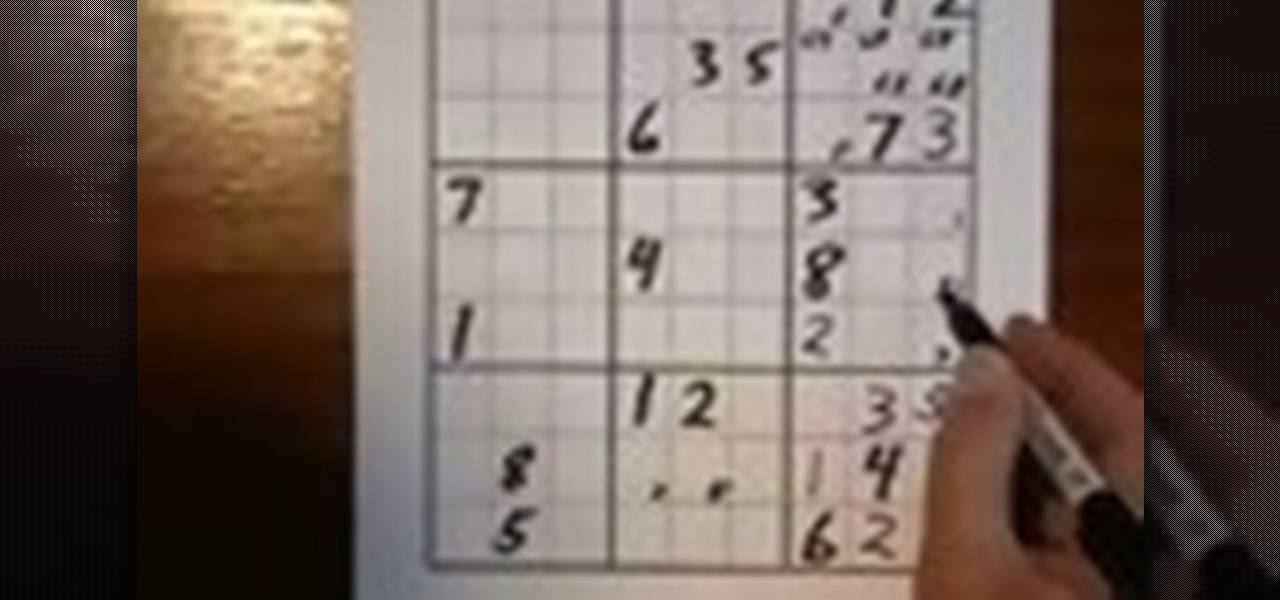
How To: Solve a sudoku puzzle with special techniques
Solve sudoku puzzle using the cross hatching, either/or, and pairs technique. If you can use a magic marker, and feel competent enough, then why not try it out?


Solve sudoku puzzle using the cross hatching, either/or, and pairs technique. If you can use a magic marker, and feel competent enough, then why not try it out?

Learn how to do the pigeon pose designed for strengthening and opening the back. You will learn Kapotasana, or pigeon pose,

Whether you're on a job interview or a first date, follow these simple steps to give the impression that you're quite intelligent – even if you're quite average.

Numerous studies have shown that people are over-confident in their own abilities. Most people, for example, think that they are better drivers than average.

HIV infections persist despite treatment that successfully decreases viral blood levels to the point where doctors can't detect the virus. But that doesn't mean the person is cured. The virus hides in the body, not replicating, just waiting for a chance to jump out of the shadows and reemerge.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.

If you really want to end your next big guitar solo with a bang, consider giving this shotgun guitar a try.

Over the past year, two trends have emerged among augmented reality development software: make it easier to create AR content, and give AR apps better environmental understanding with just a smartphone camera.

Last year, Motorola released their Moto G5 Plus, a fantastic mid-tier machine that earned praise from both reviewers and consumers. Starting at $229, it was well-built and inexpensive considering everything Motorola managed to jam into it. This year, Motorola is looking to replicate the success of their G series with the G6 Plus.

The art of persuasion is a very crucial characteristic that anyone can learn, and it has countless benefits. Whether it's at work, home, or in social situations, the ability to be veritably persuasive can have an unheralded impact on your daily life.

