Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.
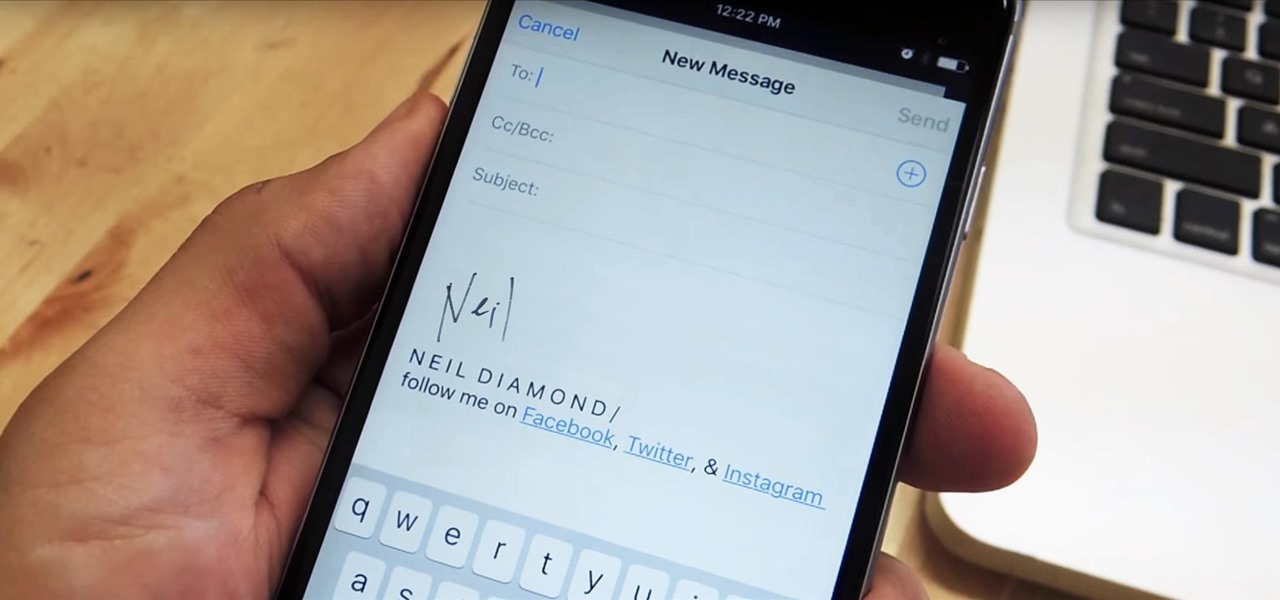
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Who needs a pen when you've got an iPhone? If you have a form, agreement, or contract that you need to quickly sign, you do it directly from iOS without the use of a third-party app. Using Markup, which is available in several native Apple apps, you can sign and send important documents in just a few seconds.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...
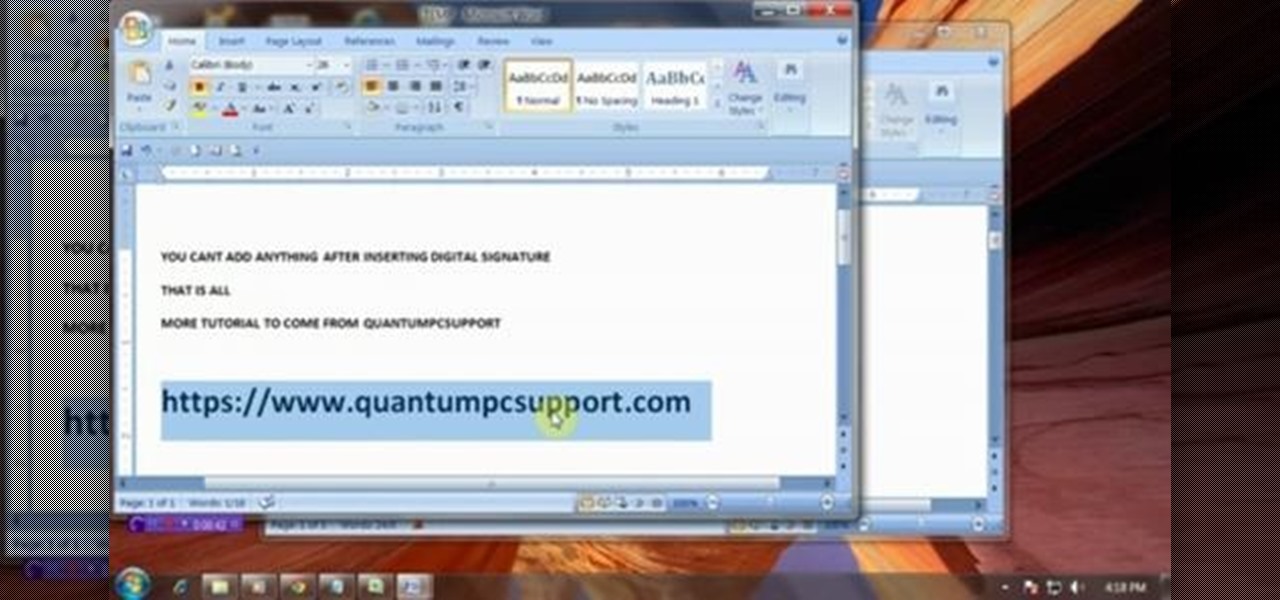
This video will guide you how to make digital signature in MS Word. The digital signature will allow to secure your document from tampering. When you set digital signature in your word text then you can't insert anything in the document anymore. You could add your image of signature with text.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

