When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

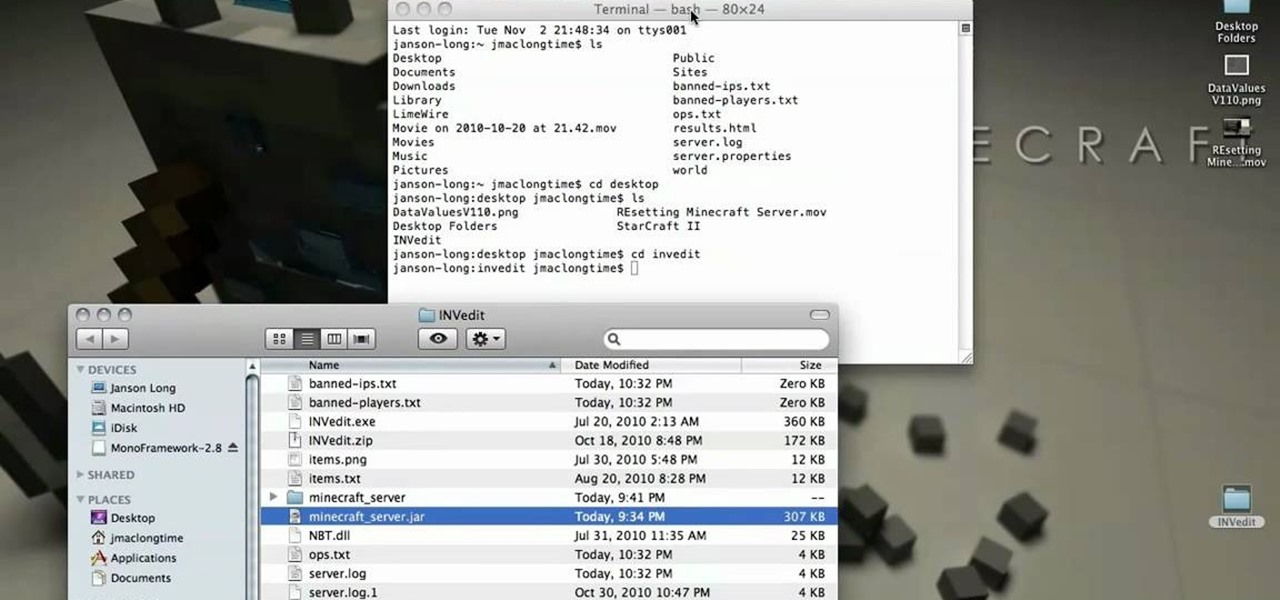
In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

Are you using the Internet at a school, library, or some other place that blocks or restricts web access? Mom and dad still trying to protect you from online predators, even though you're more than old enough to be one yourself? Learn how to bypass proxy servers that block access to certain websites by watching this how-to video. In this case it's done to access Myspace but this method can be used with any blocked website. Follow along with this video tutorial and never get hindered by restri...

How to Use COD4 Cracked Servers.

In this video, we learn how to change name servers in GoDaddy. First, go to GoDaddy and sign in with your username and password. After this, go to the side bar and click on the main manager option. Now, you will be able to see your domains. Click on the domain that you wan to change the name of, then click on "name servers". Now, click that you host your domains with another provider, and change the name server one and two. Once finished, click "ok", then your changes will be submitted. Withi...

This video shows the method of getting past blocked sites and opening them using proxy servers. The method shown is useful when the sites are blocked using another site. In this case it is 'www.lightspeedsystems.com'. It can be done using proxy servers. In the case shown it is 'treesniff.com'. The URL is typed and we choose the option of 'Continue to this website'. Press 'No' for the security information. After this the page of the proxy server is displayed. Type the name of the website you w...

Edit name servers in the domain management area. If you're buying domain and web hosting from a single provider, like Hostgator, then the domain name automatically has a corresponding host.

In this clip, you'll learn how to get started using Symantec Backup Exec to protect SharePoint & Exchange servers. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just under five minutes. For more information, including detailed, step-by-step instructions, take a look.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

This series of ping pong / table tennis videos demonstrate how to master the table tennis serve. Jim Clegg, a Level 4 Coach with the English Table Tennis Association and Head Coach of the Preston Table Tennis Association, explains and demonstrates how to do a table tennis serve correctly. Serving today is an extremely complicated topic. These are 9 in depth thought processes for a table tennis serve.

