
How To: Make LED ice cubes
Learn how to make LED ice cubes with this tutorial! Steps:


Learn how to make LED ice cubes with this tutorial! Steps:
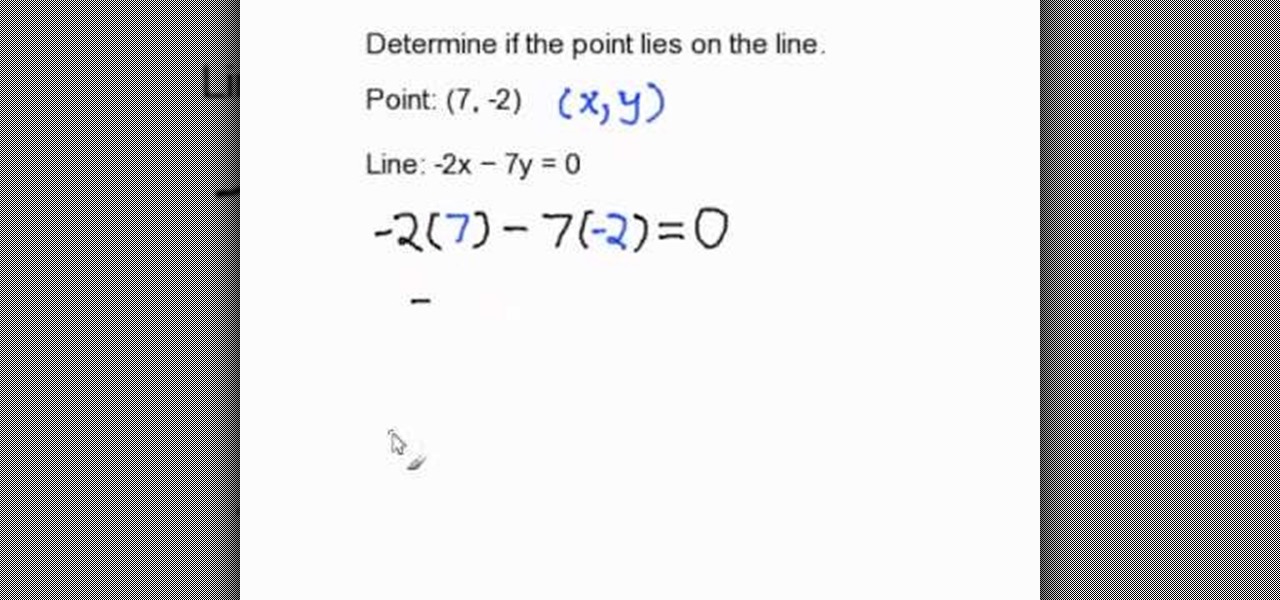
In this video, we learn how to determine if a point lies on a line in standard form. In order to do this, you will need to substitute the X and Y value with the ordered pair that is given. The X value is the first number and the Y value is the second number. Re-write your equation, substituting in the numbers to the appropriate spots. Now, simplify the equation by doing multiplication with the negatives and positives (if given). When you get through the equation, you will end up with the solu...
One of the most common positives one hears about Windows Vista is that it's pretty. Indeed, Windows Vista has new icons, a new theme and it does look nice. But what if you want to add even more pizazz to your desktop? In this video tutorial, you'll learn how to change any desktop (shortcut) icon. For more information, and to get started changing icons on your own desktop, take a look!