If you've ever received an email only to focus on the sender's signature — the hi-res image, the sharp design, the vibrant colors — you're not alone. Humans are visual creatures, and with something as ubiquitous as emails, it helps to stand out.

This video demonstrates the steps to take using Chip Foose's signature bronze base coat. Once the base coat is sprayed, we'll spray clearcoat.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Jem and the Holograms was one of the hottest cartoon series on TV back in the mid-'80s (though only for a brief time), and was recently given the big screen treatment with the feature film of the same name. While the film bombed at the box office (with good reason), your Halloween costume doesn't have to.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

Lindyhopper49, a huge fan of the "King of Pop", will teach you how to dance like Michael Jackson. He's not a professional dancer, but he does have some great advice and information on how to to Jackson's most famous moves.

Pop sensation Katy Perry has a wonderfully unique sense of style and fashion, from her clothes to her makeup to her hairstyles. And this video will show you one of the latter or the three— a great signature curls hairstyle.

Kim Kardashian is one celebrity who knows how to work what she's got (and it doesn't hurt that she's utterly gorgeous, either). With darker, bronzy skin, perfect, sharp cheekbones, and gorgeous, huge eyes, she always chooses to highlight these features when she's on the red carpet.

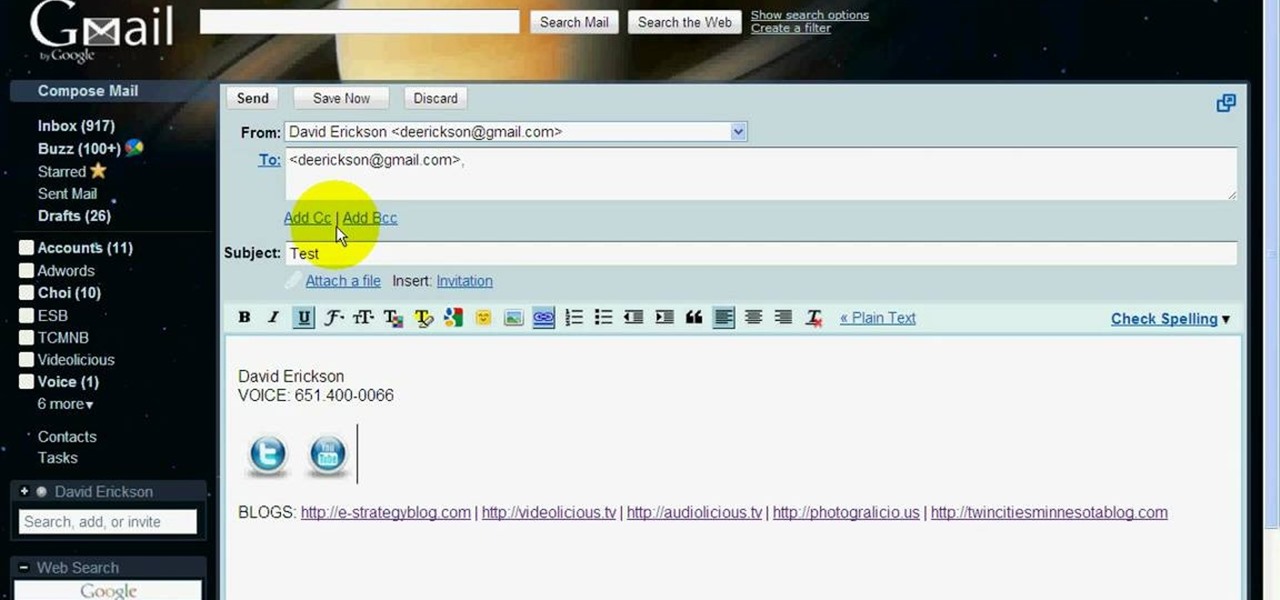
If you're getting bored of the same old same old in your e-mail messages, or if you're looking for an easier way to show off each of your social networking, as well as personal websites, then you will be happy to hear that Gmail has finally introduced rich text signature lines that'll allow you to hyper-link your images in your signature via HTML. All this can be found in the Labs section of your settings in Gmail. In this video you will learn how to set up the signature with the images and h...

