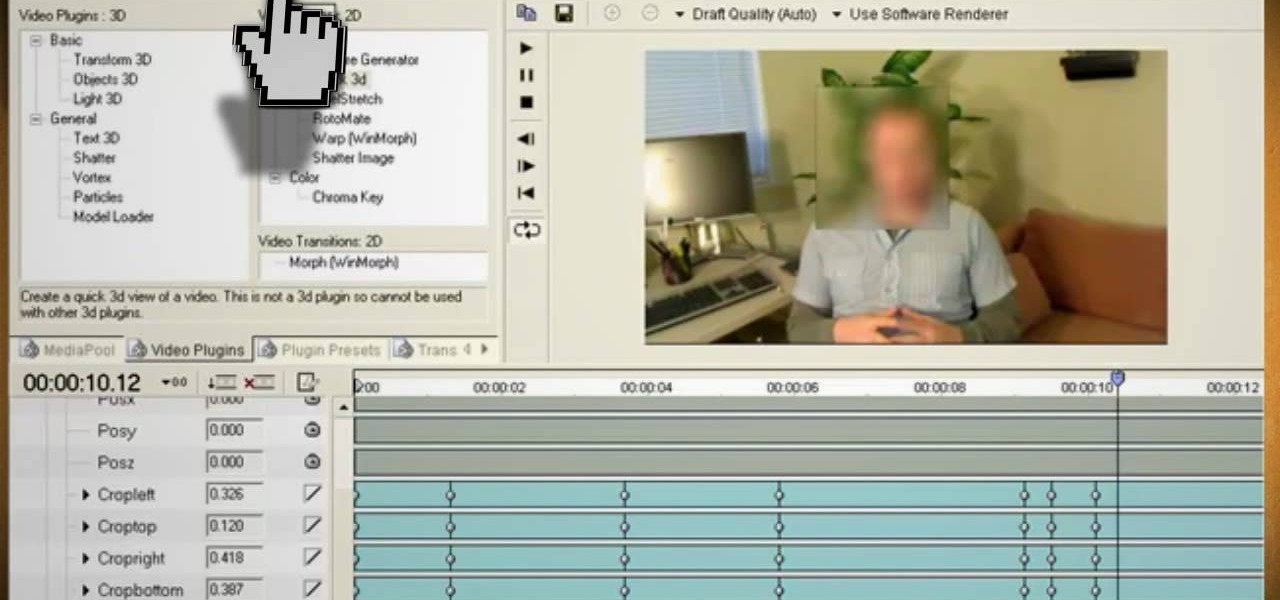
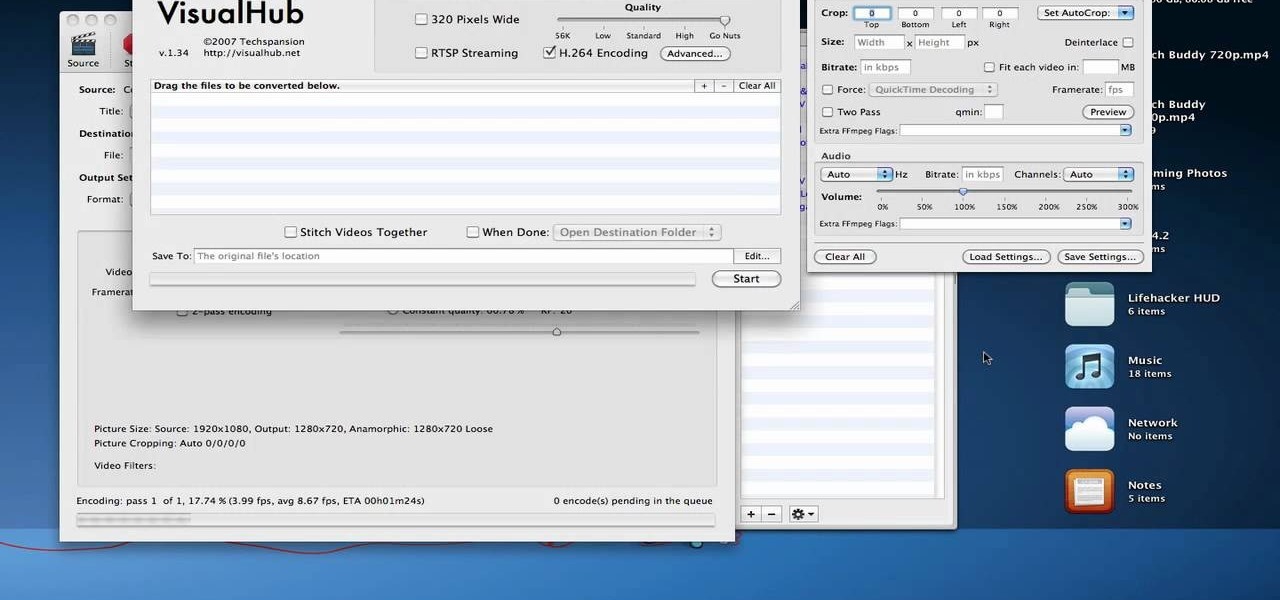
In this video by Tinkernut, we are taught all about the basics of converting and encoding videos into their various formats. He starts off by covering the video containers. Then he breaks down what is contained in these containers. He goes over the what data per second you need for each way of watching the videos. Then he suggests a couple of programs that help you convert your videos in the appropriate format for watching your videos in the many different ways out there.
Apple recently released iOS 4.2 for all devices— iPad, iPhone and iPod Touch— and one of the best features is AirPlay, which lets you stream video directly to AppleTVs. There's only one problem— it will only stream video that meet's Apple's specifications.

