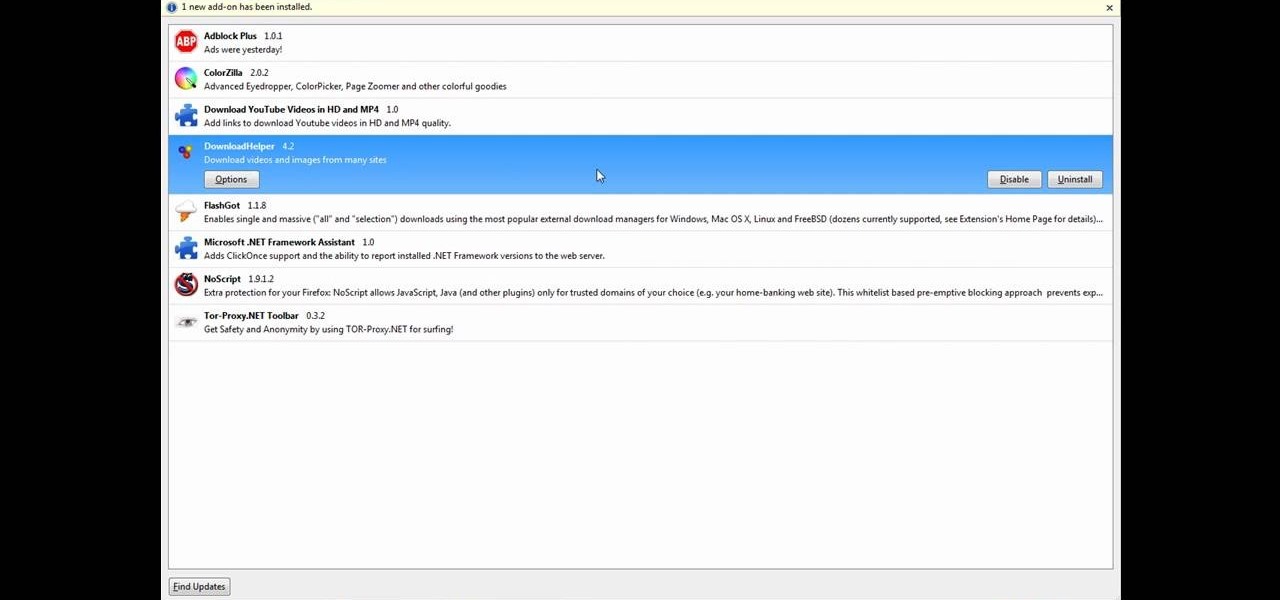
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

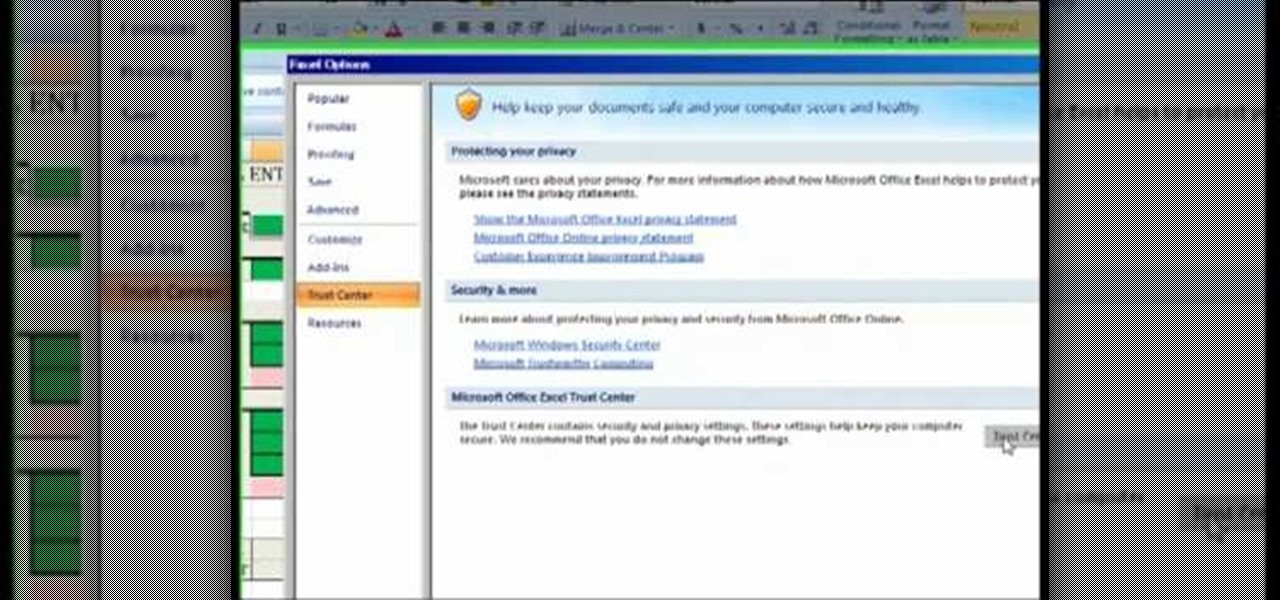
The Costsheet demonstrates how to enable macros in Excel 2007 to run correct spreadsheets. First, open up the spreadsheet. Make sure that the macros are enabled. If they have not, enable the macros by placing them in a trusted source by saving them in a particular folder. You can also choose to recognize the publisher as a trusted source. Click the office button and scroll down to Excel options. Click on the trust center option and go to trust center settings. Then, view the trusted locations...