This video is demonstrated completely through visual movement and accompanied with a brief written description. A young man speeds down the soccer field with a ball and scores a goal. His signature move leading up to the goal is broken down into very specific methods of movement, the first of which is a high speed attack as he races down the field. The next method to this signature move is the weight shift, in which the goal scorer shifts his weight, along with the ball, from foot to foot to ...

In this video, we learn how to do Andres Iniesta's signature soccer move La Croqueta. First, while you are on the field and have the ball, you need to turn and control it. Pay attention to those around you and move around them. Move the ball from left to right around the people coming towards you. Attack the open space to free yourself up and get away from crowds of the opponents. Once you do this, you will be close to the goal. Finish off the shot by kicking the ball into the goal. From here...

In our opinion, the best kind of curly hair is the kind that looks the most natural. So rather than tight ringlets that look like they've obviously been twirled around a curling iron, we're talking about loose, carefree waves that are slightly undone.

Sure, you can play minor pentatonic over the Blues all day and probably almost get away with it in a live setting. But if you want to play like the greats, you've gotta learn their licks! In this video you will learn two signature Blues licks that almost every player knows, that you can play over any sort of dominant or major slow blues progression.

Interested in fancifying your Google Gmail signature by including custom fonts and images? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over a minute and a half. For more information, including complete, step-by-step instructions, take a look.

Want to learn a sexy dance move that'll impress at the club but is also super easy to learn? Then check out this dance tutorial to learn how to do the booty shake, AKA Beyonce's signature/go-to dance move that involves popping your booty in and out while holding your arms bent at the elbows and pumping.

The card trick in this tutorial is great for beginners and seasoned magicians alike. In the video you will learn how to present a deck of cards to two spectators and amaze them with slight of hand.

Lindyhopper49, a huge fan of the "King of Pop", will teach you how to dance like Michael Jackson. He's not a professional dancer, but he does have some great advice and information on how to to Jackson's most famous moves.