HD demo on how to set encoding parameters for proper Vimeo meady video at 720p resolution. This will give you crisp HD video ready for Vimeo upload right from iMovie 08.
Adobe Media Encoder CS4 takes the place of several tools that users had to rely on for processing and compression. The Adobe Media Encoder CS4 converts to several different formats, including formats for web and mobile devices. There are also speech transcription option and batch processing. See how to use the Adobe Media Encoder CS4 in Premiere Pro CS4 for Flash video encoding and exporting from Premiere Pro CS4 in this tutorial. Use the Adobe Media Encoder CS4 in Premiere Pro CS4.

This Flash 8 tutorial covers some basics on various options of encoding videos into Flash flv format. Encode videos into Flash (flv) format using Flash 8.

Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single server that can handle OS X, Windows & Linux simultaneously, and use the best audio encoding system for Windows Media Center and Zune.

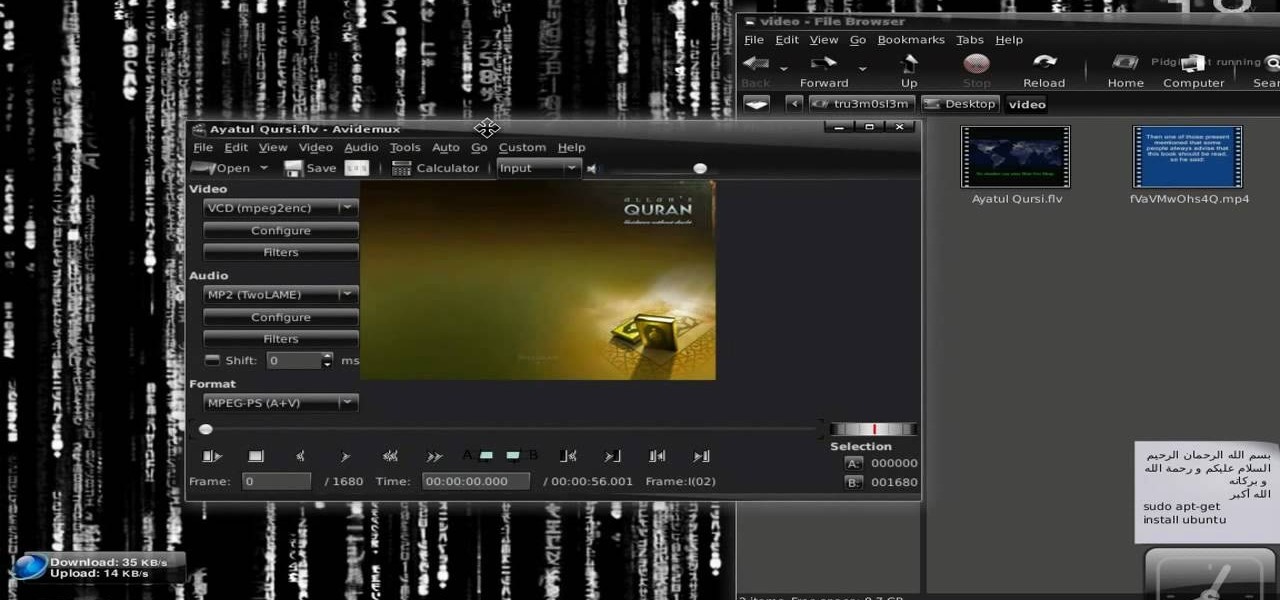
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to convert video formats with Avidemux on Ubuntu Linux.

