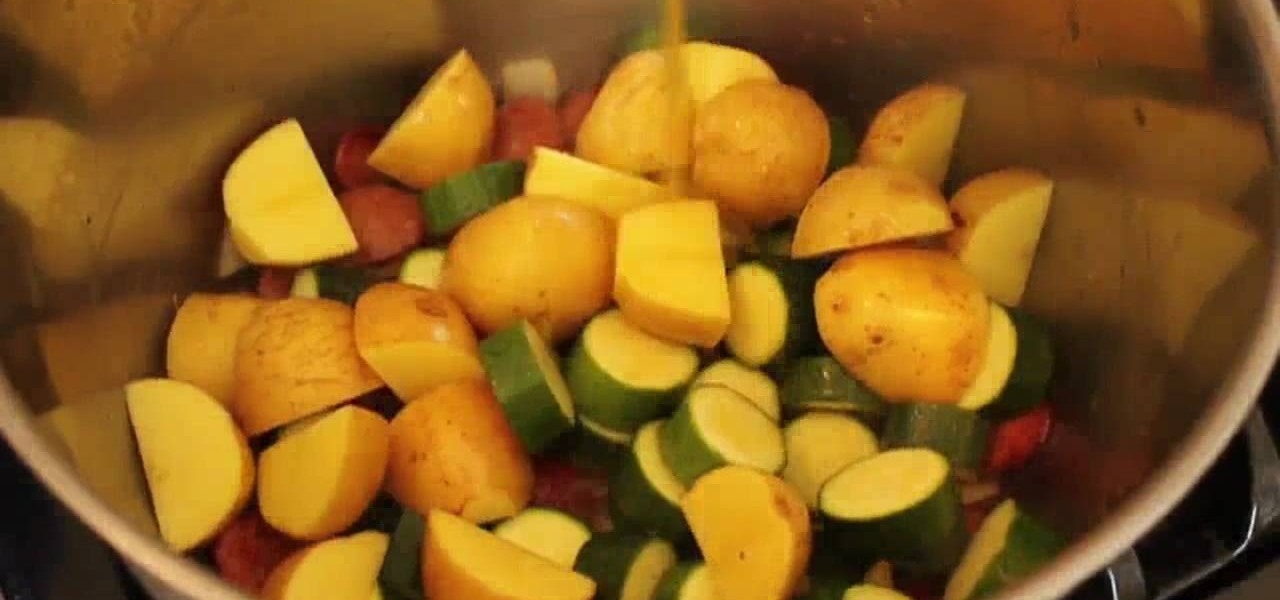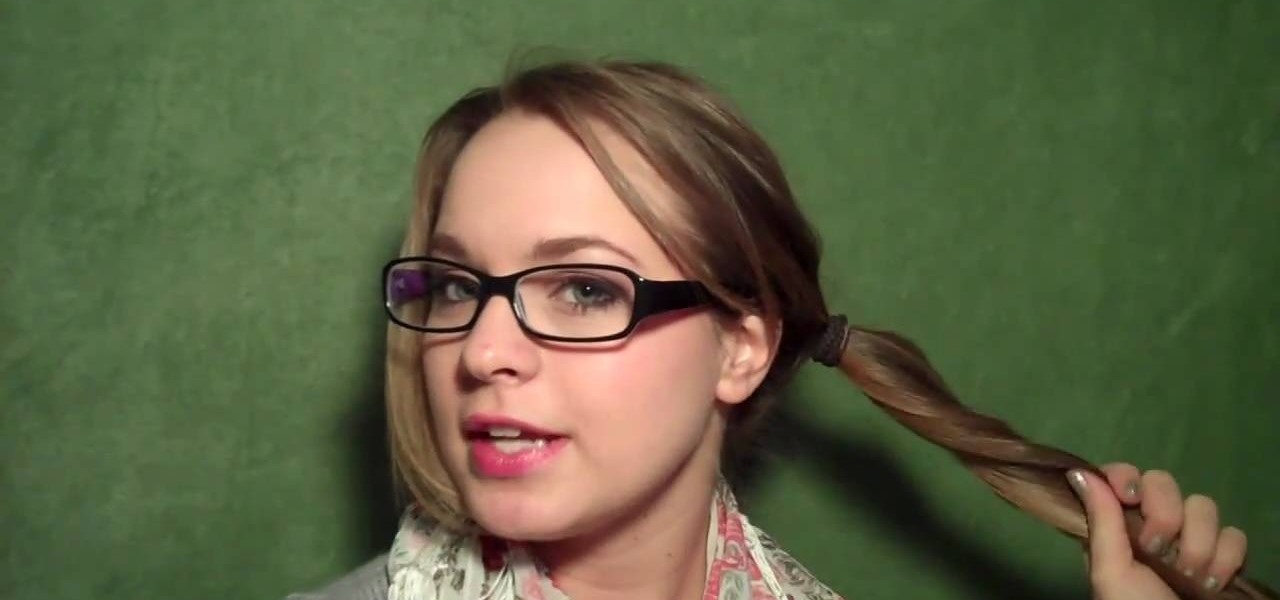A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.
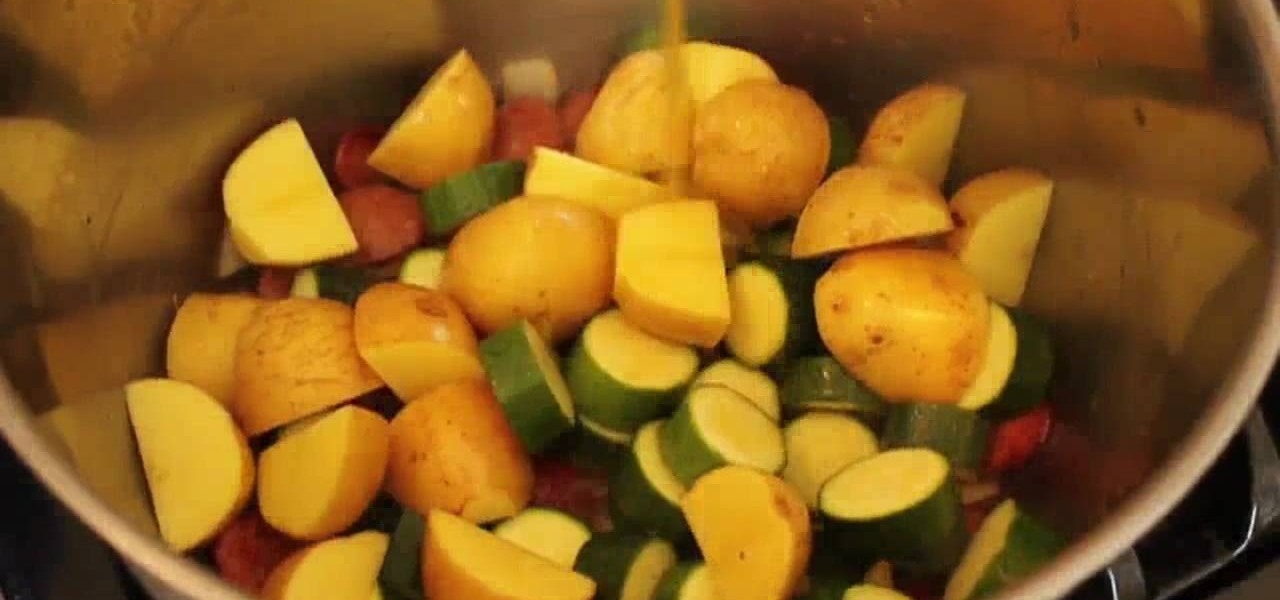
Warm summer nights call for equally warm and savory stews that harness the flavor of the fresh vegetables that are in season. So before we head into fall, try out this delicious recipe for a sausage, potato, and zucchino stew.