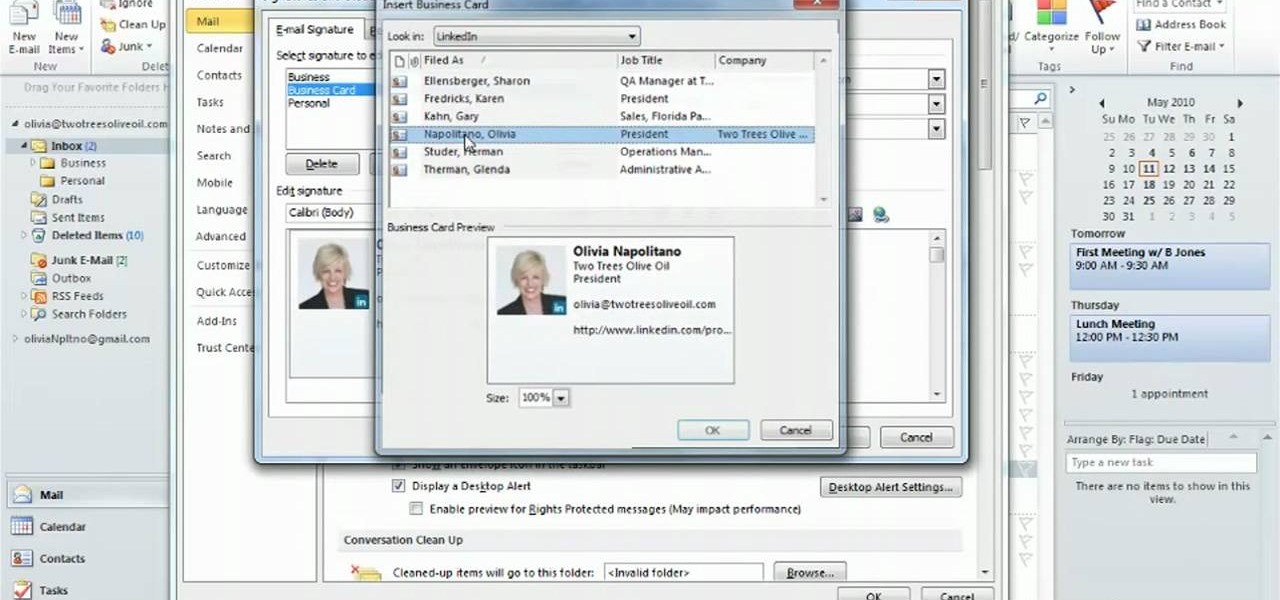
Learn how to create and apply custom email signatures to emails composed in Microsoft Outlook 2010. Whether you're new to Microsoft's popular email and scheduling application or a seasoned MS Office professional just looking to better acquaint yourself with the Outlook 2007 workflow, you're sure to be well served by this video tutorial. For more information, and to get started appending a standard signature to your own emails, watch this free video guide.

If you think about it, beauty of all beauties Angelina Jolie doesn't actually wear that many beauty products. Even when she's rubbing elbows with George Clooney at the Cannes Film Festival she's usually going with nothing more than clean, flawless skin, cat eyeliner, and pale lips.

Tattoo lady and reality TV star Kat Von D is obviously extremely talented with the tattoo needle. Creating interesting designs for clients that include celebrities, Kat Von D exudes a distinctive style that includes looking like a tougher version of a classic pin up.

Khloe Kardashian, sister of Kim Kardashian, has said that Kim has a tendency to go from man to man. And no wonder. With her smoldering, bronzed eyes and pouty lips always highlighted by a touch of petal pink gloss, Kim is one of the sexiest and most beautiful celebrities in Hollywood.

Lindyhopper49, a huge fan of the "King of Pop", will teach you how to dance like Michael Jackson. He's not a professional dancer, but he does have some great advice and information on how to to Jackson's most famous moves.

