With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Sometimes we need to share screenshots, but don't want to reveal the entire screen. This usually requires some editing that isn't typically easy to do on a smartphone. BlackBerry recognized this issue and created a tool called Redactor that makes it easy to hide your data before sharing.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

HTC is working on another flagship device that's expected to be released in mid-April. After the disastrous reception of the recently released HTC U Ultra and HTC U Play, this new model could be the true HTC 10 successor we've all been waiting for.

These days, most images we post online or share with others come from our smartphones. Whenever personal data is in them, such as debit card numbers, addresses, phone numbers, passwords, and other sensitive information, it's easy to jump into your iPhone's markup tools to black out the text before sharing. But a digital marker may not hide everything.

We live in a time where privacy is rare and our files can be easily accessed by just about anyone. Having your phone protected by a passcode is great, but if someone figures it out, they can easily access anything on your phone.

Tuesday gave us what I am dubbing a "patent dump." Can you blame me? The U.S. Patent Office released 56 patents from Apple. 56! Among them, there are patents confirming Apple is working on embedded Touch ID, edge-to-edge displays, and a 3D camera system (surprise, surprise). Some of those things we've heard rumors on for some time, but what is new is one of the patents hidden amongst the bunch, describing an Apple-made avatar system. One whose end-goal is to reflect your current emotional sta...

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

We go to such great lengths to secure our smartphones. We put passwords on our lock screens, encrypt our data, and install anti-theft programs, but it's never enough—someone, somewhere, will find a way around any protective measure you use, no matter how sophisticated.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

This video speaks about removing sensitive information in Adobe Acrobat 9. The viewer might get a very obvious idea of removing sensitive information by redaction. Redaction is the process of permanently removing sensitive information from a PDF file. This is done by opening the Advanced menu, clicking "Redaction" and then clicking "Show redaction tools", which can be in any format, images or text. The viewers will definitely get a clear idea of removing such sensitive information by redactio...

Have a file or a number of files too sensitive to be stored on your desktop hard drive? Thwart would-be snoopers with an encrypted USB flash drive. This free video tutorial from the folks at CNET TV will show you everything you'll need to know to create your own password-protected thumb drive directories.

TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

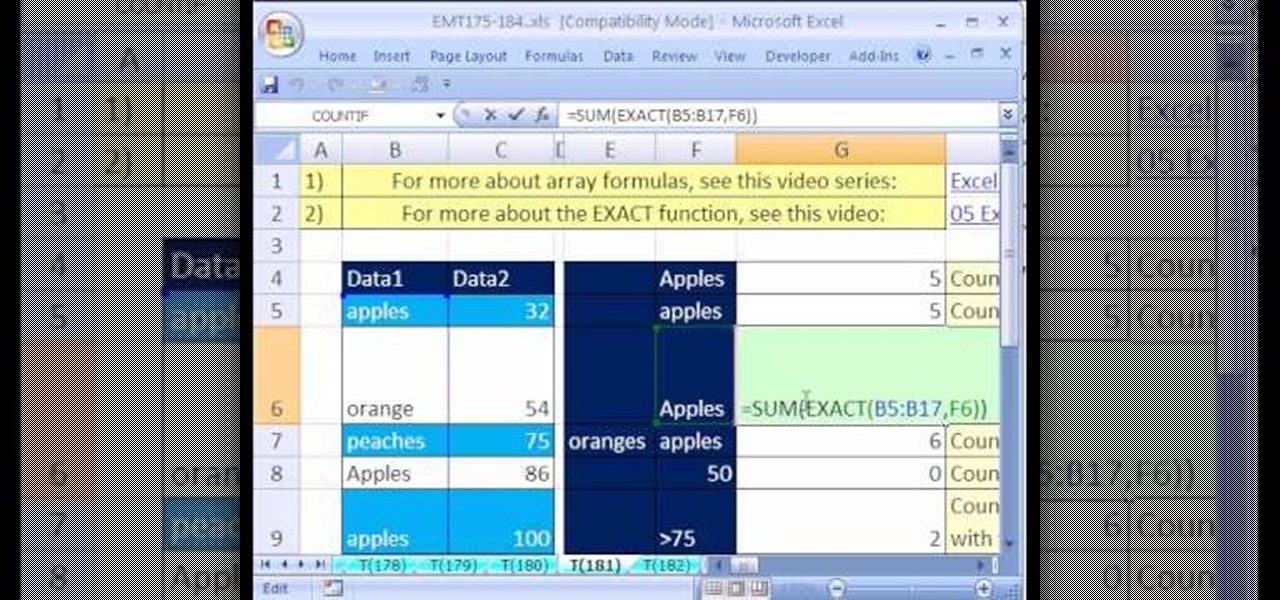
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 181st installment in their series of digital spreadsheet magic tricks, you'll learn how to count words (case sensitive) using the SUM and EXACT functions in an array formula.

Onion water makes invisible ink. The drawing becomes visible when it is heated. Use this as inspiration for one of your April Fools Day pranks!

