If not the future of computing in general, augmented, virtual, and mixed reality certainly will change the world of gaming. If you want to try your hand at shaping this evolved medium, the Unite Europe conference posted a talk that explains the first things you need to learn to develop holographic games.

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

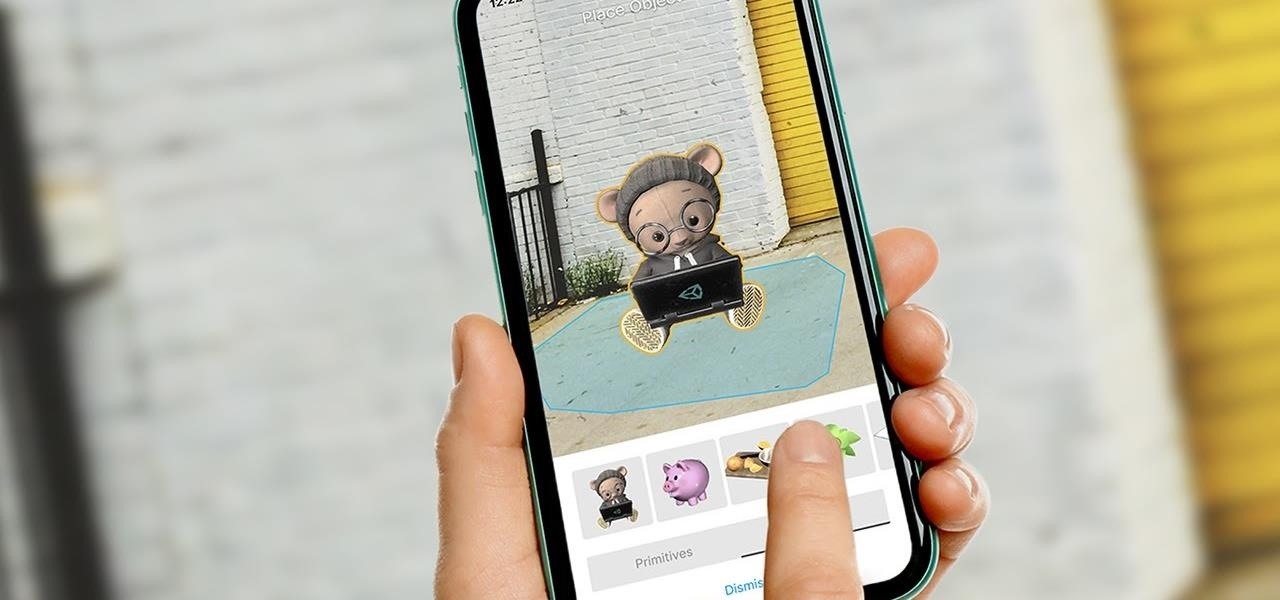
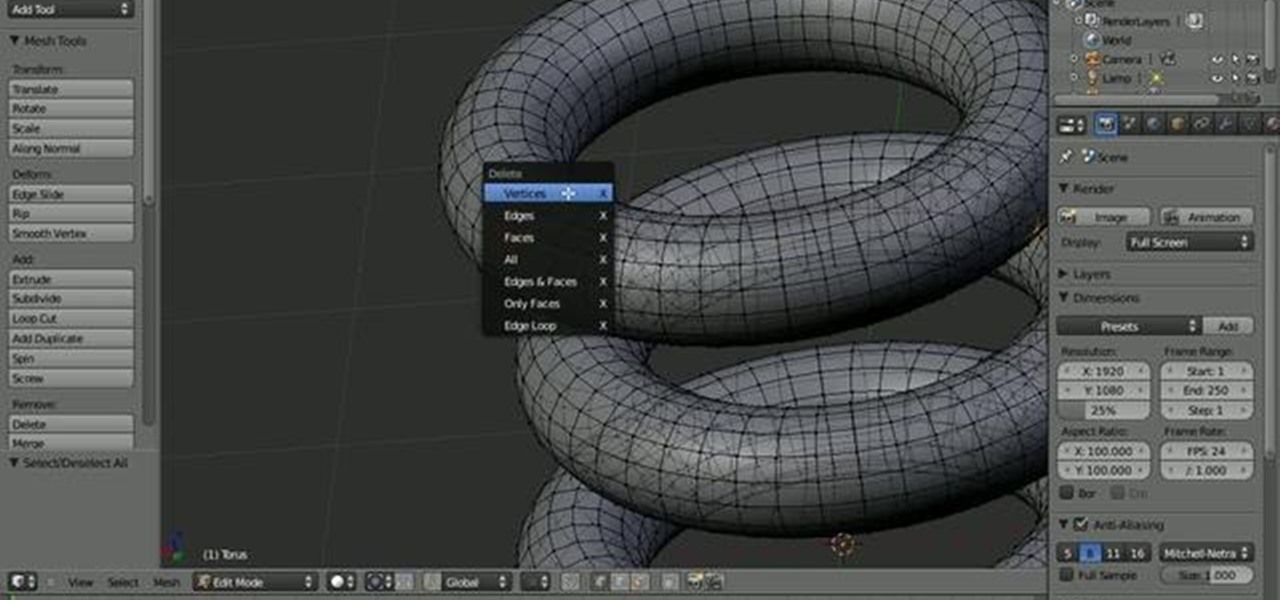
After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons.