A custom application directory partition is a method of dividing your DNS servers for replication, and allows replication to occur between domain controllers. This video shows you the process of setting up your own using Windows Server 2008, though it will also work for the 2003 version as well.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

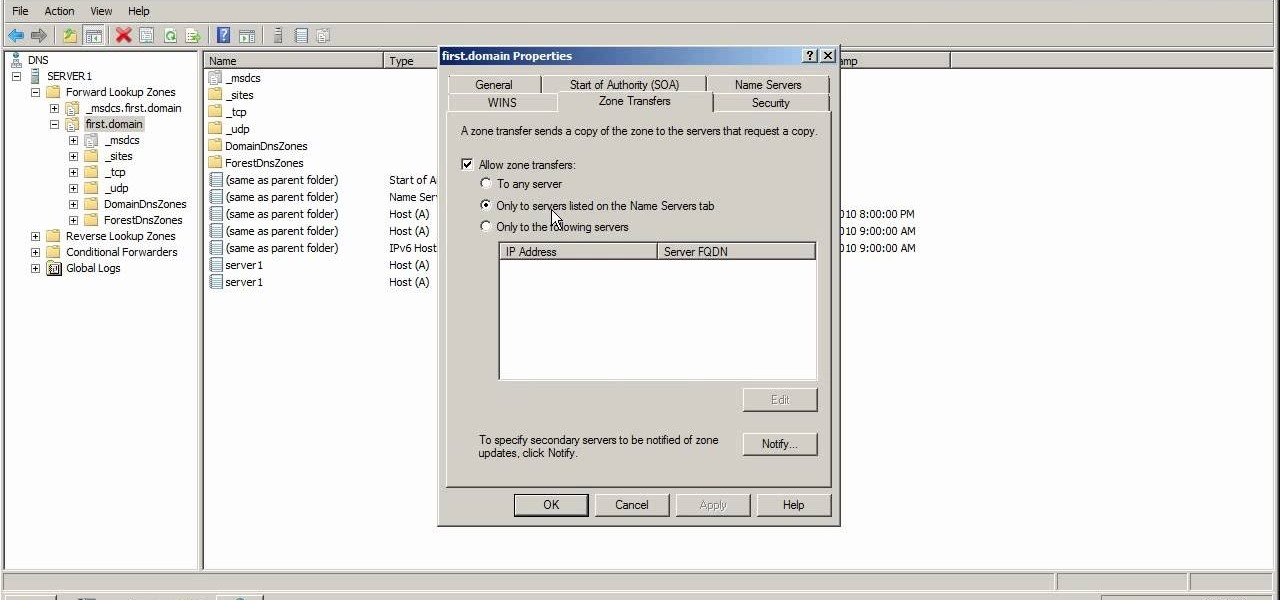
If you ever use NS lookup in Microsoft Windows Server 2008, you have to permit the machine running it to accept zone transfers. To do so, follow the instructions in this video. This video will show you how to use the name servers tab in DNS to allow machines to receive DNS lookups.

If you've already created your own Minecraft server, you can also set it up to launch with more RAM, making the game faster with more resources. This tutorial shows you how you can increase the amount of accessible RAM on your servers.

This video will show you how to set up a Garry's Mod server and allow others to access it. In order to get your Garry's Mod server public, you need to ensure that your router is properly configured to allow Garry's Mod ports.

Spotlight Server is the fastest way to search and find content on servers in Mac OS X. It's designed for work groups with shared documents, projects and file archives. To see how Spotlight works, as well as how to use it, watch this video tutorial.

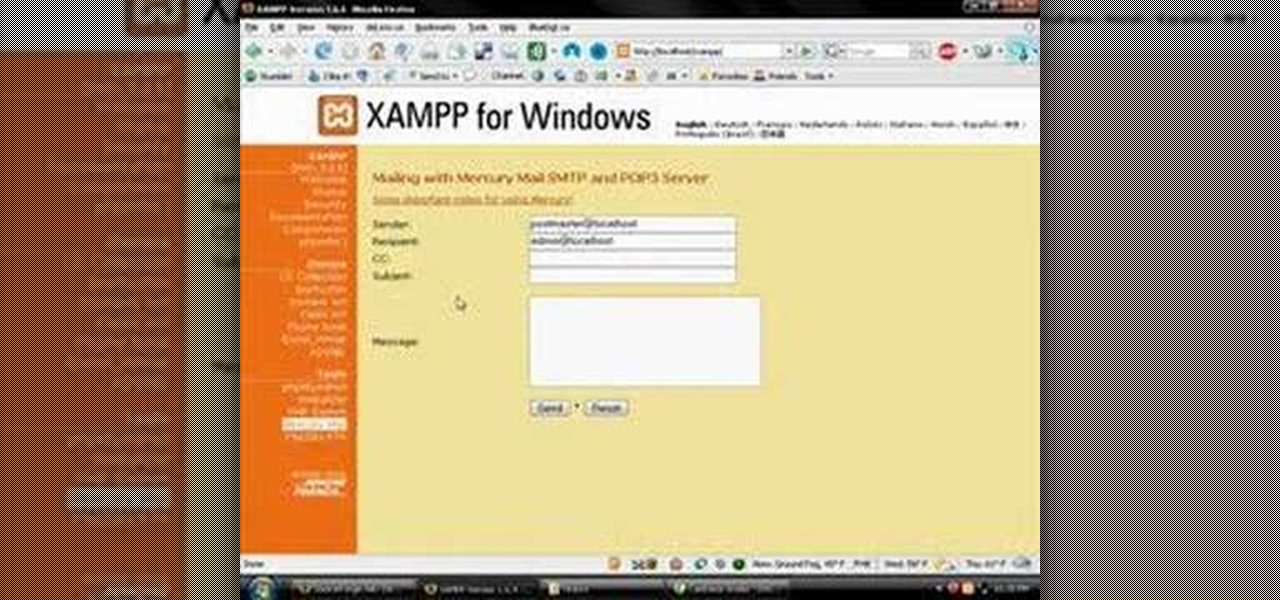
XAMPP servers are a free open source server that makes it cheap and easy for you to test and review your website building as you go. This tutorial covers how to configure your XAMPP server for windows.