Justin from Top Ten Reviews demystifies the DVD copying, ripping, and burning process as well as understanding regions, AAC, and other encoding codecs.

Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

One of the best features of Apple's Final Cut Studio is the disc designing feature DVD Studio Pro. With its ability to create high-end DVD masters, you can easily make discs for your indie film, or maybe even a professional movie. DVD Studio Pro is tightly integrated with Final Cut Pro and Motion, rendering the projects into DVD format without encoding to intermediary formats.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

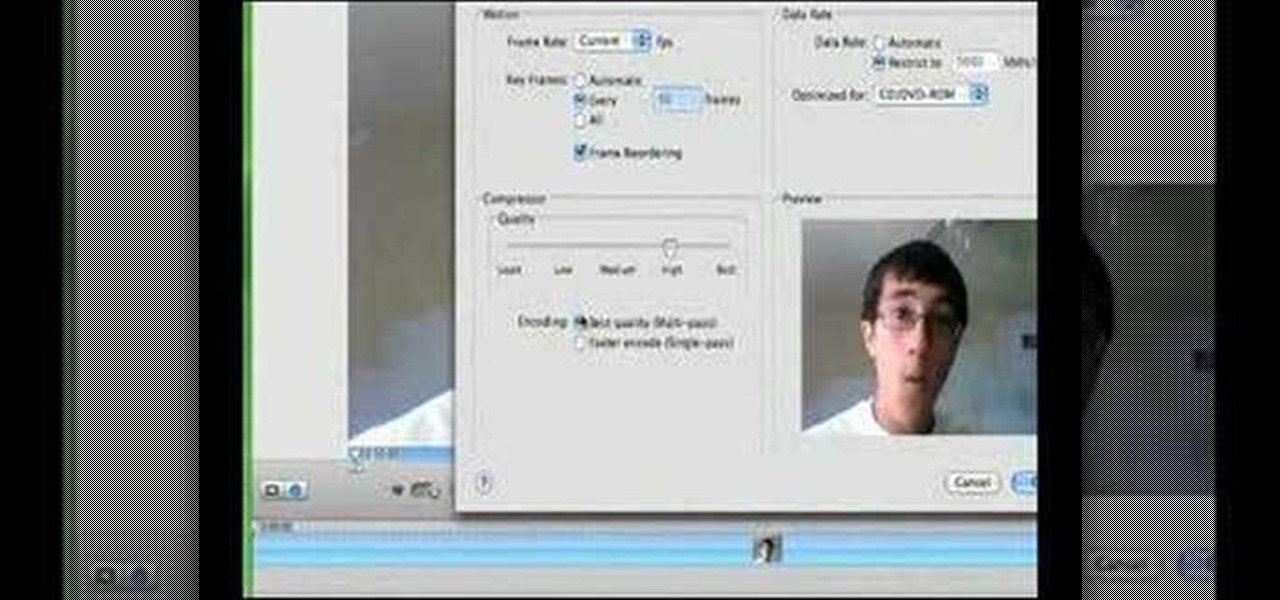
In this how-to video, you will learn how to compress iMovie files into QuickTime files to make them look really good on YouTube. First, open iMovie. Click Share and click Share again. Go to Expert Settings and click on Share. Click on Options and go to Settings. Change it to h264, current frames per second, and every. Restrict should be set at 5000. Optimize it for DVD and change encoding to best quality. Change the size to NTSC 720X486. Check de-interlace video and hit okay. Change the sound...

