When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

SCRABBLE. To some it's just a game, but to me it's life or death. Well, not really, but it feels that way anyway. On a normal weekend, a game becomes much like Jon Thomas' "friendly game of death Scrabble."

When you're flying your model airplanes, it's inevitable that it will eventually suffer some minor damages, like scuffs, breaks and bends. This video tutorial will help you alleviate and repair any damages to your flying model airplane to get you back in the skies again.

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.

Even if you're a master at the grill, dealing with the tank can be a little intimidating if you've never done it before. But there's really not much to worry about. Exchanging or refilling your gas grill tank is easy to do.
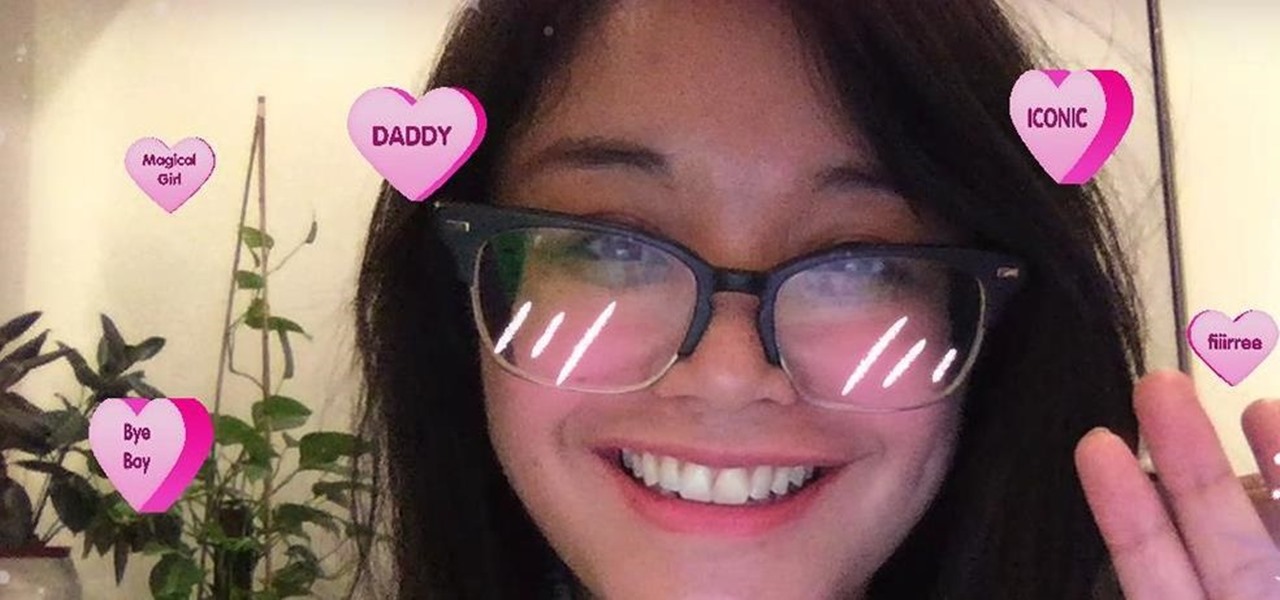
Mobile augmented reality company Snapchat now has a special option for romantic message exchanging this Valentine's Day, a day which, incidentally, happens to be the first one in 116 years where Sweethearts, the original heart-shaped candy, will be unavailable for purchase.

The Huawei Nexus 6P was released a little over a year ago, but despite doing moderately well in sales, the device has had more than its fair share of issues. When first released, there were numerous reception and memory management difficulties that left users extremely frustrated, though, those problems were solved with updates pushed by Google.

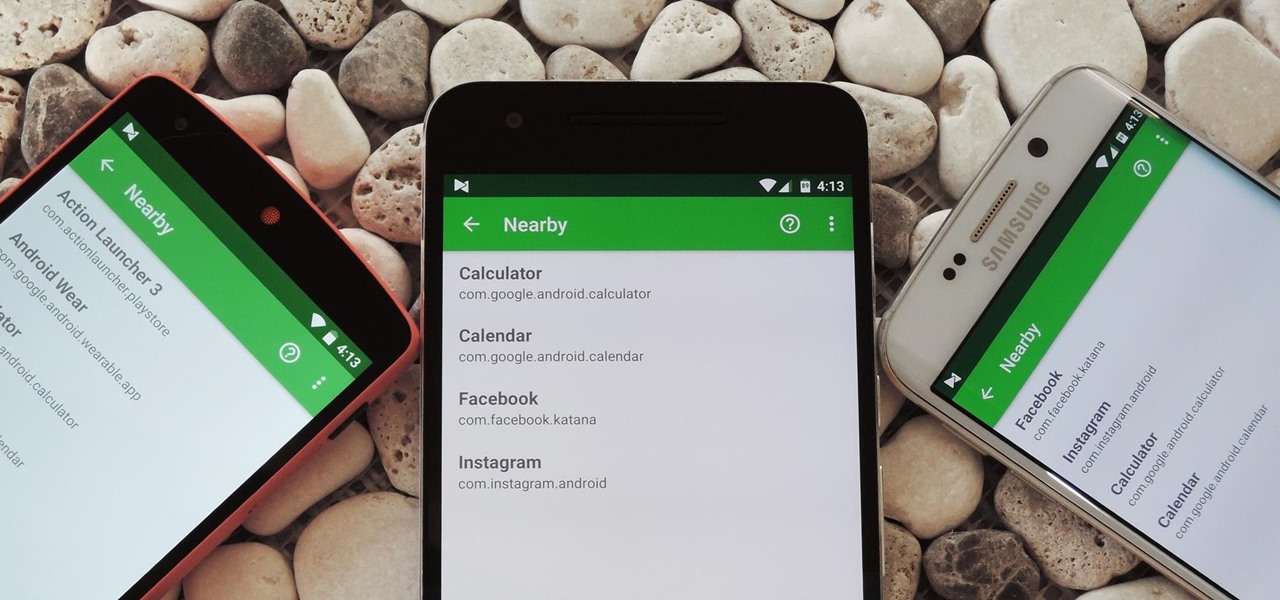
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

