Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Breaking up is hard to do, especially if you've been dumped, and avoiding the urge to call your ex and try to reconcile can be tough. This video will give you some strategies you an use to resist the temptation to call your ex and move on with your life successfully.

This video explains how to answer one of the five toughest job interview questions, this one being "what are your greatest weaknesses?" In it John Heaney of "The Job Shopper" explains that the most important thing about this question is to realize that answering in a way that really paints a negative picture of yourself will negatively impact your potential employment.

What is your greatest weakness?" Do you know how to answer this question? Hint--it's not what most career books tell you (to give a veiled positive as a negative). Watch this quick video to find out the answer... Answer interview questions about your weaknesses.

If there ever was a day to eat green candy, St. Patrick's Day would be it. But is there something better than the banality of green candy swarming the streets on St. Patty's Day? Yes—glowing green candy, and Instructables user BrittLiv wants us to show you how it's done.

It's sometimes possible to recognize when you've recently contracted HIV from signs and symptoms such as fever, rash, or swollen lymph nodes. This video will teach you how to recognize signs and symptoms of primary HIV infection that are experienced by between 40 and 90% of individuals after they are first infected with HIV. Primary HIV infection occurs during the first few weeks or months after a person first becomes infected with HIV. Symptoms include rash and/or fevers, possibly in combina...

Watch balloon twister Michael to learn how to tear a balloon into two pieces. First, inflate the balloon, tie it, and then twist to create a point of weakness. Tug hard!

Here is a short instructional video describing the weakness of large Master brand locks. See how to crack a Master Lock #5 with a soda can shim. It is so easy to hack and crack open almost any type of lock if you know its weaknesses. The only tool you really need to open a lock is an aluminum can shim made from a soda can. Check out this how-to video and embark on your new career in delinquency.

In this Spirituality video tutorial you will learn how to palm read; crosses and islands on the main lines. These very often come on the main lines and sometimes they show a lot of changes in the person's life. If there is a cross on the heart line, it implies an emotional change. It could be a divorce. Islands on the heart line imply upsets; like an upset in marriage. Islands in the head line are often there because of a slowdown, may be they have changed their thinking or may be they have g...

"The Social Man" answers a question about how to make quality friends with guys. He answers from his person experience and says that many times guys feel like they can't show weakness, and they try to act too cool, which comes across as trying to prove something. A guy who does that comes across as approval-seeking. He suggests not being competitive with other guys, and think about giving to other people instead. Guys shouldn't work so hard to get women that they don't let other men into thei...

Darnit! Are you tired of getting slammed in arm wrestling matches? Before you switch to thumb wrestling, take a little time to hone your technique with this video including tips on how to win your next arm wrestling match.

Getting splinters is no fun, but making them can be if you've got the right tools and the proper technique.

Learn how to play "Let The Flames Begin" by Paramore, an acoustic guitar tutorial. Follow along with this demonstration, lyrics here:

You know this is the job for you. Here’s how to convince the person doing the hiring. Learn how to do well in a job interview.

Don't sit back and take verbal abuse! This tutorial will teach you how to dish it back out and craft the perfect insult.

Yes, bubonic plague—the Black Death that killed millions in the Middle Ages— is still out there. It even infects and kills people in the United States. Without treatment, half the people infected die, but the Food and Drug Administration approved ciprofloxacin in 2015 to treat plague, and it has just successfully been used to stop the infection in five people.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

If you just installed the iOS 11 beta on your iPhone, you're automatically sending your location data to Apple — even if you don't want to. Luckily, there's an easy way to prevent Apple from seeing this data if you don't want them to.

If smartphone video games have a weakness, it's probably their inability to emulate the riveting and immersive experience that consoles offer.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

While there is definitely no shortage of video game emulators in the Android Market, it lacks in modern gaming consoles. Nintendo 64, Game Boys, and Sega Genesis are all accounted for, but what about emulators for some of the gaming consoles that have come out in the, let's say...past decade?

The prospect of loss or theft is something we constantly live with. Stolen iPhones fetch a premium price on the black market for parts like OLED display assemblies, frames, and charging ports. Making matters worse, if someone were to steal your phone, they could simply turn it off to avoid anti-theft features like Find My iPhone.

