Getting your dream job is reliant on impressing the hiring manager with a resume and cover letter. Make sure you tailor your resume for the specific job you're looking for, and format for maximum presentability. From title to reference, this video will help you get the job you've always wanted.

The fatal crash of Air France Flight 447 is one of the most tragic accidents in avionic history — while it also serves as a stark reminder of what can go wrong when humans rely too much on driverless vehicles.

One of the most prestigious annual events for the advertising industry, the Cannes Lions is the ideal backdrop for Snapchat to show the brands and agencies in attendance what it's got.
Rumor has it that Google Assistant will be coming to an iPhone near you. A "trusted source" broke the news of GA's arrival on iOS to Android Police ahead of Google's I/O conference this week.

Ever since Skynet took over the world in the Terminator film franchise, a large segment of the world's population has feared artificial intelligence.

The race is on to break Samsung's near-OLED Monopoly. Google joined the race back in April, reducing their reliance on Samsung's OLED's by supposedly investing about $880 million into using LG's OLED's for their Pixel phone screens. Now, Apple's stepping up with a rumored $2.5 billion investment into LG's OLED Display initiative for their phones too.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

If you've ever missed an important phone call because you're hands were too dirty to touch the screen, you won't have to worry much longer about it happening again. Apple is remedying this age-old problem on the iPhone with a hidden feature in iOS 11 that ensures you'll never miss another call again.

If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.

It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

If the interconnected worlds of blockchain, Bitcoin, and cryptocurrencies scare you a bit, you're not alone. Thanks in part to the extreme and seemingly random fluctuations in the value of Bitcoin over the past three years, more than a few developers and investors are wary of the cryptocurrency revolution and its ties to blockchain development.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Alongside the launch of Android 11, Google added a new feature to Live View, the augmented reality mode for walking navigation in Google Maps, that helps you find friends in AR. But even if you're not trying to meet up with somebody, you can easily access the AR mode and orient yourself to any location.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

I was in college, and my 15-inch Sony Vaio laptop was my prized possession. It was my first PC and probably the most important thing I brought with me to my dorm — it was both how I completed my assignments and my primary source of entertainment. How could it turn its back on me in my time of need?

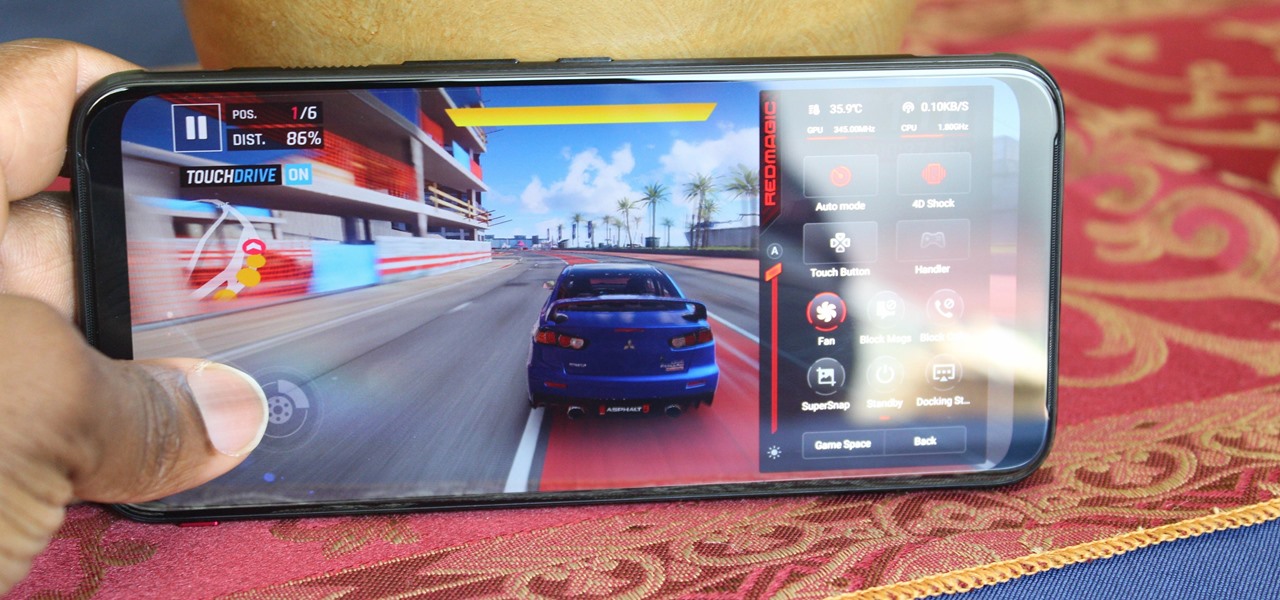
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

Amy Kline shows us in this arts and crafts series, how to make a hemp beaded necklace. Yes, you’ve seen them around the necks of all of the coolest people in town. Now learn how to make your own with relatively little training or financial outlay. Our expert will show you how to measure the length of your necklace to match your body size, how to anchor the necklace as you’re making it, and two different knotting techniques to create two different designs for your necklace. So the next time yo...

Body fat is important to understand when you are dieting. It is good to track your body fat, so that you are not as reliant on the scale. The numbers on your scale are not always accurate. Muscle weighs more than fat and if you are exercising more than usual your physique will get better but your weight may rise. Knowing the difference between fat and muscle will keep you from getting discouraged and hindering your workout. This tutorial will show you how to measure fat for success. Measure a...