Hi All, I have a new VFX tutorial online - this time I show you how to create a 3D laser in After Effects using the Trapcode Form plugin.

Unity often reminds us that the majority of AR apps and experiences are built with the Unity 3D engine, and now the Unity MARS service, which facilitates easy AR creation for seasoned coders and newcomers.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

Today, on our first episode of Steampunk Research and Development, we'll be interviewing Thomas Willeford, owner and operator of Brute Force Leather. Thomas is a man of many talents, and has worked in a vast array of fields. His Steampunk work can be seen in his book, Steampunk Gear and Gadgets, as well as on the television show Castle. Thomas is also one of the creative consultants on the upcoming television show Lantern City.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

If you use iCloud Photos, Apple's iCloud link feature is meant to make sharing multiple photos and videos faster and easier, but it's not as great as you might think. Luckily, there's a way to stop your iPhone from creating them automatically, as long as you're running iOS 13 or later.

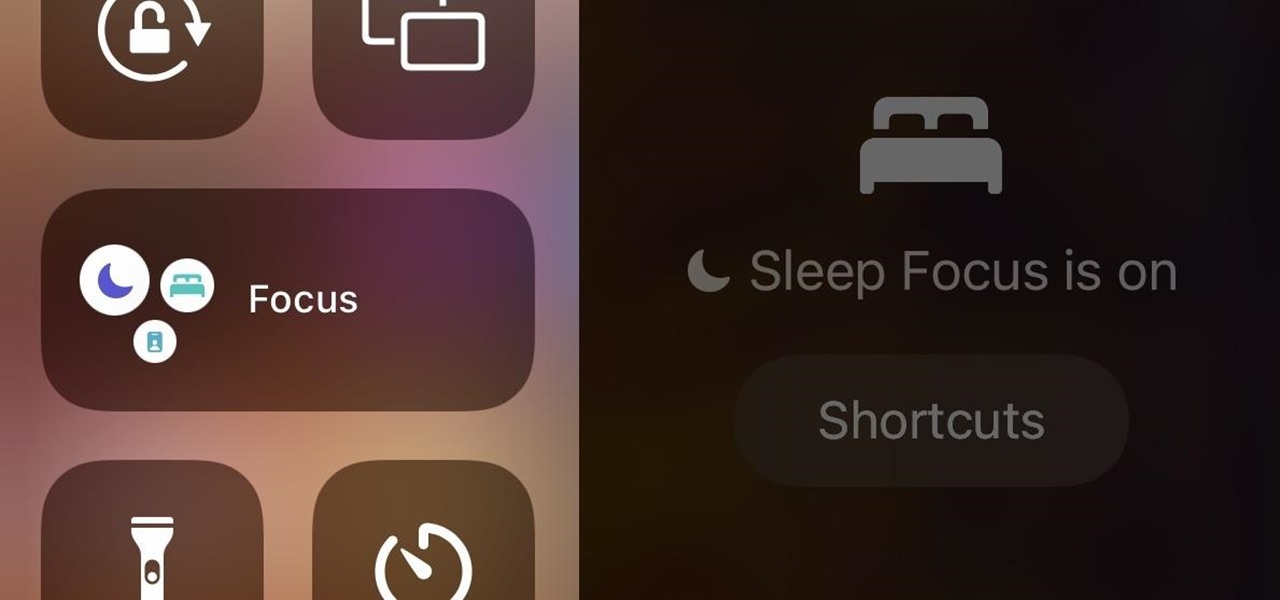
In iOS 15, Apple unveiled a new feature called Focus, an extension of Do Not Disturb that lets you focus on the one thing that's important at any particular moment. It does so by minimizing distractions from your iPhone and other Apple devices, but there's a lot you should know about setting up and using Focus on your iPhone or iPad before you dig in.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.