It is simple to make a booklet from one piece of paper. Take one A4 size paper then fold it to equally, then unfold it and you can fold it to right of edge and left of edges both sides are equal. Then unfold you can see like zigzag and cut it to middle point of the paper and fold it to use booklet. It is comfortable and easy to use it.
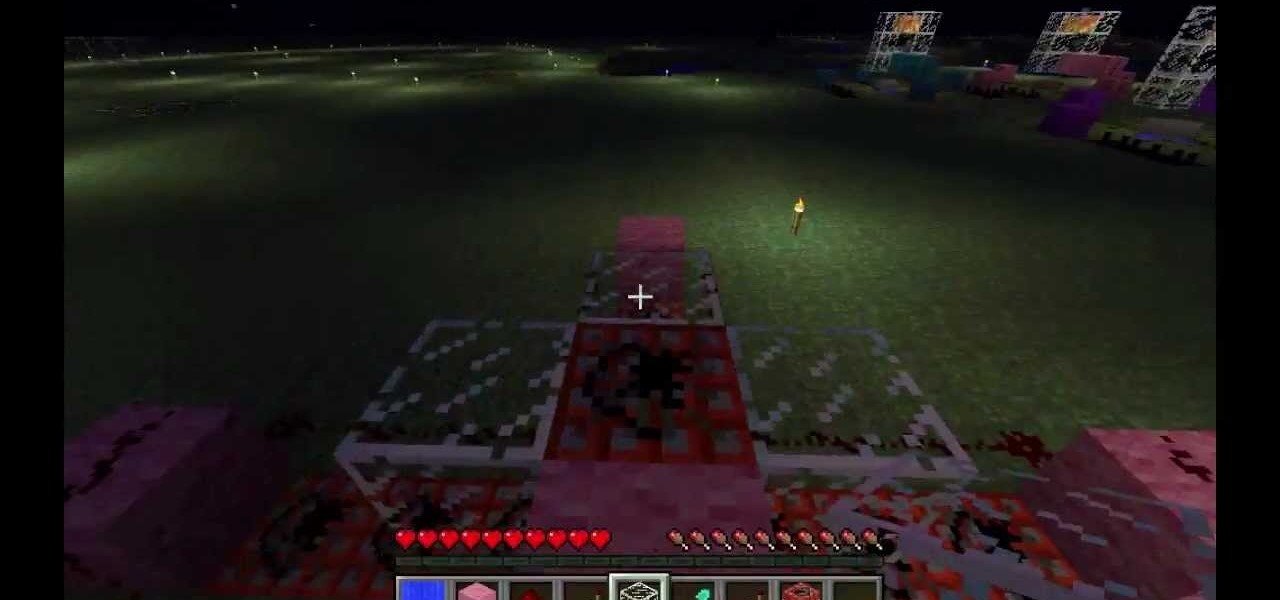
If you're looking for a big boom in Minecraft 1.8, try building one of these cannons. The first part of the tutorial will show you how to build a vertical TNT cannon that can create a huge explosion. The second part of the tutorial showcases the creation of a sand or gravel cannon in Minecraft 1.8 that is equally impressive!