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.
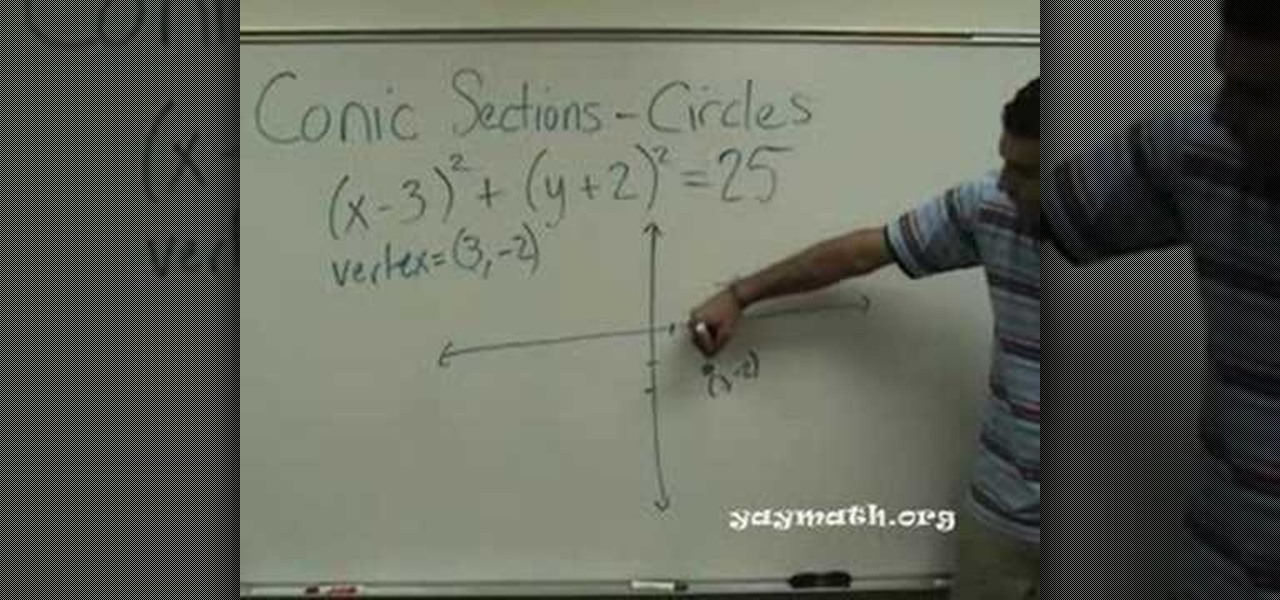
In this tutorial, we learn how to graph a circle. When given an equation to graph the circle, you will first need to find the vertex of the circle. Once you find this, you can use those coordinates to mark the vertex on the graph. Follow the negatives and positives to go up, down, left, and right on the graph. Next, you will need to find the 'r' value of the equation. After this, you will use this to continue to graph the rest of the points around the vertex. When finished, draw the outline o...

There are signs you're having a baby even before you miss a period. You Will Need: * A knowledge of physical symptoms

You know this is the job for you. Here’s how to convince the person doing the hiring. Learn how to do well in a job interview.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.
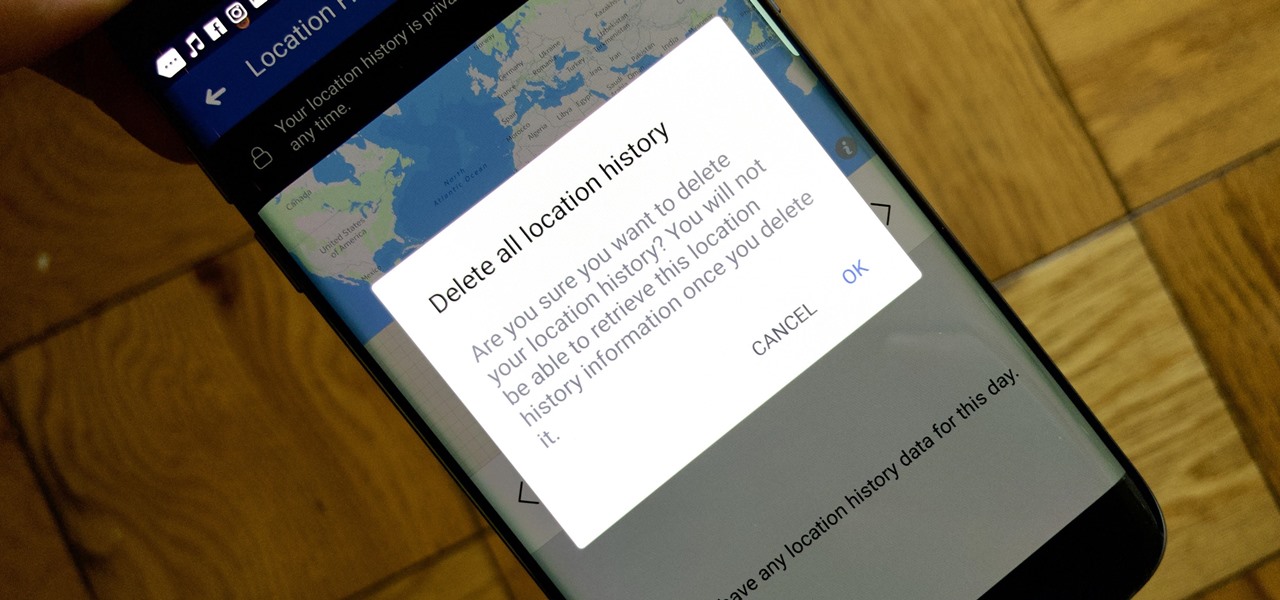
Facebook's shadiness when it comes to user privacy has never been much of a secret. The Cambridge Analytica scandal, however, has thrown the company and its practices into the limelight, with users taking their data more seriously than ever. If you're one of those users, you might want to check your "Location History" to see if and how Facebook's kept tabs on your whereabouts.