Chicken and waffles are so yesterday. Well... it's not that we won't always love them, but it's time to move on to bigger and better things, such as the pizza waffle.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

Using a dish, liquid dish soap, a lamp, and a candle, you can get rid of fleas in your home with barely any effort. A well-placed flea trap can be the answer to all of those annoying fleas your pet may be bringing inside.

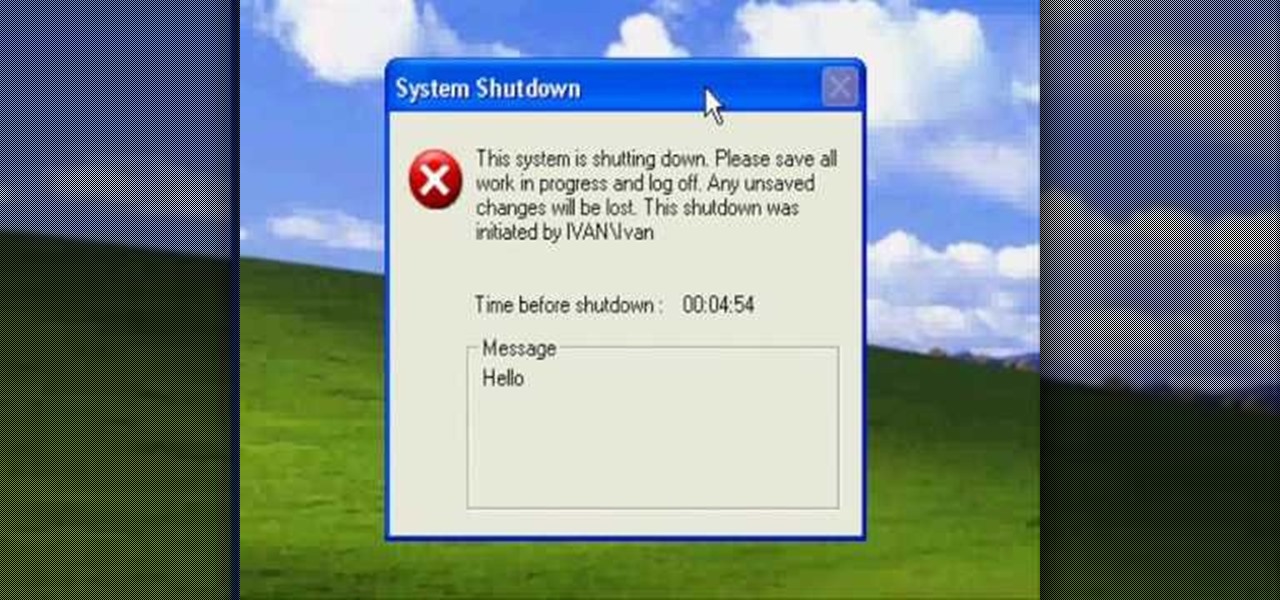
Okay, what's the greatest prank you can play on a friend in this day of technology? Mess with his computer!