Open up your mobile phone and solder on a light sensing resistor to make an alarm go off when the phone is in the light. Possible uses?

Watch Bill Myers show you an easy way to quickly hide sensitive screen capture text or images using Camtasia Studio.

Any electronic equipment is bound to accumulate dust, slight moisture, dirt or any combination of the above on its sensitive parts over time. The delicate nature of items also means further care is required.

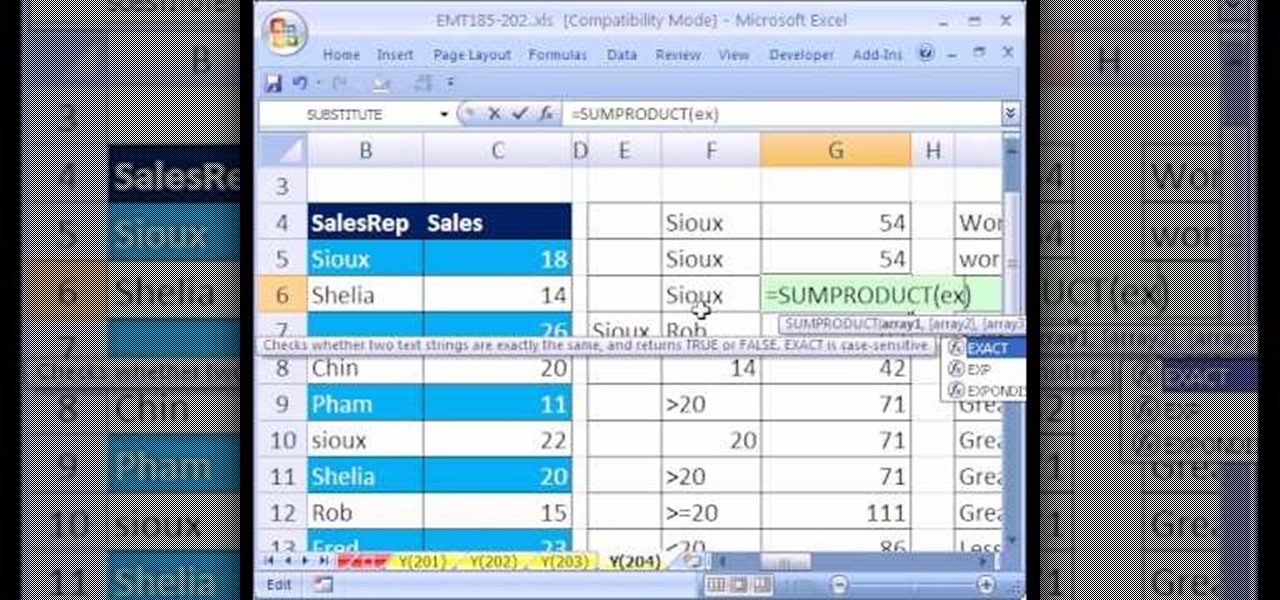
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 204th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the SUMPRODUCT and EXACT functions in an array formula to add the sales for a sales representative where lower and upper letters matter (i.e., are case sensitive) in the criteria (conditions).

This video shows how to use a special tool to redact or remove sensitive information from Adobe Acrobat 9. This includes hidden metadata, file attachments, comments, hidden text and layer elements within a PDF file. You can also set it up when you're emailing. The Examine Document function highlights information that you may want to remove. You can then select the different types of data and choose which things you want to remove.

Bathing a baby means not only keeping them clean, but also taking care of their skin. This video shows you how to keep your child's skin soft and well moisturized. Make sure your baby doesn't continually suffer from dry skin, and always moisturize after a bath.

If you’re one of the 100 million Americans with dry, itchy skin, find relief with these home remedies and lifestyle tips.

It sounds like Samsung is impressed enough with Apple's 3D Touch feature on the iPhone 6S models that the company is planning on implementing a similar feature on its upcoming Galaxy S7 handsets. A source told The Wall Street Journal that the latest iteration of Samsung's flagship will feature a similar design to this year's Galaxy S6, and will again feature both standard and curved AMOLED models. It's also rumored that the standard design will once again support microSD cards, which should p...

It may not seem like a big deal, but sometimes when your filenames are being saved in the incorrect case, it is. If you save a file with uppercase letters in the name, your computer may change them to all lowercase. This occurs when downloading files form a host server to a local hard drive. But what if you want them back how you had them? Well, there's a small Windows tweak you can use to stop it from happening. Learn how!

Playing golf could be a pain if you don't know all of the basic rules, tips and etiquette associated with the sport. You could find yourself off the fairway (and not on the green, if you know what I mean), or you could find yourself getting kicked out of the golf course for greens damages or unsafe practices and you could find yourself merely being the worst golfer with a club in his hand.

