Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.
If you're having trouble staying connected to Battlefield 3 on LAN, or if you're experiencing time outs or disconnects, take a look at this fix. You will need to follow several steps, including accessing the "services.msc" file and stoping the UPnP Device Host.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

In order to connect two personal computers to each other, you will need a crossover cable. If you don't have one, that's not a problem. Take a look at this instructional video and learn how to make a crossover cable from and ordinary LAN cable with a small connector block, a knife, tape, and a lighter.
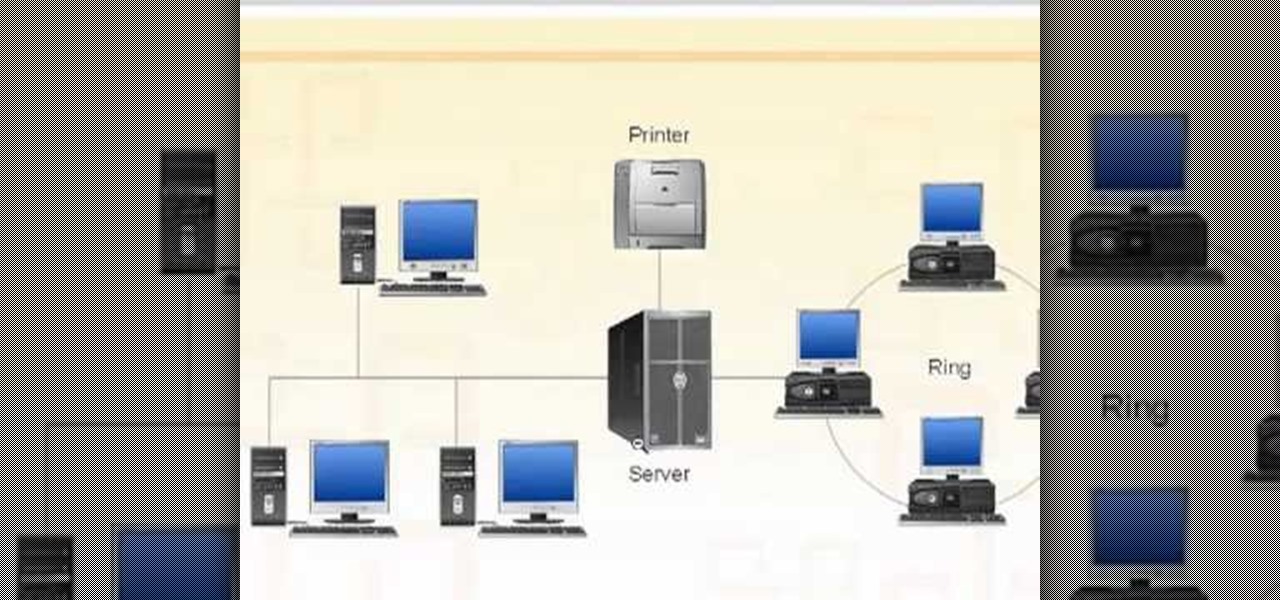
Need some help figuring out the ins and outs of LAN networks? They're easy enough to understand. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, and to learn more about LAN networks yourself, watch this helpful video guide.

In this how to video, you will learn how to play Borderlands LAN online using Tunngle. You will need Borderlands and Tunngle in order to do this. First, open Tunngle and then log in to Borderlands. Go to LAN game and select your character. From here, join a game. You are now ready to play. If your friend is not showing up, press E to refresh the list and make sure the port 11155 is being forwarded by the host. To get the in game mic to work, you must go to online game and make sure you log in...

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

Spina bifida is a birth defect involving the neural tube, resulting in an incomplete formation of the spine. Spina bifida is one of the most common birth defects, it occurs within the first few weeks of pregnancy often before a woman knows she's pregnant. Get expert tips and advice on treating and understanding spina bifida or split spine in this video.

