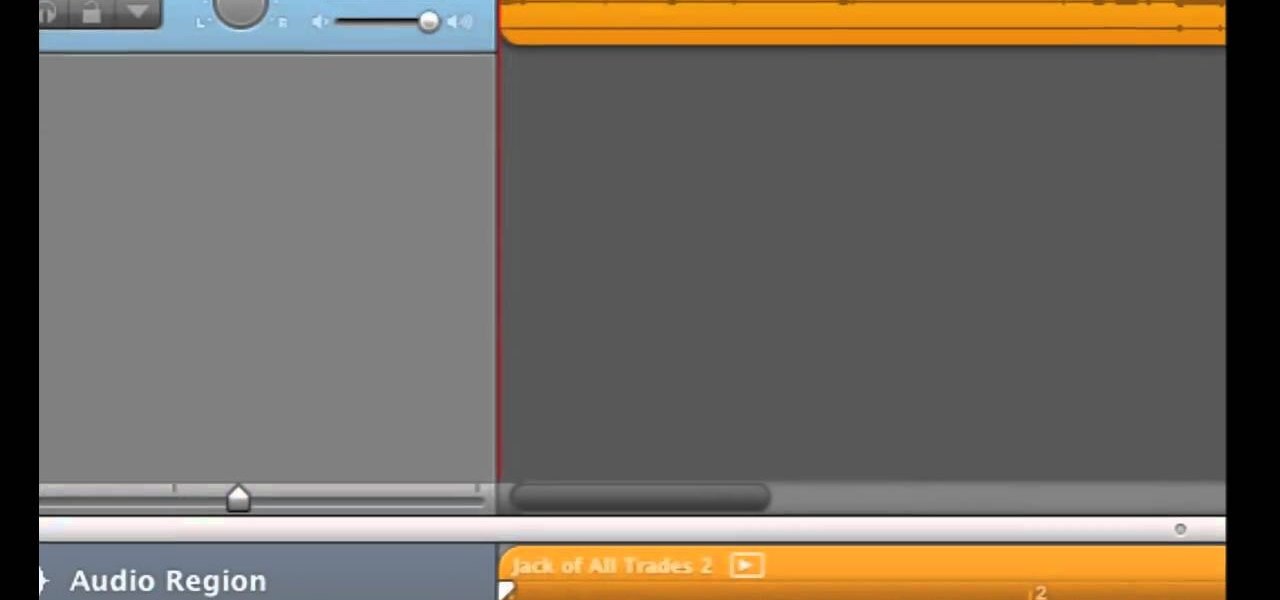
If you've just exported your masterpiece from GarageBand and found that your volume on the song is too low, then you're going to have to fix it. And increasing the levels on your "too quiet" song, you just need to get back into GarageBand and make some adjustments.

This video shows the viewer how to rejuvenate damaged hair with a few simple techniques. The first stage is to not let the hair get damaged in the first place. One of the most common causes of damaged hair is excess use of heat on the hair – either through a blow drier, straightening iron or a curling iron. Another cause of damaged hair is allowing the hair to become matted. This can be sorted out by simply combing the hair. If the hair has become damaged the recommended approach is to get it...

Cooking for the holidays invariably means preparing a lot of food for a lot of people. This includes vegetables like carrots, onions, and squashes. Luckily the Tesco Food Club is here to help. They've got Aiden Byrne showing us the shortcut techniques that restaurants take. You can apply these shortcuts to your own home as well, and save yourself some time and sanity.