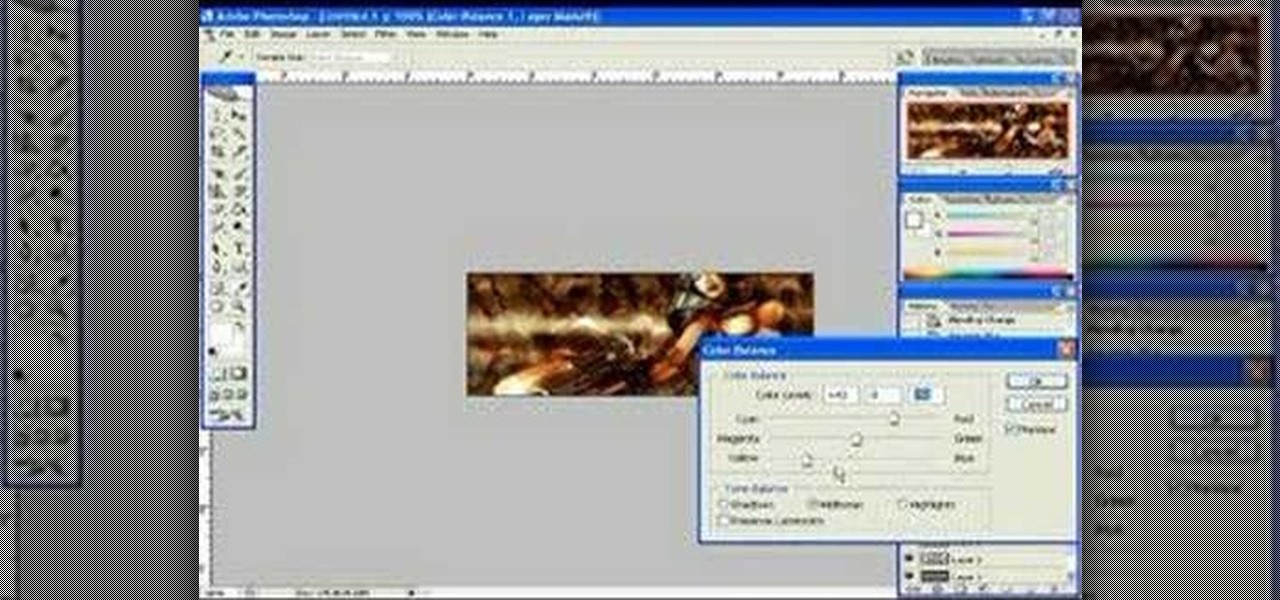
This simple Adobe Photoshop video based signature tutorial, teaches you how to create a simple effects in a forum signature.

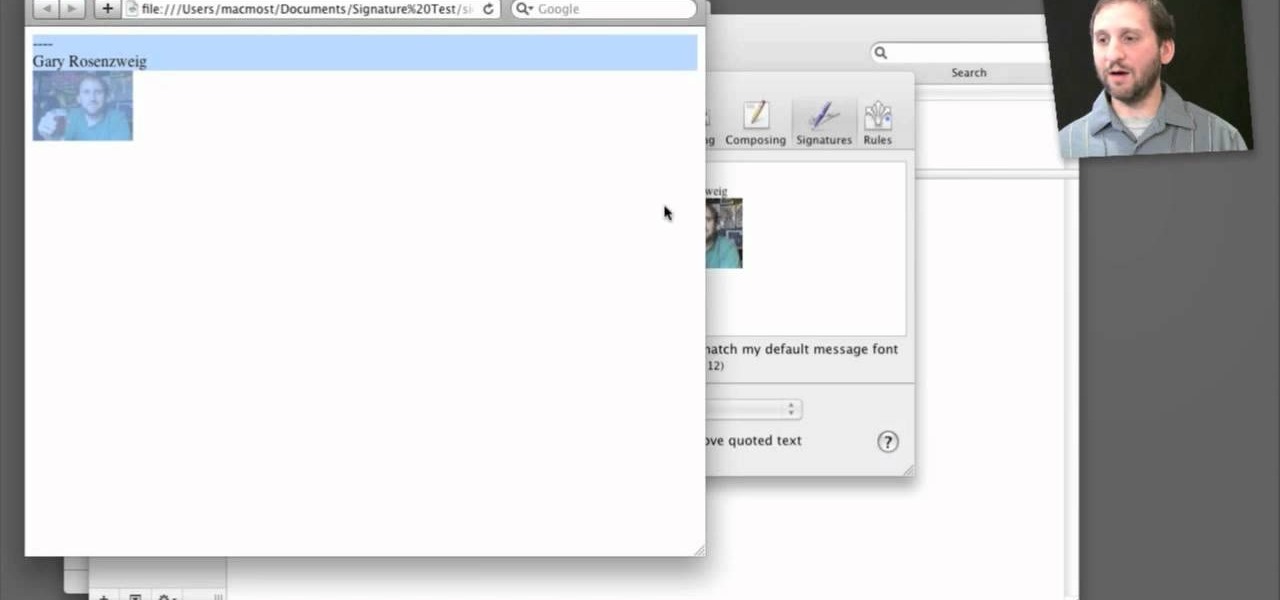
Looking to spice up your email signature a bit? Why not add an image? This simple how-to shows you an easy way to take advantage of some simple HTML embedding so you can add an image to your Apple mail signature.