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Need a hand figuring out how to set up a wired home LAN network? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

NFC, or near-field communications, is a hardware feature that has been built into most Android phones for the last four years. It's essentially a low-power data connection that can be used to initiate a quick command by bringing your device within range of a compatible receiver, be it tap-and-pay with Google Wallet, a file transfer via Android Beam, or a Tasker profile triggered by a specific NFC tag.

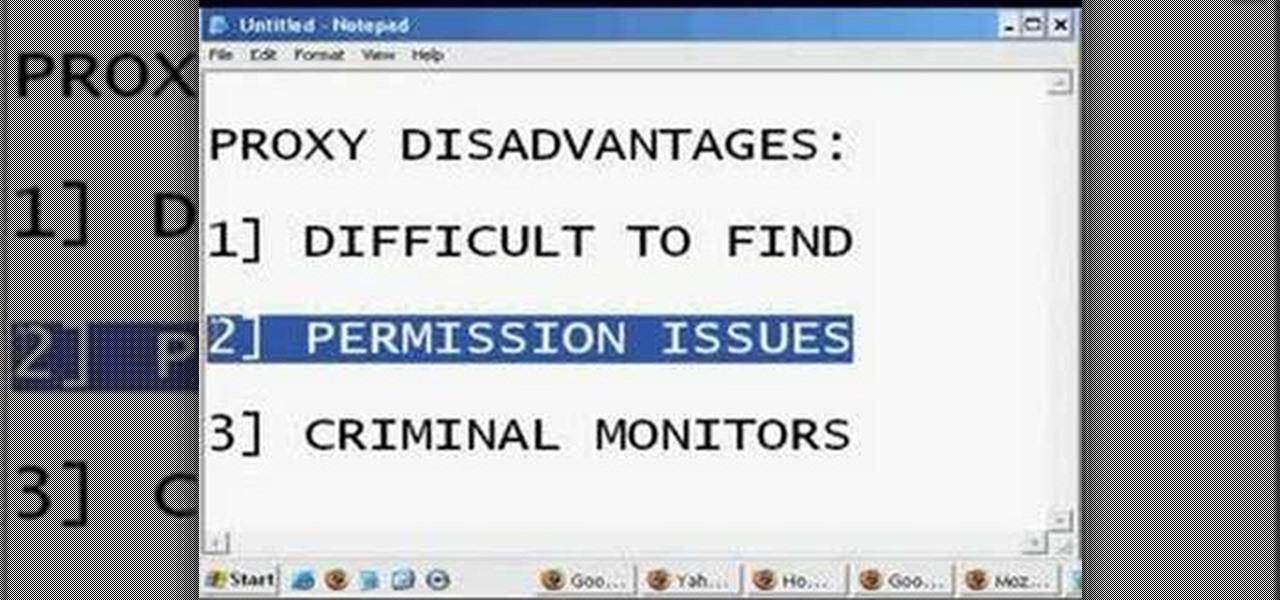
In this tutorial, we learn how to change your IP address in five different ways. First, go to your security settings and clear all cookies, then start to browse the internet with private browsing from your internet browser. You can change your IP address by going onto your internet browser and changing the LAN settings. Type in your address and port, then bypass the proxy server. Next, go to options and then advanced on your browser. Type in the proxy and port, then click where it says no pro...

In this video, we learn how to bypass WebSense at school using an http tunnel. First, open up Internet Explorer, then type in http tunnel and go to the website. Download the first link to your computer. Next, start the program and click on "free service". Now, open up the browser again and go to "internet options". Once you are on this, go to "connection", then "lan setting". Check to use a proxy server, then click "advanced", then enter in "http 127.0.01 port 1080". Click "ok", then exit out...

