
How to Program in C# : Variables and Data Types (Part 2)
Welcome back my friends !! Today we'll go through the second part of this C# series


Welcome back my friends !! Today we'll go through the second part of this C# series

Here's a classic throw-back to times past with a timeless game of kick the can. Just because you don't need expensive equipment doesn't mean you can't have tons of fun. You can play this game just about anywhere.

Welcome to a tutorial explaining functions. This article will help clarify some things we have already been exposed to such as function prototypes, function calls, return values, etc.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Does it seem like everybody you know is declaring that they're gluten-free? Some wonder if the number of people with celiac disease are on the rise or if it's the latest fad diet. And it even goes beyond food: now there are beauty products that tout themselves as being free of gluten.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

What's up guys! It's time to discuss strings in more detail. Review

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

While it's currently impossible to go back in time, there is something wonderful about being able to undo the stupid stuff that you just did. While this is only really possible in the digital world, it does save you from real-life repercussions. If you've ever sent an email to the wrong person or sent some not-so-genius text messages, you know exactly what I'm talking about.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Is "Last Resort" Steampunk? Well, no. I mean, how could it be?

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!
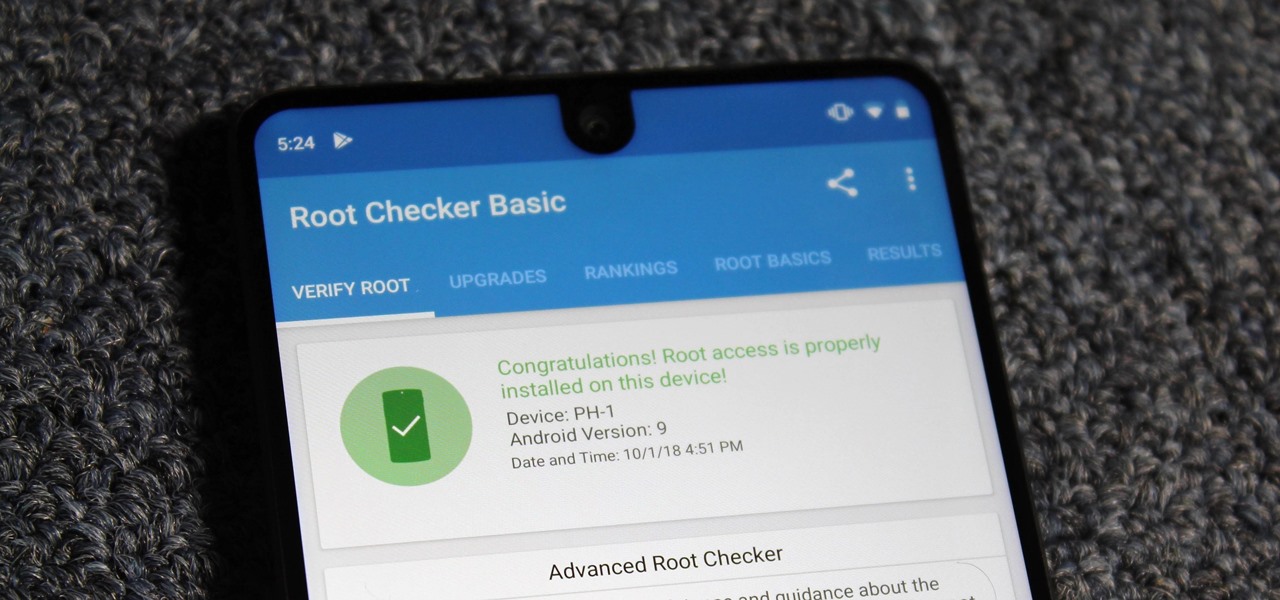
Despite its rocky start, the Essential PH-1 has a lot going for it. Not only does it get consistent security patches and system updates hours after the Pixels, but like the Google-developed lineup, it's also great for rooting. Not only is your warranty not void with rooting, but the process is pretty straightforward.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.
Hey everyone. Only found the site a few days ago but really loving it. Been