In this video, learn how to pair your Bluetooth enabled phone with your new 2009 Nissan head unit. This procedure should work with multiple Nissan models and is not as simple as other car makers, but is equally effective. This will take a few extra minutes but is worth it in terms of safety and simplicity once it is up and running.
There are a couple ways to include HTML when coding PHP. Learn two options that work equally well, then decide which one makes the code more clear and concise for you.

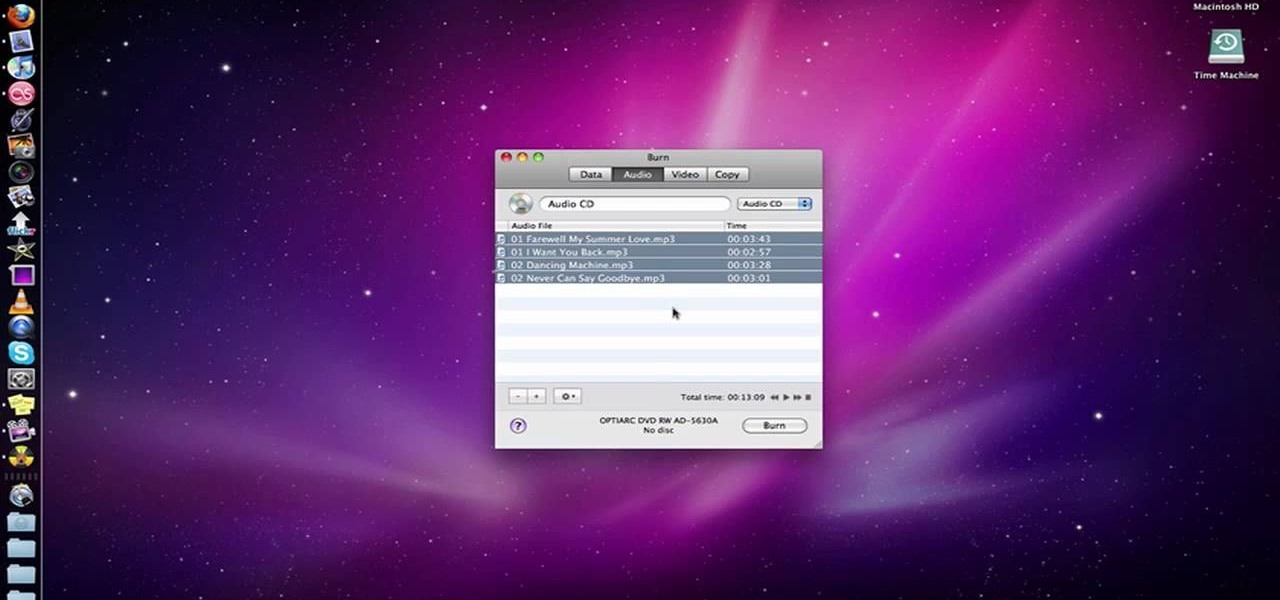
Looking better (but equally free) way to burn DVDs from within Apple's Mac OS X? See how to use Burn, the open-source optical media authoring tool, acheive just that with this home-computing how-to. For details, including step-by-step instructions, and to get started burning your own discs with Burn, watch this home-computing how-to.

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

It's important that whatever wonderful gift you have to give is encased in an equally wonderful gift bag. This tutorial paper design video will teach you to make your very own super cute paper bags with various products.

This 14-minute video explains the basics of room layout and acoustic treatment, and presents practical solutions to many common problems. The focus is on home theaters, but all of the information applies equally to professional recording studios and mastering rooms.

Learn how to use linear and lateral run/slide drills in order to achieve better control and balance of your body, working both legs equally. A must for all football and soccer players.

In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

RC Car Action Magazine Editor Paul Onorato shows how to properly make equally sized body post holes. All you need is a marker. Watch this video tutorial and learn an easy tip for making even sized post holes on an RC vehicle.

¤¤ TIPS TO VISIT KUALA LUMPUR (KL) IN 2 DAYS ¤¤ How to visit and what to see when you have a very limited time to visit this city of contrast, equally rich in heritage and urban excitement.

Lee T. Dresang, MD of the University of Wisconsin School of Medicine and Public Health from the Deaprtment of Family Medicine give a discussion and demonstration of suturing techniques. Before beginning a procedure, you will need consent. One should irrigate lesion before beginning. A simple interrupted suture is easy to learn and fast, but unable to withstand stress. Vertical mattress sutures provide a good eversion of skin edges, closure of dead space, and strength, but also lead to scarrin...