I've never understood gift cards. Aside from being severely restricted as to where you can use them, they're also a strange gift, especially if you don't shop at that particular store. Some even have expiration dates and service fees.

I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little.

It's one hell of a device, but the Samsung Galaxy S5 is still susceptible to the many hazards that other smartphones are prone to: theft, cracked screens, poor battery life, and particularly, overheating.

Send an email prematurely? Forgot to attach a file? Accidentally addressed it to the wrong person? It happens to the best of us. But what can you do to get it back? Hack into the other person's email account and delete the email before they get a chance to see it? Unless you're a hacker extraordinaire, that option is unlikely. So, what can you do? If the email has already been sent, you're probably out of luck. Even if they didn't read it yet, your chances of retrieving it are slim. But some ...

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Break out the office supplies and kitchen utensils, because improving your morning makeup routine is about to get a lot easier. Some of the things you have lying around the house can provide the perfect solution for some of the most common beauty problems. We've collected 10 of our favorites.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

You're currently playing a heated game of Scrabble or Words with Friends. The game is close, too close for comfort. But you're not sweating because you're confident. You play a huge word that puts you in the lead, but then when your letter tiles are drawn...

It's sad to say, but I will no longer be writing up anymore Scrabble Challenges. Frankly, I just don't have the time to make them now. And though they are incredibly fun and "challenging" to conjure up, I'm not sure that people are finding them as useful as I had hoped. But really, it all comes down to time. So, unless I have a future craving for puzzle-making, last week's Scrabble Challenge #20 was the last one.

Last week's challenge brought up a good question (thanks Lisa) regarding the functionality of the Official Scrabble Players Dictionary, 4th Edition, both online and in print form. The word TACTICAL was the answer to the first puzzle in that challenge, but when you search for the word directly in the print version, it can't be found. Likewise, when you search the online dictionary on Hasbro's site, you won't find it either. Go ahead, try it. You won't find it looking for TACTICAL specifically.

In an ideal world, the art of gift-exchanging is a joyous, wonderful thing that makes both parties feel equally good. But as many of us already know, gift-giving is also an emotionally charged social minefield that can leave many of us feeling... awkward.

The 2011 Toronto International Scrabble Open (TOSI) took place last weekend, with former World Champion Adam Logan beating out all of the human competition for the $3,000 grand prize. But when it came time to take on the Quackle program in the Human vs. Computer Showdown, he lost his first two games and won the last two, ultimately losing with a measly 28-point differential of the combined total scores. But he still came out three grand happier.

In recent years, communication has become more intimate with the advent of applications like Skype and FaceTime, but what about the longing for actual physical contact? What if you could feel a loved one's hand, or even exchange a kiss? Impossible, right?

Last time, we looked at archaic cryptography, so you should have a basic understanding of some of the concepts and terminology you'll need. Now, we'll discuss one of the most important advances in computer security in the 20th century—public key cryptography.

There are a lot of fantastic video games out there. Indie Games Ichiban's bread and butter is making sure that you steer clear of the bad ones and embrace the good. But really, the biggest goal here is to help everyone have more fun. To that end, today a game is not recommended, but an event. If you like games—not just video games—but tabletop, board and even hopscotch, then PAX Prime is one of the best events you could possibly go to.

You've been on Google+ for a few weeks now. You're loving it. You're exchanging thoughtful posts, pictures with your friends, meeting new people and following lots of interesting, intelligent people. There's just one problem.

If you haven't noticed yet, I've started dishing out some "Scrabble Bingo of the Day" articles that showcase interesting and somewhat unusual seven-letter words (or longer) that could give you an extra 50-point bonus on the board, as long as you empty your rack. So, for this week's Scrabble Challenge you'll have to get your brain in gear, because it's a tough one based of high-scoring bingo plays.

noob - Short for "newbie." Someone with little to no experience or skill. In some gaming communities, there is fierce debate over the distinction between "noob" and "newb"—one being derogatory while the other simply indicates being a novice. While some may argue the semantic differences, "noob" is the most common spelling seen around the internet, for both purposes.

Let's face it, not every logophile is addicted to Scrabble. Without the use of a timer, Scrabble can be a pretty slow game. Even in clubs and tournaments where the standard time limit is 25 minutes per person for a two-player game. Now, take away time restrictions and add two other players and you've got a game that could take up to 2 hours! It all really depends on who the competition is.