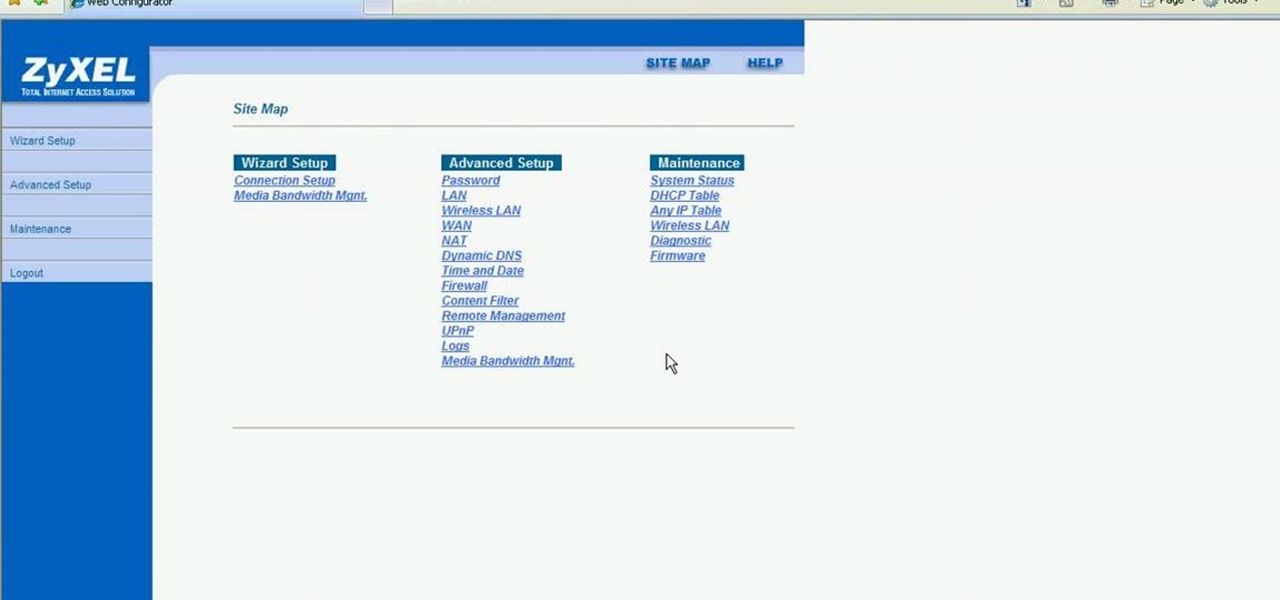
This video shows how to secure a wirelees internet connection on your Zyxel P-660hw-t1. For this, first click on Start button and open Internet Explorer(or any other browser). On the address bar of the browser, type in the IP address of your router. On the next page, enter your password and on the next page, either change the password or ignore. On the next webpage, under Advance setup, click on Wireless LAN. On the next page, click on 8021xWPA. Select authentication required and then click a...

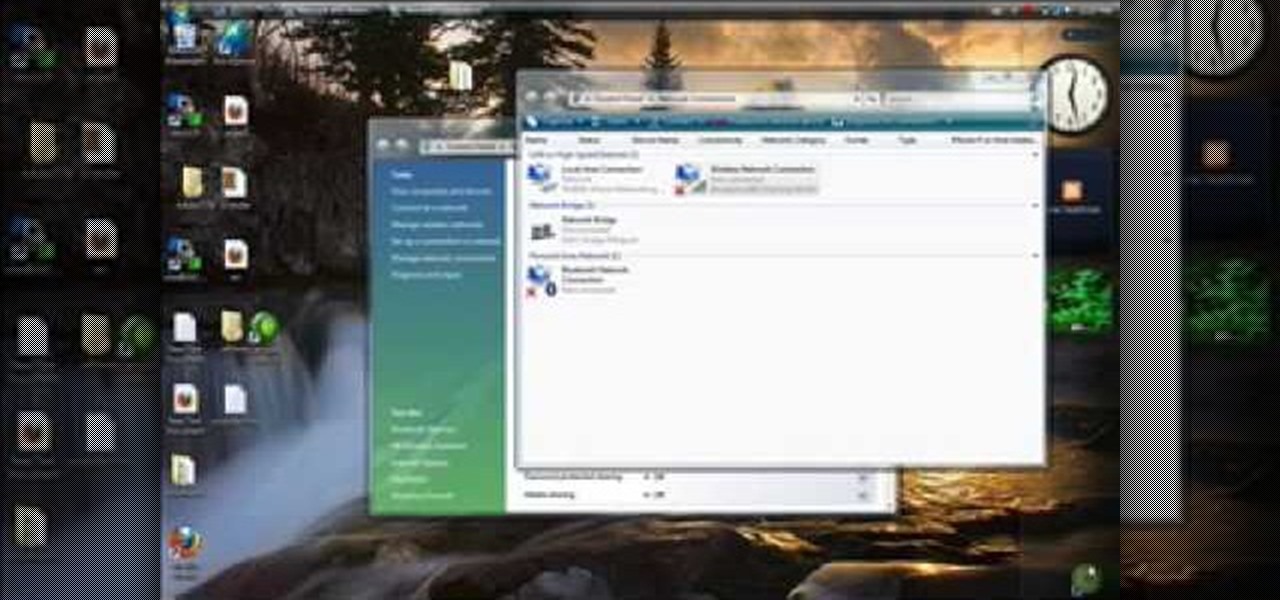
This video will show you how to connect to XBox Live through a laptop or PC’s Wi-Fi. Connect your XBox Ethernet cable and the other end of the cable you connect it to the Ethernet port of your laptop. On Vista and XP, open control panel and go to Network Connections. Right click on any one of the ‘LAN or High-Speed Internet’ icons and select ‘Bridge Connections’. After a little while bridge connection will be enabled. Close the window and go to your Xbox. Ensure all connections are in place, ...