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

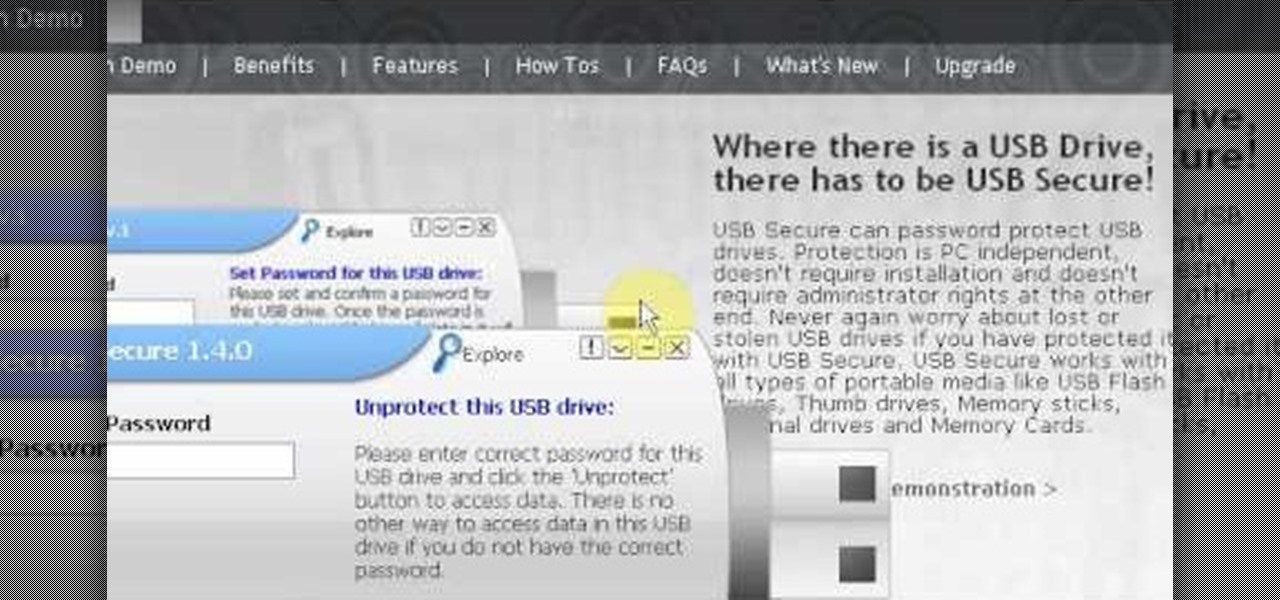
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

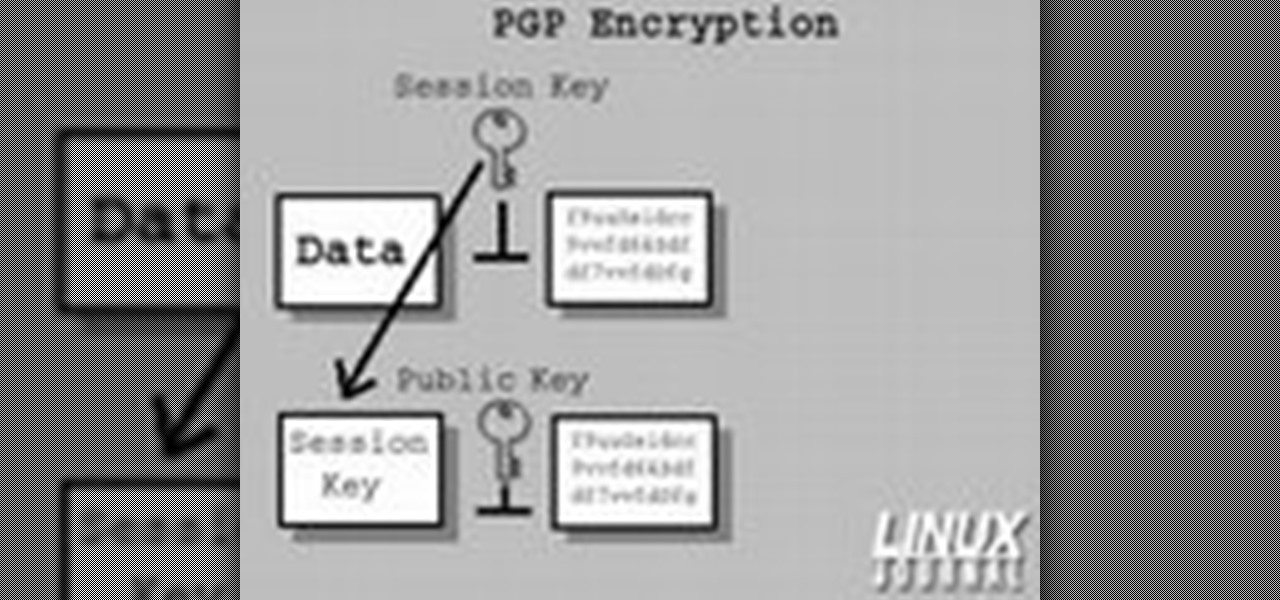
In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