According to App Annie, the average person's phone contains 60–90 apps. Such a large amount can easily crowd an app drawer, especially since the same source states that only about 30 are used in a month. Having a way to organize apps in the app drawer can help you avoid wasting time searching.

One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched this weakness with its iOS 11.3.1 update.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

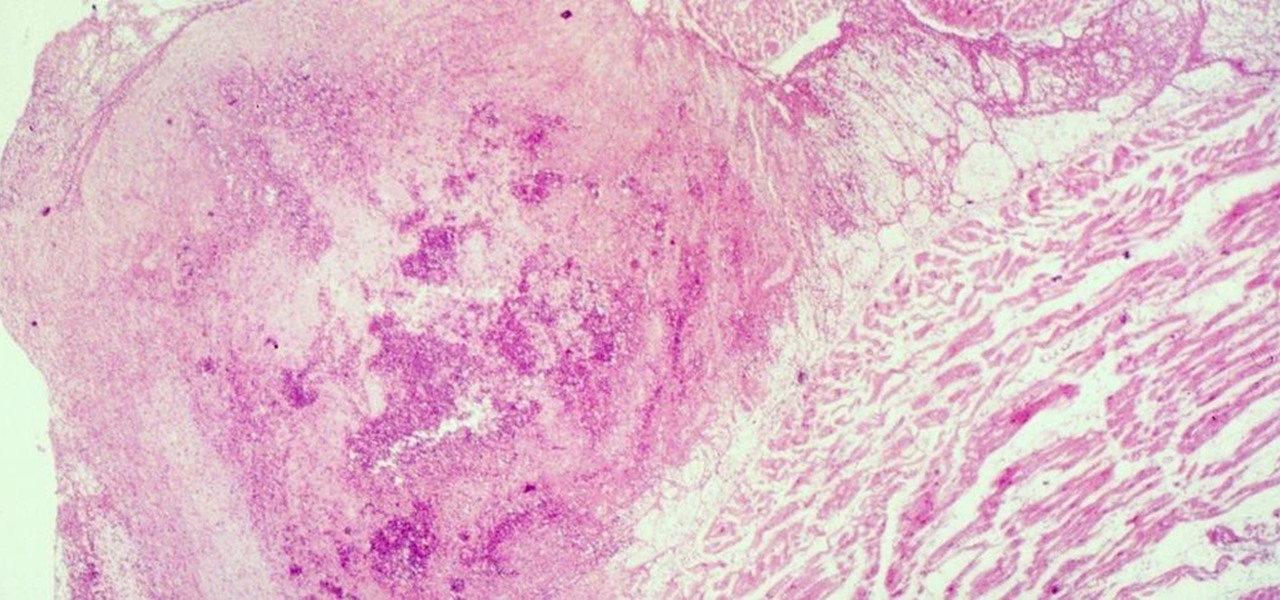
Four million Americans misused prescription opioid painkillers in 2014. Those who do are 40 times more likely to inject heroin or other drugs than other people. Now, the Centers for Disease Control and Prevention (CDC) are blaming that misuse for a 12-fold increase in endocarditis, an infection of the heart valves.

A recent case of Powassan virus has been reported in Saratoga County and may have been the cause of the infected patient's death. It's the 24th case in New York State since 2000, and will be reported to the CDC tomorrow, the NY Department of Health told Invisiverse. The tick-borne illness has no vaccine or specific treatments and can damage the nervous system.