In this clip, learn how to perform Michael Jackson's signature heel pivot or rotating slide to add to your dance routines. This is the famous way Michael turned around when he was moonwalking. Check it out and make your dances more fluid.

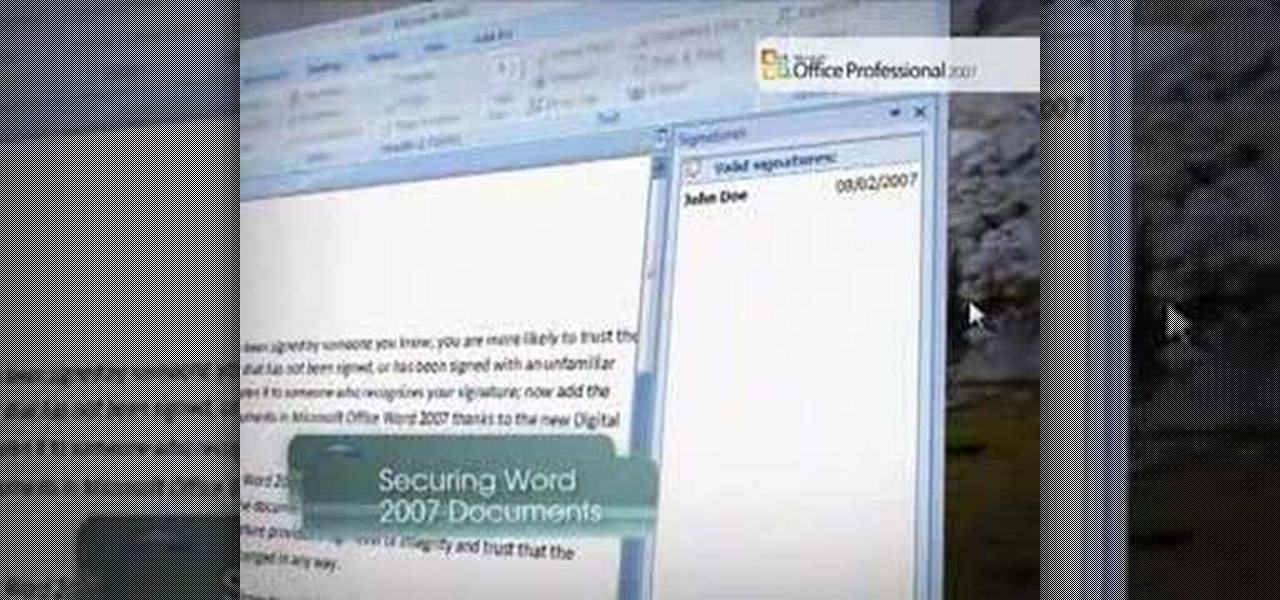
Securing Microsoft Office Word 2007 documents with Digital Signatures - When you receive a document that has been signed by someone you know, you are more likely to trust the contents than those of a document that has not been signed, or has been signed with an unfamiliar signature. Signing a document validates it to someone who recognizes your signature, now add the same degree of integrity to your documents in Microsoft Office Word 2007 thanks to the new Digital Signatures feature. For more...

Knowing music theory never hurt anyone—not Bach, not Chopin, not Schoenberg. Even if you fancy yourself a musical iconoclast, the better you know the rules of music, the better equipped you'll be to break them down the line. In this free video music theory lesson, you'll learn how to determine the root or "home" key of a song. For more information, including a very thorough overview, watch this helpful musician's guide.