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!
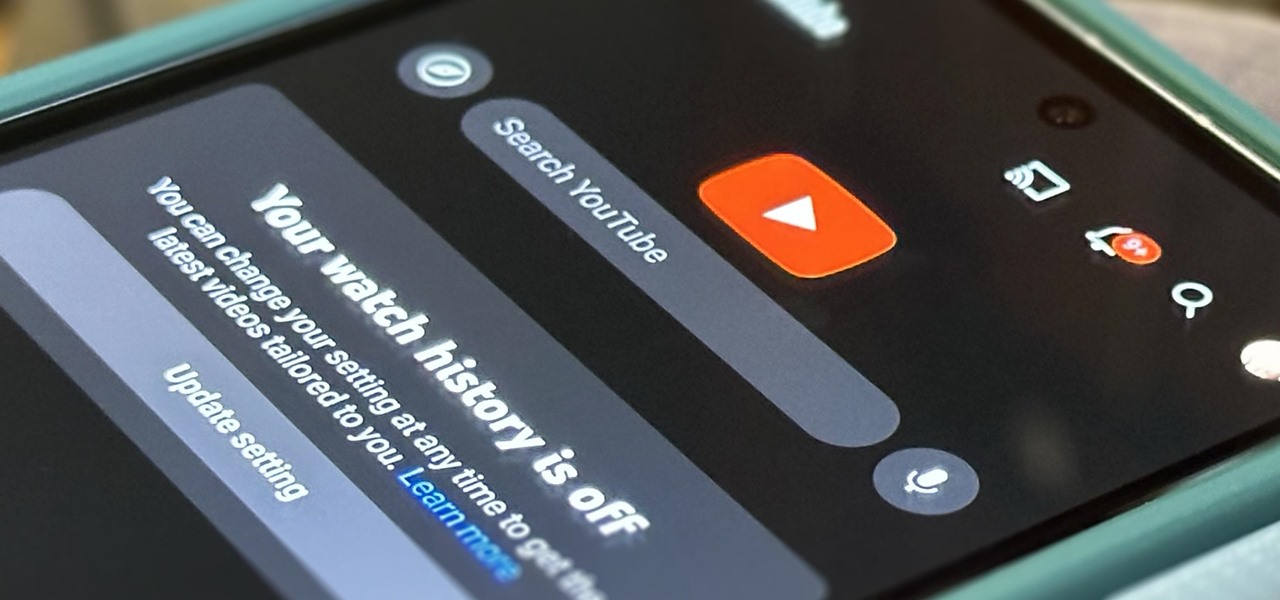
If you're an avid YouTube viewer, you may find yourself overwhelmed on the home page by recommendations from your past viewing habits. But now, you can have a clean slate on your YouTube home screen, free of recommendations.

A 13-cards Ramee game is usually played between 2 players with one pack of cards. If three players are playing, then a 9-cards Ramee is played with one deck. For 4-players and more 21-cards Ramee is played and two or more decks are needed.

This is the first of two Video's introducing you to your fingers from a Hand Analysis perspective. The Fingers mainly govern the mind and thinking. Somewhere in the vast fabric of time somebody discovered that the length and inclination of each particular finger can bring out certain personality traits. I still find it amazing and satisfying to see somebody with a longer than average 'little finger'(Mercury-communication), that sticks out that can't stop talking and buzzing around all excited...