This software tutorial shows you how to set up your FTP server using Dreamweaver. FTP servers are a great way to share and transfer data, especially when it is too large for email. So if you have a website, make it easy on yourself and set up an FTP server with Dreamweaver and this tutorial.

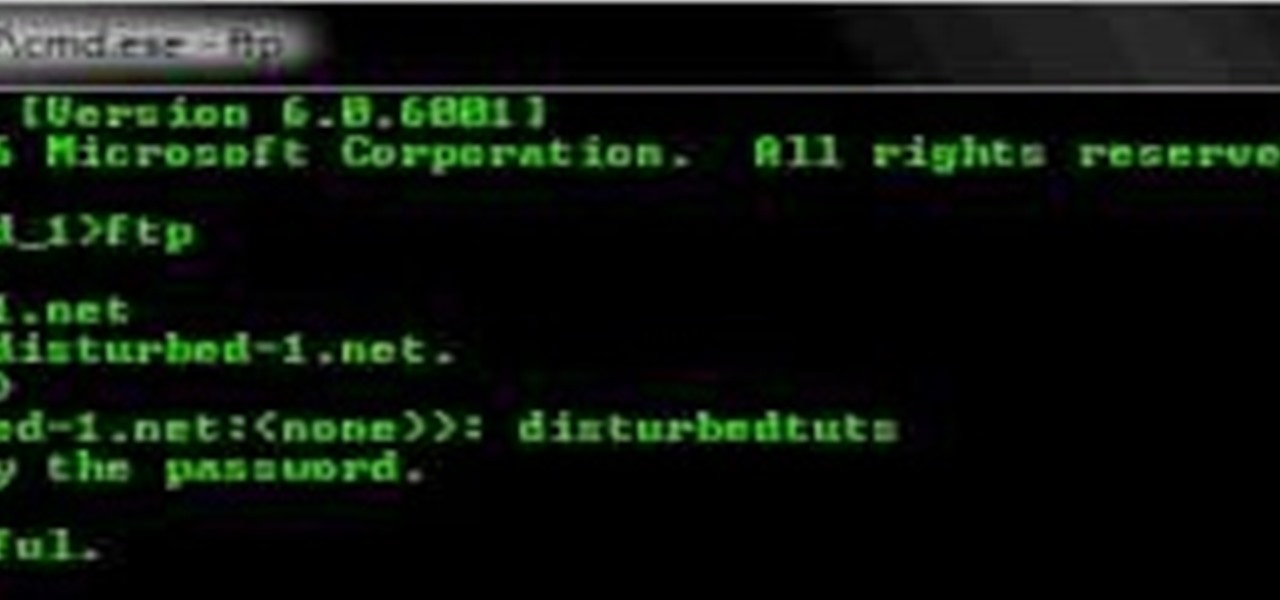
You can connect to an SSH server or connect to an FTP server from you windows computer. Open the run dialogue in your windows and type in cmd. Press OK to open the command prompt. Type in ftp command and press enter. This brings up the ftp prompt. Type o to connect to a server. Next type in the server name you want to connect to. Now you will need the authentication credentials to connect to the server. First enter the user name and then the password. Up on successful log in it shows the same...

You may need to perform routine maintenance on your DNS server from time to time by clearing the cache. Servers keep records of the lookups they have performed, and when they become resolved records they can be cleared. Follow the instructions of this how to video to clear the DNS cache in Microsoft Windows Server 2008.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Hello again, ***UPDATE: Adding links to the other Two articles****

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.