Pandora is a fantastic website that will let you listen to music for free. One of the greatest features of the music service is the ability to create your own station so you can listen to your favorite songs and even discover music you'll like. This segment will walk you through the process of creating a Pandora station.

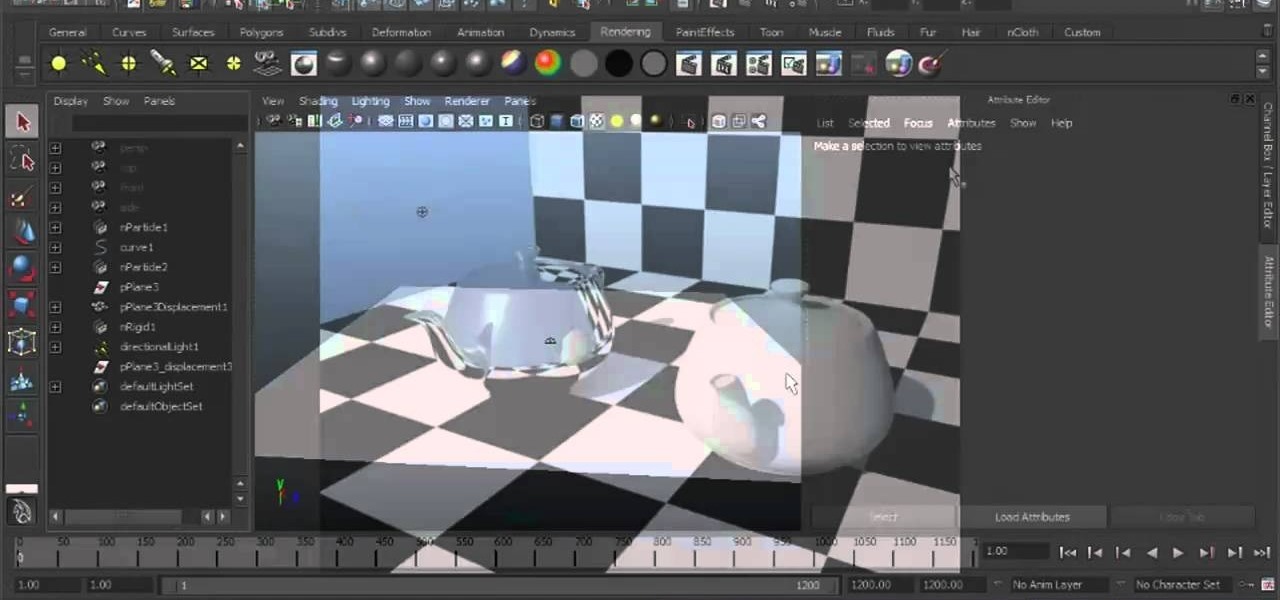
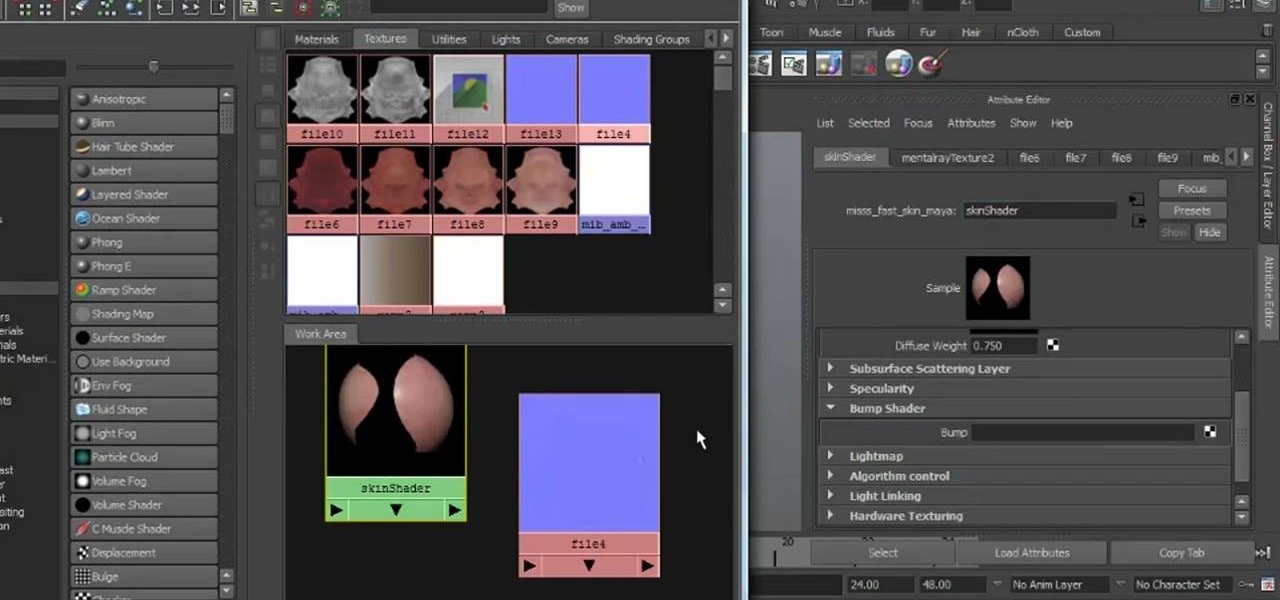
In this tutorial, we learn how to work with diffuse reflections when creating textures and shaders within Maya 2011. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the Maya 2011 workflow, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this video guide.