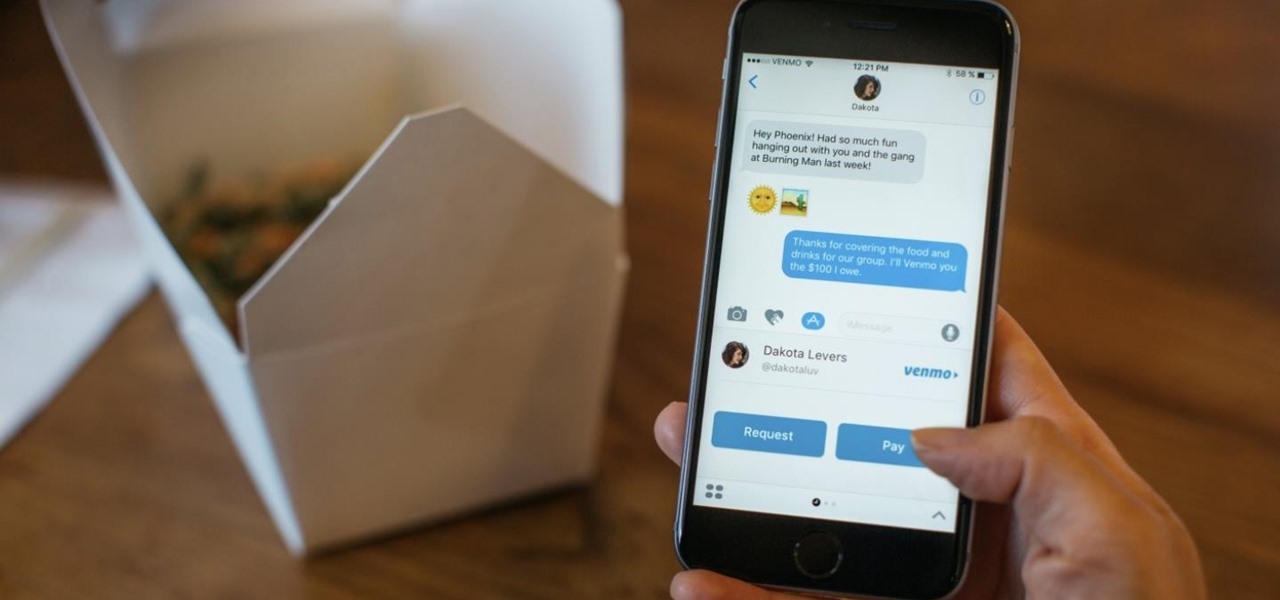
For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

A case of West Nile virus recently confirmed in a person in Barton County, is the first human case of 2017 in Kansas. State health officials confirmed the appearance of West Nile this year in a press release on June 9th.

We were really rooting for you this time, BlackBerry! With the phone company having minimal success in the past with smartphones, the BlackBerry KEYone was extremely promising. That is until YouTube Reviewer JerryRigEverything discovered a fatal flaw, the phone's screen popped off with just a bit of pressure and then stopped working. So...there's that.

The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

Every fall, we can expect a few things: leaves changing colors, cooler temperatures, and Samsung and Apple releasing new phones that fanboys and fangirls will argue about until the following year. This year, Samsung is mixing it up, releasing two phones in the Galaxy Note series. Let's see how the larger phones compare.

Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

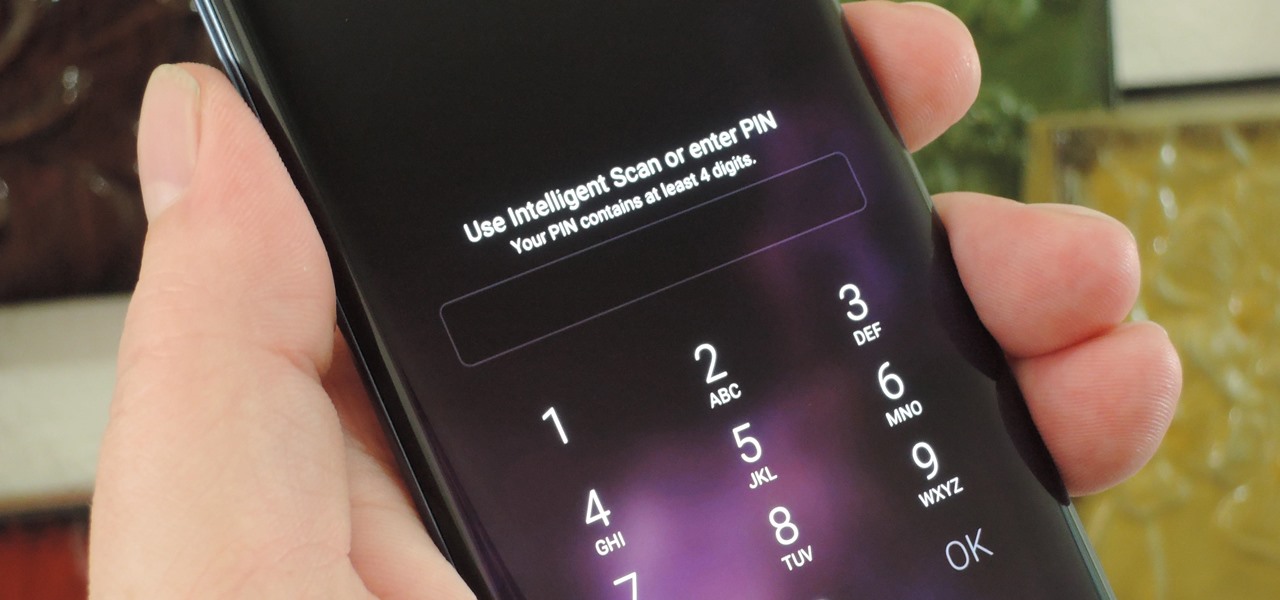
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