This is a tutorial to get XBox live without paying $100 for the router. You need an Ethernet cable and a laptop or computer with a wireless internet connection. To begin, go to the start menu and click on control panel. Change the control panel view to classic view. Then click on network connections and go to your wireless connection under the heading 'LAN or High Speed Internet'. Right click on the wireless connection icon and select properties. In the properties window, go on to the advance...

AntiVirus Live is a fake antivirus software which comes onto your system and asks you to buy it. It doesn't provide any security to the computer. Here is the procedure to remove it: (1) disable the proxy server for your LAN in Internet Explorer. 2) download the process explorer from ms technet. 3) locate and kill the sysguard.exe. 4) finally remove AntiVirus Live. After following all these steps reboot the computer. Protection against future intrusion is mentioned. You should be aware of the ...

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install Frozen Bubble 2 on Ubuntu Linux.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn a Fon+ wireless router into a network tap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a web-enable remote controlled tank.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to set up SSH tunneling to securely transmit HTTP traffic.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to turn any Windows application into a service.

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

This tutorial gives a start to finish explanation of how to make an Internet Wi-Fi router with Windows Vista. With real time computer screen video and narrative, it is easy to follow along at home.

This video illustrates the method to Set up a Remote Desktop connection on a Windows PC. This process is composed of the following steps: Step 1Install "TeamViwer" software on the PC's which would be involved in this process.Step 2Create a connection between the computer you want to access remotely and the one which would be used to gain remote access. To create a connection , you need to connect them through Wi-Fi, LAN or through the internet.Step 3Open the TeamViewer software from the compu...

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Directions on creating a LAN cable with an RJ45 cable

This video tutorial will teach you how to use the Nintendo Wii Shop Channel to download and play your favorite console games on your Nintendo Wii. To follow along, you'll need either a WiFi Internet connection or Wii Lan adapter.

Watch this tutorial to learn how to draw any cartoon character: line drawing. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