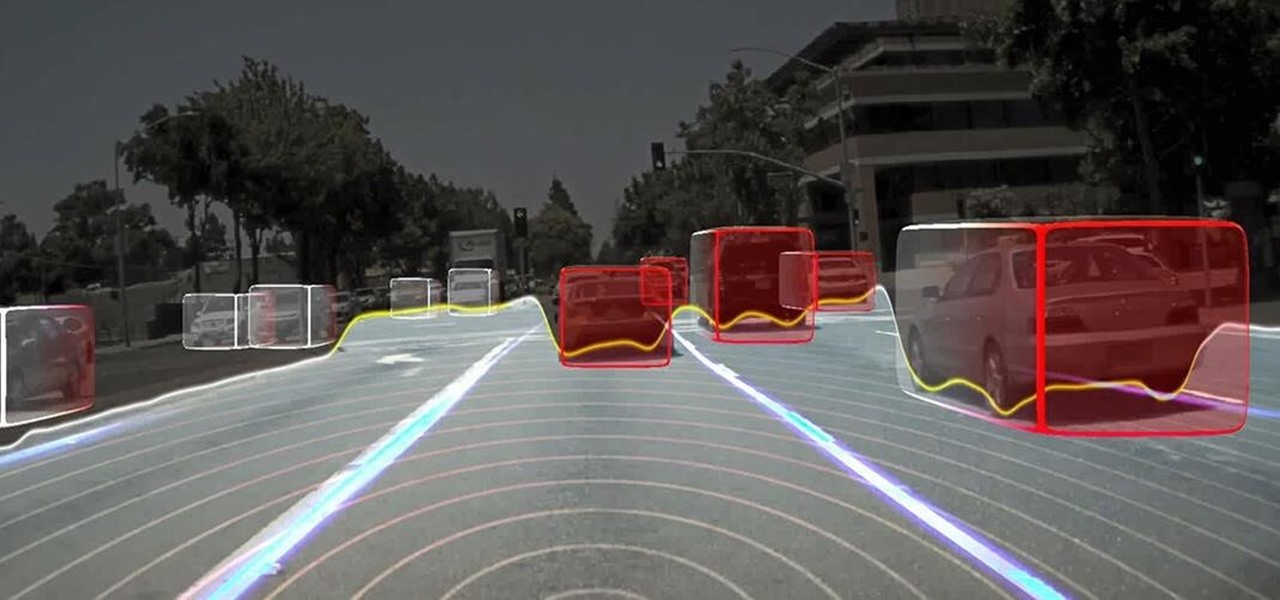
Nauto, which develops driver-monitor cameras and algorithms for autonomous vehicles, is among a growing list of driverless startups able to attract tens of millions of dollars in funding after raising $159 million in its latest round of financing.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.
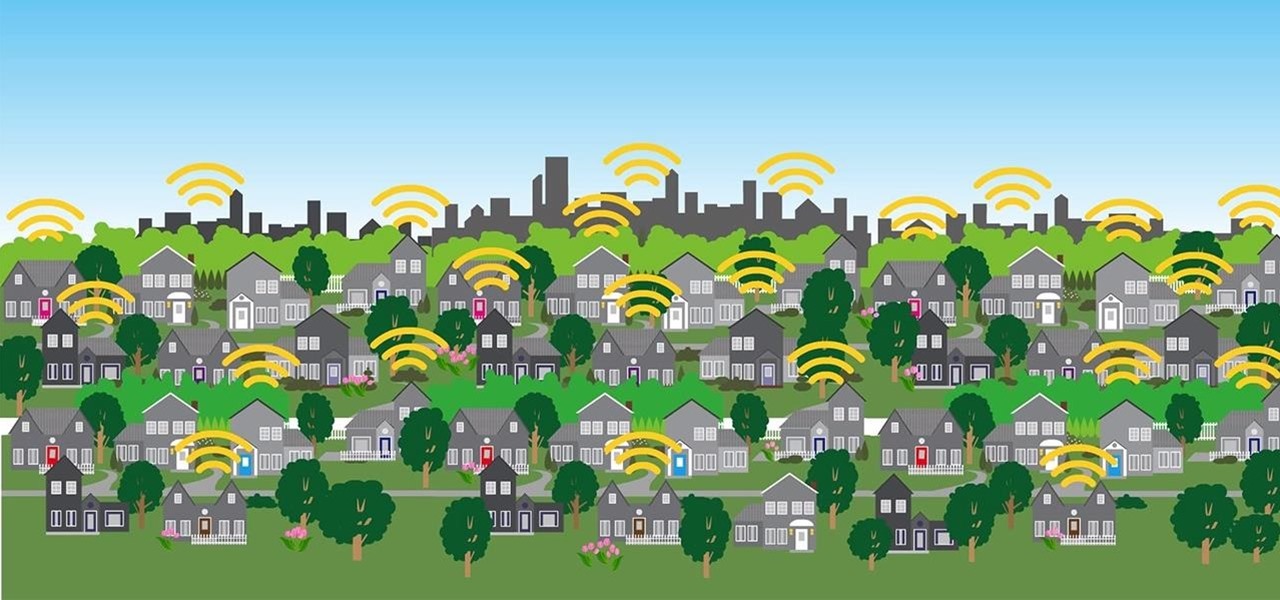
In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

Rock-hard ice cream is the bane of my culinary existence. If I try and scoop it out with a spoon, the spoon invariably bends. If I use a traditional ice cream scooper, I end up with a torqued wrist and one or two pathetic curls of ice cream for my efforts.