Apps went from a novelty to the main way we control the functionality of our phones and tablets in what felt like an instant. Apps are ubiquitous, and you can find one for virtually every need. However, what's right for someone else isn't always right for you, and what's right for you might be right for more people.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

When just floating peacefully in the water with their brood mates, the Culex mosquito larvae in the image above does not look very frightening. But in their adult form, they are the prime vector for spreading West Nile virus — a sometimes mild, sometimes fatal disease.
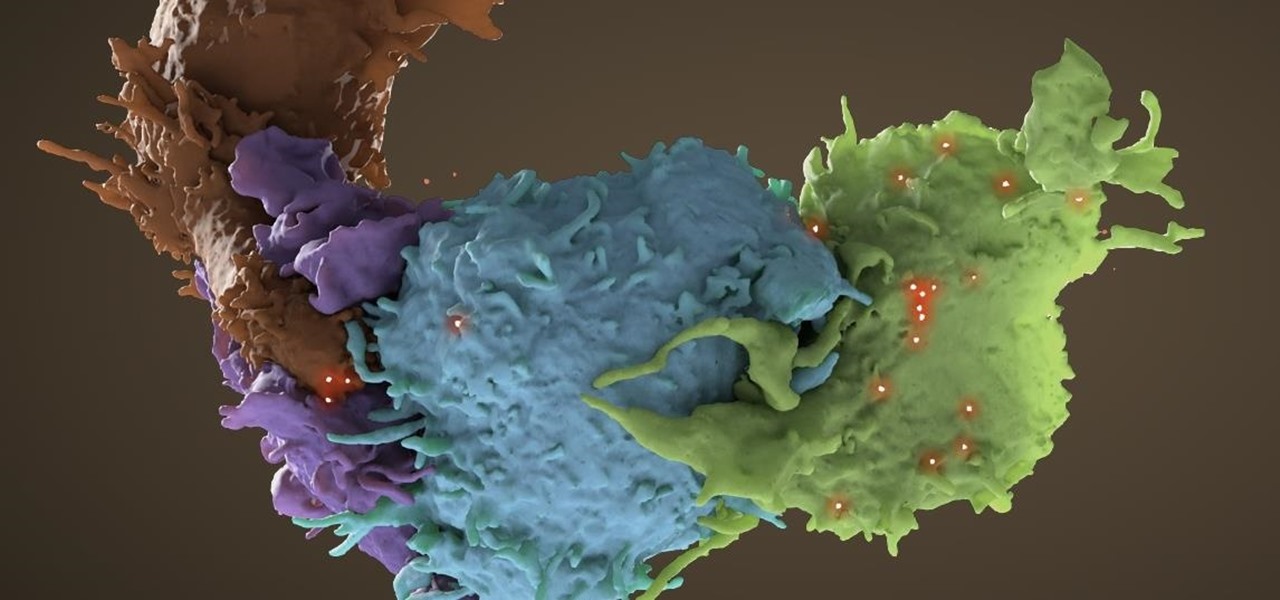
Tremendous strides have been made in the treatment and outlook for patients infected with HIV, the human immunodeficiency virus. Treatment with a combination of antiretroviral drugs can keep patients with HIV alive for decades, without symptoms of the infection. The trouble is, if HIV-infected people stop taking their medications, the virus takes over in full force again—because the virus hides out quietly in cells of the immune system, kept in check, but not killed by the treatment.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

If you use Goals in Google Calendar, you've probably already received the notification that Google, in typical executioner fashion, has marked the feature for death. As of November 2022, you can't create new goals, and your current goals won't repeat anymore. Google suggests switching to repeating events or tasks, but there's a better option to use on your Android and iOS device.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

To do this "curtsy lunge" exercise is a great for a leg workout. But you should first be completely competent with the lunge and split squat exercises first. This lunge exercises is brought to you by Men's Health.

Looking to be the world's best violinist or fastest banjo player? If you didn't start practicing when you were a kid, learning a new stringed instrument is extremely challenging. But an upcoming device may change all of that, if you don't mind being shocked by 28 different electrodes.

Two weeks ago I reviewed browser-based video editor WeVideo and was amazed. Amazed not because WeVideo is a competent iMovie replacement for the casual editor (which it is), but amazed that a browser-based editor can work at all.

Carol Platt was caught in the middle of the economic downturn with no backup plan. Searching for a stable job in an unstable economy proved to be difficult without a college degree. Her work history and past successes were overlooked. It had always been a dream of hers to complete her degree; after a failed first attempt, she was unsure of her ability to follow through. She began researching online education options and felt that Kaplan University stood out; she decided to complete her colleg...

Deep in their heart of hearts, most Americans dream of having their car festooned with missile launchers and machine guns. Anyone who cuts them off or looks at them funny in traffic could be dispensed with quick and extreme justice, leaving a real-life James Bond and his passengers free to pursue their American dreams faster than everyone else. Racing games and shooting games are among the two most popular types of video games. So why aren't there more games where one can race cars and shoot ...