This is a lengthy, detailed series on iPhone development, for which you'll need an Intel-based Mac computer, running Mac OS X 10.5 (Leopard) or higher. Then, before you actually get started developing for the iPhone, you'll need to register as a developer with Apple. Then, you'll need to download Xcode and the iPhone SDK. Once you have all this, you can start developing iPhone applications!

Learn how to cut tile with this DIY video tutorial. If you need to make angular and circular cuts, use an angle grinder and fit a diamond disk. You'll need to fit a continuous diamond disk, not a segmented one, because a segmented disk will chip the tiles. And if you're using an angle grinder, don't forget your personal protection equipment, ear muffs, dust mask, and eye protection.

Balloons are not just a way to entertain kids. Watch this video to learn how to use balloons to mimic complex real life objects. In this video the presenter makes a four lead clouds using only balloons.

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.

As summer mosquito season approaches, researchers are warning people with previous exposure to West Nile virus to take extra precautions against Zika. A new study found that animals with antibodies to West Nile in their blood have more dangerous infections with Zika than they would normally.

Please read the following in Rod Serling's voice. Picture, if you will, a mother. She comes home after a long day at the office, relieved that she took some chicken breasts out to thaw and will be able to make a quick and easy dinner for her family. She opens her refrigerator to get the chicken, but to her horror she does not see it… she forgot to take the chicken out of the freezer after all. What will she make for dinner now? How will she feed her family? She has entered…the Panic Zone.

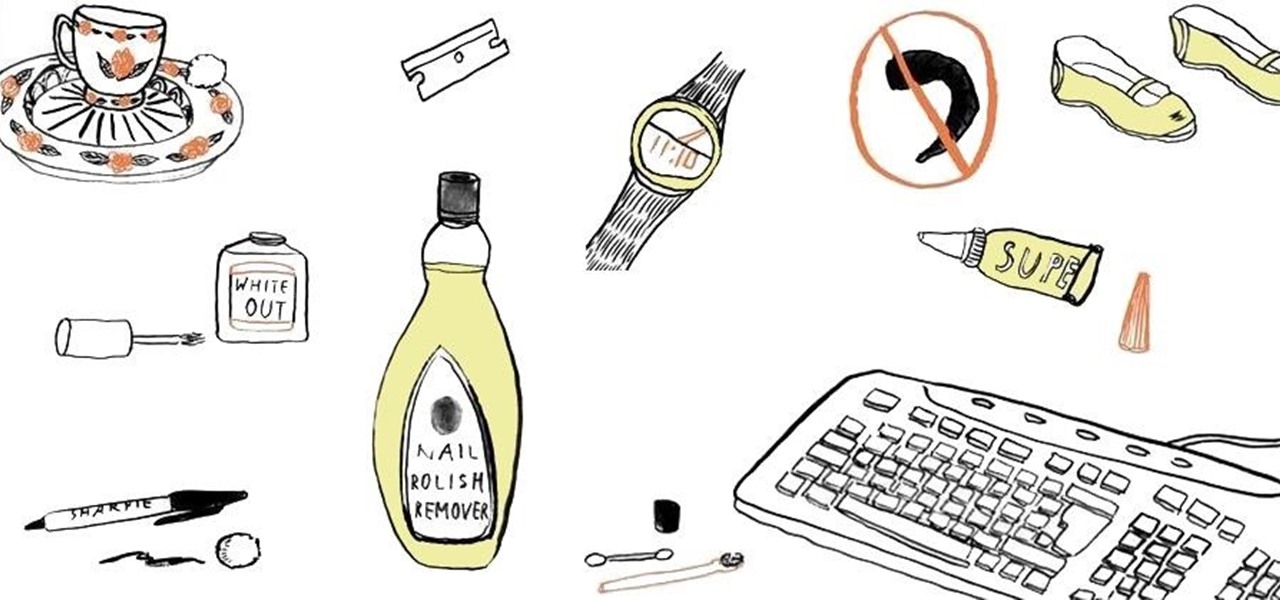
Acetone-based nail polish remover is great for removing nail polish, and it's also great for some DIY uses around the home. From eliminating scratches to fixing the consistency of correction fluid, its uses are varied but all effective. With nail polish remover, you can also clean your computer keyboard, get rid of ink stains, and even remove leeches from your skin. Talk about versatile!

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Warfare strategies have become an inspiration to different marketing professionals, many of them drawing influence from Sun Tzu’s Art of War. This ancient Chinese text provided treaties on how to effectively manage resources, tactical positioning, and timing attacks. It also states that “..if you know your enemies and know yourself, you can win a hundred battles without a single loss”, a basic concept in which you have to always watch your competitor to anticipate his next move.

Love folk art but could do without the folk? Prepare to have your heart stolen by a self-folding origami automaton.

On October 7th, the IndieCade Conference will open its doors to some of the most innovative minds in the independent gaming industry. The three day event located in Culver City, California includes presentations by notable indie designers, workshops, galleries, and mixers. On the following day, however, the IndieCade Festival begins. Unlike the conference, the festival includes events targeted at gamers and the general public. While a $15 wristband will grant you access to keynotes, events, a...