From its official launch back in September, iOS 11 has been equal parts revered as it has been criticized. Even with all the great, new features we've come to expect from a major iOS update, plenty of bugs and glitches have forced users to overlook the positives. Perhaps that is why, four months later, 25% of iPhone owners are still running iOS 10.3 or earlier.

There's never an Apple announcement without some good ol' anger and backlash. To be fair, Apple received some really positive feedback from parts of the iOS 11 presentation at WWDC back in June. Fans had been waiting for years to customize the Control Center, as well as for native screen recording. But if there was one thing that got fanboys and Apple haters raging about in unison, it's that weird, incomprehensible notification system.

Can't stand seeing your Facebook news feed full of peoples' good news and awesome accomplishments? Those oversharing friends are, in a sense, hampering their great news simply by sharing it. If you hold back and keep your accomplishments from friends, you might find even more success than if you'd shared with your support network.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

We've heard the rumors for months, but it's finally official: The iPhone 7 will not include a traditional 3.5 mm headphone jack. Instead, you'll need to hook your favorite headphones up with a Lightning adapter (or use ones with a Lightning connector built-in) and connect to your phone using the same port that your charger occupies.

When you're trapped at your desk before a jumble of data just waiting to be categorized, or zoning out during an important meeting, your mind wanders and, chances are, you feel a little guilty because of it. Yet you shouldn't try to reign in that distracted thinking. Instead, let your brain get distracted, and you'll unconsciously strengthen your memory.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

When your cat goes missing, chances are it's just chilling in a cozy spot under the couch, or maybe even hiding from you. So it's okay to not freak out just yet. Cats love to hide as if they're spiders, and even their hiding spots are similar. You can find them in corners, on the refrigerator, and according to my roommate, even the dryer hose is fair game.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

Google Now, Siri, and Cortana aside, the main way you interact with your smartphone is through the keyboard. Every app you use, every search you perform, every message you send—the most fundamental interface between you and your device is that handful of characters and those 26 letters on the bottom half of your screen.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

A dead man's switch is a fairly simple concept. If you don't perform a specific task before a set amount of time, it'll perform a specific action you set. They can be handy not just for hackers but for everyone who wants to protect themselves, someone else, or something tangible or intangible from harm. While there are more nefarious uses for a dead man's switch, white hats can put one to good use.

Samsung's lineup of Galaxy Note devices for 2020 include the specs-behemoth Galaxy Note 20 Ultra and the slightly more cost-effective Galaxy Note 20. Excuse the pun, but there's a lot to unpack here in terms of unique features and hardware.
Truecrypt 5.0 adds many new features, most importantly Windows system partition encryption. To put it in slightly inaccurate layman's terms, this means encrypting your entire C: drive. Even if you already write your sensitive data to an encrypted space, files are sometimes squirreled away in unencrypted temp space or in the page file where they may be recovered. Using Truecrypt to encrypt your Windows XP system partition will help eliminate this problem.

The electric air freshener is one of those devices that seems like it could only have one possible function, but can actually be repurposed in a few different ways. If you're looking for a practical use, you can turn it into a bug killer, but it's also perfect for pranks.

Spent the weekend with Sprint's new phone, the HTC Evo G4. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple will be announcing the new version of their phone this week. If it's comparable to leaked phone shown over at Gizmodo, then to say which phone is better is debatable. The iphone might have a better battery life but the Evo has an unlimited data plan, unlike AT&T's new tier pricing structure.
One of the things I consistently notice amongst fellow internet users is that many people don't know how to properly search for stuff. Google may have served you well in the past, but I'm going to share a few little tricks with you to help make your search results even spiffier.

Written by JD Coverly of WonderHowTo World, LoadSave:We've spent the last week with Sprint's new phone, the HTC Evo 4G. Specification wise, it's better than Verizon's Incredible and T-Mobile's HD2. Apple has unveiled the new version of their phone this week and thankfully it's debatable as to which phone is better. The iPhone has better battery life and a more robust App store, but it suffers from a smaller screen, smaller camera resolution, no HDMI out, face talk only on wi-fi networks, and ...