There are two kinds of people who will find this video tutorial useful: Jewelers/jewelry making aficionados and cosplay fans. That's because this crystal clear, shiny resin gemstone can be used just as equally for a beautiful pendant or a paperweight as it can be for cosplay costume accessories like shoulder pads and helms.

Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Every girl needs a "go-to" recipe, as it were, for looking good. For every girl this "go-to" is different: One gal may fall back to a red lip and neutral eyes when she wants to look hot with minimal effort, while another may work some magic with her smudge brush to create the perfect smoky eye.

We all have a general idea of what a pin-up looks like: Big, buxom hips, wild curves that render men speechless, finger curled hair, and the iconic red lips with cat eyes combo. Bread out of the mold by creating a pin-up look that's equally glamorous and sexy but with a slight twist.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

This is one of the few times you should be a square. After all, achieving perfect, equally measured sides and angles involves fine tuned calculations that aren't open to creativity and whims.

Here's a news flash for you: Celebrities don't just wake up every morning with a head of Pantene commercial hair, a full face of perfectly airbrushed makeup, and a 1000 watt smile. In fact, they wake up a bit more like us: Groggy, major clow slick, and looking more like a sleepy mole person than a high paid action star.

Jazz music, along the lines of jazz greats like Coltrane and Thelonius Monk, is usually associated with the piano and the sax (as well as backup clarinets, oboes, etc.). But an equally fit instrument for playing jazz tunes is the acoustic guitar, which offers a light contrast to the larger, deeper toned instruments.

We love cupcakes equally with or without frosting, but sometimes adding that extra bit of vanilla buttercream frosting shaped into a rose or other flower turns the cupcake nomming experience from delicious to divine.

Hilary Duff is a very fun pop starlet. She does it all: sings, dances, acts, models! And with this look, you will feel like you can do it all too!

Welcome to a tennis lesson from FuzzyYellowBalls, the the best place to learn how to play tennis online. Our free video tennis lessons teach you how to play the game in a new way that combines technical analysis, visual learning, and step-by-step progressions.

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A formal occasion calls for a classic look. You Will Need

When "Hannah Montana: The Movie" came out, Miley Cyrus' song "The Climb" exploded and even made it to the top of the Billboard 100, obscuring several equally good though not as highly publicized singles. One of these excellent tunes is "Butterfly Fly Away," sung by the chanteuse and her father, Billy Ray Cyrus.

In this tutorial, we learn how to draw a horse step-by-step. First, you will want to draw the face of the horse. You can use intersecting lines in the face so you place the features of the face equally apart. After this, draw the outline for the body of the horse. Once you have this perfected, you can start to add in the hair for the horse. Next, draw in the details of the body and draw the shoes on the bottom of the horses feet. Draw in the tail, then add in shading and other lines to make i...