The battle between first-person shooters is officially underway with the release of Battlefield 3 today. Who will win? Most experts are already declaring Call of Duty: Modern Warfare 3 the champ of the holiday retail clash between EA and Activision, despite MW3 not coming out until November 8th.
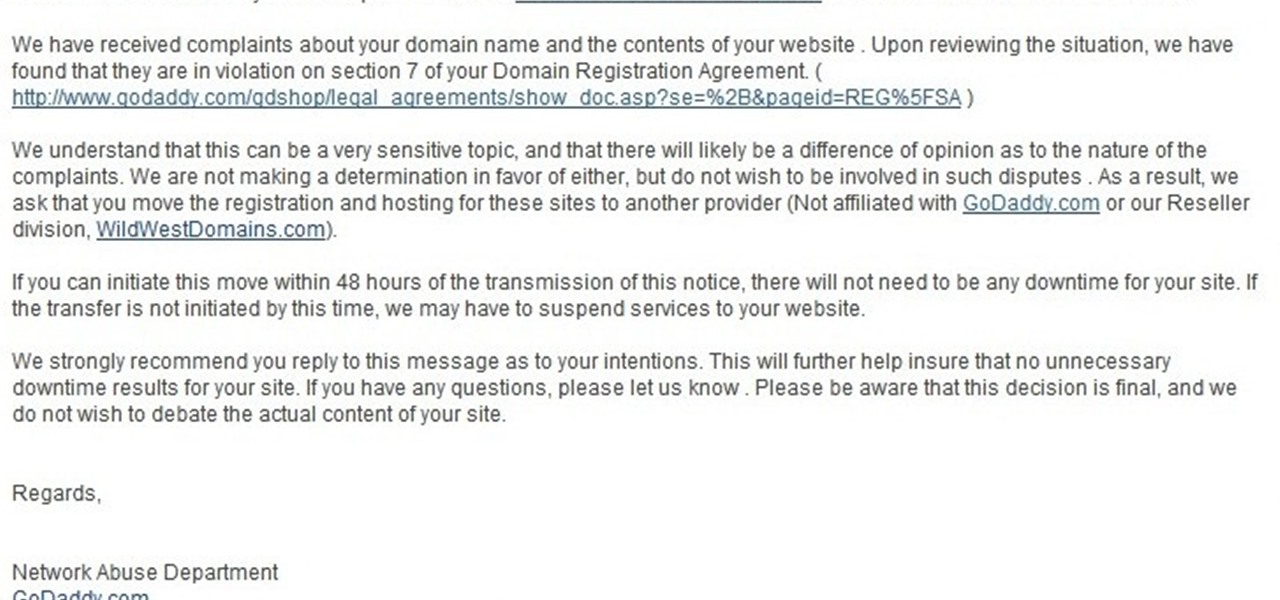
» ‘Obama Truth Team’ Orders GoDaddy To Shut Down Website. A political website that contained stinging criticism of the Obama administration and its handling of the Fast and Furious scandal was ordered to be shut down by the Obama campaign’s ‘Truth Team’. » Former Bush Attorney General Alberto Gonzales Confronted On Torture.
I read Timothy Keller’s The Reason for God on the recommendation of a philosophical friend and before I had finished it I was adding Keller’s The Prodigal God to my list of books to read. Keller has a gift for succinct and wise writing. I believe he truly has his finger on where society currently is spiritually, and where it might be going. In The Reason for God, Keller says that our society is both more spiritual and more secular than it has ever been. The book is a great look at the Christi...

It's been five long years since Dead Island was first revealed to the public, but today the zombie game finally saw the light of day with its release on PC, PlayStation 3 and Xbox 360. When the first teaser trailer came out from developer Techland, Dead Island looked nothing more than a cheap Resident Evil ripoff—on an island.

As Google+ became available to more people, it started running into issues of accounts being suspended due to names that did not sound "real". According to Google+'s community standards, names that users "commonly go by" were encouraged, but not pseudonyms. Those who were using pseudonyms in their Google+ profiles quickly found themselves suspended from using Google+.

Watch this first 'tutorial'.FauxTo! Hoax! Con! May 28, 2008, this video was uploaded to YouTube illustrating the popcorn popping power of a circle of ringing mobile phones. Radiation. Amazing. Viral. Millions viewed.