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Apple's iPhone is considered one of the best smartphones in the world. Many cell phone makers have tried to take down the juggernaut, with some Android-based devices coming close, but in order to become an actual iPhone killer, something revolutionary needs to happen in the mobile world. And Human Media Lab (HML) may be the ones to make it happen.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

If you had to answer the following statement, which answer would you choose? Water is:

Reading people's minds is something that most inquisitive and sensitive people have wished that they could do at some point. Well, what if you could? This video will show you a great multipurpose bar trick that will allow you to appear to read the mind or body of people in a variety of situations. It's really remarkable how easy this is and how well it works.

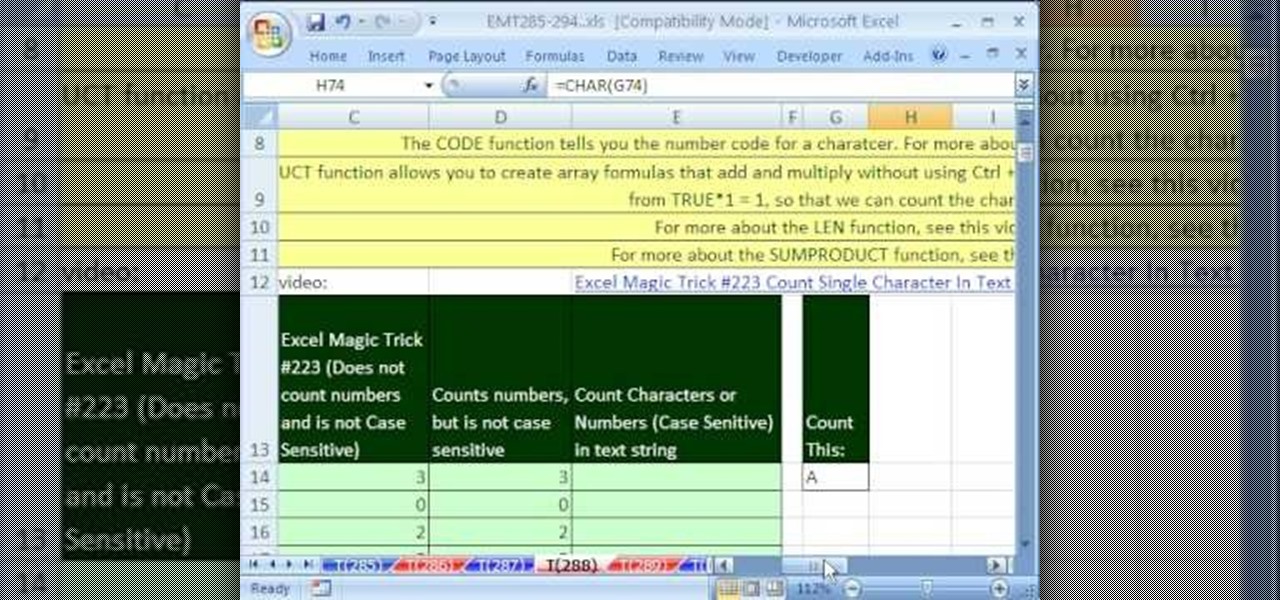
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 288th installment in their series of digital spreadsheet magic tricks, you'll learn how to count the number of characters or numbers in a text string with a formula that is case sensitive.

We all know the G-spot as that sensitive area that drives women crazy, but for auto enthusiasts, it has a whole new meaning. The G-Spot, designed by Daniel Davies, is a vehicle immobilizer, which keeps your vehicles safe from car thieves. And you don't need to pay a huge amount of money to get one, either! You can make on yourself, right at home, provided you have all the right materials.

When you need a website to showcase your product or service, it can be quite confusing. Follow these easy steps to gather everything you need to have a successful website. Start your search for a domain name in the domain name registrar. (Example: www.companyname.com) Rent space from a hosting company to hold the files for your website. Set up an email account for your company. Create the content for your website (example: products, prices, services, etc). Get internet security to protect sen...

This is a video guide for measuring your foot and calf size correctly. This is important in order to properly fit shoes. It's a video intended for athletes and individuals sensitive to their foot and leg health. This is brought to you by a retailer that fits wide or narrow feet with proper shoes. You'll need a wall and a measurement guide. Measure for both feet and sometimes you have two different sized feet.

If you're a God of Mount Olympis, you may want to leave town, because Kratos is still angry in God of War 3 for the PS3. Killing Gods and defiling women are just a couple of his his hobbies. The other is treasure hunting. And in this IGN Strategize video, you'll find the locations of all ten Godly Possessions in God of War III. The Godly Possessions are more than just conversation pieces. Each has a special power you'll be able to use after beating the game once. You'll also get a gold trophy...

Check out this six-part video lesson on shaving for men. This covers the most uncomfortable places to shave on the body. Body shaving can be sensitive, so do so with caution. Yes, you WILL learn how to shave your private parts with this video.

Data thieves don't have to be programming wizards to get their hands on your personal information. They often find hard drives that contain financial and other sensitive data at flea markets, charity shops, the city dump—even on eBay. In this video tutorial, PC World explains how to completely erase sensitive data from old drives before recycling or discarding them. Wipe your old hard drives with this how-to.