Cruise Automation is actively seeking to recruit a lead engineer to head its development efforts of 3D maps with expertise in city environments, signaling the GM driverless unit's move towards a mobility-as-a-service business model.

I grew up in a rural town, and that meant that we dehydrated a lot of food. Even with a hungry family of five, there was no way that we could eat all of the season's tomatoes before they molded, or all of the orchard's apples before they grew soft, or all of the wild mushrooms that we picked. And so our dehydrator was always getting a good workout.

I've never understood gift cards. Aside from being severely restricted as to where you can use them, they're also a strange gift, especially if you don't shop at that particular store. Some even have expiration dates and service fees.

Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

I've cracked thousands of eggs in my life, yet I still usually mess up when I make my morning eggs. Sometimes I crack the egg to hard and end up leaving half of the white on the counter. Other times I don't crack the egg hard enough, and end up spending 20 seconds digging with my fingers until I can pry apart the shell. Sometimes I puncture the yolk on the shell, and other times the entire thing slips out of my hands.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

When I was younger, my family would go to fancy restaurants and I would invariably order a Shirley Temple. (Ironically, the real Shirley Temple actually didn't like it much.) But it's hard to really find anything offensive in this kiddie cocktail: It's ginger ale with a splash of grenadine. There's also the less famous Roy Rogers, which is Coca-Cola with grenadine. The grenadine, red and sumptuous, always made its drinks look and taste much cooler.

Cooking with animal blood is as old as civilization itself. I promise that your ancient ancestors, no matter where you're from, didn't have the luxury of throwing away any part of the animal, including the very lifeblood that used to run through it. Animal blood, along with everything but the skin, would invariably end up in the stew.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

General Motors acquired Cruise Automation in March 2016 for a reported $1 billion (well, at least $581 million). GM President Dan Ammann made a point of being in the press release photograph with Cruise founders Kyle Vogt and Daniel Kan (see photo below). On January 19, 2017, Vogt posted on Twitter: "Took GM Pres. Dan Ammann for a ride in a Cruise AV."

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

With warm weather comes bugs, and with bugs come bites, and with bites come itches. From ticks and spiders to mosquitoes and bees, insect bites come in sundry shapes and sizes, but they all commonly pull an itchy, red reaction out of our bodies.

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell

My first encounter with a phablet was late last year with the AT&T version of the Samsung Galaxy Note 2, having never touched or even seen its highly-acclaimed and pioneering predecessor. Initially, I was a bit overwhelmed by the enormous screen and taken aback by the dated stylus, which brought up ugly memories of my dad using his ten pound PalmPilot.

Most often when cleaning, using your wet dry vacuum cleaner, you tend to pull at the hose while towing it around. This invariably leads to the hose being pulled off very often. In this video, Joe demonstrates how you can overcome this problem and thereby make your ‘Wet Dry Vacuum’ more mobile. Sealing the hose pipe to the cleaner with a duct tape doesn’t help much, especially when you need to put the cleaner back for storage. So Joe shows an innovative and effective way out. He drills a hole ...

Tony Robbins is a megastar. He's on Oprah's level. And he is big. In fact, he has acromegaly: big hands and big head. 6 foot 7 inches tall.

The one arm dumbbell chest press is perfect for strengthening the pectoralis (chest) muscles. Most chest exercises involve compound movements, or the use of more than one joint. Invariably, the triceps and anterior deltoid are often involved in chest exercises.

Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

If you've ever been inside of a real laboratory, you probably noticed how expensive the equipment is. You'd never be able to afford even just one of those ultra high-tech machines required to splice genes or split atoms. Even the lesser machines can be prohibitively costly, including a stir plate.