The incidence of tuberculosis (TB) is dropping in the US, but the World Health Organization (WHO) considers it to be epidemic in the rest of the world — there were over 10 million new cases in 2016.

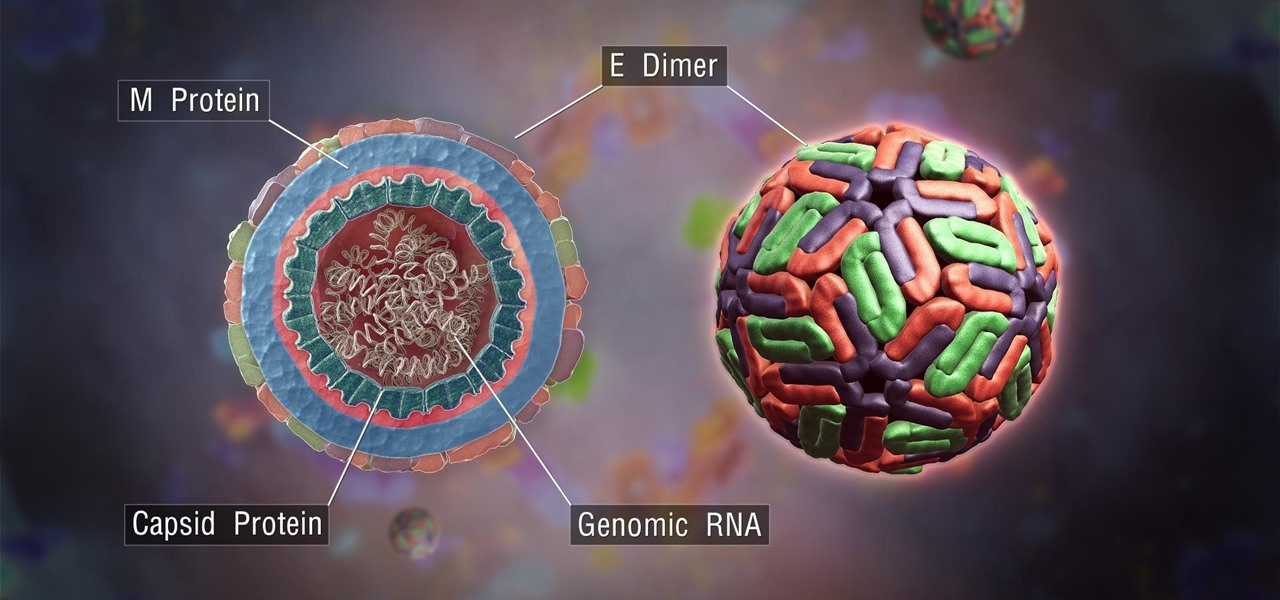
A recent study offers information that might help combat a deadly virus that affects an estimated 300,000 people each year in West Africa.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.