Whenever you see a website that has some weird fonts or characters displayed on the web page, like a website containing Arabic fonts, but which are not displayed properly, then InshaAllaah, check this tutorial and you'll have the problems rectified.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

In this video tutorial, viewers learn how to export MP3 with Audacity. Users will need to download the Lame_enc.dll encoder. The download link is located in the video description. Once downloaded, open Audacity and find the song that you want. Once you have found your song, simply drag the song into the program. Now click on File and select Export As MP3. It will then ask you to Lame_enc.dll file. Click on Yes and locate the file. Now wait for your file to finish encoding. This video will ben...

David Shrein provides a video recording with step-by-step instructions on how to utilize the DVD ripping software 'Handbrake' on a computer running Mac OS X. He shows how to deal with an initial error message, and then moves onto selecting the DVD. You have to be careful as to what you choose, as different DVDs will have different numbers of chapters and features, which use different settings in Handbrake. He shows how to select the right settings for a movie, and preview a chapter using pict...

This video will show you how to use video and audio to hide your identity. After you have your audio and video you will need a converter program, for example Format Factory which will convert the audio and video into the necessary formats. You will be encoding your clip as an AVI Video, as well as MP3. To start you will need to change the pitch of the audio track. A good program to use for this is Audacity. Play around by making the pitch either higher or lower. Save it as a Wav file To edit ...

In this video tutorial, Chris Pels will show how information can be passed from one page to another using a query string. First, see how to construct a query string including variable names and values from information on a data entry form. Next, see how to access the query string information when the page is posted including how multiple query string variables are handled. As part of the server side processing of query string information, see how to implement validation for existence of query...

In this tutorial, we learn how to rip a DVD with a free DVD ripper. If you want to rip a DVD that you own so you can play it on your computer, this is an easy way to do it for free. To do this, download and install Free DVD Ripper 2.25. First open the software and then open your DVD up and select the title. Next, change the language and other settings as you prefer. Play the DVD just to make sure it works after this. You can change the output settings as well, if you want the movie to be play...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to build a motorcycle camera mount for under five bucks.

In this how to video, you will learn how to convert DVD movies to AVI or any other type of file for free. First, you will need to download DVDx 2.1 and the install it. Next, open the program and insert the DVD disc you want to copy. Go to file and click DVD root. Find the video and select the video_ts folder. You will see the IFO files. Look for the one with the longest time. Click on this one and press select. If you have a DVD already ripped on your hard drive go to file and click open IFO....

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

The Camera app on your iPhone includes new features with the iOS 17 update that will help you take better photos and more impressive videos, but there are a lot of cool new things available that you might not see right away.

That didn't take very long! Yesterday, after a lengthy delay, Google opened up the development kit for their Chromecast HDMI dongle.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Many of the iPhone 15, 15 Plus, 15 Pro, and 15 Pro Max features were carried over from last year's models. Still, quite a few capabilities are exclusive to the 2023 lineup, and some may be worth the upgrade.

Filmic Pro harnesses the full native power of your iPhone or Android phone — and then some. If your smartphone shoots in 4K resolution, Filmic Pro will let you choose that resolution. However, it's not all about the pixels — bit rate is an essential factor in determining the overall quality of your 720p, 1080p, or 4K video, something Filmic Pro gives you full control over.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.