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

Learn how to do an air - aereo on your BMX. Step-by-step tips from a trusted BMX'er himself.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

Keep your possessions safe from thieves with these tips. You Will Need

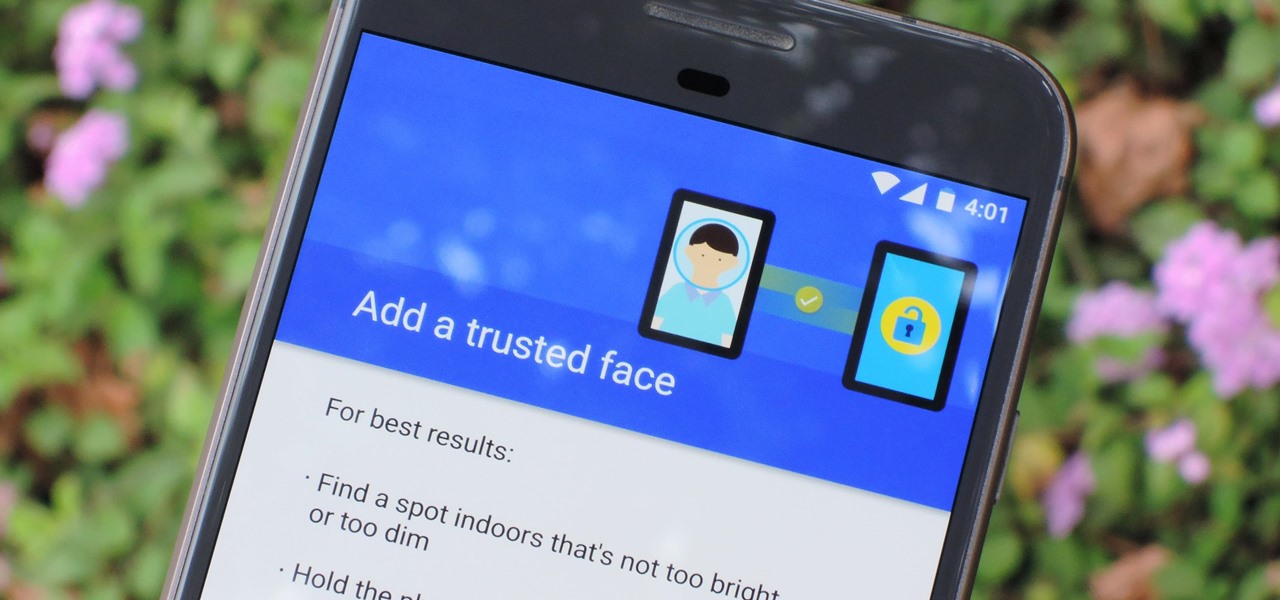
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

One of the most challenging, arduous parts of gardening is weeding vegetables that are close to the ground. Cabbage, for instance, leafs out near the earth and can be fiendishly tricky to weed. In this Growing Wisdom gardening tutorial, you'll learn about some of the tools that can help you weed those hard-to-reach spots without breaking your back in the process.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

The supra combination lock box has been one of the most trusted door locks for the past forty years, and is commonly used by real estate agents for protecting their houses. Generally a supra combination lock operates with a four-digit password.

Garmin is a popular and trusted brand of GPS devices. In this video, learn how to enter destinations and perform other basic tasks with a Garmin Nuvi 750. This video shows you the Nuvi 750 but all of the instructions should also work with other Garmin models. GPS is fantastic for traveling to new destinations, getting out of a lost situation and finding unknown places faster.

Abusive relationships are unhealthy and should be remedied immediately. There are many steps that can be taken to help end an abusive relationship.