Before you can work in Blender, you'll have to learn how to work with it. Fortunately, this guide will show you everything you'll need to know to get started creating your own models within Blender. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the folks at CG Cookie. For more information, ...

Ramses and Tara from Skills of the Game explain why creating an attention-getting headline is important in online dating, especially on dating sites that emphasize a headline rather than a thumbnail picture. They explain how and why a poor headline can diminish a person’s standing. They give examples of bad headlines, and suggest writing headlines that are either lighthearted or call the reader to action. After giving a few examples of good profile headlines, Tara explains why the most import...

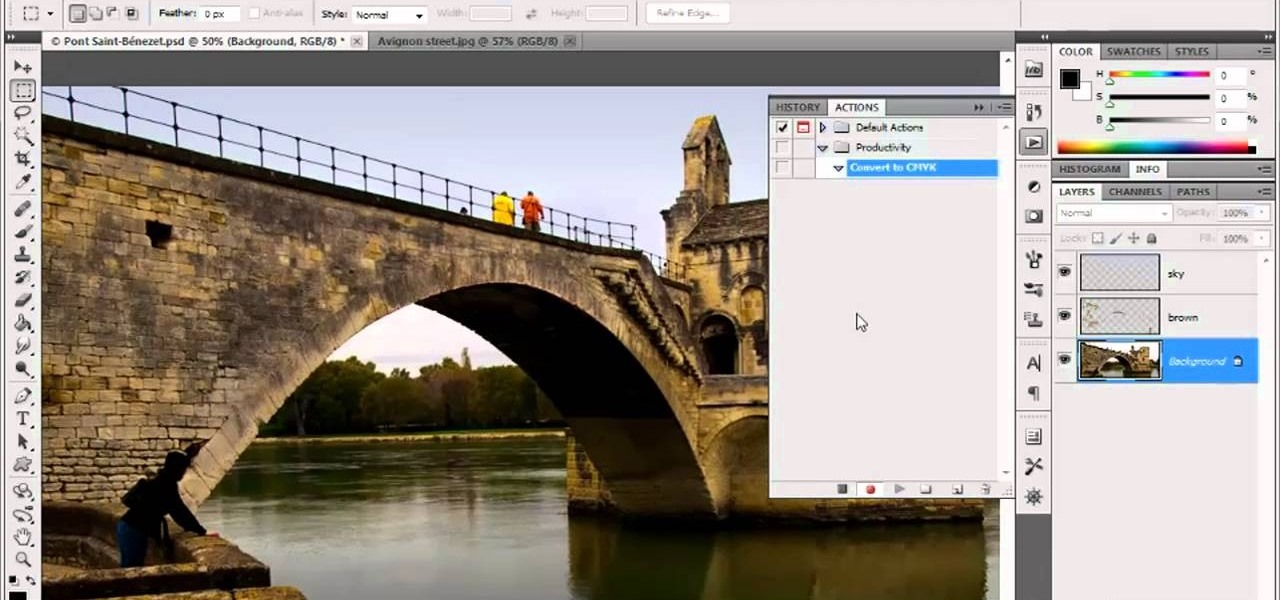
In this video tutorial, we learn how to create custom actions to automate repetetive tasks within Adobe Photoshop CS5. Whether you're new to Adobe's popular raster graphics editor or a seasoned designer looking to better acquaint yourself with the new features and functions of the latest iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this video guide.