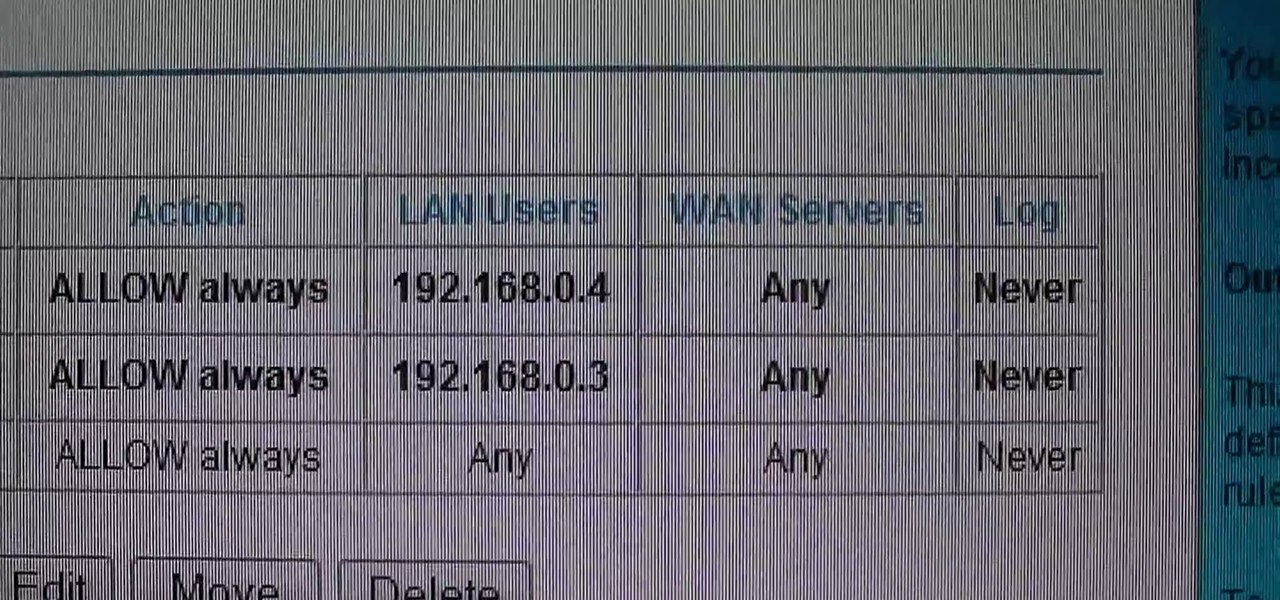
This video shows how to change the NAT type on a PS3. Go to connection settings>network settings>internet connection settings>OK>custom>wired connection>auto detect>manual. Choose an IP address that is different from your router, any other consoles, etc. Click right>automatic>do not use>enable. Press x to save settings, and test your connection. In this example, NAT type is 2. Now go to your PC and open IE. In the address bar, input router IP address, username and password. Go to Firewall Rul...

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

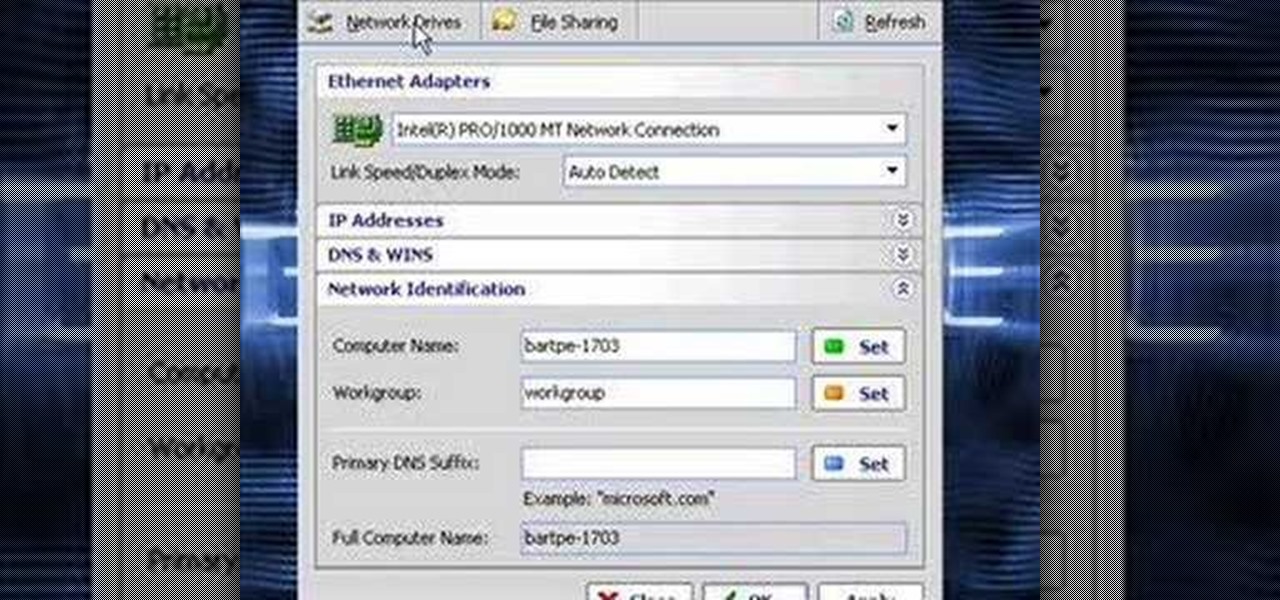
In this video the instructor shows how to clone computers across the Local Area Network using BartPE and Selfimage. To do this first we will have an original computer. Now create the image of the hard drive of the computer and share it on the network drive. Now, using that image from the shared folder you can start the clones of other computers by overriding their hard drive using this image of the main hard drive. Using this technique you can clone multiple computers which are the exact dupl...