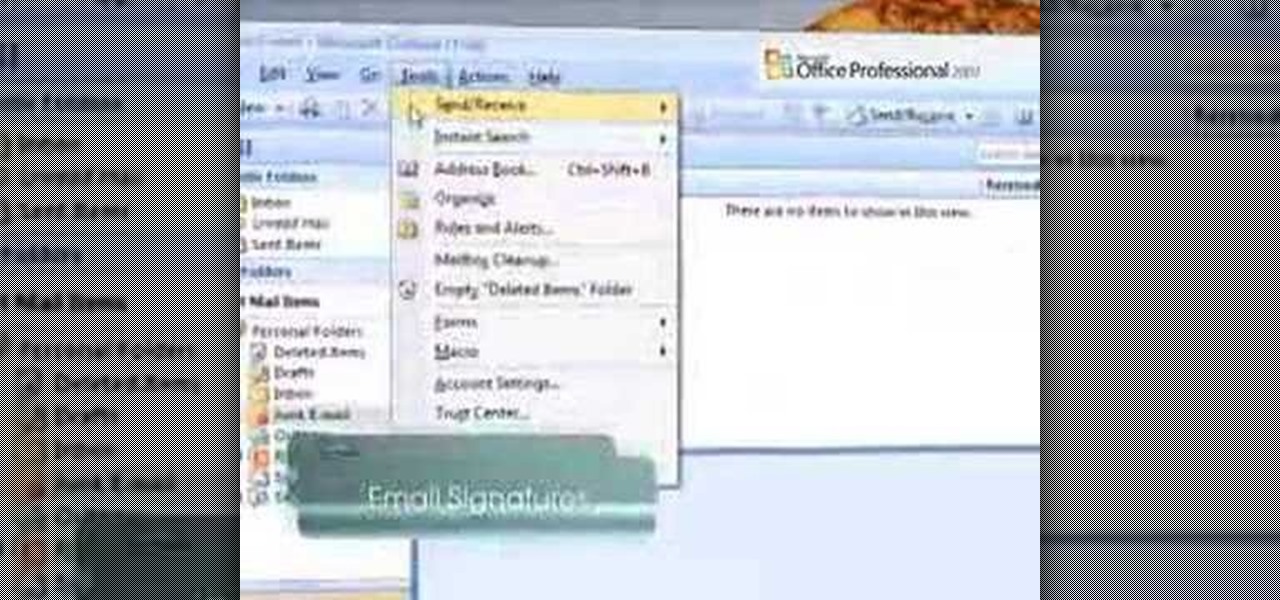
Microsoft Outlook 2007 Tip - Setup Signatures for Multiple Email Accounts - One of the difficulties with using multiple mail accounts is making sure your messages have the correct signature, or sig, attached to them. The new Signatures feature in Microsoft® Office Outlook® 2007 takes the hassle out of creating and applying signatures to your email.

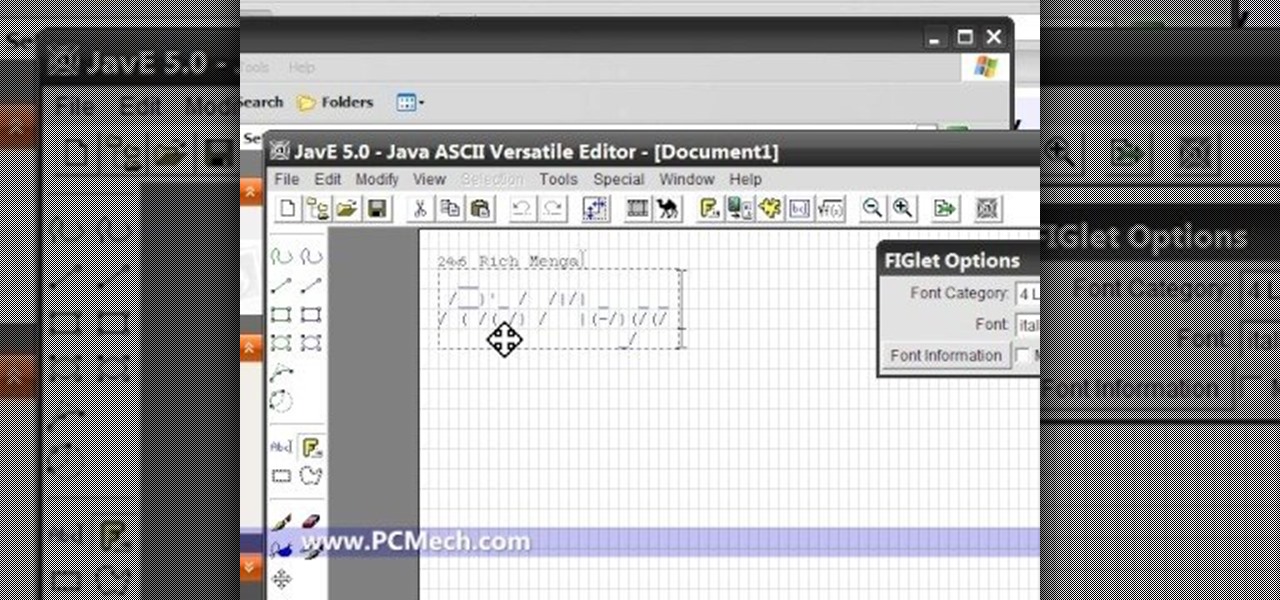
In this tutorial the author shows how to make a cool ASCII E-mail signature. He uses Hotmail as an example. He directs how to find the options in the Hotmail email and points us to the location where we can make a Personal e-mail signature. Now he demonstrates how to make sample ASCII signature. As the signature allows only text the author advices to user a tool called JavE to make a good signature. He now shows how to download that software for free and how to use it. Now using this tool he ...