In this tutorial, we learn how to work with normal maps within Maya 2011. Whether you're new to Autodesk's popular modeling software or a seasoned 3D artist just looking to better acquaint yourself with the Maya 2011 workflow, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this video guide.

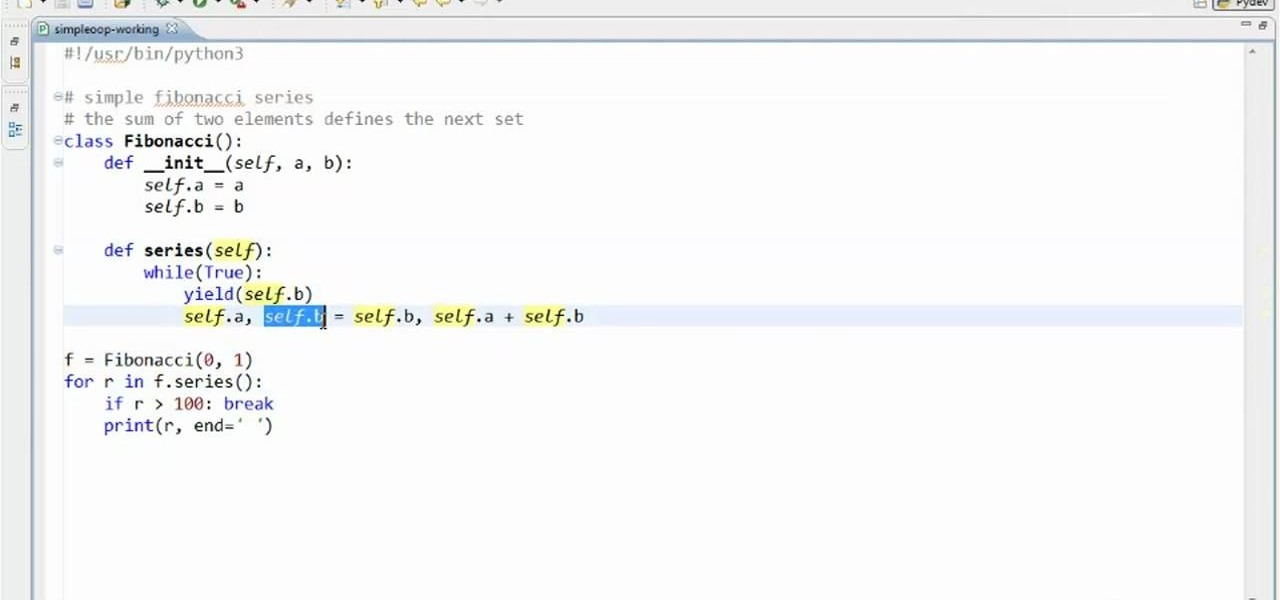
Need a class on how to use classes in Python? You're in luck. Whether you're new to the Python Software Foundation's popular general purpose programming language or a seasoned developer looking to better acquaint yourself with the new features and functions of Python 3.0, you're sure to benefit from this free video programming lesson. For more information, including detailed, step-by-step instructions, watch this video guide.