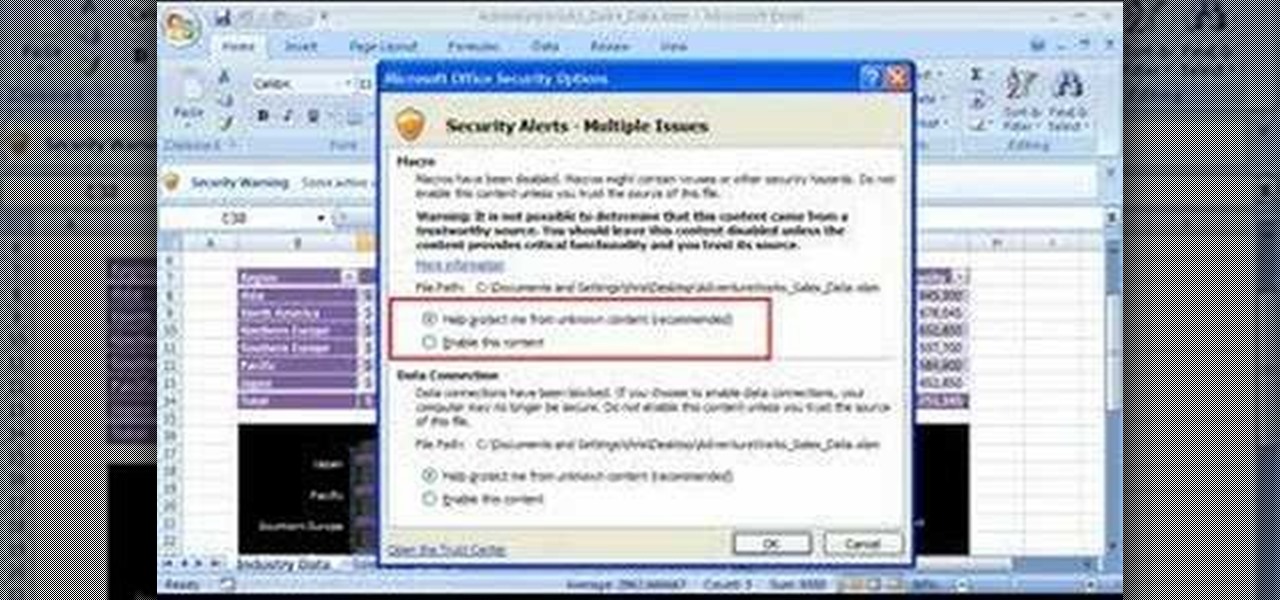
Not sure what to do when you get a security warning about a macro? What are macro security settings, the Trust Center, and Trusted Locations anyway? Watch this instructional video to learn how to enable macros and make informed security decisions that can help you keep your computer safer while you work in Microsoft Office Excel, Outlook, Word, Publisher, PowerPoint, and Visio 2007.

The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T has centered around the new face unlock method. Thanks to a clever hack, you can now get this feature on almost any phone!

This video tutorial from JdudeTutorials presents how to download a torrent for the first time.To start, open your Internet browser. Browse to utorrent web page.Download and install uTorrent client version, suitable for your operating system (MacOS or Windows).Once you've installed application, browse to The Pirate Bay.This is the largest torrent source in the world.Check Video option under the search bar and type family guy (as an example).Click Enter. A list of torrents connected to family g...

In this episode of Growing Wisdom, Dave Epstein and fiber sculptor Susan Barrett Merrill discuss how to spin wool. Barrett Merrill demonstrates the spinning wheel and explains how wool is transformed into yarn. She also shows some of her own work and explains her artistic process.

Your driveway can make a big difference in the appearance of your house. As nice as it would be to have a brick, slate or cobblestone driveway, those are expensive options that not everybody can afford. In this episode of Growing Wisdom, you'll learn how to use a comparatively inexpensive process called street printing to really class up your driveway by creating the illusion of brick and other textures.

Every day, the average American throws away about four pounds of trash. But a lot of your daily trash could actually be very useful in the garden, as composting. In this episode of Growing Wisdom, Dave Epstein shows you how to use a three-bin composting system.

If you've grown tomatoes from seed, perhaps you've wondered how the seed company extracts those seeds. In this episode of Growing Wisdom, Dave Epstein walks you through a process known as sluicing. Using sluicing, you can extract vegetable seeds yourself.

When you head to your neighborhood gardening center to find a shade tree for your garden, the variety of choices can be pretty overwhelming. There are so many kinds of trees, and each of those trees has its own varieties. In this clip, Dave Epstein from Growing Wisdom will help find the best shade tree for you.

A soil block maker is a cool device for starting your seeds. All you do is fill a container with soil and use the block maker like a cookie cutter. Then you'll have little blocks of soil to plant your seeds in, and you can easily transfer the block to your garden. Now stand back and watch your plants grow!

The vinca, or periwinkle, is a hearty flower that adds a lot to any garden. It comes in a variety of colors, and grows in the sun as well as the shade. But they're so hearty that you have to watch them, or they'll start springing up where they're not supposed to. In this video, Dave Epstein from Growing Wisdom walks you through using periwinkles in your garden.

With low garden tunnels you can protect your plants from frost and insects, and you can overwinter your crops. In this episode of Growing Wisdom, host Dave Epstein will look at how to build a garden low tunnel. He'll focus on using the Quick Hoops Bender for the project.

A climber needs to consult with an expert when choosing and fitting harnesses for rock climbing. Different harnesses have different uses and features. Learn how to use a harness for rock climbing in this climbing video tutorial. Take action: use a harness, go with a trusted partner, and adjust the harness accordingly. Josh, the instructor in this how-to video from Live Strong, is an avid climber that resides off the coast in central California. He has managed for a mountaineering sports compa...

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.