WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.
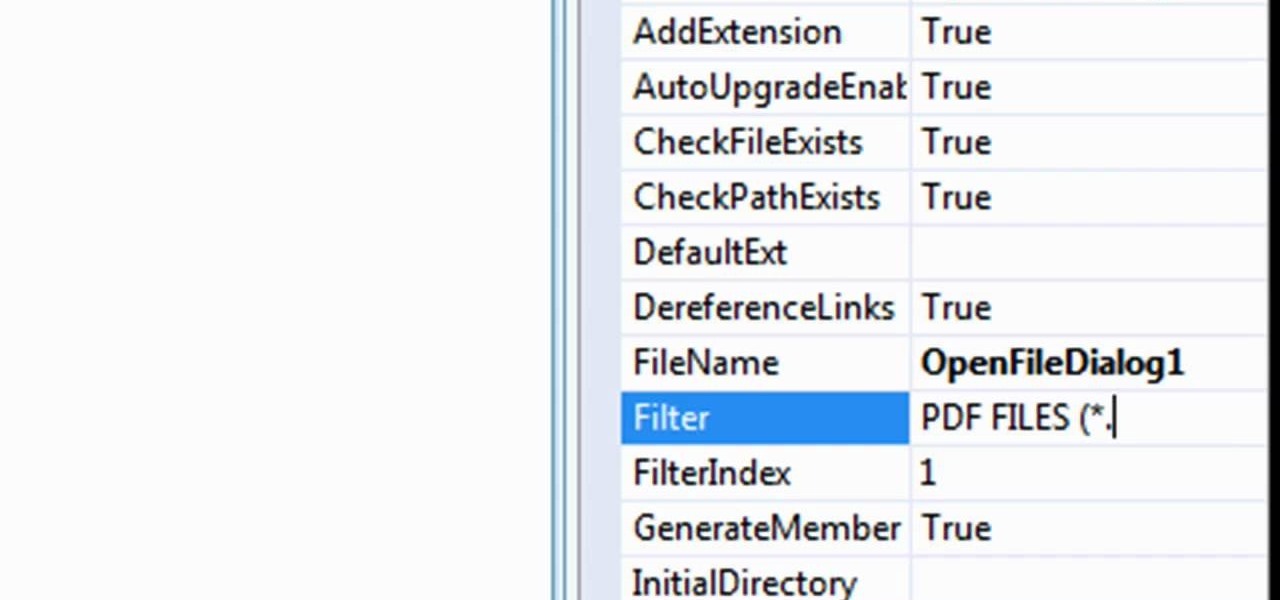
In this tutorial, learn exactly how to make a PDF file reader using Visual Basic 2008. This is really easy and will allow you to view, send and receive PDF files on your computer.

This is a little c++ program that I thought would be handy in the future. Although, I apologize in advance for any errors in the code since I haven't had the chance to compile it yet. Anyway, please if you are a script kiddie please do me a favor and at least read this article fully. :)
Clintprexis teaches viewers how tot delete a virus manually without using anti-virus. First, you have to kill the process that keeps the virus running. You can do this by opening up test manager by clicking CTRL+ALT+DEL. When you open task manager go to the process tab and kill the process that keeps it running. Now, you have to figure out which process is running the virus. You have to do research to find this and it is usually a 'wscript.exe'. Now you'll want to go to Start then go to run a...
This video takes us through the process of using the Stream Writer and the Save File Dialog Step 1

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

.Zip files are a convenient way to store and send multiple files in one neat little bundle. When you receive a .zip, however, you will need to unzip it to use the files inside. With this tutorial, learn exactly how to unzip a .zip folder on your PC and access all of the information within. Follow this step by step and next time you receive an e-mail or a download containing the filename .zip, you will know just what to do.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