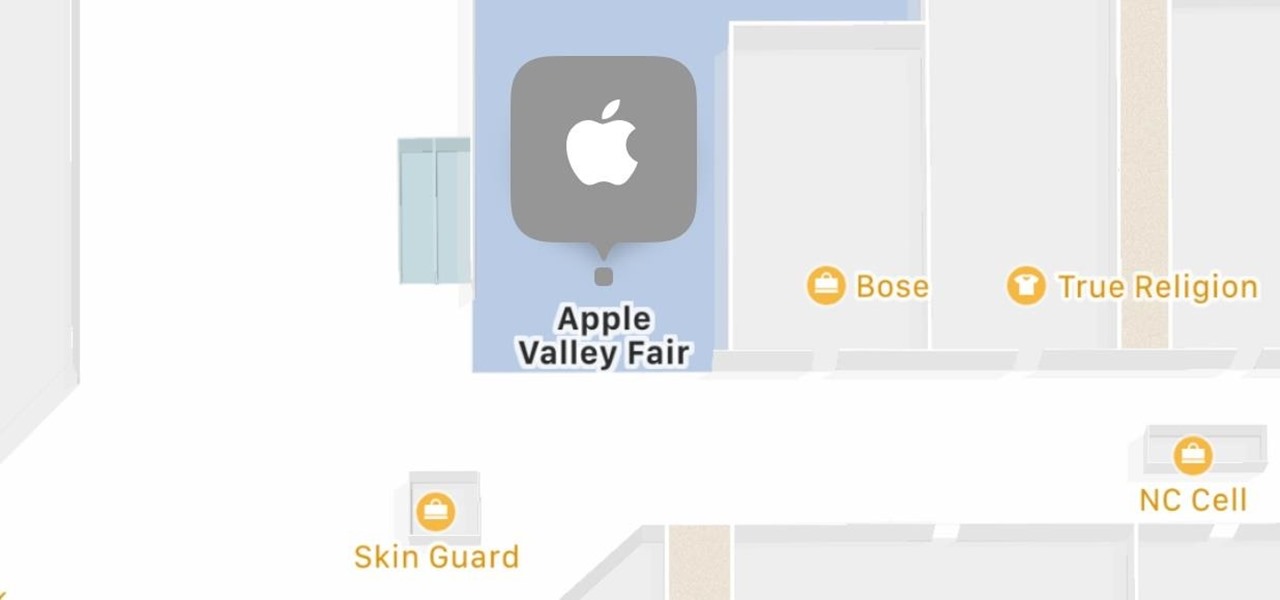
Apple has some great features aimed at making the lives of globetrotters and mall aficionados significantly easier, such as having detailed floor plans for airports and shopping centers in its native Maps app. With this feature available in Apple Maps, you no longer need to rely on publicly posted maps and directions that are often hard to understand.

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.