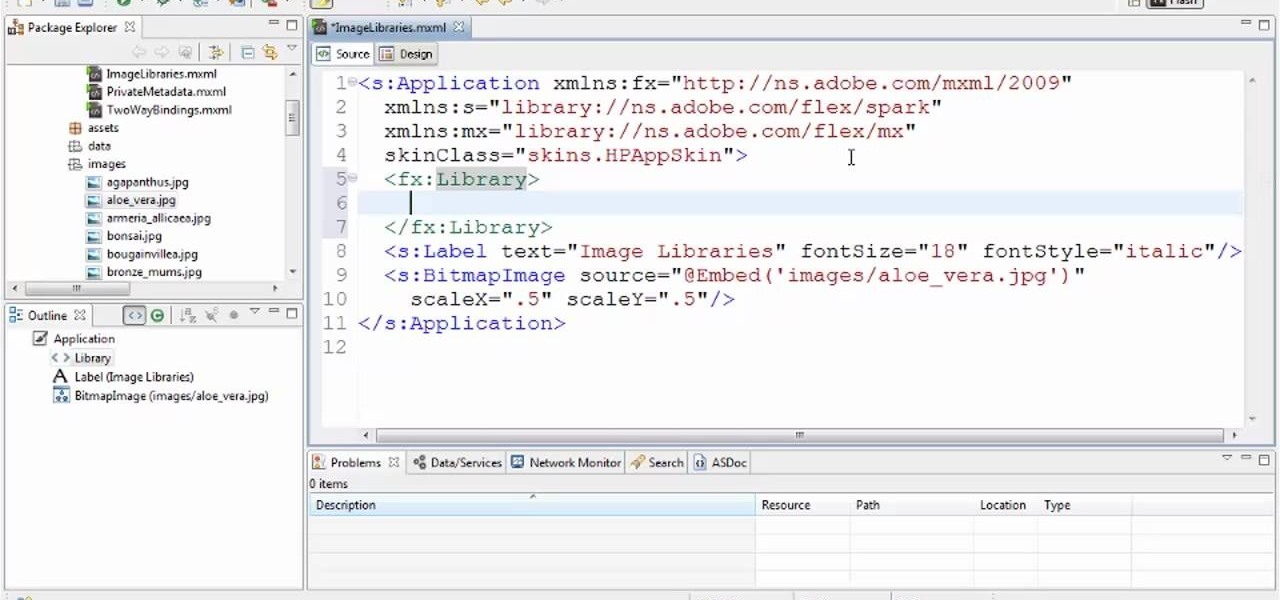
See how to create custom image libraries when working in Adobe Flash Builder 4. This clip will show you what to do. Whether you're new to Adobe's popular Flash IDE (previously titled Adobe Flex Builder) or simply wish to become better acquainted with the program, you're sure to find benefit in this free video software tutorial. For more information, including specific, step-by-step instructions, take a look.

Does one of your coworkers at the office really make you mad? Do you want to mess with them at the office without having to destroy any property? This video can help. It will show you how to quickly create a fake wallpaper on someone's computer with Windows XP, which will infuriate them for a long time if they aren't very computer-saavy or familiar with this prank. Try it out and marvel at the hilarious results.

There are different techniques to apply the glue on the latex sheeting, none of them is right or wrong. All that matters is what works best for you. This latex tip is helpful for making fetish clothing or latex fashion pieces. Latex clothing is integral to fetish clothing and used frequently in BDSM or S&M sex.