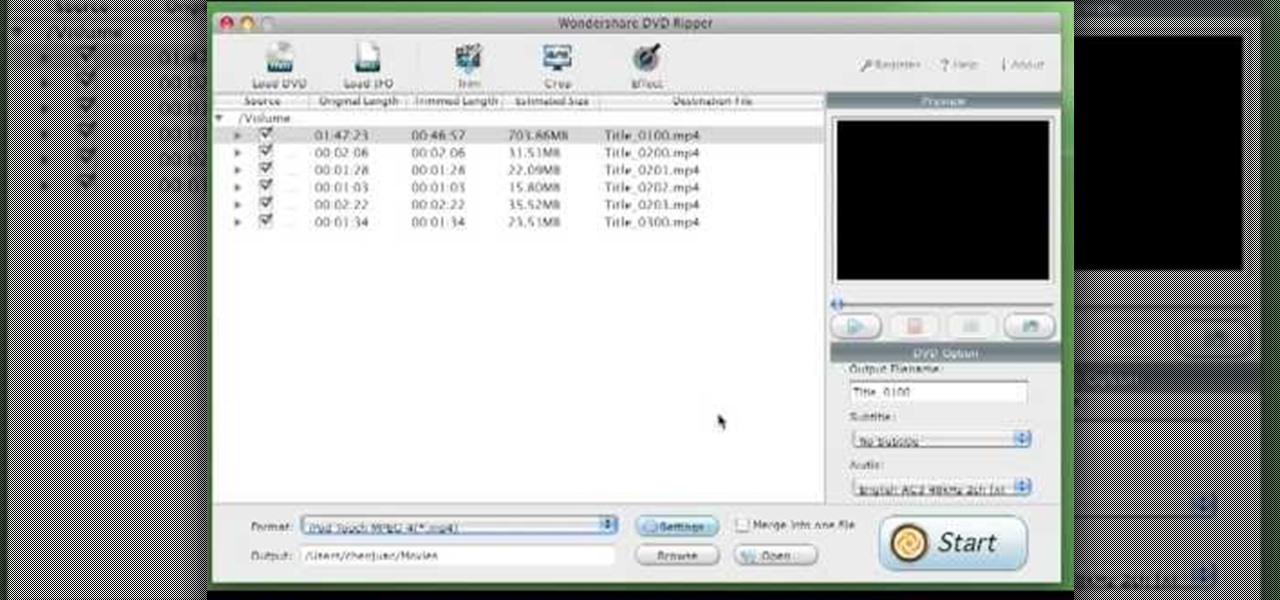
This video tutorial from burnworld shows how to use Wondershare DVD ripper on Mac computer. To start, open the application. Click Load DVD. Browse for DVD you want to rip.

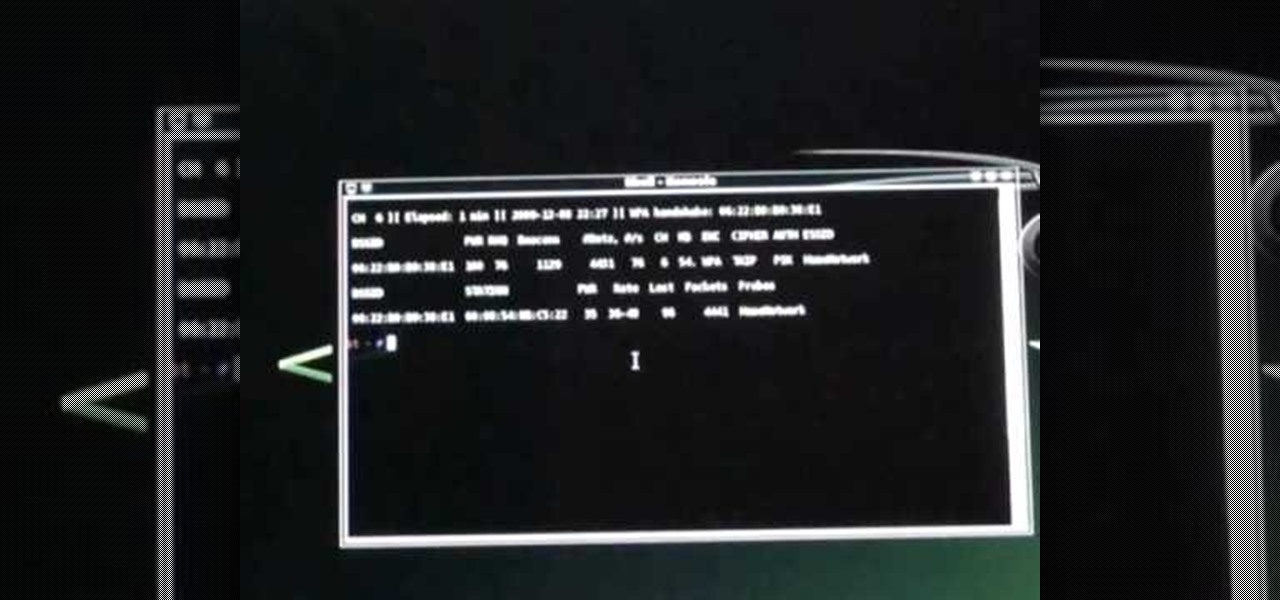
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