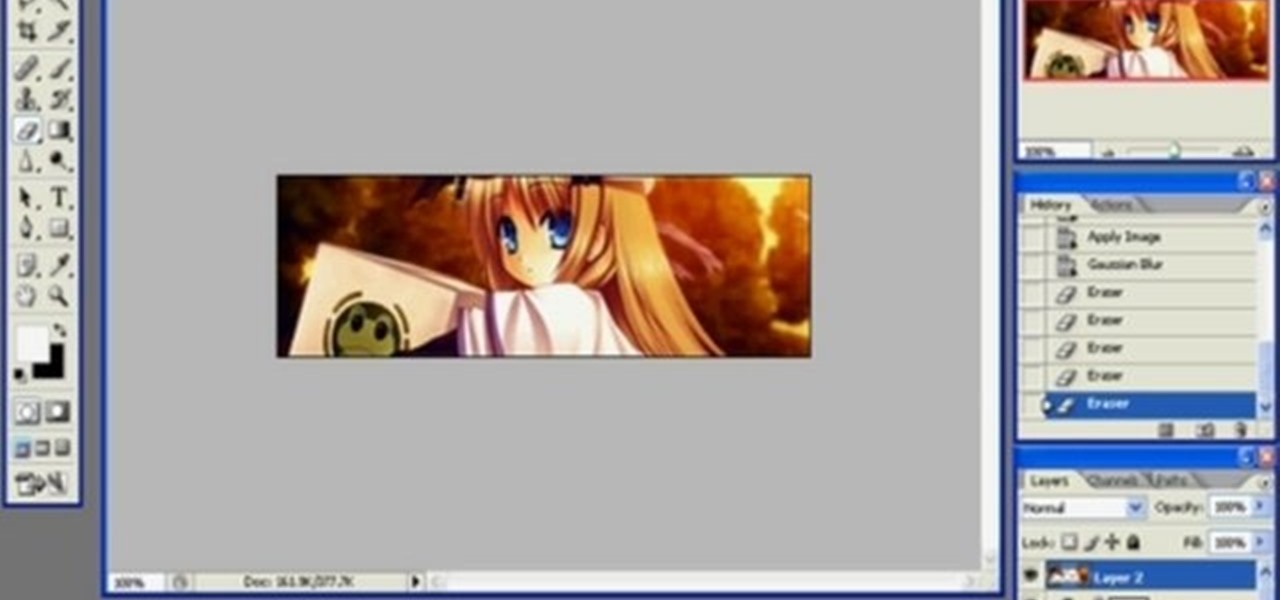
If you like participating in online forums, you might want to have your very own signature graphic. In this video tutorial you will learn how to create one using Photoshop. If you want to promote a blog, using a signature graphic might be a good idea.

Create a custom brush which you can use to stamp your own signature onto projects you've worked with in Adobe Photoshop. You'll be able to change the size or color of your signature, and put it anywhere on the image you want.