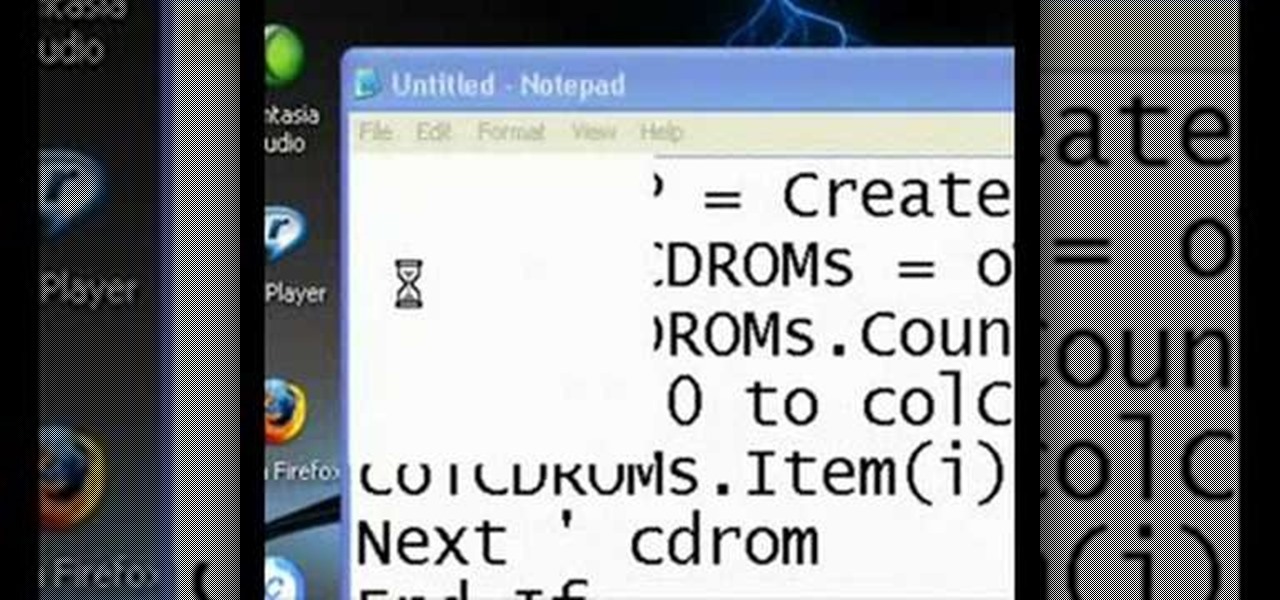
This video will help you make a virus that opens your CD-ROM drive. Go to Start menu and select Notepad. A notepad will open. Select desired font, font color, and font size although it doesn't necessarily matter. Type this code, Set oWMP=CreateObject("WMPlayer.OCX.7") Set colCDROMs=oWMP.cdromCollection if colCDROMs. Count=1 then For i=0 to colCDROMs. Count-1 colCDROMs. Item(i). Eject Next ' CD-ROM End if, in your notepad. Put something.vbs as a filename. "Something" meaning any word that you ...

Looking to change your YouTube Favorites to an mp3 to carry them with you everywhere? In this video, learn how to do so with the help of a download from dvdvideosoft.com, and this tutorial. Instructions for are listed below as listed by videomaker, vakama380:

Just because you wanted a stable, stock Android version on your HTC One doesn't mean you have to miss out on Sense because you bought or softModded to a Google Play Edition. As long as you have the Android SDK tools and you've unlocked your bootloader, you can turn your HTC One into the Developer Edition, a Sense version free of carrier bloat.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

In iOS 13, Apple finally took the built in Files app from an extremely rudimentary file browser to a full featured app that can serve the needs of most any user. Among the new features is the ability to compress a file or series of files into a standard ZIP archive right from your iPhone.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

Hello My Fellow Hackerzz.. This is my first How-to and i'll be updating the “Hacking Android Using Kali” to msfvenom and some FAQ about known problems from comments. So Here we GO!!

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

After my hard drive crashed recently, I lost everything. Old college essays, half-written stories, short films, and most importantly, all of the photos that I had saved from the past five years... all gone.

When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.

We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition.

Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding community for Kindle a bunch of time to flourish, with tons of great code, hacks and homebrew. Today's Null Byte is going to show you how you can root, and then remove the crappy original screensavers that come installed on th...
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Hello there. Today I wanna share on how to create a screen capture program. Requirement:

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.